配置相关接口IP地址及区域
[FW1-GigabitEthernet1/0/0]ip add 10.1.1.1 24
[FW1-GigabitEthernet1/0/0]service-manage ping permit
[FW1-GigabitEthernet1/0/6]ip add 20.1.1.1 24
[FW1-GigabitEthernet1/0/6]service-manage ping permit
[FW1]firewall zone trust
[FW1-zone-trust]add interface GigabitEthernet 1/0/0
[FW1]firewall zone untrust
[FW1-zone-untrust]add interface GigabitEthernet 1/0/6
[FW2-GigabitEthernet1/0/0]ip add 10.1.2.1 24
[FW2-GigabitEthernet1/0/0]service-manage ping permit
[FW2-GigabitEthernet1/0/6]ip add 20.1.1.2 24
[FW2-GigabitEthernet1/0/6]service-manage ping permit
[FW2]firewall zone trust
[FW2-zone-trust]add interface GigabitEthernet 1/0/0
[FW2]firewall zone untrust
[FW2-zone-untrust]add interface GigabitEthernet 1/0/6
在防火墙上配置到对端的路由
[FW1]ip route-static 10.1.2.0 24 20.1.1.2
[FW2]ip route-static 10.1.1.0 24 20.1.1.1
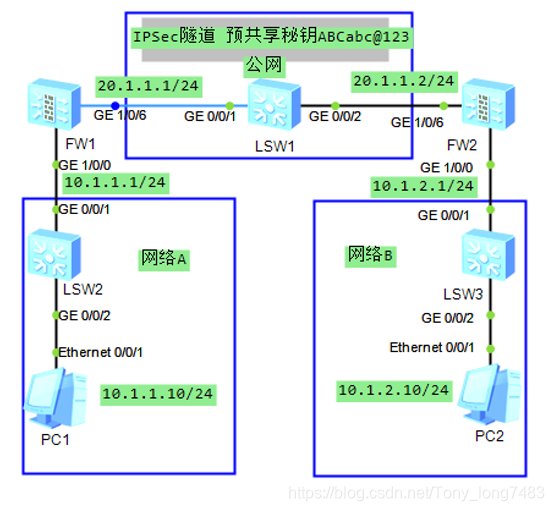
配置安全策略(配置ipsec1和ipsec2,允许网络AB间互访;配置ipsec3和ipsec4,允许IKE协商后的报文及加密后的报文通过)
[FW1]security-policy
[FW1-policy-security]rule name ipsec1
[FW1-policy-security-rule-ipsec1]source-zone trust
[FW1-policy-security-rule-ipsec1]destination-zone untrust
[FW1-policy-security-rule-ipsec1]source-address 10.1.1.0 mask 255.255.255.0
[FW1-policy-security-rule-ipsec1]destination-address 10.1.2.0 mask 255.255.255.0
[FW1-policy-security-rule-ipsec1]action permit
[FW1-policy-security]rule name ipsec2
[FW1-policy-security-rule-ipsec2]source-zone untrust
[FW1-policy-security-rule-ipsec2]destination-zone trust
[FW1-policy-security-rule-ipsec2]source-address 10.1.2.0 mask 255.255.255.0
[FW1-policy-security-rule-ipsec2]destination-address 10.1.1.0 mask 255.255.255.0
[FW1-policy-security-rule-ipsec2]action permit
[FW1-policy-security]rule name ipsec3
[FW1-policy-security-rule-ipsec3]source-zone local
[FW1-policy-security-rule-ipsec3]destination-zone untrust
[FW1-policy-security-rule-ipsec3]source-address 20.1.1.1 mask 255.255.255.255
[FW1-policy-security-rule-ipsec3]destination-address 20.1.1.2 mask 255.255.255.255
[FW1-policy-security-rule-ipsec3]action permit
[FW1-policy-security]rule name ipsec4
[FW1-policy-security-rule-ipsec4]source-zone untrust
[FW1-policy-security-rule-ipsec4]destination-zone local
[FW1-policy-security-rule-ipsec4]source-address 20.1.1.2 mask 255.255.255.255
[FW1-policy-security-rule-ipsec4]destination-address 20.1.1.1 mask 255.255.255.255
[FW1-policy-security-rule-ipsec4]action permit
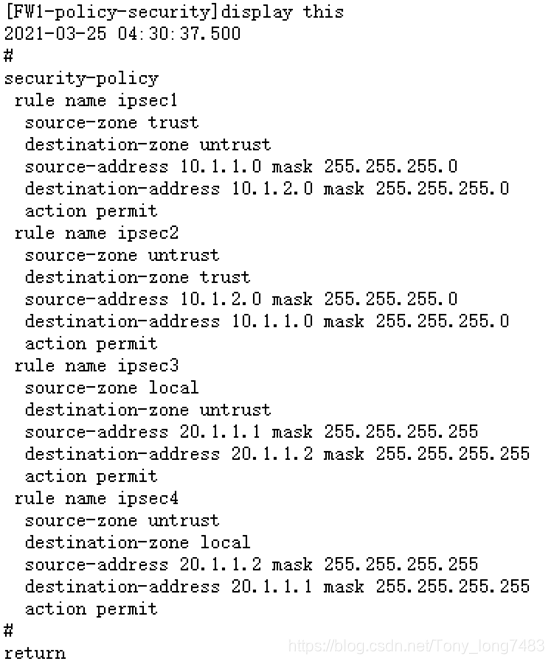
[FW2]security-policy
[FW2-policy-security]rule name ipsec1
[FW2-policy-security-rule-ipsec1]source-zone trust
[FW2-policy-security-rule-ipsec1]destination-zone untrust
[FW2-policy-security-rule-ipsec1]source-address 10.1.2.0 mask 255.255.255.0
[FW2-policy-security-rule-ipsec1]destination-address 10.1.1.0 mask 255.255.255.0
[FW2-policy-security-rule-ipsec1]action permit
[FW2-policy-security]rule name ipsec2
[FW2-policy-security-rule-ipsec2]source-zone untrust
[FW2-policy-security-rule-ipsec2]destination-zone trust
[FW2-policy-security-rule-ipsec2]source-address 10.1.1.0 mask 255.255.255.0
[FW2-policy-security-rule-ipsec2]destination-address 10.1.2.0 mask 255.255.255.0
[FW2-policy-security-rule-ipsec2]action permit
[FW2-policy-security]rule name ipsec3
[FW2-policy-security-rule-ipsec3]source-zone local
[FW2-policy-security-rule-ipsec3]destination-zone untrust
[FW2-policy-security-rule-ipsec3]source-address 20.1.1.2 mask 255.255.255.255
[FW2-policy-security-rule-ipsec3]destination-address 20.1.1.1 mask 255.255.255.255
[FW2-policy-security-rule-ipsec3]action permit
[FW2-policy-security]rule name ipsec4
[FW2-policy-security-rule-ipsec4]source-zone untrust
[FW2-policy-security-rule-ipsec4]destination-zone local
[FW2-policy-security-rule-ipsec4]source-address 20.1.1.1 mask 255.255.255.255
[FW2-policy-security-rule-ipsec4]destination-address 20.1.1.2 mask 255.255.255.255
[FW2-policy-security-rule-ipsec4]action permit
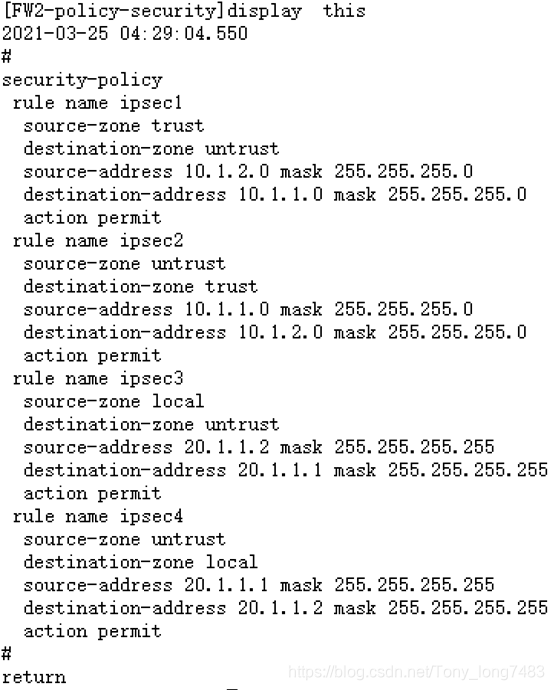
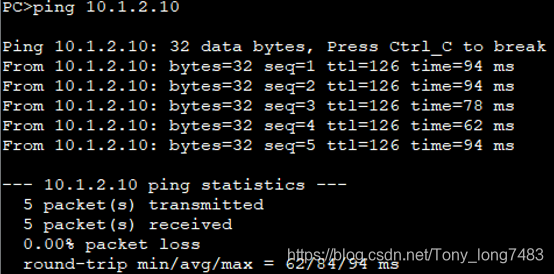
PC1和PC2已经连通
FW1和FW2已经连通
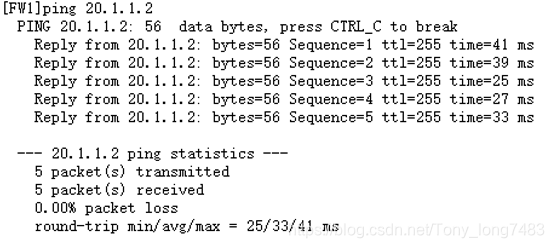
配置IPSec策略
[FW1]acl 3000
[FW1-acl-adv-3000]rule 5 permit ip source 10.1.1.0 0.0.0.255 destination 10.1.2.0 0.0.0.255 //抓取流量
[FW1]ipsec proposal propAB //配置防火墙ipsec安全提议
[FW1-ipsec-proposal-propAB]encapsulation-mode auto //使用自动模式
[FW1]ike proposal 1 //配置IKE安全提议
[FW1-ike-proposal-1]integrity-algorithm aes-xcbc-96 //ike安全提议类型为aes
[FW1]ike peer ikeAB //配置IKE对等体
[FW1-ike-peer-ikeAB]exchange-mode auto //ike对等体信息交换模式为自动模式
[FW1-ike-peer-ikeAB]pre-shared-key ABCabc@123
[FW1-ike-peer-ikeAB]ike-proposal 1
[FW1-ike-peer-ikeAB]remote-id-type ip
[FW1-ike-peer-ikeAB]remote-id 20.1.1.2
[FW1-ike-peer-ikeAB]local-id 20.1.1.1
[FW1-ike-peer-ikeAB]remote-address 20.1.1.2 //ike对端IP地址
[FW1]ipsec policy ipsecAB 1 isakmp //配置防火墙ipsec安全策略
[FW1-ipsec-policy-isakmp-ipsecAB-1]security acl 3000
[FW1-ipsec-policy-isakmp-ipsecAB-1]ike-peer ikeAB
[FW1-ipsec-policy-isakmp-ipsecAB-1]proposal propAB
[FW1-ipsec-policy-isakmp-ipsecAB-1]tunnel local applied-interface
[FW2]acl 3000
[FW2-acl-adv-3000]rule 5 permit ip source 10.1.2.0 0.0.0.255 destination 10.1.1.0 0.0.0.255
[FW2]ipsec proposal propBA
[FW2-ipsec-proposal-propBA]encapsulation-mode auto
[FW2]ike proposal 1
[FW2-ike-proposal-1]integrity-algorithm aes-xcbc-96
[FW2]ike peer ikeBA
[FW2-ike-peer-ikeBA]exchange-mode auto
[FW2-ike-peer-ikeBA]pre-shared-key ABCabc@123
[FW2-ike-peer-ikeBA]ike-proposal 1
[FW2-ike-peer-ikeBA]remote-id-type ip
[FW2-ike-peer-ikeBA]remote-id 20.1.1.1
[FW2-ike-peer-ikeBA]local-id 20.1.1.2
[FW2-ike-peer-ikeBA]remote-address 20.1.1.1
[FW2]ipsec policy ipsecBA 1 isakmp
[FW2-ipsec-policy-isakmp-ipsecBA-1]security acl 3000
[FW2-ipsec-policy-isakmp-ipsecBA-1]ike-peer ikeBA
[FW2-ipsec-policy-isakmp-ipsecBA-1]proposal propBA
[FW2-ipsec-policy-isakmp-ipsecBA-1]tunnel local applied-interface
应用IPSec策略
[FW1-GigabitEthernet1/0/6]ipsec policy ipsecAB
[FW2-GigabitEthernet1/0/6]ipsec policy ipsecBA
验证
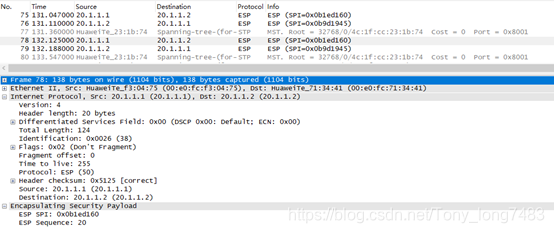
PC1 ping PC2时在FW1的G1/0/6口抓包





 本文详细介绍了如何在两台防火墙FW1和FW2上配置IP地址、区域、路由及安全策略,包括允许网络间的互访及IKE协商后的报文通过,并通过配置IPSec策略实现数据加密传输。
本文详细介绍了如何在两台防火墙FW1和FW2上配置IP地址、区域、路由及安全策略,包括允许网络间的互访及IKE协商后的报文通过,并通过配置IPSec策略实现数据加密传输。
















 7184
7184

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








