NSSCTF Crypto 探索
常用编码
前两个题ID303,287在入门时做过了,详见另一篇wp链接
[AFCTF 2018]BASE ID:463
打开文件直接麻了,如果人工解码,估计黄花菜都要凉了,这就需要用到拥有强大数据处理能力的python了,下面是我借鉴得几个大佬的脚本。
首先是大佬xenny的,NSSCTF这个题的wp也有
import re, base64
s = open('/Users/x3nny/Downloads/flag_encode.txt', 'rb').read()
base16_dic = r'^[A-F0-9=]*$'
base32_dic = r'^[A-Z2-7=]*$'
base64_dic = r'^[A-Za-z0-9/+=]*$'
n= 0
while True:
n += 1
t = s.decode()
if '{' in t:
print(t)
break
elif re.match(base16_dic, t):
s = base64.b16decode(s)
print(str(n) + ' base16')
elif re.match(base32_dic, t):
s = base64.b32decode(s)
print(str(n) + ' base32')
elif re.match(base64_dic, t):
s = base64.b64decode(s)
print(str(n) + ' base64')

然后是看到另一个博主的脚本链接
import base64
with open(r'D:/谷歌下载/flag_encode.txt', 'r', encoding='utf-8') as f:
for a in f:
while 1:
try:
a = base64.b64decode(a).decode("utf-8")
except:
pass
try:
a = base64.b32decode(a).decode("utf-8")
except:
pass
try:
a = base64.b16decode(a).decode('utf-8')
except:
pass
if "{" in a:
print(a)
break
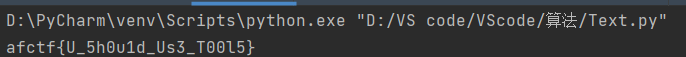
得flag: afctf{U_5h0u1d_Us3_T00l5}
[BJDCTF 2020]base?? ID:691
打开文件一看有个字典,还有密文,先试一试密文能不能直接解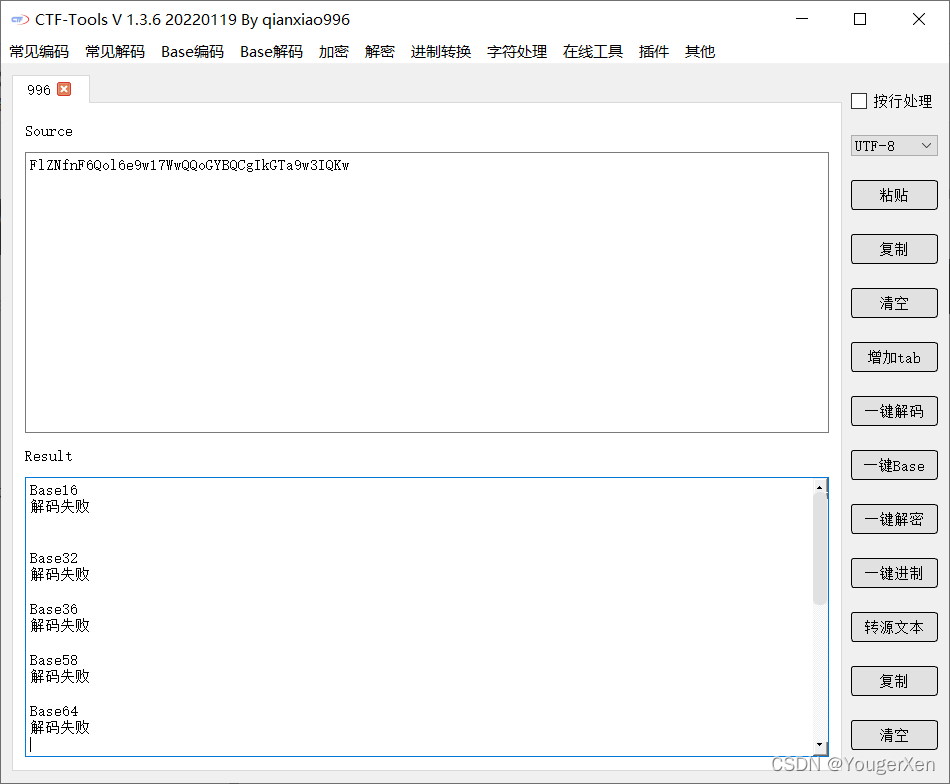
果然没结果,仔细查看字典再对比base64编码表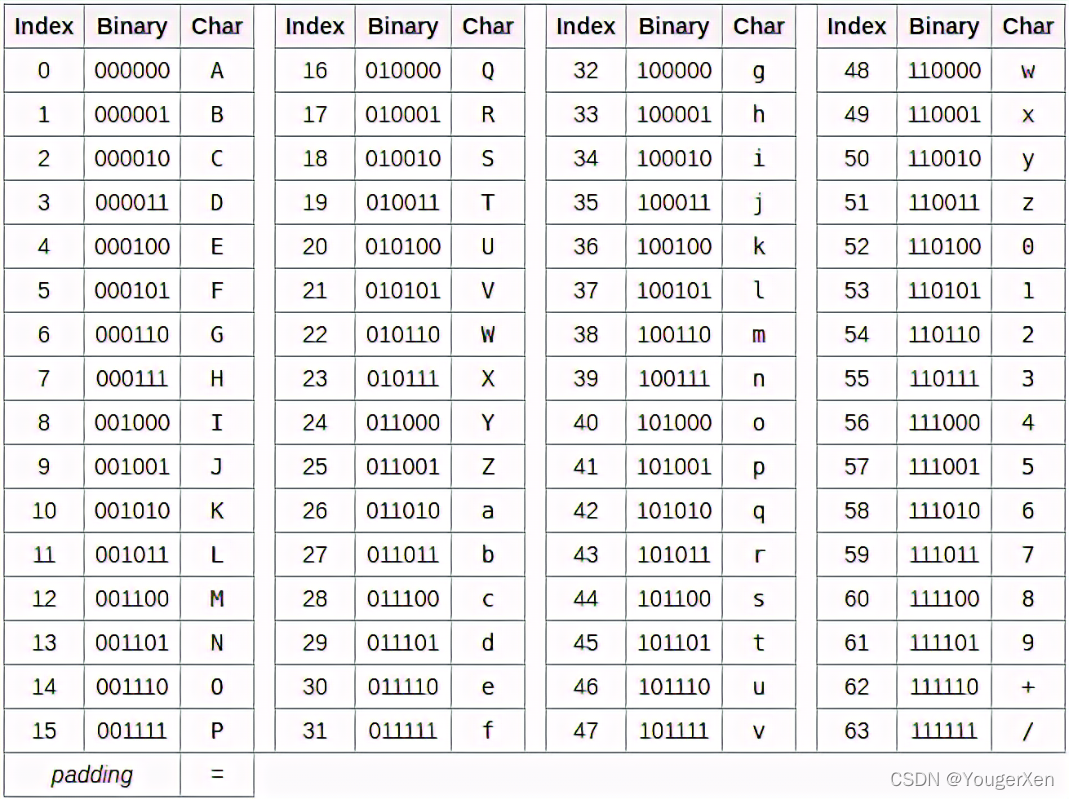
发现字典里面多了个等号,说明很有可能是密文经过字典里的编码出来的。
直接上脚本
#Jaeger
import base64
dict={0: 'J', 1: 'K', 2: 'L', 3: 'M', 4: 'N', 5: 'O', 6: 'x', 7: 'y', 8: 'U', 9: 'V', 10: 'z', 11: 'A', 12: 'B', 13: 'C', 14: 'D', 15: 'E', 16: 'F', 17: 'G', 18: 'H', 19: '7', 20: '8', 21: '9', 22: 'P', 23: 'Q', 24: 'I', 25: 'a', 26: 'b', 27: 'c', 28: 'd', 29: 'e', 30: 'f', 31: 'g', 32: 'h', 33: 'i', 34: 'j', 35: 'k', 36: 'l', 37: 'm', 38: 'W', 39: 'X', 40: 'Y', 41: 'Z', 42: '0', 43: '1', 44: '2', 45: '3', 46: '4', 47: '5', 48: '6', 49: 'R', 50: 'S', 51: 'T', 52: 'n', 53: 'o', 54: 'p', 55: 'q', 56: 'r', 57: 's', 58: 't', 59: 'u', 60: 'v', 61: 'w', 62: '+', 63: '/', 64: '='}
base64code=['A', 'B', 'C', 'D', 'E', 'F', 'G', 'H', 'I', 'J', 'K', 'L', 'M', 'N', 'O', 'P','Q', 'R', 'S', 'T', 'U', 'V', 'W', 'X', 'Y', 'Z', 'a', 'b', 'c', 'd', 'e', 'f','g', 'h', 'i', 'j', 'k', 'l', 'm', 'n', 'o', 'p', 'q', 'r', 's', 't', 'u', 'v','w', 'x', 'y', 'z', '0', '1', '2', '3', '4', '5', '6', '7', '8', '9', '+', '/']
str = 'FlZNfnF6Qol6e9w17WwQQoGYBQCgIkGTa9w3IQKw'
m=''
for i in str:
for j in range(64):
if i == dict[j]:
m+=base64code[j]
print(base64.b64decode(m))
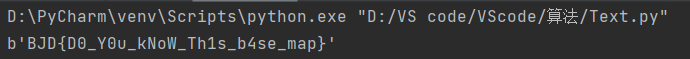
BJD{D0_Y0u_kNoW_Th1s_b4se_map}
[安洵杯 2019]JustBase ID:723
VGhlIGdlb@xvZ#kgb@YgdGhlIEVhcnRoJ#Mgc#VyZmFjZSBpcyBkb@!pbmF)ZWQgYnkgdGhlIHBhcnRpY#VsYXIgcHJvcGVydGllcyBvZiB#YXRlci$gUHJlc@VudCBvbiBFYXJ)aCBpbiBzb@xpZCwgbGlxdWlkLCBhbmQgZ@FzZW(!cyBzdGF)ZXMsIHdhdGVyIGlzIGV$Y@VwdGlvbmFsbHkgcmVhY#RpdmUuIEl)IGRpc#NvbHZlcywgdHJhbnNwb#J)cywgYW%kIHByZWNpcGl)YXRlcyBtYW%%IGNoZW!pY@FsIGNvbXBvdW%kcyBhbmQgaXMgY@(uc#RhbnRseSBtb@RpZnlpbmcgdGhlIGZhY@Ugb@YgdGhlIEVhcnRoLiBFdmFwb#JhdGVkIGZyb@)gdGhlIG(jZWFucywgd@F)ZXIgdmFwb#IgZm(ybXMgY@xvdWRzLCBzb@!lIG(mIHdoaWNoIGFyZSB)cmFuc#BvcnRlZCBieSB#aW%kIG(@ZXIgdGhlIGNvbnRpbmVudHMuIENvbmRlbnNhdGlvbiBmcm(tIHRoZSBjbG(!ZHMgcHJvdmlkZXMgdGhlIGVzc@VudGlhbCBhZ@VudCBvZiBjb@%)aW%lbnRhbCBlcm(zaW(uOiByYWluLlRoZSByYXRlIGF)IHdoaWNoIGEgbW(sZWN!bGUgb@Ygd@F)ZXIgcGFzc@VzIHRob#VnaCB)aGUgY#ljbGUgaXMgbm()IHJhbmRvbQpBbmQgdGhlIGZsYWcgaXM^IENURnsyMi!RV)VSVFlVSU*tUExLSkhHRkRTLUFaWENWQk%NfQ==
题目说只有base,姑且相信一次,显而易见的是这里面有很多不属于base的字符’!@#$%^&*()',然后发现刚好对应键盘上的190,那应该是字符替换
上脚本
import base64
m = 'VGhlIGdlb@xvZ#kgb@YgdGhlIEVhcnRoJ#Mgc#VyZmFjZSBpcyBkb@!pbmF)ZWQgYnkgdGhlIHBhcnRpY#VsYXIgcHJvcGVydGllcyBvZiB#YXRlci$gUHJlc@VudCBvbiBFYXJ)aCBpbiBzb@xpZCwgbGlxdWlkLCBhbmQgZ@FzZW(!cyBzdGF)ZXMsIHdhdGVyIGlzIGV$Y@VwdGlvbmFsbHkgcmVhY#RpdmUuIEl)IGRpc#NvbHZlcywgdHJhbnNwb#J)cywgYW%kIHByZWNpcGl)YXRlcyBtYW%%IGNoZW!pY@FsIGNvbXBvdW%kcyBhbmQgaXMgY@(uc#RhbnRseSBtb@RpZnlpbmcgdGhlIGZhY@Ugb@YgdGhlIEVhcnRoLiBFdmFwb#JhdGVkIGZyb@)gdGhlIG(jZWFucywgd@F)ZXIgdmFwb#IgZm(ybXMgY@xvdWRzLCBzb@!lIG(mIHdoaWNoIGFyZSB)cmFuc#BvcnRlZCBieSB#aW%kIG(@ZXIgdGhlIGNvbnRpbmVudHMuIENvbmRlbnNhdGlvbiBmcm(tIHRoZSBjbG(!ZHMgcHJvdmlkZXMgdGhlIGVzc@VudGlhbCBhZ@VudCBvZiBjb@%)aW%lbnRhbCBlcm(zaW(uOiByYWluLlRoZSByYXRlIGF)IHdoaWNoIGEgbW(sZWN!bGUgb@Ygd@F)ZXIgcGFzc@VzIHRob#VnaCB)aGUgY#ljbGUgaXMgbm()IHJhbmRvbQpBbmQgdGhlIGZsYWcgaXM^IENURnsyMi!RV)VSVFlVSU*tUExLSkhHRkRTLUFaWENWQk%NfQ=='
c = ')!@#$%^&*('
for i in m:
for j in range(10):
if i == c[j]:
m = m.replace(i,str(j))
print(m)
print(base64.b64decode(m))
得到一段自然科学和flag
The geology of the Earth's surface is dominated by the particular properties of water. Present on Earth in solid, liquid, and gaseous states, water is exceptionally reactive. It dissolves, transports, and precipitates many chemical compounds and is constantly modifying the face of the Earth. Evaporated from the oceans, water vapor forms clouds, some of which are transported by wind over the continents. Condensation from the clouds provides the essential agent of continental erosion: rain.The rate at which a molecule of water passes though the cycle is not random
And the flag is: CTF{22-QWERTYUIO-PLKJHGFDS-AZXCVBNM}





 这篇博客介绍了如何使用Python进行编码解码,包括base16、base32和base64,以及在CTF挑战中遇到的字符替换加密。作者分享了解密过程,通过脚本展示了如何从加密文本中提取flag,并提供了多个CTF挑战的解题思路和解密代码,涉及到的信息隐藏技术包括自定义base映射。
这篇博客介绍了如何使用Python进行编码解码,包括base16、base32和base64,以及在CTF挑战中遇到的字符替换加密。作者分享了解密过程,通过脚本展示了如何从加密文本中提取flag,并提供了多个CTF挑战的解题思路和解密代码,涉及到的信息隐藏技术包括自定义base映射。

















 1541
1541

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








