1、kali中使用sqlamp 访问靶机OWAS中页面进行SQL注入提示:unable to connect to the target URL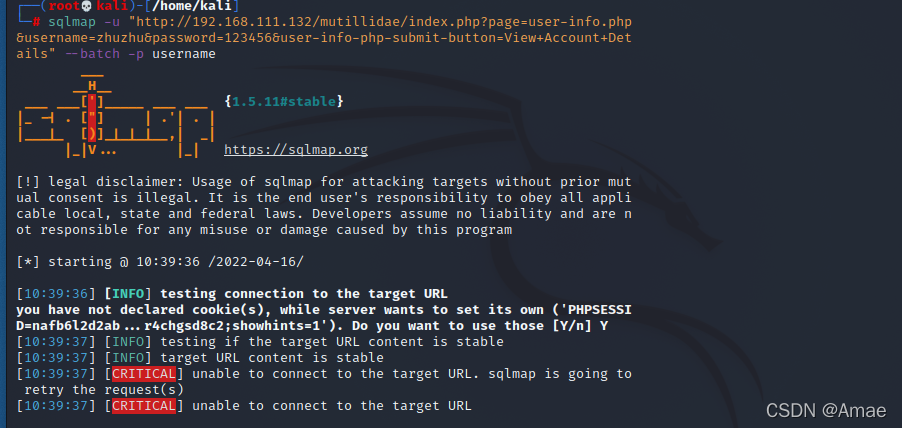
2、看了网上的都是扯淡增加代理访问
sqlmap -u "http://192.168.111.132/mutillidae/index.php?page=user-info.php&username=zhuzhu&password=123456&user-info-php-submit-button=View+Account+Details" --batch -p username --proxy=http://192.168.1.1 --level=5 --rick=3





 在Kali Linux中尝试使用sqlmap工具访问OWASP靶机上的user-info.php页面进行SQL注入测试时,遇到了无法连接目标URL的问题。尝试了网上建议的增加代理设置,如`--proxy=http://192.168.1.1`,但问题依旧。命令行参数包括`--batch`、`--level=5`和`--risk=3`,但连接失败。这可能涉及到网络配置、靶机状态或者sqlmap的使用方法等多方面因素。
在Kali Linux中尝试使用sqlmap工具访问OWASP靶机上的user-info.php页面进行SQL注入测试时,遇到了无法连接目标URL的问题。尝试了网上建议的增加代理设置,如`--proxy=http://192.168.1.1`,但问题依旧。命令行参数包括`--batch`、`--level=5`和`--risk=3`,但连接失败。这可能涉及到网络配置、靶机状态或者sqlmap的使用方法等多方面因素。
















 2万+
2万+

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








