DVWA ( Dam Vulnerable Web Application ) DVWA 是用 PHP + Mysql 编写的一套用于常规
WEB 漏洞教学和检测的WEB脆弱性测试程序。包含了 SQL 注入、 XSS 、盲注等常见的一些安全漏洞。Kali
已自带了平台所需的环境,所以搭建非常简单。
配置环境
开启 MySQL
service mysql start关闭Apache
service apache2 stop运行 mysql -u root 连接 MySQL 并设置 MySQL root 密码
MariaDB [(none)]> use mysql \\使用数据库 mysql
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [mysql]> update user set password=PASSWORD('xxxxxx') where User='root'; \\更改 root 密码为 xxxxxx
Query OK, 4 rows affected (0.00 sec)
Rows matched: 4 Changed: 4 Warnings: 0
MariaDB [mysql]> flush privileges; \\刷新 MySQL 的系统权限相关表
Query OK, 0 rows affected (0.00 sec)
MariaDB [mysql]> create database dvwa; \\创建数据库 dvwa
Query OK, 1 row affected (0.00 sec)
由于 Kali Linux 下 MySQL 默认是使用 MariaDB, 所以无法使用 root 用户连接 mysql 必须创建一个新的用户用于连接使用, 根据需要可以赋予 root 权限.
MariaDB [mysql]> grant all on dvwa.* to dvwa@localhost identified by 'password';注意: 新用户(dvwa)的密码(password)最好不要为空!
配置 PHP
1.更新源
执行命令:sudo gedit /etc/apt/source.list,然后把下面的内容复制到source.list
#aliyun 阿里云
deb http://mirrors.aliyun.com/kali kali-rolling main non-free contrib
deb-src http://mirrors.aliyun.com/kali kali-rolling main non-free contrib
# ustc 中科大
deb http://mirrors.ustc.edu.cn/kali kali-rolling main non-free contrib
deb-src http://mirrors.ustc.edu.cn/kali kali-rolling main non-free contrib
#deb http://mirrors.ustc.edu.cn/kali-security kali-current/updates main contrib non-free
#deb-src http://mirrors.ustc.edu.cn/kali-security kali-current/updates main contrib non-free
# kali 官方源
deb http://http.kali.org/kali kali-rolling main non-free contrib
deb-src http://http.kali.org/kali kali-rolling main non-free contrib执行命令:sudo apt-get update
GD 支持
apt-get install php7.0-gd --fix-missing编辑 /etc/php/7.0/apache2/php.ini 修改 824 行 allow_url_include = Off 为 allow_url_include = On;然后Ctrl+F找到extension=,将extension=gd2前的分号去掉,让php开启gd2库
vim /etc/php/7.0/apache2/php.ini修改网站配置文件
mv config.inc.php.dist config.inc.php编缉dvwa/config/config.inc.php
$_DVWA[ 'db_user' ] = 'dvwa';
$_DVWA[ 'db_password' ] = 'password';
$_DVWA[ 'recaptcha_public_key' ] = '6LdK7xITAAzzAAJQTfL7fu6I-0aPl8KHHieAT_yJg';
$_DVWA[ 'recaptcha_private_key' ] = '6LdK7xITAzzAAL_uw9YXVUOPoIHPZLfw2K1n5NVQ';
$_DVWA[ 'default_security_level' ] = 'low';开启 Apache
service apache2 start下载 配置 DVWA
下载
wget https://github.com/ethicalhack3r/DVWA/archive/master.zip配置
mv master.zip /var/www/html
cd /var/www/html
unzip master.zip
mv DVWA-master dvwa
chown www-data:www-data /var/www/html/dvwa/hackable/uploads
chown www-data:www-data /var/www/html/dvwa/external/phpids/0.6/lib/IDS/tmp/phpids_log.txt
dvwa文件夹提权
chmod -R 777 /var/www/html/dvwa打开浏览器输入 ip/dvwa/setup.php 如本机 127.0.0.1/dvwa/setup.php
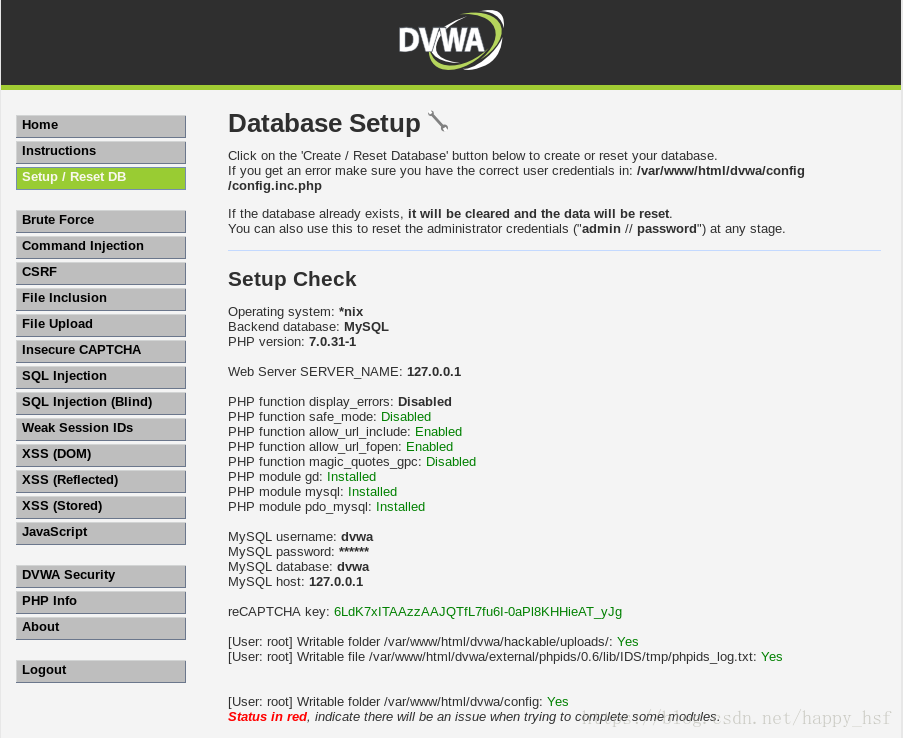
点击 Create/Reset Database
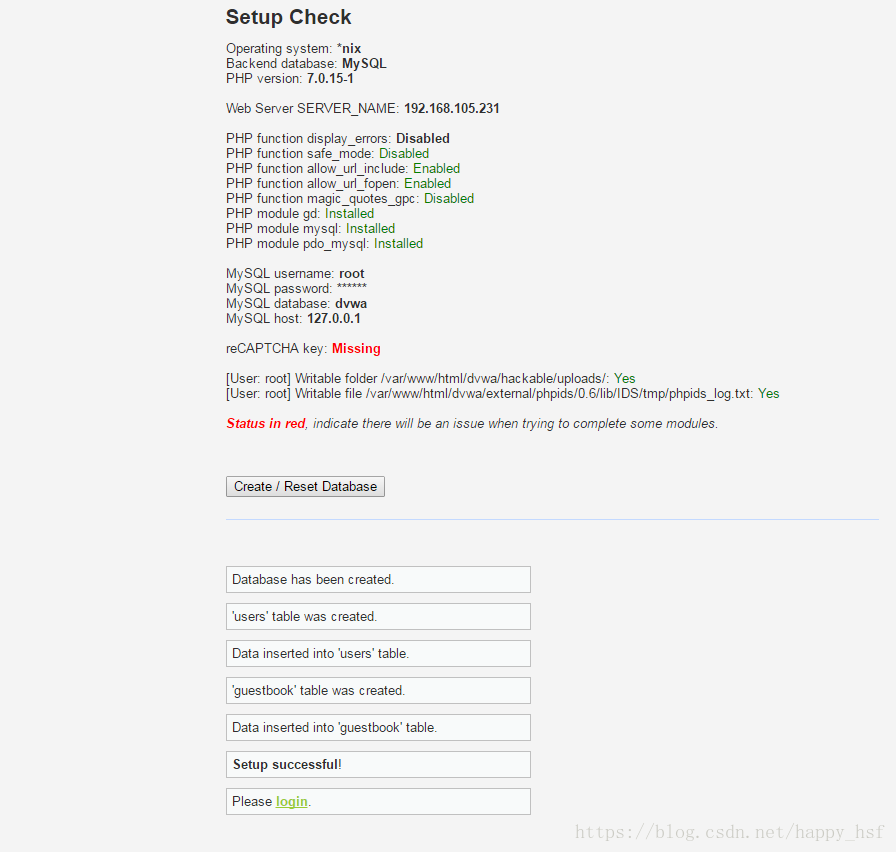

输入Username admin Password password 登录








 本文详细介绍了如何在Kali Linux环境下搭建DVWA(Dam Vulnerable Web Application)平台,包括配置MySQL、设置PHP环境、下载及配置DVWA程序等步骤,为网络安全学习和渗透测试提供实践环境。
本文详细介绍了如何在Kali Linux环境下搭建DVWA(Dam Vulnerable Web Application)平台,包括配置MySQL、设置PHP环境、下载及配置DVWA程序等步骤,为网络安全学习和渗透测试提供实践环境。
















 1万+
1万+

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








