CRYPTO
Numbers Game
题目不难,没搞出来很难受呜呜呜
math
题目信息
from Crypto.Util.number import *
from secret import flag,a,b
from random import shuffle
D = 0x1337
assert a**2 - D*b**2 == 1
m = bytes_to_long(flag)
p = getPrime(512)
x = (a * m + b) % p
y=bin(x)[2:]
c=[y[i:i+85] for i in range(0,len(y),85)]
shuffle(c)
print(p)
print(c)
# p=11199186558148426014734492874345932099384932524559726349180064588241518696390926354448476750322781683505497782040786332571272422812867731614415519029276349
# c=['0010101111100011101101011111111001011000100110001001000000010001111011110101110011111', '0011010010010010110010011011001100110001100010101110001010001101110001100000111011010', '0110101101011101110000100001000000010001110110001010000000010110010101100100101110000', '0100111001011010000101100111100110101100011100100111011000110001111101000110110101101', '1100100110011101010011011111000101011011010000101100011001110100101000101101111110100', '1110111110001110000101100000000100111010110000001111010001101001100001010110101010001']解题步骤
D = 0x1337 a**2 - D*b**2 == 1为Pell方程
网站在线(http://www.numbertheory.org/php/pell.html)解一下,得到方程a,b的最小整数解
a = 1809338099956399320,b = 25797719546469589
from Crypto.Util.number import *
from itertools import permutations
D = 0x1337
a = [1809338099956399320]
b = [25797719546469589]
for i in range(20):
a, b = a + [a[-1] * a[0] + D * b[-1] * b[0]], b + [a[-1] * b[0] + b[-1] * a[0]]
p = 11199186558148426014734492874345932099384932524559726349180064588241518696390926354448476750322781683505497782040786332571272422812867731614415519029276349
c = ['0010101111100011101101011111111001011000100110001001000000010001111011110101110011111', '0011010010010010110010011011001100110001100010101110001010001101110001100000111011010', '0110101101011101110000100001000000010001110110001010000000010110010101100100101110000', '0100111001011010000101100111100110101100011100100111011000110001111101000110110101101', '1100100110011101010011011111000101011011010000101100011001110100101000101101111110100', '1110111110001110000101100000000100111010110000001111010001101001100001010110101010001']
res = [int(''.join(res), 2) for res in permutations(c)]
for i in range(len(a)):
ai, bi = a[i], b[i]
for c in res:
m = (c - bi) * inverse(ai, p) % p
flag = long_to_bytes(m)
if b'flag' in flag:
print(flag)
#b'flag{5b80aaa2-2bb2-0ef1-4aa0-a5a9387239d5}'flag{5b80aaa2-2bb2-0ef1-4aa0-a5a9387239d5}
REVERSE
babyre
jadx打开在MainActivity中发现判断逻辑

查看check函数
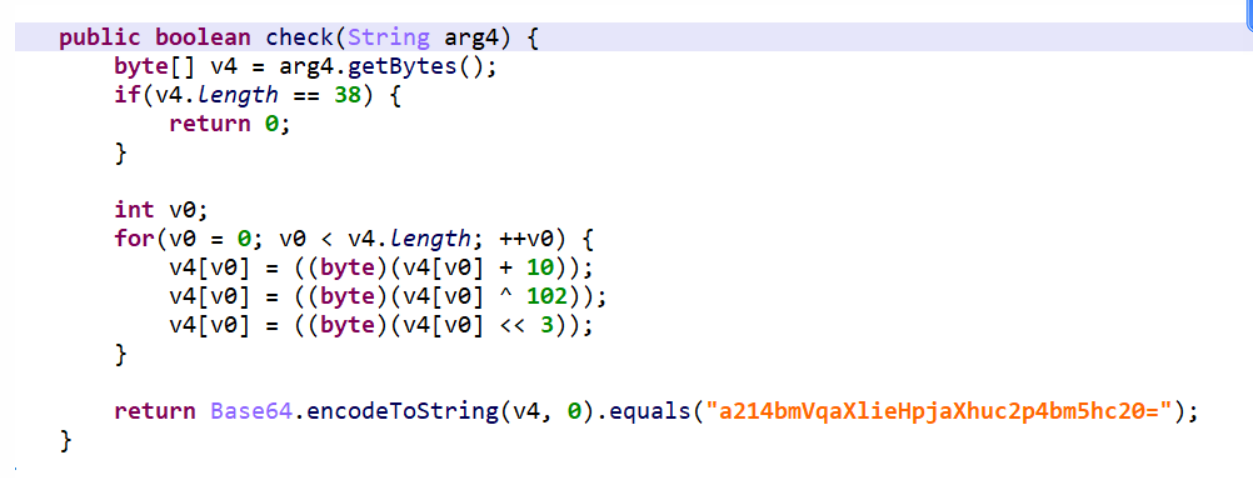
因为看到了check函数,根据逻辑去解发现解不出来
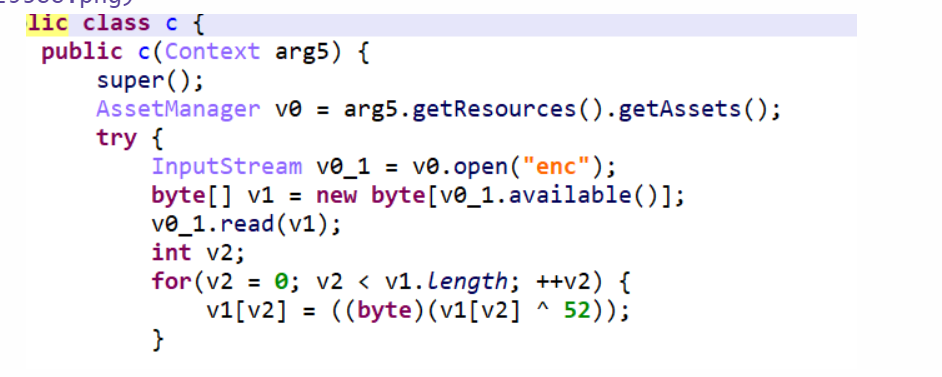
看到了c这个类中对enc这个文件进行了异或。将apk解压发现assets文件夹下有enc这个文件。按逻辑复原数据。
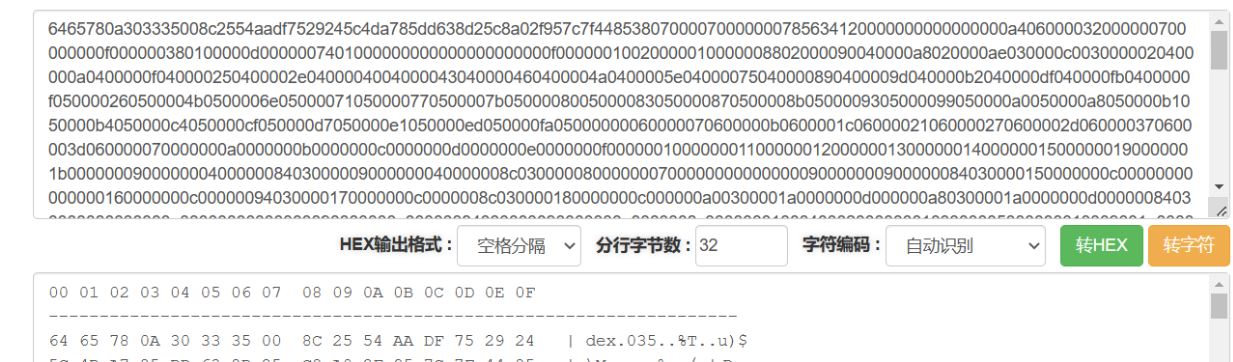
发现这是一个dex文件,接着用jadx打开
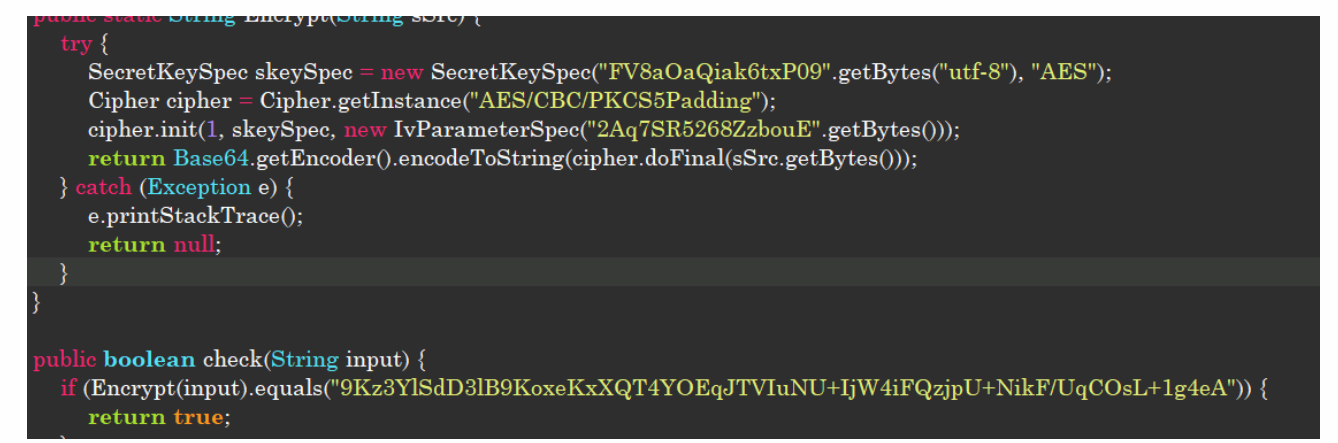
发现aes加密,网站直接解
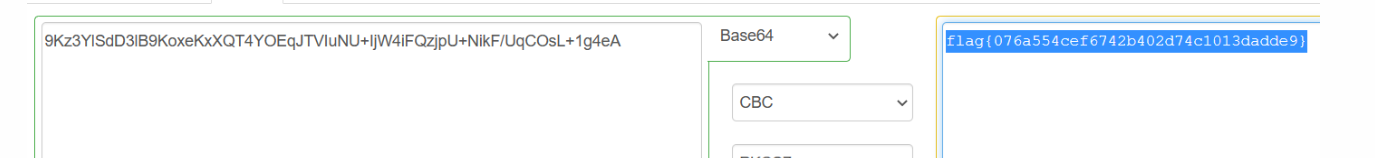
flag{076a554cef6742b402d74c1013dadde9}
MISC
sound from somewhere
一眼顶针为SSTV 使用MSSTV转换

flag{OuTer_Wilds}





 文章是一篇关于解决加密挑战的描述,涉及到数学中的Pell方程求解和加密解密过程。作者首先使用在线工具找到Pell方程的解,然后利用这些解进行加密数的计算。解密过程中,通过所有可能的字符串排列组合尝试恢复原始数据,最终成功获取到flag。
文章是一篇关于解决加密挑战的描述,涉及到数学中的Pell方程求解和加密解密过程。作者首先使用在线工具找到Pell方程的解,然后利用这些解进行加密数的计算。解密过程中,通过所有可能的字符串排列组合尝试恢复原始数据,最终成功获取到flag。
















 12万+
12万+

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








