Reverse
crackme
直接从cmd窗口运行附件即可得flag
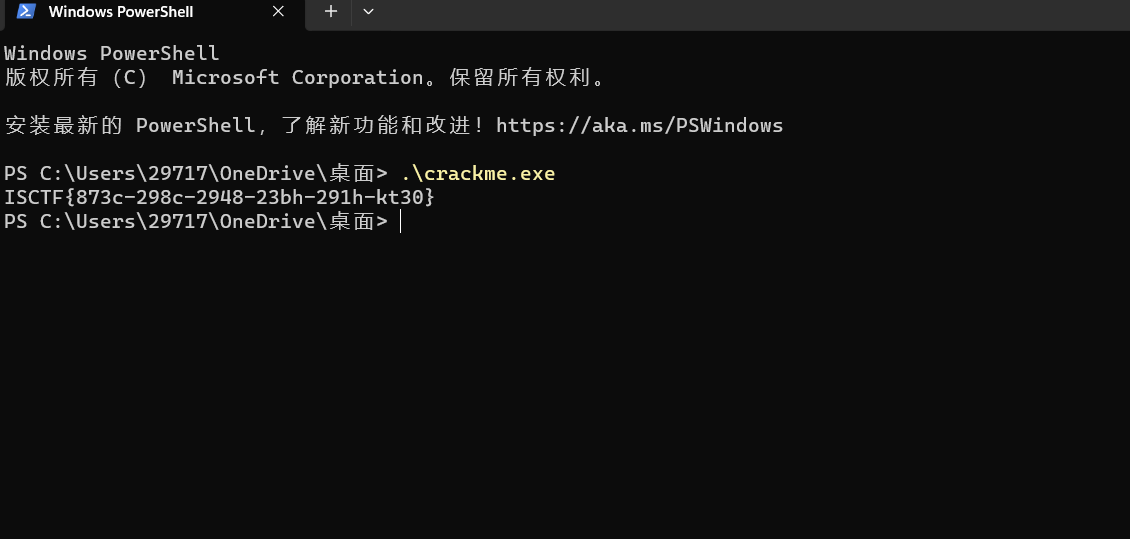
mfx_re
用010Editor打开附件,将附件的MFX字段全部替换为UPX
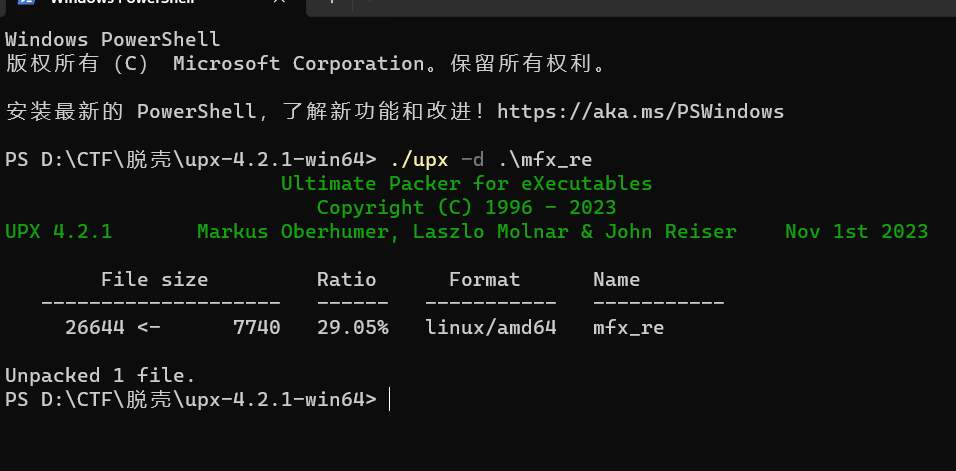
然后使用upx -d命令进行脱壳
之后使用ida64打开,对代码进行分析,可知程序对输入字符串的每一位的ASCII码值都减了1,逆向解密只需加1即可
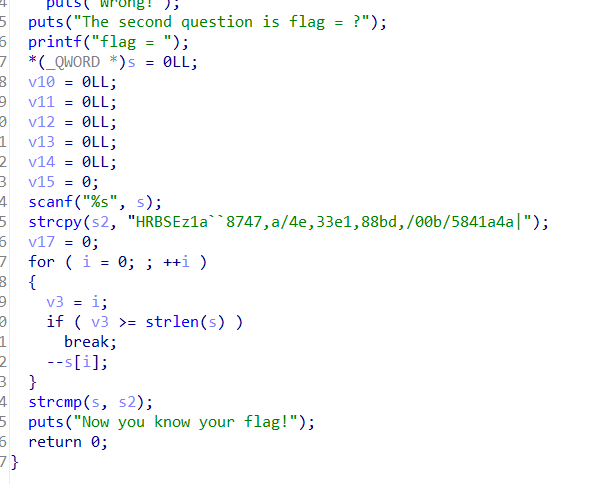
写出exp:
enc = 'HRBSEz1a``8747,a/4e,33e1,88bd,/00b/5841a4a|'
flag = ''
for i in enc:
flag += chr(ord(i) + 1)
print(flag)
得到flag为:ISCTF{2baa9858-b05f-44f2-99ce-011c06952b5b}
EasyRe
ida64打开附件,找到主要加密函数。

分析函数,先对字符串异或17,然后如果字符发ASCII码值等于66或88,用155减去该字符,最后对字符串进行逆序。
写出解密脚本解密,exp如下:
enc = ']P_ISRF^PCY[I_YWERYC'
ttmp = ''
flag = ''
ttmp = reversed(enc)
for i in ttmp:
if ord(i) == (155 - 66) or ord(i) == (155 - 88):
flag += chr((155 - ord(i)) ^ 17)
else:
flag += chr(ord(i) ^ 17)
print(flag)
解出结果为:ISCTFSNXJSIAOWCBXNAL
flag为:ISCTF{SNXJSIAOWCBXNAL}
easy_flower_tea
ida打开,找到主要加密函数,简单花指令,直接修复,反编译分析代码
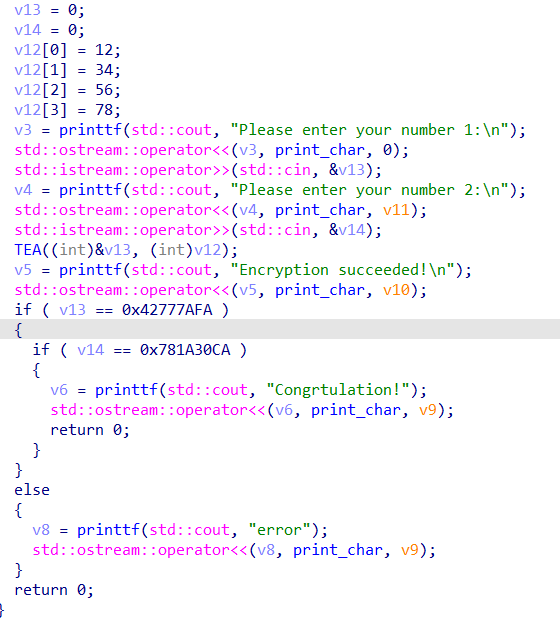
简单的tea加密,脚本直接解出,exp:
#include <stdio.h>
#include <stdlib.h>
void decrypt (unsigned int* v, unsigned int* k);
int main()
{
unsigned int flag[3] = {0x42777AFA,0x781A30CA};
unsigned int key[4] = {12,34,56,78};
decrypt(flag,key);
for(int i = 0;i < 2;i++)
{
printf("%d,",flag[i]);
}
return 0;
}
void decrypt(unsigned int* v, unsigned int* k)
{
int j,n;
for(j = 0;j < 1;j += 2)
{
n = j + 1;
unsigned int delta = 1640531527;
unsigned int sum = 0 - delta*32;
for (int i = 0; i < 32; i++)
{
v[n] -= (16 * v[j] + k[2]) ^ (v[j] + sum) ^ ((v[j] >> 5) + k[3]);
v[j] -= (16 * v[n] + k[0]) ^ (v[n] + sum) ^ ((v[n] >> 5) + k[1]);
sum += delta;
}
}
}
得到的10进制数字加上ISCTF头即可:ISTCTF{1472353 3847872}
babyRe
运行程序发现babyRE.py报错
使用PyInstaller Extractor 对.exe进行解包
python pyinstxtractor.py .\babyRe.exe
找到babyRe文件,发现其无后缀名,使用010Editor打开,分析其应为.pyc文件,对其文件头进行补全,并加上后缀名
对.pyc文件进行反编译,得到.py文件
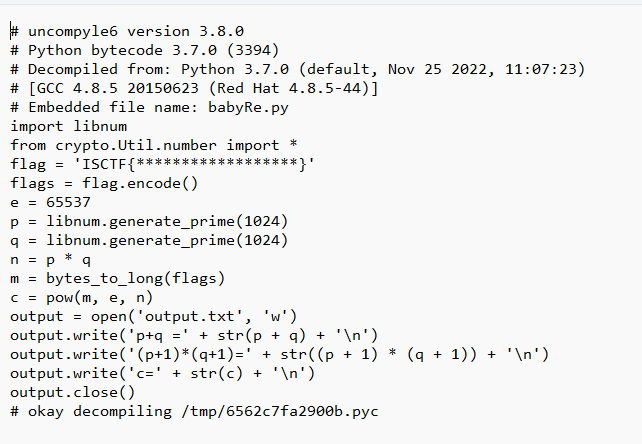
简单RSA,脚本直接解出flag,exp:
a=292884018782106151080211087047278002613718113661882871562870811030932129300110050822187903340426820507419488984883216665816506575312384940488196435920320779296487709207011656728480651848786849994095965852212548311864730225380390740637527033103610408592664948012814290769567441038868614508362013860087396409860
b=21292789073160227295768319780997976991300923684414991432030077313041762314144710093780468352616448047534339208324518089727210764843655182515955359309813600286949887218916518346391288151954579692912105787780604137276300957046899460796651855983154616583709095921532639371311099659697834887064510351319531902433355833604752638757132129136704458119767279776712516825379722837005380965686817229771252693736534397063201880826010273930761767650438638395019411119979149337260776965247144705915951674697425506236801595477159432369862377378306461809669885764689526096087635635247658396780671976617716801660025870405374520076160
c=5203005542361323780340103662023144468501161788183930759975924790394097999367062944602228590598053194005601497154183700604614648980958953643596732510635460233363517206803267054976506058495592964781868943617992245808463957957161100800155936109928340808755112091651619258385206684038063600864669934451439637410568700470057362554045334836098013308228518175901113235436257998397401389511926288739759268080251377782356779624616546966237213737535252748926042086203600860251557074440685879354169866206490962331203234019516485700964227924668452181975961352914304357731769081382406940750260817547299552705287482926593175925396
import libnum
import gmpy2
phi=b-a*2
e=65537
n=b-a-1
print(phi)
print(n)
d=gmpy2.invert(e,phi)
m=pow(c,d,n)
print(libnum.n2s(int(m)))
解得flag为:ISCTF{kisl-iopa-qdnc-tbfs-ualv}
FloweyRSA
ida64打开,简单花指令,直接去花,反编译main函数
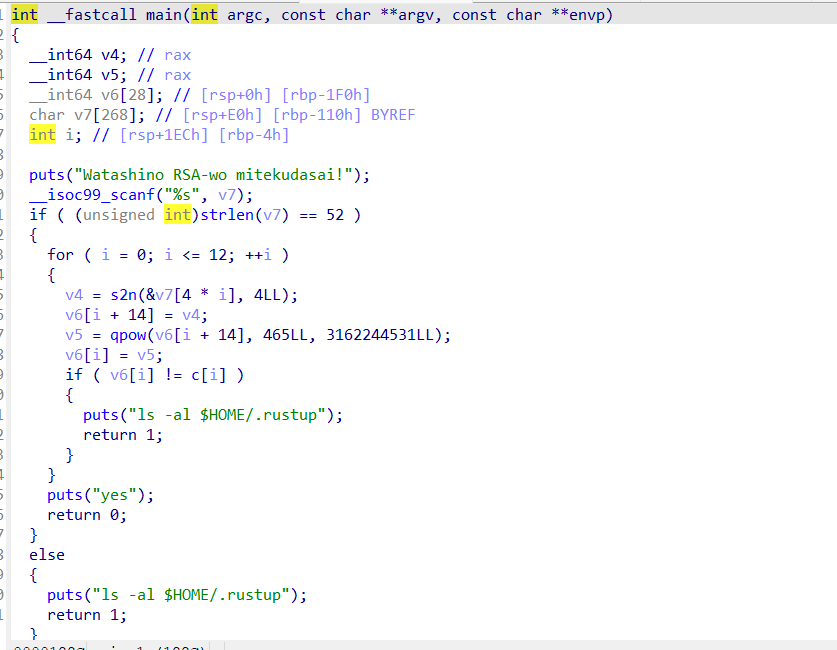
简单rsa,网站在线分解素数
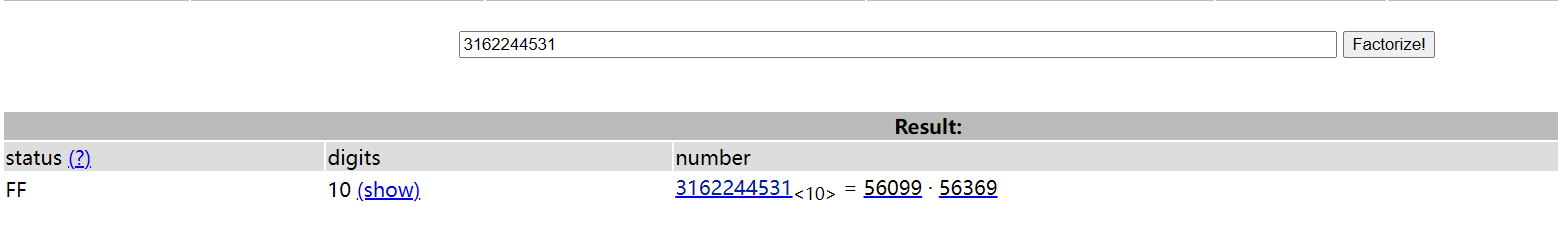
直接脚本一把梭,exp:
p = 56099
q = 56369
ppp = [1966878405,2375075638,2166893744,2129446000,2488145363,746243878,1904115824,818668601,2983811740,1840670651,306202172,2009857636,299417177]
import libnum
import gmpy2
flag = ''
for c in ppp:
phi = (p - 1) * (q - 1)
e = 465
n = p * q
d=gmpy2.invert(e,phi)
m=pow(c,d,n)
printtt = libnum.n2s(int(m)).decode()
flag += printtt
print(flag)
解得flag:flag{reverse_is_N0T_@lways_jusT_RE_myy_H@bIb1!!!}
z3_revenge
ida打开,查看主要函数,发现约束条件
printf("Printf input the flag:");
scanf("%s", &v4);
if ( !BYTE3(v9)
&& (char)v4 + 394 - 740 * SBYTE1(v4) == -60953
&& SBYTE1(v4) + 878 - (SBYTE2(v4) + 614) == 280
&& 195 * SBYTE2(v4) + 457 - SBYTE3(v4) == 13438
&& SBYTE3(v4) - 330 - (186 - SBYTE4(v4)) == -362
&& 840 * SBYTE4(v4) - 977 * SBYTE5(v4) == -61371
&& 729 * SBYTE5(v4) - (197 - SBYTE6(v4)) == 89567
&& SBYTE6(v4) - 899 + 946 - SHIBYTE(v4) == 44
&& SHIBYTE(v4) - 593 - 373 * (char)v5 == -18770
&& 842 * (char)v5 + 261 * SBYTE1(v5) == 55613
&& 787 * SBYTE1(v5) - (SBYTE2(v5) + 204) == 43029
&& 664 * SBYTE2(v5) + 160 - SBYTE3(v5) == 34635
&& SBYTE3(v5) - 885 + 366 * SBYTE4(v5) == 35768
&& 659 * SBYTE4(v5) + 892 - SBYTE5(v5) == 66691
&& 500 * SBYTE5(v5) - (SBYTE6(v5) + 535) == 49920
&& SBYTE6(v5) - 983 + 194 - SHIBYTE(v5) == -844
&& SHIBYTE(v5) - 871 + 545 - (char)v6 == -326
&& 762 * (char)v6 - 443 * SBYTE1(v6) == 51835
&& 846 * SBYTE1(v6) - (SBYTE2(v6) + 964) == 45464
&& SBYTE2(v6) - 363 + 218 * SBYTE3(v6) == 9549
&& SBYTE3(v6) - 477 - 170 * SBYTE4(v6) == -9272
&& SBYTE4(v6) - 177 - (351 - SBYTE5(v6)) == -379
&& SBYTE6(v6) + 541 + 492 * SBYTE5(v6) == 48314
&& SBYTE6(v6) - 952 - (454 - SHIBYTE(v6)) == -1306
&& SHIBYTE(v6) - 731 - ((char)v7 + 890) == -1615
&& (char)v7 - 941 - (SBYTE1(v7) + 380) == -1332
&& SBYTE1(v7) - 328 + SBYTE2(v7) + 124 == -98
&& SBYTE2(v7) + 695 + SBYTE3(v7) + 186 == 980
&& SBYTE3(v7) - 412 + 632 * SBYTE4(v7) == 62205
&& SBYTE4(v7) + 820 + SBYTE5(v7) + 257 == 1221
&& SBYTE5(v7) - 155 + SBYTE6(v7) + 673 == 613
&& 786 * SBYTE6(v7) - (773 - SHIBYTE(v7)) == 38625
&& SHIBYTE(v7) + 929 - (956 - (char)v8) == 171
&& (char)v8 + 913 + 311 - SBYTE1(v8) == 1270
&& SBYTE1(v8) + 113 - 705 * SBYTE2(v8) == -40018
&& SBYTE3(v8) + 782 + 901 * SBYTE2(v8) == 52237
&& SBYTE3(v8) - 716 + 255 - SBYTE4(v8) == -411
&& SBYTE4(v8) + 307 + SBYTE5(v8) + 874 == 1329
&& SBYTE5(v8) + 355 - (201 - SBYTE6(v8)) == 308
&& SBYTE6(v8) + 934 + 531 - SHIBYTE(v8) == 1465
&& SHIBYTE(v8) - 801 - ((char)v9 + 413) == -1209
&& (char)v9 - 690 + 558 - SBYTE1(v9) == -135
&& SBYTE1(v9) - 559 + SBYTE2(v9) + 953 == 571
&& SBYTE2(v9) + 141 - 654 * (char)v4 == -47476 )
{
puts("true");
}
else
{
puts("false");
}
使用z3库进行方程组求解,exp:
from z3 import *
s = Solver()
c = [Int('v%d'%i)for i in range(43)]
s.add(c[0] + 394 - 740 * c[1] == -60953)
s.add(c[1] + 878 - (c[2] + 614) == 280)
s.add(195 * c[2] + 457 - c[3] == 13438)
s.add(c[3] - 330 - (186 - c[4]) == -362)
s.add(840 * c[4] - 977 * c[5] == -61371)
s.add(729 * c[5] - (197 - c[6]) == 89567)
s.add(c[6] - 899 + 946 - c[7] == 44)
s.add(c[7] - 593 - 373 * c[8] == -18770)
s.add(842 * c[8] + 261 * c[9] == 55613)
s.add(787 * c[9] - (c[10] + 204) == 43029)
s.add(664 * c[10] + 160 - c[11] == 34635)
s.add(c[11] - 885 + 366 * c[12] == 35768)
s.add(659 * c[12] + 892 - c[13] == 66691)
s.add(500 * c[13] - (c[14] + 535) == 49920)
s.add(c[14] - 983 + 194 - c[15] == -844)
s.add(c[15] - 871 + 545 - c[16] == -326)
s.add(762 * c[16] - 443 * c[17] == 51835)
s.add(846 * c[17] - (c[18] + 964) == 45464)
s.add(c[18] - 363 + 218 * c[19] == 9549)
s.add(c[19] - 477 - 170 * c[20] == -9272)
s.add(c[20] - 177 - (351 - c[21]) == -379)
s.add(c[22] + 541 + 492 * c[21] == 48314)
s.add(c[22] - 952 - (454 - c[23]) == -1306)
s.add(c[23] - 731 - (c[24] + 890) == -1615)
s.add(c[24] - 941 - (c[25] + 380) == -1332)
s.add(c[25] - 328 + c[26] + 124 == -98)
s.add(c[26] + 695 + c[27] + 186 == 980)
s.add(c[27] - 412 + 632 * c[28] == 62205)
s.add(c[28] + 820 + c[29] + 257 == 1221)
s.add(c[29] - 155 + c[30] + 673 == 613)
s.add(786 * c[30] - (773 - c[31]) == 38625)
s.add(c[31] + 929 - (956 - c[32]) == 171)
s.add(c[32] + 913 + 311 - c[33] == 1270)
s.add(c[33] + 113 - 705 * c[34] == -40018)
s.add(c[35] + 782 + 901 * c[34] == 52237)
s.add(c[35] - 716 + 255 - c[36] == -411)
s.add(c[36] + 307 + c[37] + 874 == 1329)
s.add(c[37] + 355 - (201 - c[38]) == 308)
s.add(c[38] + 934 + 531 - c[39] == 1465)
s.add(c[39] - 801 - (c[40] + 413) == -1209)
s.add(c[40] - 690 + 558 - c[41] == -135)
s.add(c[41] - 559 + c[42] + 953 == 571)
s.add(c[42] + 141 - 654 * c[0] == -47476)
s.check()
result = s.model()
flag = ''
for i in range(43):
flag += chr(result[c[i]].as_long())
print(flag)
解出flag为:ISCTF{ad1745de-dd7f-4a13-821c-2bd69b0d6614}




















 1716
1716

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








