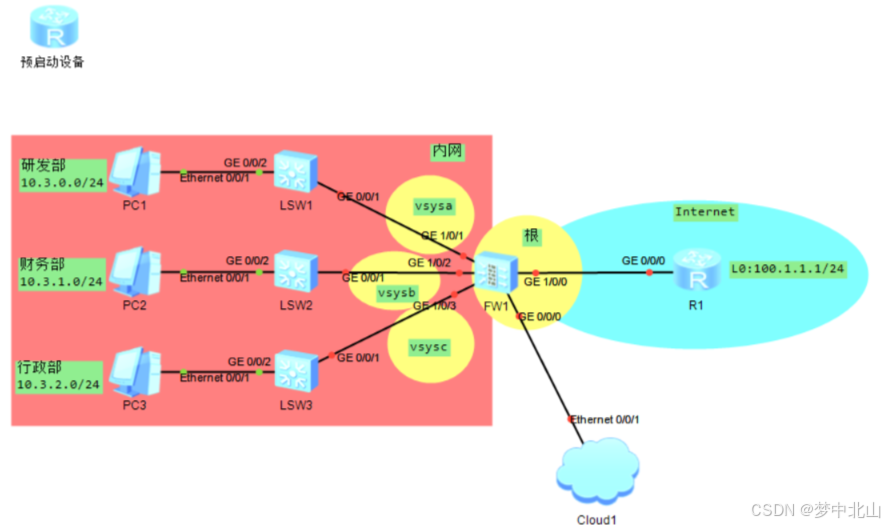
拓扑图
安全策略要求:
1 、只存在一个公网 IP 地址,公司内网所有部门都需要借用同一个接口访问外网
2 、财务部禁止访问 Internet ,研发部门只有部分员工可以访问 Internet ,行政部门全部可以访问互联网
3 、为三个部门的虚拟系统分配相同的资源
需求分析
1 、由根系统管理员创建虚拟系统 abc 并且为其分配资源以及配置管理员
2 、根系统管理员为内网用户创建安全策略和 NAT 策略
3 、由 abc 三个虚拟系统各自完成 IP 、路由、安全策略配置
配置信息
1、启动虚拟系统
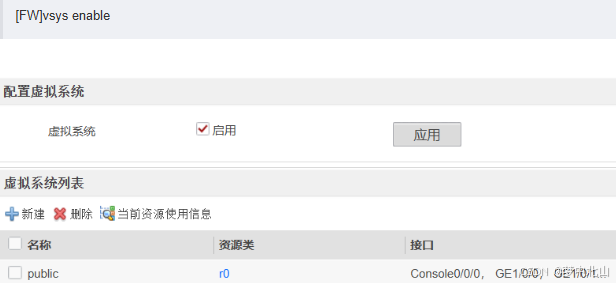
2、配置资源类
[FW]resource-class r1
[FW-resource-class-r1]resource-item-limit session reserved-number 500 maximum 1000
[FW-resource-class-r1]resource-item-limit bandwidth 2 outbound
[FW-resource-class-r1]resource-item-limit user reserved-number 100
[FW-resource-class-r1]resource-item-limit policy reserved-number 200
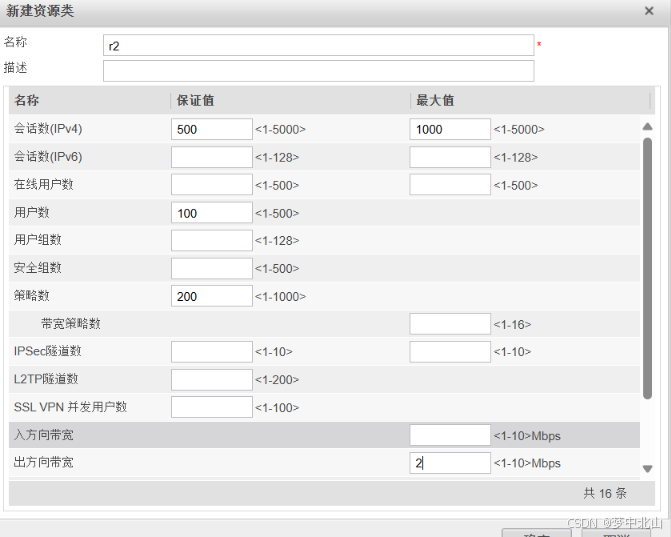
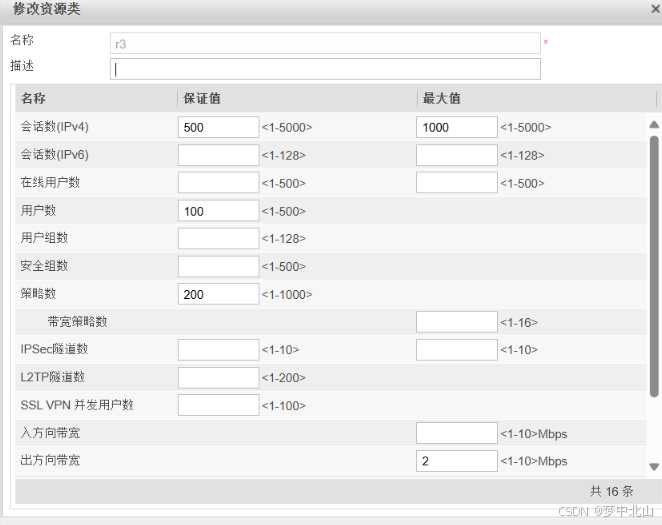
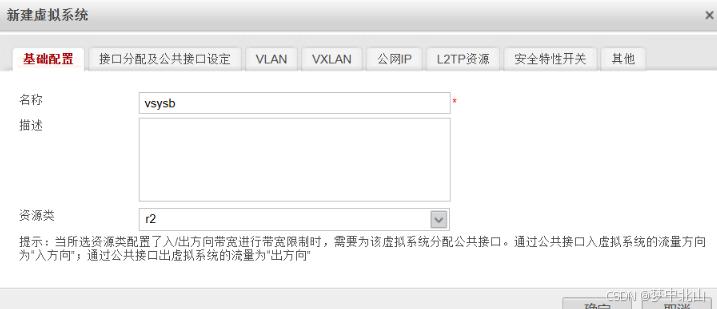
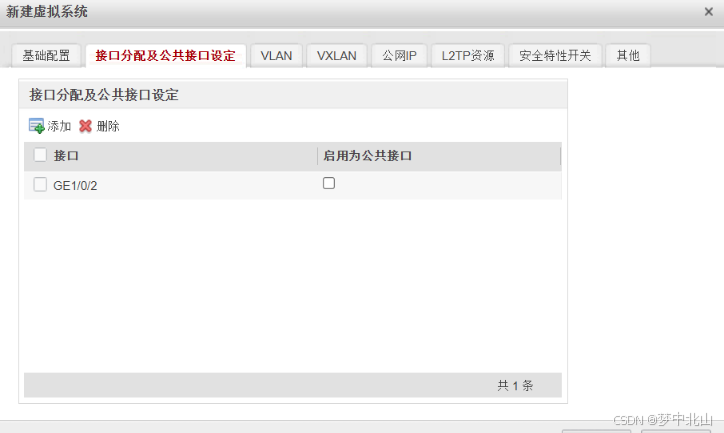
3、创建虚拟系统
[FW]vsys name vsysa
[FW-vsys-vsysa]assign resource-class r1
[FW-vsys-vsysa]assign interface GigabitEthernet 1/0/1
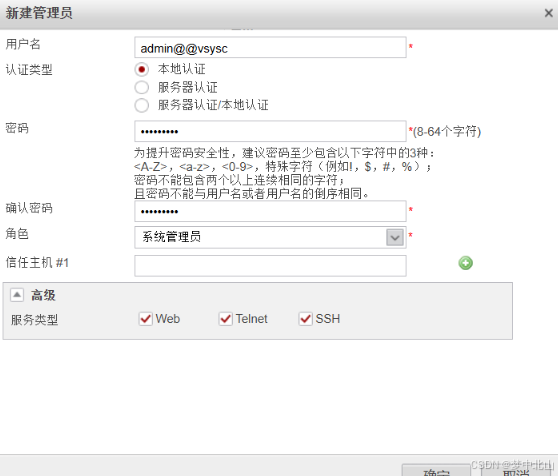
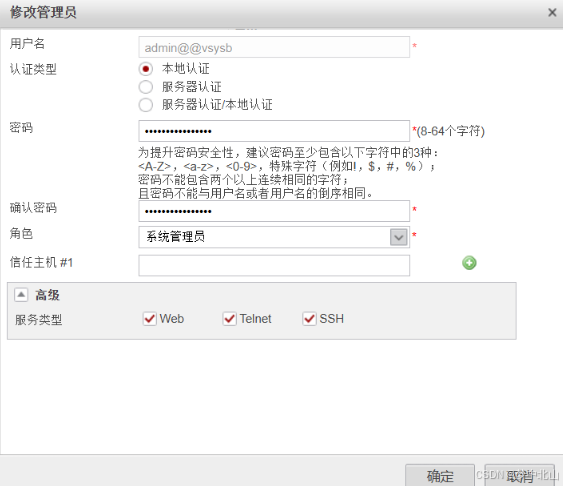
4、管理员配置
[FW]switch vsys vsysa
[FW-vsysa]aaa[FW-vsysa-aaa]manager-user admin@@vsysa
[FW-vsysa-aaa-manager-user-admin@@vsysa]password
[FW-vsysa-aaa-manager-user-admin@@vsysa]level 15
[FW-vsysa-aaa-manager-user-admin@@vsysa]service-type web telnet ssh
[FW-vsysa-aaa-manager-user-admin@@vsysa]quit
[FW-vsysa-aaa]bind manager-user admin@@vsysa role system-admin
5、根系统配置
[FW]ip route-static 10.3.1.0 24 vpn-instance vsysb
[FW]ip route-static vpn-instance vsysa 10.3.1.0 24 vpn-instance vsysb
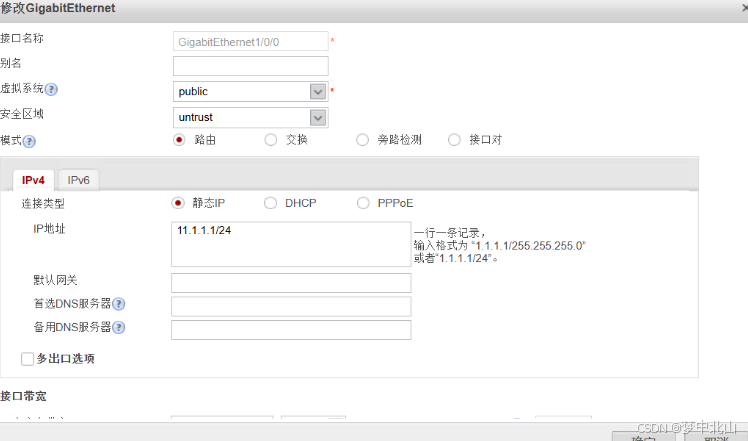
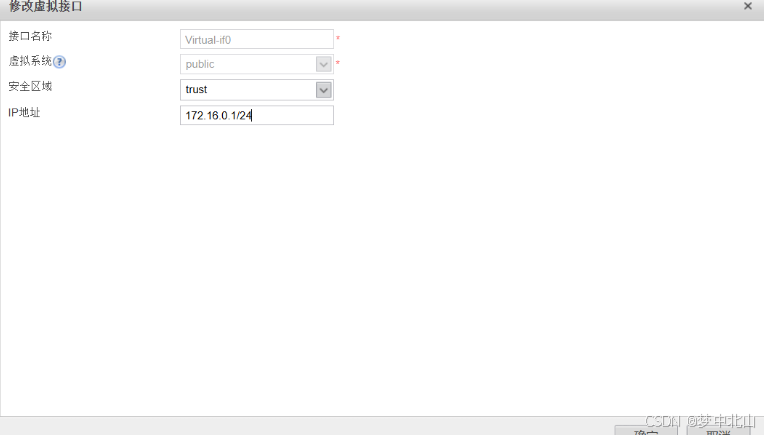
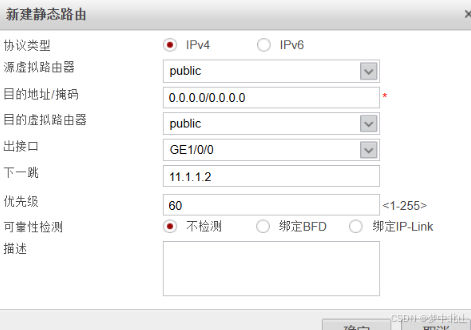
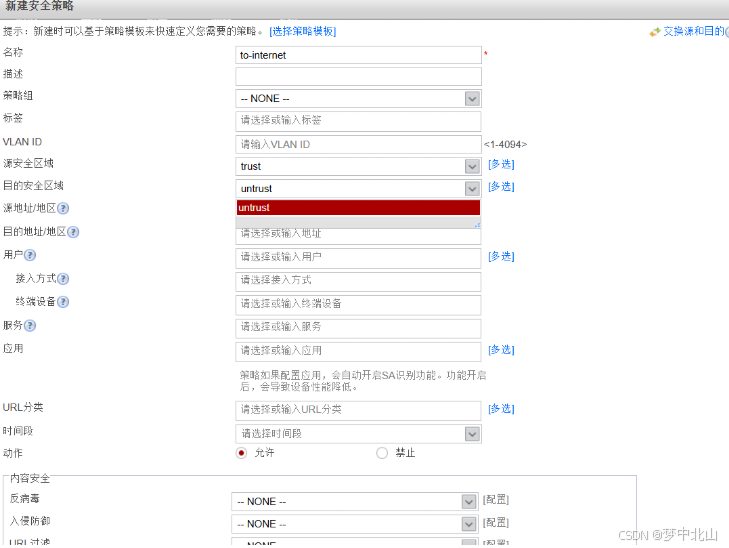
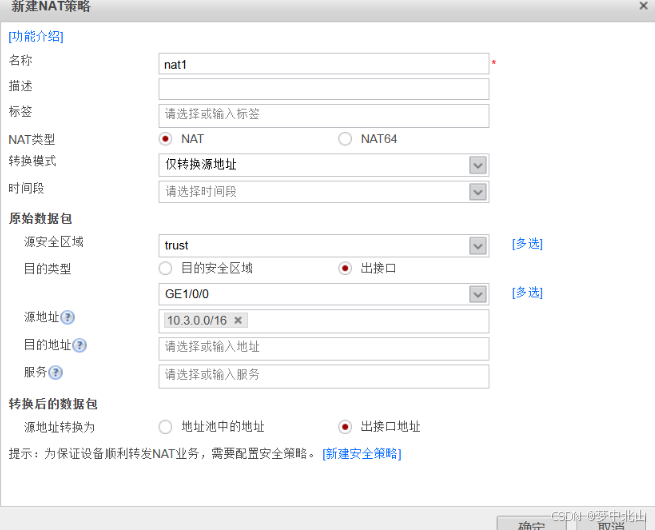
6、vsysa配置
[FW-vsysa]interface GigabitEthernet 1/0/1
[FW-vsysa-GigabitEthernet1/0/1]ip address 10.3.0.254 24
[FW-vsysa]interface Virtual-if 1
[FW-vsysa-Virtual-if1]ip address 172.16.1.1 24
[FW-vsysa]firewall zone trust
[FW-vsysa-zone-trust]add interface GigabitEthernet 1/0/1
[FW-vsysa]firewall zone untrust
[FW-vsysa-zone-untrust]add interface Virtual-if 1
[FW-vsysa]ip route-static 0.0.0.0 0 public
[FW-vsysa]ip address-set ip_add01 type object
[FW-vsysa-object-address-set-ip_add01]address range 10.3.0.1 10.3.0.10
[FW-vsysa]security-policy
[FW-vsysa-policy-security]rule name to_internet
[FW-vsysa-policy-security-rule-to_internet]source-zone trust
[FW-vsysa-policy-security-rule-to_internet]destination-zone untrust
[FW-vsysa-policy-security-rule-to_internet]source-zone
[FW-vsysa-policy-security-rule-to_internet]source-address address-set ip_add01
[FW-vsysa-policy-security-rule-to_internet]action permit
[FW-vsysa]sec
[FW-vsysa-policy-security]rule name to_vsysb
[FW-vsysa-policy-security-rule-to_vsysb]source-zone trust
[FW-vsysa-policy-security-rule-to_vsysb]destination-zone untrust
[FW-vsysa-policy-security-rule-to_vsysb]source-address 10.3.0.0 24
[FW-vsysa-policy-security-rule-to_vsysb]destination-address 10.3.1.0 24
[FW-vsysa-policy-security-rule-to_vsysb]action permit
[FW-vsysa-policy-security]rule move to_vsysb before to_internet
7、vsysb配置
[FW]switch vsys vsysb
[FW-vsysb]interface Virtual-if2
[FW-vsysb-Virtual-if2]ip address 172.16.2.1 24
[FW-vsysb]interface GigabitEthernet 1/0/2
[FW-vsysb-GigabitEthernet1/0/2]ip address 10.3.1.254
[FW-vsysb]firewall zone trust
[FW-vsysb-zone-trust]add interface GigabitEthernet 1/0/2
[FW-vsysb]firewall zone untrust
[FW-vsysb-zone-untrust]add interface Virtual-if 2
[FW-vsysb]ip route-static 0.0.0.0 0 public
[FW-vsysb]security-policy
[FW-vsysb-policy-security]rule name vsysa_to
[FW-vsysb-policy-security-rule-vsysa_to]source-zone untrust
[FW-vsysb-policy-security-rule-vsysa_to]destination-zone trust
[FW-vsysb-policy-security-rule-vsysa_to]source-address 10.3.0.0 24
[FW-vsysb-policy-security-rule-vsysa_to]destination-address 10.3.1.0 24
[FW-vsysb-policy-security-rule-vsysa_to]action permit
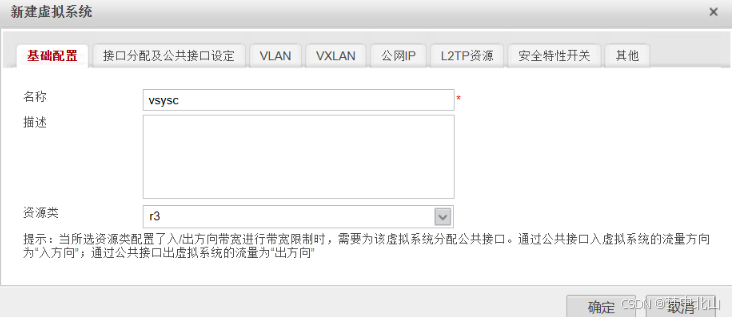
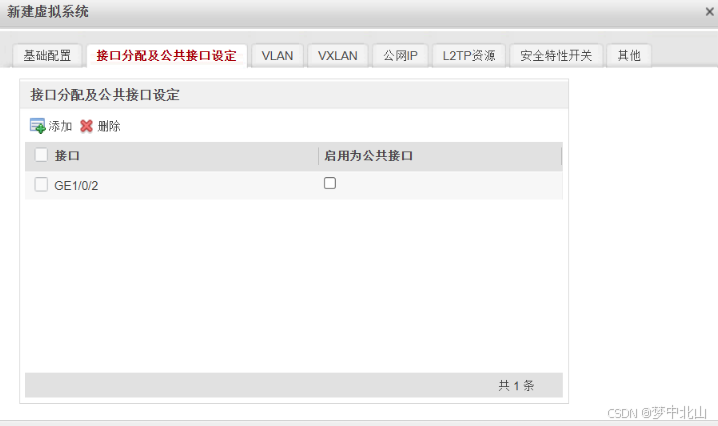
8、vsysc配置
[FW]switch vsys vsysc
[FW-vsysc]interface GigabitEthernet 1/0/3
[FW-vsysc-GigabitEthernet1/0/3]ip address 10.3.2.254 24
[FW-vsysc]interface Virtual-if 3
[FW-vsysc-Virtual-if3]ip address 172.16.3.1 24
[FW-vsysc]firewall zone trust
[FW-vsysc-zone-trust]add interface GigabitEthernet 1/0/3
[FW-vsysc]firewall zone untrust
[FW-vsysc-zone-untrust]add interface Virtual-if 3
[FW-vsysc]ip route-static 0.0.0.0 0 public
[FW-vsysc]security-policy
[FW-vsysc-policy-security]rule name to_internet
[FW-vsysc-policy-security-rule-to_internet]source-zone trust
[FW-vsysc-policy-security-rule-to_internet]destination-zone untrust
[FW-vsysc-policy-security-rule-to_internet]source-address 10.3.2.0 24
[FW-vsysc-policy-security-rule-to_internet]action permit
测试
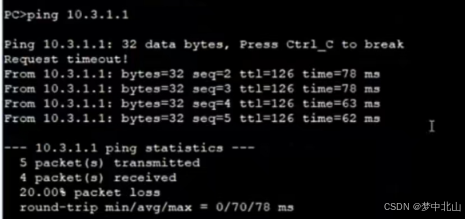
研发部门只有部分员工可以访问Internet
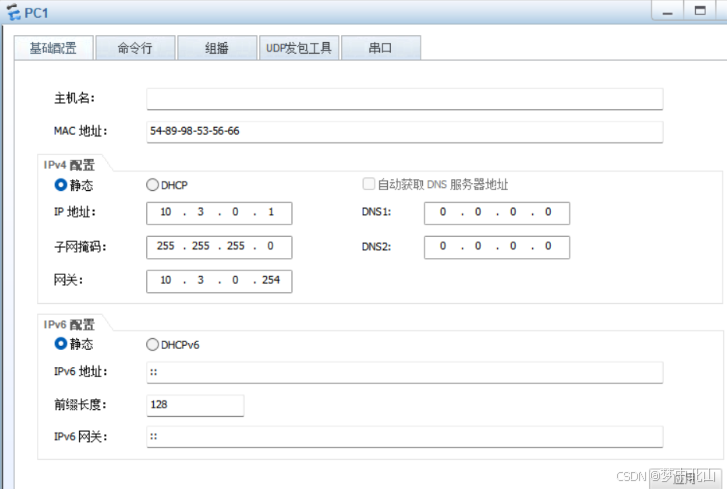
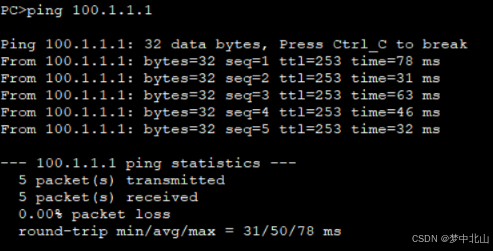
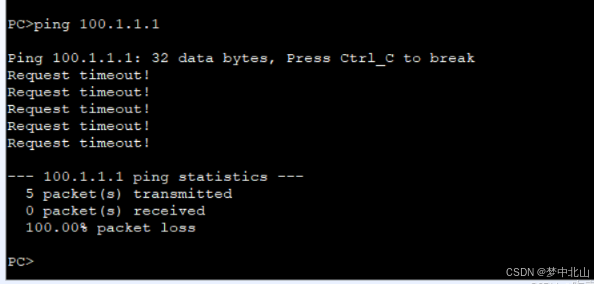
财务部禁止访问Internet
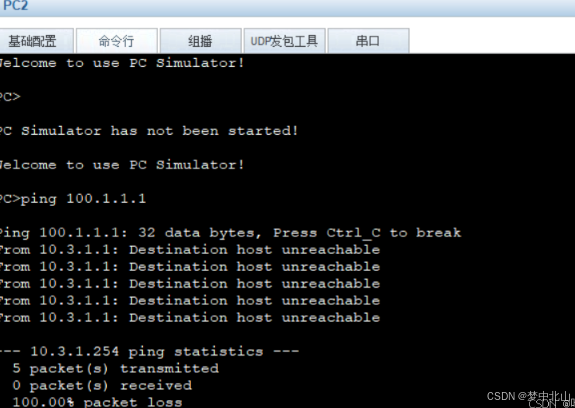
行政部门全部可以访问互联网
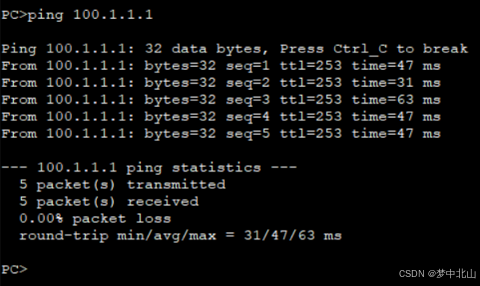
内网互通























 625
625

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








