根据Apache Tomcat官方安全报告,Apache Tomcat的多个版本存在因为内存泄漏而导致的拒绝服务的漏洞(CVE编号:CVE-2021-42340)。
受影响的各个大版本:
8.5.xx 版本: 8.5.60 到 8.5.71(8.5.72 版本修复)
9.0.xx 版本:9.0.40 到 9.0.53(9.0.54 版本修复)
10.0.xx 版本: 10.0.0-M10 到 10.0.11(10.0.12 版本修复)
建议升级到以下对应大版本的最新版本(需要考虑JDK与Tomcat的版本兼容性关系):
8.5.73 、9.0.56、10.0.14
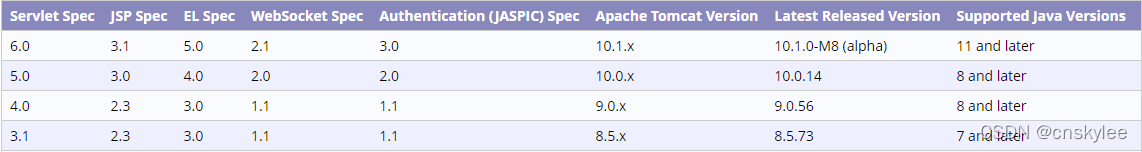
附1:官方对于此漏洞的说明
Important: Denial of Service CVE-2021-42340
The fix for bug 63362 introduced a memory leak. The object introduced to collect metrics for HTTP upgrade connections was not released for WebSocket connections once the WebSocket connection was closed. This created a memory leak that, over time, could lead to a denial of service via an OutOfMemoryError.
The memory leak was reported publicly via the users mailing list on 23 September 2021. The security implications were identified by the Tomcat Security team the same day. The issue was made public on 14 October 2021.
附2:官方对应的安全公告页面
https://tomcat.apache.org/security-8.html#Fixed_in_Apache_Tomcat_8.5.72
https://tomcat.apache.org/security-9.html#Fixed_in_Apache_Tomcat_9.0.54
https://tomcat.apache.org/security-10.html#Fixed_in_Apache_Tomcat_10.0.12





 Apache Tomcat 的 8.5, 9.0 和 10.0 大版本存在因内存泄漏导致的拒绝服务漏洞(CVE-2021-42340)。该漏洞在指定版本的 WebSocket 连接关闭后未释放内存,随着时间推移可能引发 OutOfMemoryError,从而造成 DoS 攻击。官方已发布修复版本:8.5.73, 9.0.56 和 10.0.14,建议用户升级至这些版本以解决安全问题。
Apache Tomcat 的 8.5, 9.0 和 10.0 大版本存在因内存泄漏导致的拒绝服务漏洞(CVE-2021-42340)。该漏洞在指定版本的 WebSocket 连接关闭后未释放内存,随着时间推移可能引发 OutOfMemoryError,从而造成 DoS 攻击。官方已发布修复版本:8.5.73, 9.0.56 和 10.0.14,建议用户升级至这些版本以解决安全问题。

















 1108
1108

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










