Our vulnerability-scanning system at PeckShield has so far discovered several dangerous smart contract vulnerabilities ( batchOverflow[1], proxyOverflow[2], transferFlaw[3], ownerAnyone[4], multiOverflow[5], burnOverflow[6]). These vulnerabilities typically affect various tokens that may be publicly traded in exchanges. Today, we would like to report a new vulnerability named ceoAnyone, which affects, instead of tradable tokens in exchanges, but Crypto-Games.
Starting from the end of 2017, blockchain-based crypto-games have become popular especially with the initial success of CryptoKitties. Among crypto-games, cypto idle game is an interesting category that enables players to make money by idling for hours, then followed by a profit-making transaction (e.g., selling a Lab Rat on Ether Goo). Many of the cypto idle game owners make profit from the transaction fee. However, what if the owner address could be manipulated or completely hijacked by attackers?
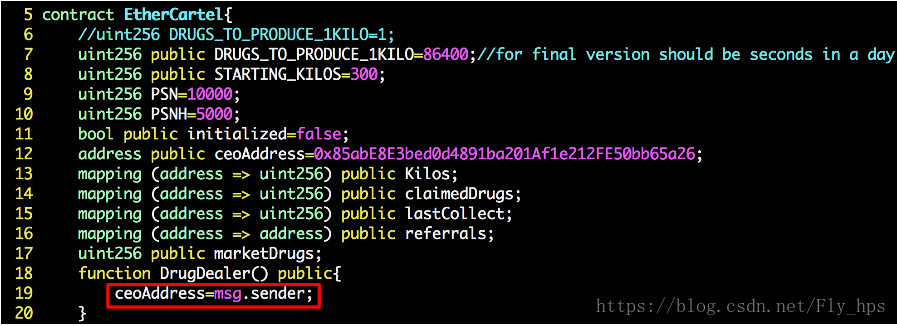
Figure 1: A ceoAnyone-affected Crypto Idle Game Smart Contract
Figure 1 illustrates such a smart contract of a crypto idle game named Ether Cartel. Similar to Ether Shrimp Farm that requires end users to hatch and sell shrimp in a bid to maximize production before ultimately exchanging eggs for ether, Ether Cartel takes the same concept but applies it to drug running. The game “features a high tech automated market that lets you instantly buy or sell drugs with a single transaction. The more kilos you have, the more drugs they produce (each kilo produces at a rate of 1 per day). Collect more kilos with your drugs to multiply your production.”

Ether Cartel was deployed in mainnet on Friday, May-18-2018 05:14:56 PM +UTC. Unfortunatley, it was exploited on the same Friday, May-18-2018 06:25:12 PM +UTC, within 1 hour and 11 minutes after deployment! The vulnerable code is in lines 18-20: there’s a public function named DrugDealer() which allows the caller to change the beneficiary address — ceoAddress.
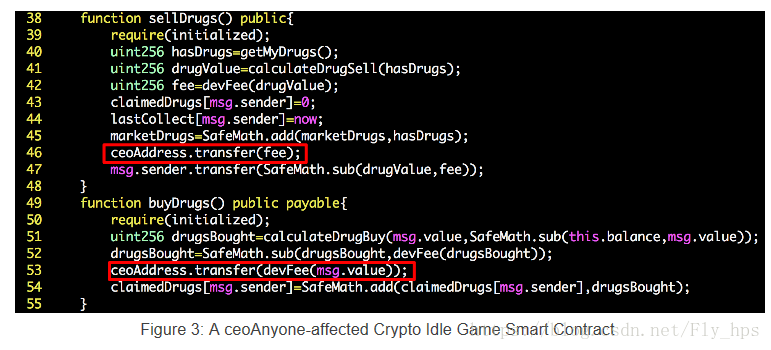
As shown in Figure 3, the ceoAddress collects the fee whenever sellDrugs() or buyDrugs() is called. Our analysis shows that this particular game has three versions of smart contracts deployed by the same author. After cross-examining these contracts, we have the reason to believe that the buggy drugDealer() is actually the constructor of the smart contract. However, the author accidentally gave it a wrong name (not identical to the contract name). This seems to be a classic problem that has been studied since 2016 (the Rubixi contract was pointed out to have a similar bug in [7]).
As of writing this blog, we have found multiple attackers are gaming to exploiting this vulnerability. And one particular attacker seems to monitor the change of ceoAddress and will immediately regain the control if it has been modified by others. (One attacker has collected around 1.6 ETH by exploiting this vulnerable Ether Cartel game.) After identifying this particular vulnerability, we immediately made the efforts to contract the author. Also, our internal scanning shows that some other smart contracts of similar crypto games have the same problem. We are now contacting these affected development teams by providing necessary technical support.
About US
PeckShield Inc. is a leading blockchain security company with the goal of elevating the security, privacy, and usability of current blockchain ecosystem. For any business or media inquires (including the need for smart contract auditing), please contact us at telegram, twitter, or email.
References
- [1] PeckShield: New batchOverflow Bug in Multiple ERC20 Smart Contracts (CVE-2018-10299), April 22, 2018
- [2] PeckShield: New proxyOverflow Bug in Multiple ERC20 Smart Contracts (CVE-2018-10376), April 25, 2018
- [3] PeckShield: Your Tokens Are Mine: A Suspicious Scam Token in A Top Exchange, April 28, 2018
- [4] PeckShield: New ownerAnyone Bug Allows For Anyone to ‘‘Own’’ Certain ERC20-Based Smart Contracts (CVE-2018-10705), May 03, 2018
- [5] PeckShield: New multiOverflow Bug Identified in Multiple ERC20 Smart Contracts (CVE-2018-10706), May 10, 2018
- [6] PeckShield: New burnOverflow Bug Identified in Multiple ERC20 Smart Contracts (CVE-2018-11239), May 18, 2018
- [7] Atzei N., Bartoletti M., Cimoli, T.: A Survey of Attacks on Ethereum Smart Contracts, Oct, 2016







 PeckShield发现了一个新的智能合约漏洞“CEO Anyone”,该漏洞影响Crypto-Games中的CryptoIdleGame类别。攻击者可以利用此漏洞篡改或完全劫持游戏所有者的地址,从而非法获取交易费用。
PeckShield发现了一个新的智能合约漏洞“CEO Anyone”,该漏洞影响Crypto-Games中的CryptoIdleGame类别。攻击者可以利用此漏洞篡改或完全劫持游戏所有者的地址,从而非法获取交易费用。
















 1万+
1万+

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








