C/S中单向认证大致流程

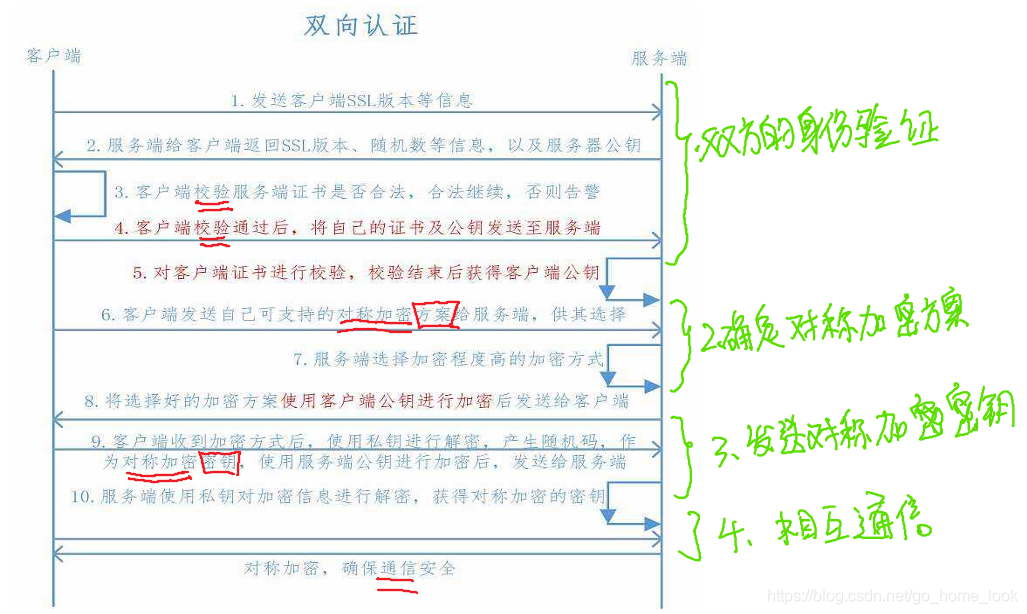
C/S中双向认证大致流程
使用命令生成各自的私钥和证书
客户端:
openssl req -newkey rsa:512 -nodes -keyout client.key -x509 -days 5 -out client.crt
-newkey rsa:512选项声明了使用RAS算法生成512位的私钥。
-nodes选项表明我们不使用密码加密私钥。
-keyout client.key:生成私钥
-out client.crt:生成CSR证书
服务器端:
openssl req -newkey rsa:512 -nodes -keyout server.key -x509 -days 5 -out server.crt

测试一下:
google@ubuntu1404:~/workspace/openssl/server$ openssl s_server -accept 2020 -key server.key -cert server.crt
Using default temp DH parameters
error setting certificate
140273329796928:error:0909006C:PEM routines:get_name:no start line:crypto/pem/pem_lib.c:745:Expecting: DH PARAMETERS
140273329796928:error:140AB18F:SSL routines:SSL_CTX_use_certificate:ee key too small:ssl/ssl_rsa.c:310:
结果出现了问题,貌似是在产生私钥时给的值太小了,那就删掉原来的文件,把原来的客户端和服务器端的值都改大一点吧!改成1024试一下看看
openssl req -newkey rsa:1024 -nodes -keyout server.key -x509 -days 5 -out server.crt
openssl req -newkey rsa:1024 -nodes -keyout client.key -x509 -days 5 -out client.crt
填写好生成证书的信息之后
服务器端输入openssl s_server -accept 2020 -key server.key -cert server.crt
客户端输入openssl s_client -connect localhost:2020 -cert client.crt -key client.key
双向认证测试结果
连上后服务器端输入hello world!结果如下:
google@ubuntu1404:~/workspace/openssl/server$ openssl s_server -accept 2020 -key server.key -cert server.crt
Using default temp DH parameters
ACCEPT
-----BEGIN SSL SESSION PARAMETERS-----
MH0CAQECAgMEBAITAgQgi7VOIMA4IwKdDQPAGKfZYIAaQF166qiWfYxrBMmFPZUE
MLGAyyYryR9kChTPG6Z3rgSKHC7nVoXHIhEnNtLBcXdv9Azjmb0Jb1CoVcvqknNa
PaEGAgRfB9mAogQCAhwgpAYEBAEAAACuBgIEZSqe7A==
-----END SSL SESSION PARAMETERS-----
Shared ciphers:TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256:TLS_AES_128_GCM_SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384:DHE-RSA-AES256-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES256-SHA:ECDHE-RSA-AES256-SHA:DHE-RSA-AES256-SHA:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES128-SHA:DHE-RSA-AES128-SHA:AES256-GCM-SHA384:AES128-GCM-SHA256:AES256-SHA256:AES128-SHA256:AES256-SHA:AES128-SHA
Signature Algorithms: ECDSA+SHA256:ECDSA+SHA384:ECDSA+SHA512:Ed25519:Ed448:RSA-PSS+SHA256:RSA-PSS+SHA384:RSA-PSS+SHA512:RSA-PSS+SHA256:RSA-PSS+SHA384:RSA-PSS+SHA512:RSA+SHA256:RSA+SHA384:RSA+SHA512:ECDSA+SHA224:ECDSA+SHA1:RSA+SHA224:RSA+SHA1:DSA+SHA224:DSA+SHA1:DSA+SHA256:DSA+SHA384:DSA+SHA512
Shared Signature Algorithms: ECDSA+SHA256:ECDSA+SHA384:ECDSA+SHA512:Ed25519:Ed448:RSA-PSS+SHA256:RSA-PSS+SHA384:RSA-PSS+SHA512:RSA-PSS+SHA256:RSA-PSS+SHA384:RSA-PSS+SHA512:RSA+SHA256:RSA+SHA384:RSA+SHA512:ECDSA+SHA224:ECDSA+SHA1:RSA+SHA224:RSA+SHA1
Supported Elliptic Groups: X25519:P-256:X448:P-521:P-384
Shared Elliptic groups: X25519:P-256:X448:P-521:P-384
CIPHER is TLS_AES_256_GCM_SHA384
Secure Renegotiation IS supported
hello world!
在客户端显示结果如下:
google@ubuntu1404:~/workspace/test/client$ openssl s_client -connect localhost:2020 -cert client.crt -key client.key
CONNECTED(00000003)
Can't use SSL_get_servername
depth=0 C = 12, ST = 12, L = 12, O = 12, OU = 121, CN = 2, emailAddress = 12
verify error:num=18:self signed certificate
verify return:1
depth=0 C = 12, ST = 12, L = 12, O = 12, OU = 121, CN = 2, emailAddress = 12
verify return:1
---
Certificate chain
0 s:C = 12, ST = 12, L = 12, O = 12, OU = 121, CN = 2, emailAddress = 12
i:C = 12, ST = 12, L = 12, O = 12, OU = 121







 本文介绍了在C/S架构下使用OpenSSL进行单向和双向认证的流程,包括私钥和证书的生成,以及测试过程。在双向认证中,通过调整私钥长度解决遇到的问题,最终实现成功通信。
本文介绍了在C/S架构下使用OpenSSL进行单向和双向认证的流程,包括私钥和证书的生成,以及测试过程。在双向认证中,通过调整私钥长度解决遇到的问题,最终实现成功通信。
 最低0.47元/天 解锁文章
最低0.47元/天 解锁文章

















 1193
1193

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








