文档:https://help.aliyun.com/document_detail/109791.html?spm=a2c4g.11186623.6.580.55031c6fdzUdch
开源项目(基于sercurity 实现的sp+idp):https://github.com/OpenConext/Mujina
笔者未完成最终的对接,原因阿里云该功能处于内测阶段
大致思路就是根据文档上来,
一、上传至阿里云的xml(与【saml 基于用户的联盟访问(我方idp实现)】对接阿里 一致,不用修改)
<?xml version="1.0"?>
<EntityDescriptor xmlns="urn:oasis:names:tc:SAML:2.0:metadata" entityID="https://mytest.com">
<IDPSSODescriptor xmlns:ds="http://www.w3.org/2000/09/xmldsig#" protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol">
<KeyDescriptor use="signing">
<ds:KeyInfo xmlns:ds="http://www.w3.org/2000/09/xmldsig#">
<ds:X509Data>
<ds:X509Certificate>
MIIDEzCCAfugAwIBAgIJAKoK/heBjcOYMA0GCSqGSIb3DQEBBQUAMCAxHjAcBgNVBAoMFU9yZ2Fu
aXphdGlvbiwgQ049T0lEQzAeFw0xNTExMTExMDEyMTVaFw0yNTExMTAxMDEyMTVaMCAxHjAcBgNV
BAoMFU9yZ2FuaXphdGlvbiwgQ049T0lEQzCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEB
ANBGwJ/qpTQNiSgUglSE2UzEkUow+wS8r67etxoEhlzJZfgK/k5TfG1wICDqapHAxEVgUM10aBHR
ctNocA5wmlHtxdidhzRZroqHwpKy2BmsKX5Z2oK25RLpsyusB1KroemgA/CjUnI6rIL1xxFn3KyO
Fh1ZBLUQtKNQeMS7HFGgSDAp+sXuTFujz12LFDugX0T0KB5a1+0l8y0PEa0yGa1oi6seONx849ZH
xM0PRvUunWkuTM+foZ0jZpFapXe02yWMqhc/2iYMieE/3GvOguJchJt6R+cut8VBb6ubKUIGK7pm
oq/TB6DVXpvsHqsDJXechxcicu4pdKVDHSec850CAwEAAaNQME4wHQYDVR0OBBYEFK7RqjoodSYV
XGTVEdLf3kJflP/sMB8GA1UdIwQYMBaAFK7RqjoodSYVXGTVEdLf3kJflP/sMAwGA1UdEwQFMAMB
Af8wDQYJKoZIhvcNAQEFBQADggEBADNZkxlFXh4F45muCbnQd+WmaXlGvb9tkUyAIxVL8AIu8J18
F420vpnGpoUAE+Hy3evBmp2nkrFAgmr055fAjpHeZFgDZBAPCwYd3TNMDeSyMta3Ka+oS7GRFDeP
kMEm+kH4/rITNKUF1sOvWBTSowk9TudEDyFqgGntcdu/l/zRxvx33y3LMG5USD0x4X4IKjRrRN1B
bcKgi8dq10C3jdqNancTuPoqT3WWzRvVtB/q34B7F74/6JzgEoOCEHufBMp4ZFu54P0yEGtWfTwT
zuoZobrChVVBt4w/XZagrRtUCDNwRpHNbpjxYudbqLqpi1MQpV9oht/BpTHVJG2i0ro=
</ds:X509Certificate>
</ds:X509Data>
</ds:KeyInfo>
</KeyDescriptor>
<SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://sgarcia-us-preprod.onelogin.com/trust/saml2/http-redirect/slo/672234"/>
<NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress</NameIDFormat>
<SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="http://kxhxs2.natappfree.cc/SingleSignOnService"/>
<SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="http://kxhxs2.natappfree.cc/SingleSignOnService"/>
<SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:SOAP" Location="http://kxhxs2.natappfree.cc/SingleSignOnService"/>
</IDPSSODescriptor>
</EntityDescriptor>二、我方idp配置
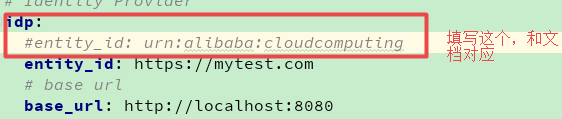
修改IdpConfiguration.resetAttributes 中的方法
private void resetAttributes() {
attributes.clear();
//TODO 下面三条配置参考文档,第一条笔者未测试通过(着重看文档)
putAttribute("https://www.aliyun.com/SAML-Role/Attributes/Role", "\n" +
"acs:ram::1878148656329563:role/aliyuncccdefaultrole,acs:ram::$account_id:saml-provider/provider1");
putAttribute("https://www.aliyun.com/SAML-Role/Attributes/RoleSessionName","ss");
putAttribute("https://www.aliyun.com/SAML-Role/Attributes/SessionDuration","1800");
}修改SsoController.doSSO 中方法
private void doSSO(HttpServletRequest request, HttpServletResponse response, Authentication authentication, boolean postRequest) throws ValidationException, SecurityException, MessageDecodingException, MarshallingException, SignatureException, MessageEncodingException, MetadataProviderException, IOException, ServletException {
SAMLMessageContext messageContext = samlMessageHandler.extractSAMLMessageContext(request, response, postRequest);
AuthnRequest authnRequest = (AuthnRequest) messageContext.getInboundSAMLMessage();
String assertionConsumerServiceURL = idpConfiguration.getAcsEndpoint() != null ? idpConfiguration.getAcsEndpoint() : authnRequest.getAssertionConsumerServiceURL();
List<SAMLAttribute> attributes = attributes(authentication);
SAMLPrincipal principal = new SAMLPrincipal(
authentication.getName(),
attributes.stream().filter(attr -> "urn:oasis:names:tc:SAML:1.1:nameid-format".equals(attr.getName()))
.findFirst().map(attr -> attr.getValue()).orElse(NameIDType.UNSPECIFIED),
attributes,
authnRequest.getIssuer().getValue(),
authnRequest.getID(),
assertionConsumerServiceURL,
messageContext.getRelayState());
//参考文档
principal.setAssertionConsumerServiceURL("https://signin.aliyun.com/saml-role/sso");
samlMessageHandler.sendAuthnResponse(principal, response);
}
最终效果:
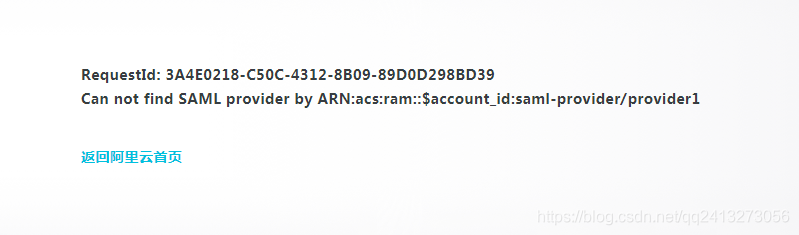
这个错误是因为, 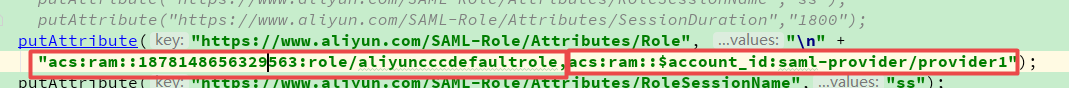
未解决







 本文档介绍了如何使用SAML进行基于角色的联盟访问,并通过我方IDP实现与阿里的对接。参考阿里云官方文档及开源项目Mujina,主要涉及上传XML配置到阿里云及修改IDP的IdpConfiguration和SsoController。由于阿里云功能尚处内测,目前对接未完成,存在错误待解决。
本文档介绍了如何使用SAML进行基于角色的联盟访问,并通过我方IDP实现与阿里的对接。参考阿里云官方文档及开源项目Mujina,主要涉及上传XML配置到阿里云及修改IDP的IdpConfiguration和SsoController。由于阿里云功能尚处内测,目前对接未完成,存在错误待解决。
















 1824
1824

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








