二进制文件部署k8s方式(4)
Master节点_kube-apiserver部署
下载二进制安装包
https://github.com/kubernetes/kubernetes/blob/master/CHANGELOG/CHANGELOG-1.26.md#v1183
里面能看到很多安装包,我们针对master节点只需要下载Server Binaries
各安装包对应内容分别为
Client Binaries(客户端二进制文件)
kubectl- Kubernetes 命令行工具,用于管理集群- 平台版本:Linux、Windows、macOS(amd64/arm64)
Server Binaries(服务器端二进制文件)
核心控制平面组件:
kube-apiserver- API 服务器,集群的前端入口kube-controller-manager- 运行各种控制器进程kube-scheduler- 负责调度 Pod 到节点kube-proxy- 网络代理,实现 Service 概念kubelet- 节点代理,管理 Pod 和容器- 平台:Linux(amd64/arm64)
Node Binaries(节点二进制文件)
最小化节点运行所需:
kubelet- 必须在每个节点上运行kube-proxy- 可选,但通常需要- 平台:Linux(amd64/arm64)
Container Images(容器镜像)
所有核心组件的容器化版本:
kube-apiserverkube-controller-managerkube-schedulerkube-proxy- 镜像仓库:
registry.k8s.io
Source Code(源代码)
- 完整的 Kubernetes 项目源代码
- 构建脚本和配置
- 文档和示例
下载后再上传到master节点
解压二进制包
创建k8s安装目录
master1节点执行
mkdir -p /opt/kubernetes/{bin,cfg,ssl,logs}
解压
tar zxvf kubernetes-server-linux-amd64.tar.gz
cd kubernetes/server/bin
master节点主要安装kube-apiserver、kube-scheduler和kube-controller-manager三个服务
cp kube-apiserver kube-scheduler kube-controller-manager /opt/kubernetes/bin
安装kubectl服务
cp kubectl /usr/bin/
同步到其他master节点
NODES='master2 master3'; \
for NODE in $NODES; \
do \
ssh $NODE "mkdir -p /opt/kubernetes/{bin,cfg,ssl,logs}"; \
scp kube-apiserver $NODE:/opt/kubernetes/bin;\
scp kube-scheduler $NODE:/opt/kubernetes/bin;\
scp kube-controller-manager $NODE:/opt/kubernetes/bin;\
scp kubectl $NODE:/usr/bin;\
done
kube-apiserver部署
生成ca证书
进入证书存放目录
均只在master1执行
cd /opt/kubernetes/ssl
创建CA配置文件
cat > ca-config.json << EOF
{
"signing": {
"default": {
"expiry": "876000h"
},
"profiles": {
"kubernetes": {
"usages": [
"signing",
"key encipherment",
"server auth",
"client auth"
],
"expiry": "876000h"
}
}
}
}
EOF
创建CA证书签名请求文件
cat > ca-csr.json << EOF
{
"CN": "kubernetes",
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"ST": "Beijing",
"L": "Beijing",
"O": "Kubernetes",
"OU": "Kubernetes-manual"
}
],
"ca": {
"expiry": "876000h"
}
}
EOF
以上俩文件作用在《二进制文件方式部署k8s(2)》中有所提及
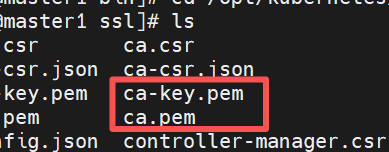
生成证书
cfssl gencert -initca ca-csr.json | cfssljson -bare ca - && ls *.pem
签发kube-apiserver证书
在master1执行
创建证书申请文件
cat > kube-apiserver-csr.json<< EOF
{
"CN": "kube-apiserver",
"hosts": [
"10.96.0.1",
"127.0.0.1",
"192.168.153.200", //这里预留一条IP为后续负载均衡做准备
"192.168.153.161",
"192.168.153.162",
"192.168.153.163",
"192.168.153.181",
"192.168.153.182",
"kubernetes",
"kubernetes.default",
"kubernetes.default.svc",
"kubernetes.default.svc.cluster",
"kubernetes.default.svc.cluster.local"
],
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"ST": "Beijing",
"L": "Beijing",
"O": "Kubernetes",
"OU": "Kubernetes-manual"
}
]
}
EOF
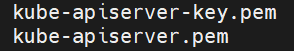
生成证书
cfssl gencert -ca=ca.pem -ca-key=ca-key.pem -config=ca-config.json -profile=kubernetes kube-apiserver-csr.json | cfssljson -bare kube-apiserver && ls kube-apiserver*pem
生成apiserver聚合证书
在master1执行
创建证书申请文件
cat > front-proxy-ca-csr.json << EOF
{
"CN": "kubernetes",
"key": {
"algo": "rsa",
"size": 2048
},
"ca": {
"expiry": "876000h"
}
}
EOF
cfssl gencert -initca front-proxy-ca-csr.json | cfssljson -bare front-proxy-ca - && ls front-proxy-ca*.pem
证书签发
cat > front-proxy-client-csr.json << EOF
{
"CN": "front-proxy-client",
"key": {
"algo": "rsa",
"size": 2048
}
}
EOF
cfssl gencert -ca=front-proxy-ca.pem -ca-key=front-proxy-ca-key.pem -config=ca-config.json -profile=kubernetes front-proxy-client-csr.json | cfssljson -bare front-proxy-client && ls front-proxy-client*pem
创建ServiceAccount Key
ServiceAccount Key(服务账户密钥) 是 Kubernetes 中用于身份验证和授权的重要凭证
openssl genrsa -out /opt/kubernetes/ssl/sa.key 2048
openssl rsa -in /opt/kubernetes/ssl/sa.key -pubout -out /opt/kubernetes/ssl/sa.pub
证书拷贝到其他节点
NODES='master2 master3 worker1 worker2'; \
for NODE in $NODES; \
do \
for FILE in ca-key.pem ca.pem front-proxy-ca-key.pem front-proxy-ca.pem front-proxy-client-key.pem front-proxy-client.pem kube-apiserver-key.pem kube-apiserver.pem sa.key sa.pub; \
do \
scp /opt/kubernetes/ssl/${FILE} $NODE:/opt/kubernetes/ssl/${FILE};\
done \
done
创建配置文件
各master节点执行
cat > /opt/kubernetes/cfg/kube-apiserver.conf << EOF
KUBE_APISERVER_OPTS="--v=2 \\
--allow-privileged=true \\
--bind-address=0.0.0.0 \\
--secure-port=6443 \\
--advertise-address=192.168.153.161 \\ #master节点ip
--service-cluster-ip-range=10.96.0.0/12 \\
--service-node-port-range=30000-32767 \\
--etcd-servers=https://192.168.153.161:2379,https://192.168.153.162:2379,https://192.168.153.163:2379 \\
--etcd-cafile=/opt/etcd/ssl/ca.pem \\
--etcd-certfile=/opt/etcd/ssl/etcd.pem \\
--etcd-keyfile=/opt/etcd/ssl/etcd-key.pem \\
--client-ca-file=/opt/kubernetes/ssl/ca.pem \\
--tls-cert-file=/opt/kubernetes/ssl/kube-apiserver.pem \\
--tls-private-key-file=/opt/kubernetes/ssl/kube-apiserver-key.pem \\
--kubelet-client-certificate=/opt/kubernetes/ssl/kube-apiserver.pem \\
--kubelet-client-key=/opt/kubernetes/ssl/kube-apiserver-key.pem \\
--service-account-key-file=/opt/kubernetes/ssl/sa.pub \\
--service-account-signing-key-file=/opt/kubernetes/ssl/sa.key \\
--service-account-issuer=https://kubernetes.default.svc.cluster.local \\
--kubelet-preferred-address-types=InternalIP,ExternalIP,Hostname \\
--enable-admission-plugins=NamespaceLifecycle,LimitRanger,ServiceAccount,DefaultStorageClass,DefaultTolerationSeconds,NodeRestriction,ResourceQuota \
--authorization-mode=Node,RBAC \\
--enable-bootstrap-token-auth=true \\
--requestheader-client-ca-file=/opt/kubernetes/ssl/front-proxy-ca.pem \\
--proxy-client-cert-file=/opt/kubernetes/ssl/front-proxy-client.pem \\
--proxy-client-key-file=/opt/kubernetes/ssl/front-proxy-client-key.pem \\
--requestheader-allowed-names=aggregator \\
--requestheader-group-headers=X-Remote-Group \\
--requestheader-extra-headers-prefix=X-Remote-Extra- \\
--requestheader-username-headers=X-Remote-User \\
--enable-aggregator-routing=true"
EOF
其中各条目意思如下
-v:日志等级
–etcd-servers:etcd集群地址
–bind-address:监听地址
–secure-port:https 安全端口
–advertise-address:集群通告地址
–allow-privileged:启用授权
–service-cluster-ip-range:Service虚拟 IP地址段
–enable-admission-plugins:准入控制模块
–authorization-mode:认证授权,启用 RBAC 授权和节点自管理
–enable-bootstrap-token-auth:启用 TLS bootstrap 机制
–token-auth-file:bootstrap token文件
–service-node-port-range:Service nodeport类型默认分配端口范围
–kubelet-client-xxx:apiserver 访问 kubelet客户端证书
–tls-xxx-file:apiserver https 证书
–etcd-xxxfile:连接 Etcd 集群证书
–audit-log-xxx:审计日志
1.20版本以上必须添加参数:--service-account-issuer,--service-account-signing-key-file
启动聚合层相关配置:--requestheader-client-ca-file、--proxy-client-cert-file、--proxy-client-key-file、--requestheader-allowed-names、--requestheader-group-headers、--requestheader-extra-headers-prefix、--requestheader-username-headers
设置启动配置
master1节点执行
cat > /usr/lib/systemd/system/kube-apiserver.service << EOF
[Unit]
Description=Kubernetes API Server
Documentation=https://github.com/kubernetes/kubernetes
After=network.target
[Service]
EnvironmentFile=/opt/kubernetes/cfg/kube-apiserver.conf
ExecStart=/opt/kubernetes/bin/kube-apiserver \$KUBE_APISERVER_OPTS
Restart=on-failure
RestartSec=10s
LimitNOFILE=65535
[Install]
WantedBy=multi-user.target
EOF
拷贝到其他master节点
NODES='master2 master3'; \
for NODE in $NODES; \
do \
scp /usr/lib/systemd/system/kube-apiserver.service $NODE:/usr/lib/systemd/system/;\
done
设置开机启动
所有master节点执行
systemctl daemon-reload && systemctl enable --now kube-apiserver
验证
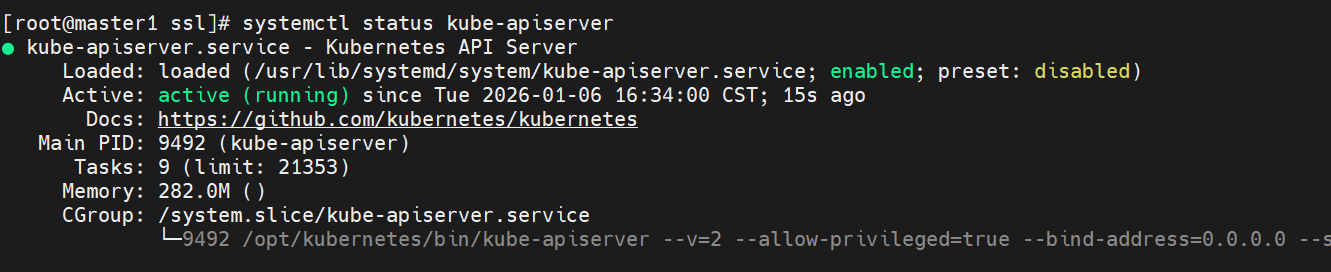
systemctl status kube-apiserver























 5749
5749

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








