Our vulnerability-scanning system at PeckShield has so far discovered several dangerous smart contract vulnerabilities ( batchOverflow[1], proxyOverflow[2], transferFlaw[3], ownerAnyone[4],multiOverflow[5]), burnOverflow[6]), ceoAnyone[7]). Some of them could be used by attackers to generate tokens out of nowhere or steal tokens from legitimate holders, while others can be used to take over the ownership from legitimate contract owner (or administrator).
Today, our system reports a new vulnerability called allowAnyone that affects a number of publicly tradable tokens (including EDU). Because of the vulnerability, attackers can steal valuable tokens (managed by affected, vulnerable smart contracts) from legitimate holders. More specifically, our investigation shows that in those vulnerable smart contracts, the ERC20 standard API,transferFrom(), has an issue when checking the allowed[ ][ ] storage, which typically represents the amount of tokens that _from allows msg.sender to use. As a result, anyone can transfer tokens on behalf of another one who has non-zero balance.
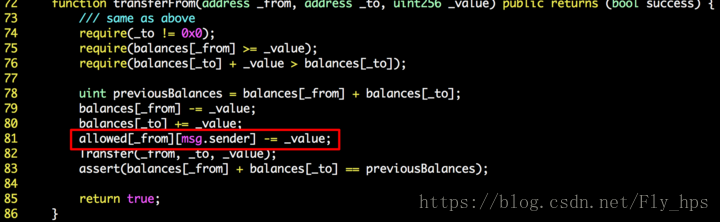
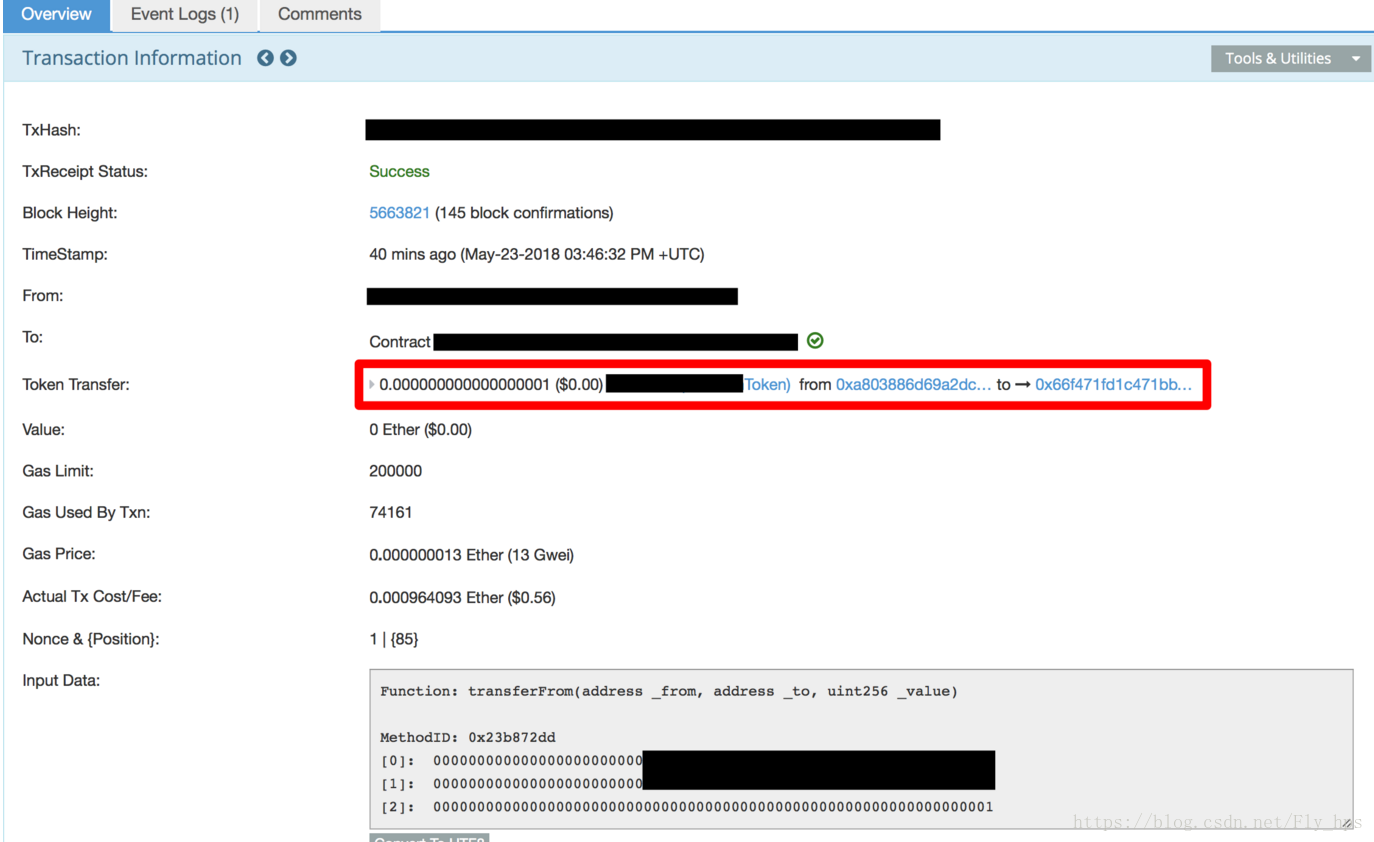
In a safe transferFrom implementation, checking the allowance is essential and is typically the case in a number of reference ERC20 transferFrom() implementation. (Otherwise, it would be a stealFrom() implementation!) On the other hand, SafeMath again proves itself as a solid library since it can even cover the missed allowance check logic in this case. As always, make sure you use it in all smart contracts that have arithmetic operations!
We have notified a number of affected development teams and a few major cryptocurrency exchanges have taken preventative actions to suspend relevant deposit and withdrawal operations. In the meantime, we closely monitor latest development. Affected development teams are strongly encouraged to contract us and we are willing to offer any necessary help!







 PeckShield发现了一个新的智能合约漏洞allowAnyone,该漏洞影响了包括EDU在内的多个公开交易代币。攻击者利用此漏洞可以从合法持有者那里窃取有价值的代币。受影响的智能合约在使用ERC20标准API transferFrom()时存在问题,导致任何人可以代表另一个拥有非零余额的人转账。
PeckShield发现了一个新的智能合约漏洞allowAnyone,该漏洞影响了包括EDU在内的多个公开交易代币。攻击者利用此漏洞可以从合法持有者那里窃取有价值的代币。受影响的智能合约在使用ERC20标准API transferFrom()时存在问题,导致任何人可以代表另一个拥有非零余额的人转账。
















 1424
1424

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








