文章目录
一、MISC
(二)Retrieve_the_passcode
ARCHPR不能破解RAR5.0版本的rar文件
import numpy as np
import matplotlib.pyplot as plt
from mpl_toolkits.mplot3d import Axes3D
lis = [1,3,1,1.25,3,1,1.5,3,1,1.75,3,1,2,3,1,2,2.75,1,2,2.5,1,2,2.25,1,2,2,1,2,1.75,1,2,1.5,1,1,2.25,1,1.25,2.25,1,1.5,2.25,1,1.75,2.25,1,1,1.5,1,1.25,1.5,1,1.5,1.5,1,1.75,1.5,1,3,3,1,3.25,3,1,3.5,3,1,3.75,3,1,4,3,1,3.25,2.25,1,3.5,2.25,1,3.75,2.25,1,4,2.25,1,4,2,1,4,1.75,1,4,1.5,1,3,1.5,1,3.25,1.5,1,3.5,1.5,1,3.75,1.5,1,3,1.75,1,3,2,1,3,2.25,1,3,2.5,1,3,2.75,1,5,3,1,5.25,3,1,5.5,3,1,5.75,3,1,6,3,1,6,2.25,1,6,2,1,6,1.75,1,6,1.5,1,5.75,1.5,1,5.5,1.5,1,5.25,1.5,1,5,1.5,1,5,2.25,1,5.25,2.25,1,5.5,2.25,1,5.75,2.25,1,5,2.5,1,5,2.75,1,7,3,1,7.25,3,1,7.5,3,1,7.75,3,1,8,3,1,8,2.75,1,8,2.5,1,8,2.25,1,8,2,1,8,1.75,1,8,1.5,1,9,3,1,9.25,3,1,9.5,3,1,9.75,3,1,10,3,1,10,2.75,1,10,2.5,1,10,2.25,1,9.75,2.25,1,9.5,2.25,1,9.25,2.25,1,9,2.25,1,9,2,1,9,1.75,1,9,1.5,1,9.25,1.5,1,9.5,1.5,1,9.75,1.5,1,10,1.5,1,11,3,1,11.25,3,1,11.5,3,1,11.75,3,1,12,3,1,12,2.75,1,12,2.5,1,12,2.25,1,12,2,1,12,1.75,1,12,1.5,1,11.75,1.5,1,11.5,1.5,1,11.25,1.5,1,11,1.5,1,11,1.75,1,11,2,1,11,2.25,1,11,2.5,1,11,2.75,1,11.25,2.25,1,11.5,2.25,1,11.75,2.25,1]
x = lis[0::3]
y = lis[1::3]
z = lis[2::3]
fig = plt.figure()
ax = plt.figure().add_subplot(111, projection = '3d')
ax.set_title('Scatter Plot')
ax.set_xlabel('X Label')
ax.set_ylabel('Y Label')
ax.set_zlabel('Z Label')
ax.scatter(x,y,z,c = 'r',marker = '.')
plt.legend('x1')
plt.show()

解压之后打开pdf。里面是pdf里有摩斯密码,解码后得到flag(转小写)

(二)海市蜃楼-1
改zip文件之后本能先搜一下字符串
grep -rni "iscc" *

得到flag
ISCC{zheshishui}
(三)区块链
pragma solidity ^0.7.0;
//SPDX-License-Identifier: UNLICENSED
contract look_look {
function sloc111() public pure returns (string memory){
return "flag{}";
}
}
合约地址: 0x0ed72dfd4c63dd97df8fec07e5a6bba466c6adf5
TESTNET Rinkeby (ETH) Blockchain Explorer (etherscan.io)输入合约地址查询一下

点击下面这个交易记录看交易细节

然后utf-8解码input data,这是交易的输入数据,其中包含了调用哪个函数,以及传递的参数。

(四)小明的宠物兔
foremost分离出压缩包,得到一串加盐对称加密(后来知道是rabbit)过的密文和一个里面放着密钥的加密过的压缩包
U2FsdGVkX18kNy7RlBvcV9WJsqa+oxvdd0Ir86U2cU2996N6ltZi7VVOaw==
直接CRC32把内容碰撞出来
import zipfile
import string
import binascii
def CrackCrc(crc): #CRC爆破
with open('flag.txt','a') as f:
dic = string.printable
for i in dic:
for j in dic:
for k in dic:
for h in dic:
for l in dic:
s = i + j + k + h + l
if crc == (binascii.crc32(s.encode())):
f.write(s)
return
def CrackZip(): #获取压缩文件的CRC校验码
path = r'key.zip'
crc = zipfile.ZipFile(path,'r').getinfo('key.txt').CRC
CrackCrc(crc)
if __name__=='__main__':
CrackZip()
print("CRC32碰撞完成")
拿到密钥(0_0)和密文rabbit解密一下得到flag
ISCC{u_really_know_rabbits}
(五)小明的表情包
提取一下关键字

先凯撒解密一下得到年份是NINETEEN NINETY NINE,即1999,然后ARCHPR设置????1999进行掩码解密解出来07071999

解压出的图片改一下文件头
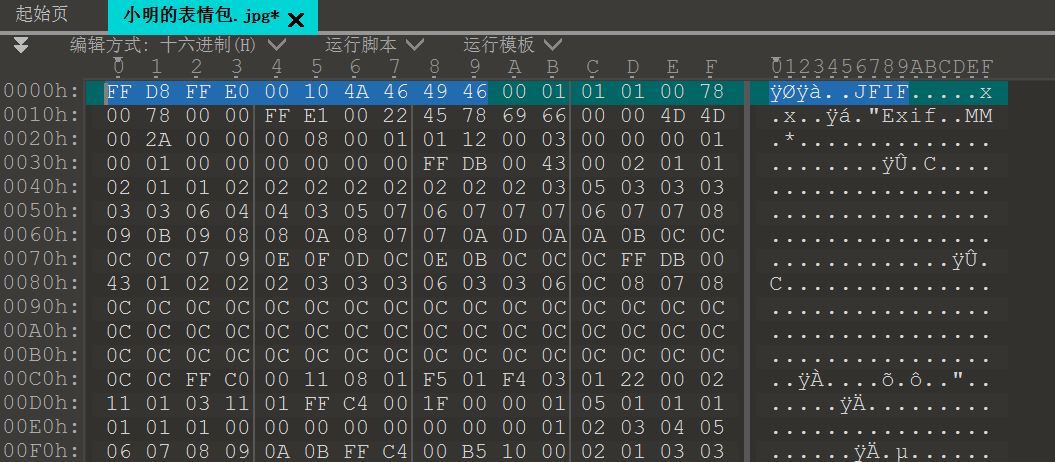
得到flag

二、Mobile
(一)Mobile Normal
前半部分是base64,主要是如何定位后半部分,看样子是藏在一个名为smile,编号为0x7F0B002B的资源文件里
jadx-gui反编译
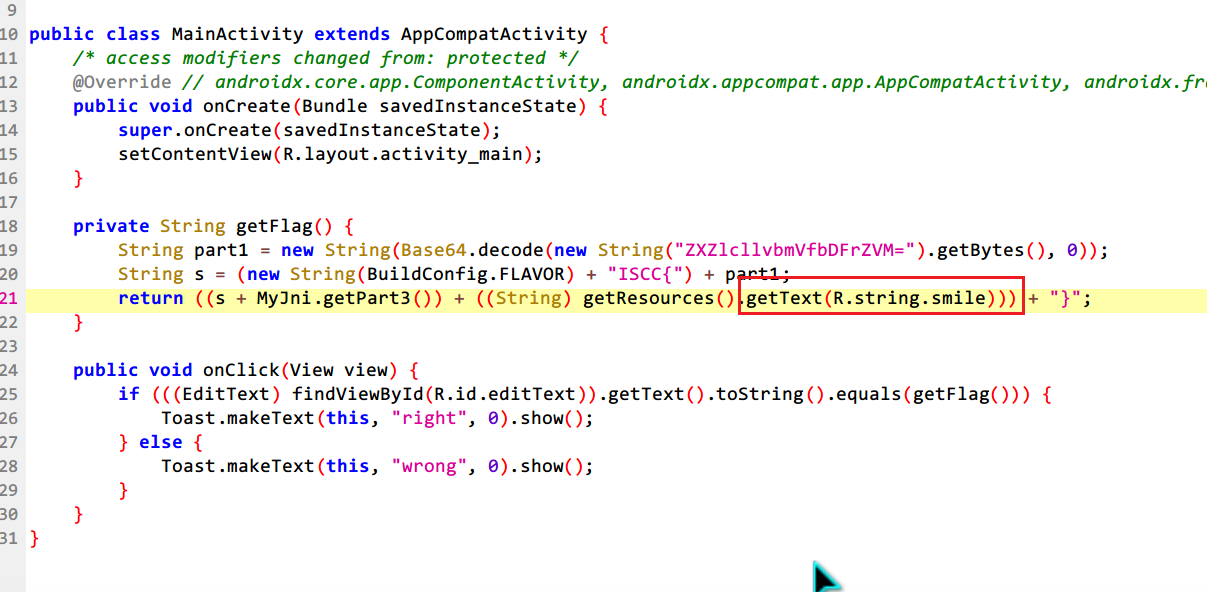
jeb反编译
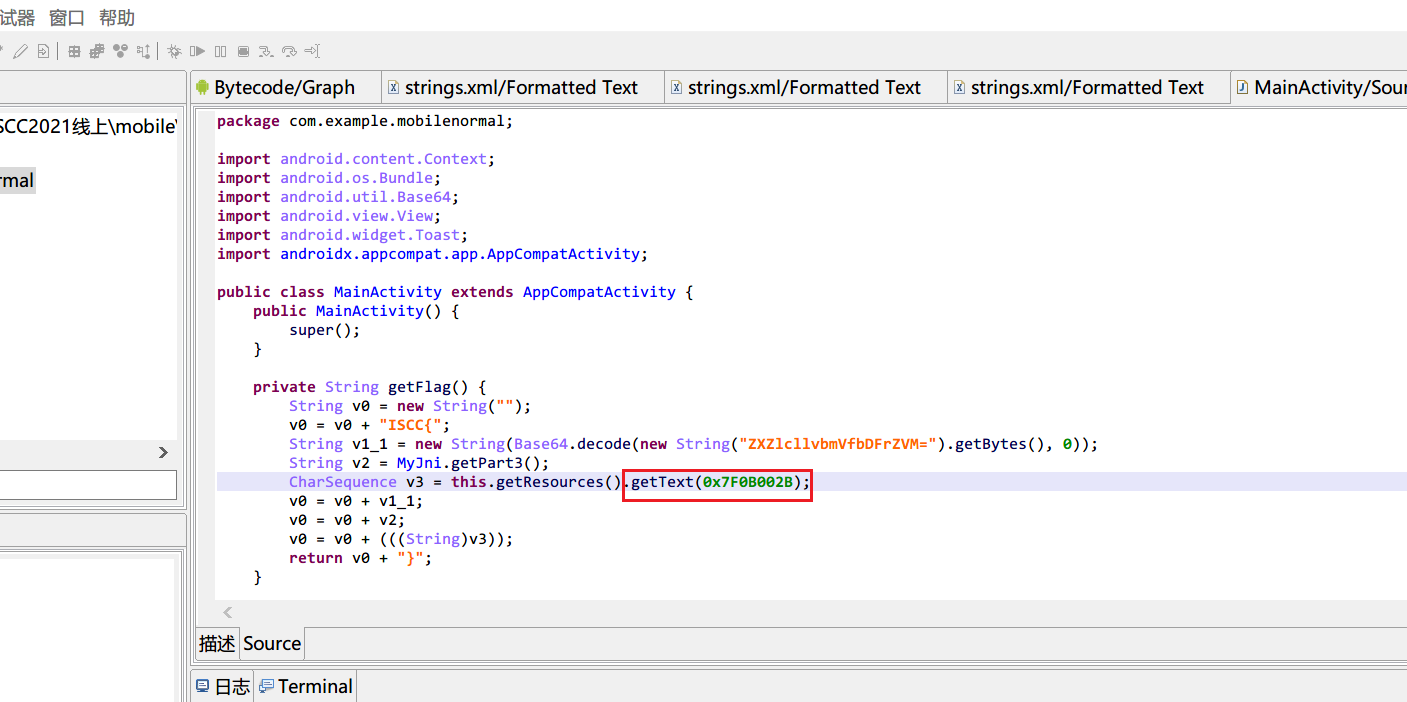
resources.arsc表存储着ID跟资源文件的映射关系,直接查一下表得到后半部分

拼一下得到flag
ISCC{everYone_l1keS_ANdr01d^_^}
(二)Mobile Easy
整个程序流程如下
f
i
r
s
t
置
换
→
{
Second把前半部分跟一个AES加密的密文作比对
Third把后半部分代入方程组验证
first置换\rightarrow\begin{cases} &\text{Second把前半部分跟一个AES加密的密文作比对}\\ &\text{Third把后半部分代入方程组验证} \end{cases}
first置换→{Second把前半部分跟一个AES加密的密文作比对Third把后半部分代入方程组验证
Second直接找个在线网站(AES在线加密解密工具 - MKLab在线工具)解一下AES,或者dump出来跑一下都行

再First逆置换一下得到
a='+0dNlE8us8'
flag=a.replace("dN", "B1").replace("8", "_").replace("P", "!").replace("hwl", "rea").replace('u', '1').replace("+", "m")
print(flag)
m0B1lE_1s_
Third直接用z3解一下
from z3 import *
a=[BitVec(f'a[{i}]',8) for i in range(8)]
solver=Solver()
solver.add(a[0] % 8 == 7)
solver.add(a[0] % 9 == 8)
solver.add(a[1] - 3 == 100)
solver.add(a[2] ^ 93 == 100)
solver.add(a[2] * 2 - 10 == a[3])
solver.add(a[4] + 1 == 120)
solver.add(a[5] ^ a[6] == 56)
solver.add(a[5] - a[6] == 24)
solver.add(a[6] - a[7] == 4)
solver.add(a[7] == 80)
if solver.check() == sat: #check()方法用来判断是否有解,sat(satisify)表示满足有解
ans = solver.model() #model()方法得到解
print(ans)
else:
print("no ans!")
得到
[a[3] = 104,
a[2] = 57,
a[0] = 255,
a[7] = 80,
a[6] = 84,
a[5] = 108,
a[4] = 119,
a[1] = 103]
a0貌似没解出来(bug吧),额外弄个循环跑一下,然后first再逆置换一下得到flag的后半部分
import string
a=[0]*8
for i in string.printable:
if ord(i)% 8 == 7 and ord(i) % 9 == 8:
a[0] = ord(i)
a[1] = 103
a[2] = 57
a[3] = 104
a[4] = 119
a[5] = 108
a[6] = 84
a[7] = 80
flag=''
for i in a:
flag+=chr(i)
a=flag.replace("dN", "B1").replace("8", " ").replace("P", "!").replace("hwl", "rea").replace('u', '1').replace("+", "m")
print(a)
最后拼接得到flag
ISCC{m0B1lE_1s_Gg9reaT!}
三、Reverse
(一)Garden
uncompyle6反编译一下

# uncompyle6 version 3.7.4
# Python bytecode 2.7 (62211)
# Decompiled from: Python 3.8.9 (tags/v3.8.9:a743f81, Apr 6 2021, 14:02:34) [MSC v.1928 64 bit (AMD64)]
# Embedded file name: garden.py
# Compiled at: 2021-02-28 12:29:29
import platform, sys, marshal, types
def check(s):
f = '2(88\x006\x1a\x10\x10\x1aIKIJ+\x1a\x10\x10\x1a\x06'
if len(s) != len(f):
return False
checksum = 0
for a, b in zip(f, s):
checksum += ord(b) ^ ord(a) ^ 123
return checksum == 0
if sys.version_info.major != 2 or sys.version_info.minor != 7:
sys.exit('试试 Python 2.7.')
if len(sys.argv) != 2:
sys.exit('usage: bronze.pyc <flag>')
flag = sys.argv[1]
if len(flag) >= 32:
print '太长了.'
sys.exit(1)
alphabet = set('abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789{}!@#$%+')
for ch in flag:
if ch not in alphabet:
print '不对.'
sys.exit(1)
if check(flag):
print '就是这个!'
sys.exit(0)
else:
print '搞错了.'
sys.exit(1)
123跟'2(88\x006\x1a\x10\x10\x1aIKIJ+\x1a\x10\x10\x1a\x06'每一位异或一下
key='2(88\x006\x1a\x10\x10\x1aIKIJ+\x1a\x10\x10\x1a\x06'
flag=''
for i in key:
flag+=chr(ord(i)^123)
print(flag)
ISCC{Makka2021Pakka}
(二)Analysis
先把比对密文取出来
Str[0] = 0x43;
Str[1] = 0xDF;
Str[2] = 0x14;
Str[3] = 3;
Str[4] = 0xD;
Str[5] = 0x2C;
Str[6] = 9;
Str[7] = 1;
Str[8] = 0x17;
Str[9] = 0x17;
Str[10] = 8;
Str[11] = 0xFC;
Str[12] = 0x2B;
Str[13] = 0xFA;
Str[14] = 0x14;
Str[15] = 0x17;
Str[16] = 0xF9;
Str[17] = 0x25;
Str[18] = 0xF5;
Str[19] = 0x22;
Str[20] = 0x3D;
Str[21] = 0xCE;
Str[22] = 0x18;
Str[23] = 0x16;
Str[24] = 0xA;
主要的逻辑是mix函数
int __cdecl mix(char *a1, char *Str, int a3)
{
char v3; // dl
int result; // eax
char v5; // [esp+14h] [ebp-24h]
int n; // [esp+18h] [ebp-20h]
int m; // [esp+1Ch] [ebp-1Ch]
int l; // [esp+20h] [ebp-18h]
size_t k; // [esp+24h] [ebp-14h]
int j; // [esp+28h] [ebp-10h]
int i; // [esp+2Ch] [ebp-Ch]
for ( i = 0; i < a3; ++i )
a1[i] -= 64;
for ( j = 0; j < a3; ++j )
a1[j] -= a1[j + 1];
for ( k = 0; k < strlen(Str); ++k )
Str[k] %= 64;
for ( l = 0; l < a3; ++l )
a1[l] += Str[l % 7];
for ( m = 0; a3 / 2 > m; ++m )
{
v5 = a1[m];
a1[m] = a1[a3 - m - 1];
a1[a3 - m - 1] = v5;
}
for ( n = 0; ; ++n )
{
result = n;
if ( n >= a3 )
break;
if ( (Str[n % 7] & 1) != 0 )
v3 = a1[n] + 2;
else
v3 = a1[n] + 1;
a1[n] = v3;
}
return result;
}
写exp
Str=[0 for i in range(25)]
Str[0] = 67
Str[1] = -33
Str[2] = 20
Str[3] = 3
Str[4] = 13
Str[5] = 44
Str[6] = 9
Str[7] = 1
Str[8] = 23
Str[9] = 23
Str[10] = 8
Str[11] = -4
Str[12] = 43
Str[13] = -6
Str[14] = 20
Str[15] = 23
Str[16] = -7
Str[17] = 37
Str[18] = -11
Str[19] = 34
Str[20] = 61
Str[21] = -50
Str[22] = 24
Str[23] = 22
Str[24] = 10
key="REVERSE"
key_l=[]
for i in key:
key_l.append(ord(i)%64)
for i in range(len(Str)):
if key_l[i%len(key_l)]&1==0:
Str[i]-=1
else:
Str[i]-=2
Str.reverse()
for i in range(len(Str)):
Str[i]-=key_l[i%len(key)]
for i in range(len(Str)-2,-1,-1):
Str[i]+=Str[i+1]
for i in range(len(Str)):
Str[i]+=64
flag=''
for i in range(len(Str)):
try:
flag+=chr(Str[i])
except:
continue
print(flag)
得到flag
ISCC{REVERSE_IS_NOT_HARD}










 本文详细介绍了参加信息安全挑战赛的过程,涉及多个技术领域,如密码学、区块链、逆向工程和移动应用分析。参赛者需解决包括摩斯密码解码、RAR文件破解、智能合约交互、加解密算法应用及移动应用资源提取等一系列问题,通过这些挑战深入理解并实践了信息安全技术。
本文详细介绍了参加信息安全挑战赛的过程,涉及多个技术领域,如密码学、区块链、逆向工程和移动应用分析。参赛者需解决包括摩斯密码解码、RAR文件破解、智能合约交互、加解密算法应用及移动应用资源提取等一系列问题,通过这些挑战深入理解并实践了信息安全技术。


















 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










