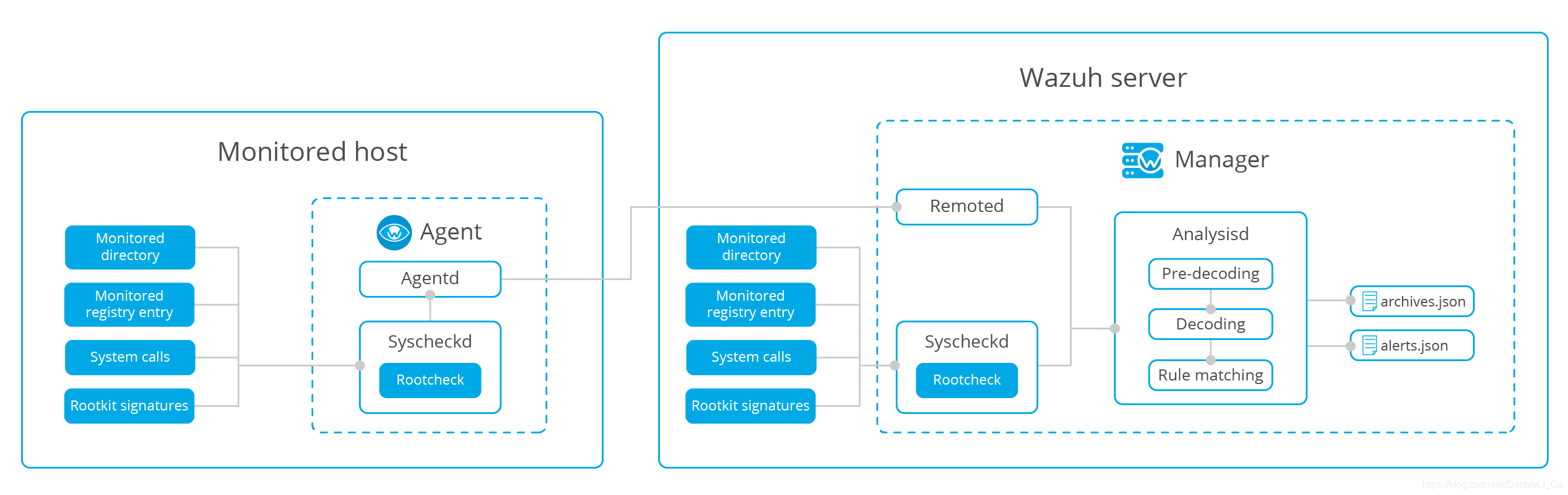
Wazuh由三部分组成:Agent端、Server端、ES
下图是官方给出的整体架构图:
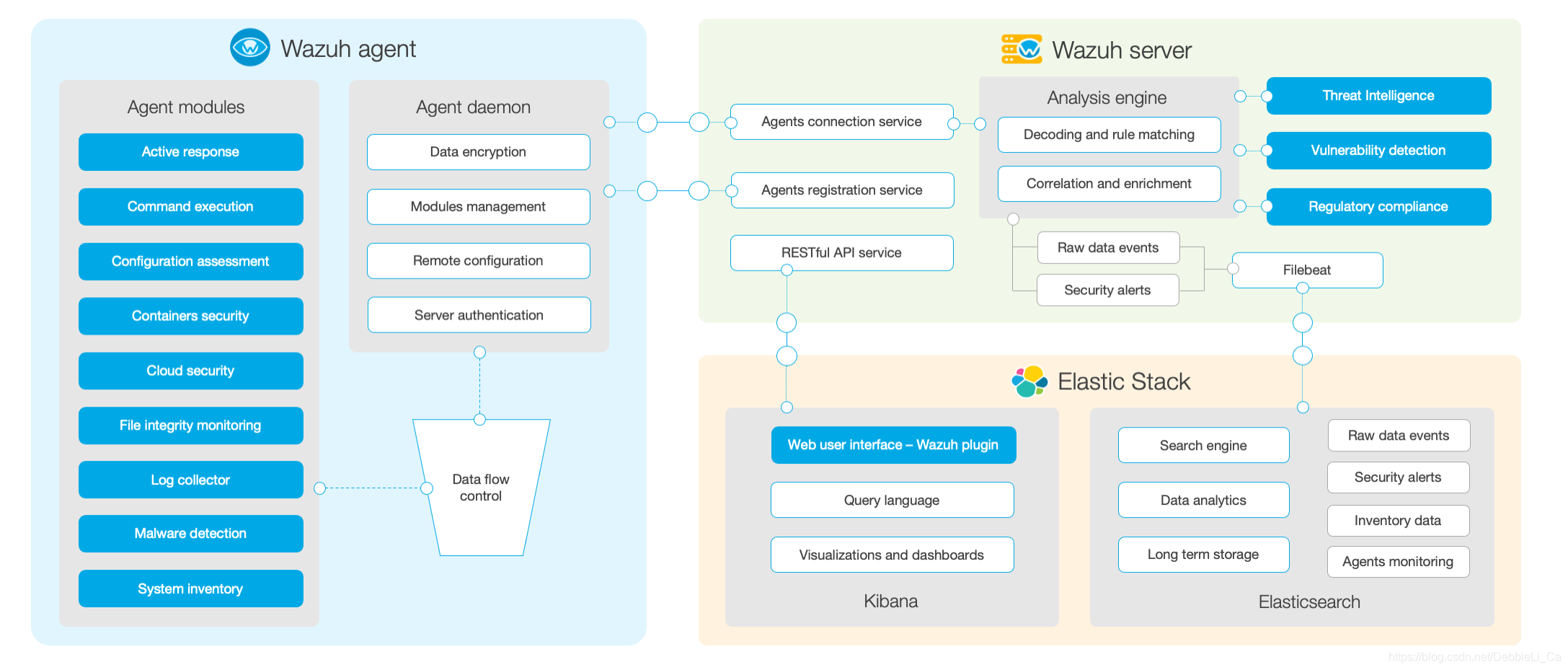
server端收集数据以日志形式加密后发送到manager,经过解码和规则匹配生成事件和告警通过filebeat采集送到ES之中,经过logstash进行数据处理在kibana上展示出来。
Agent
agent端负责信息收集,预防威胁和检测、响应功能,详细介绍继续观看呦~~
下图为官方给出的Agent端详细架构:
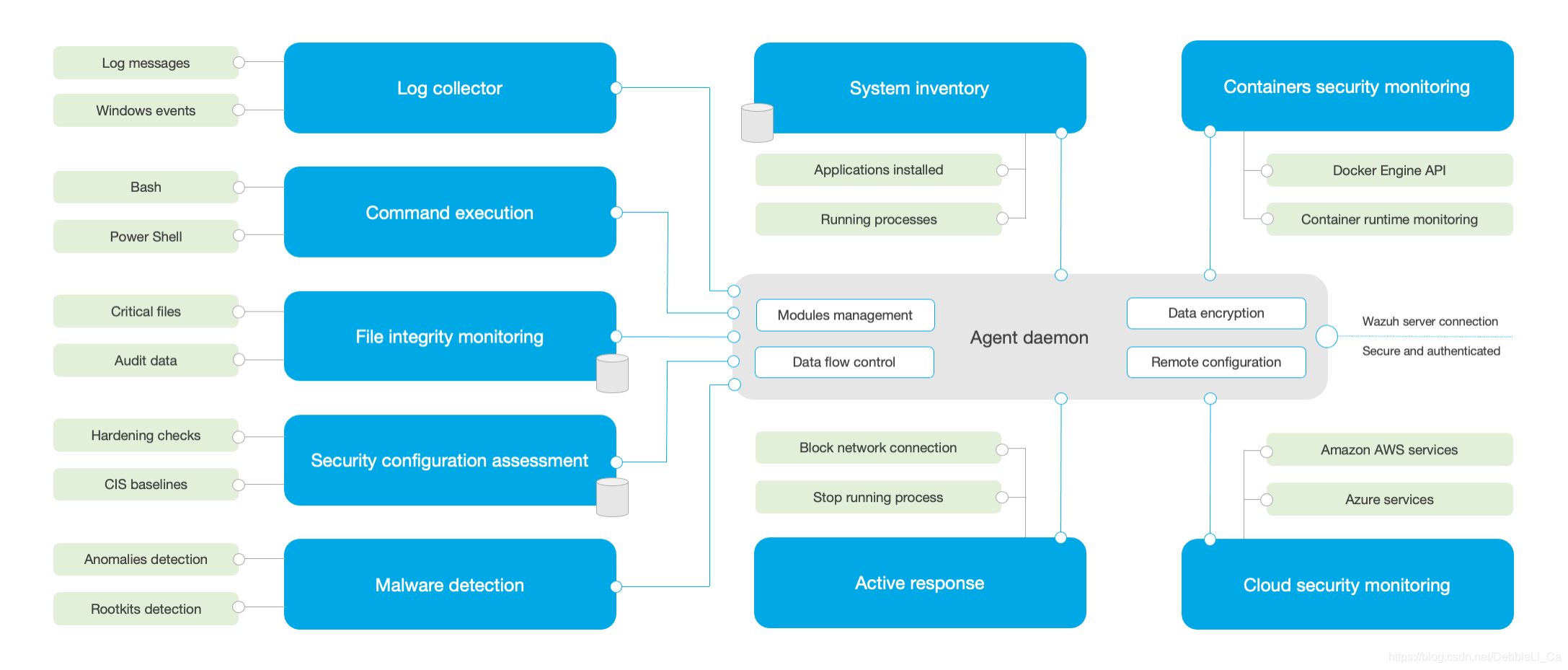
以下是他的部分功能~~
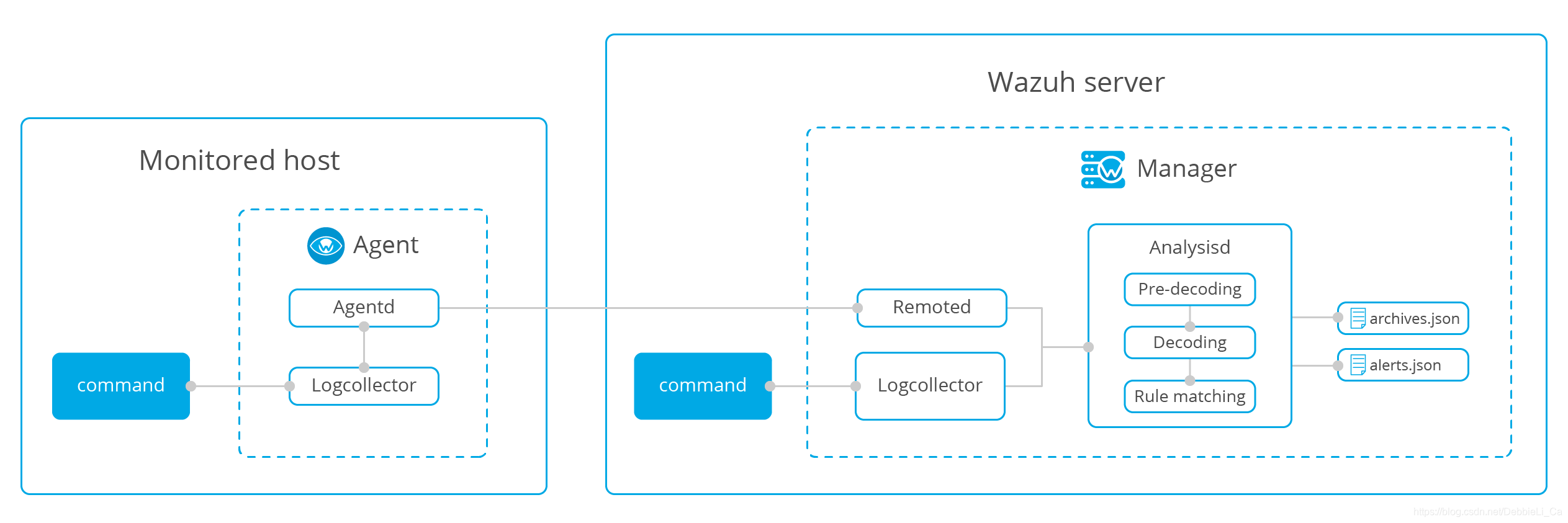
Log collector
这个模块可以读取日志信息和Windows事件
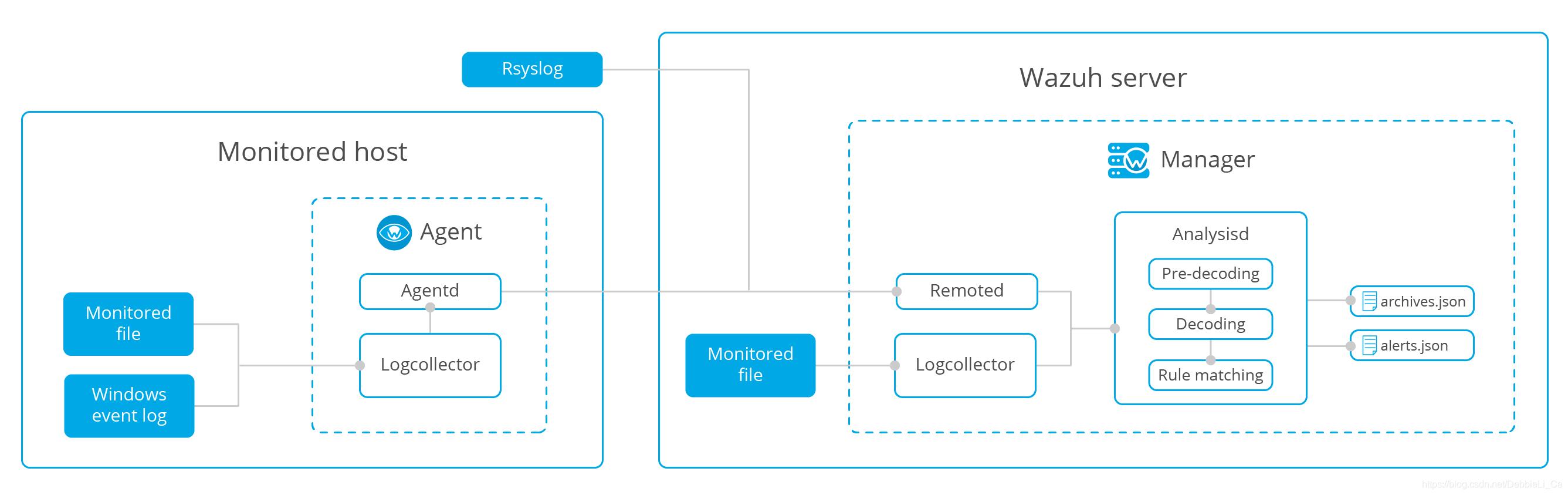
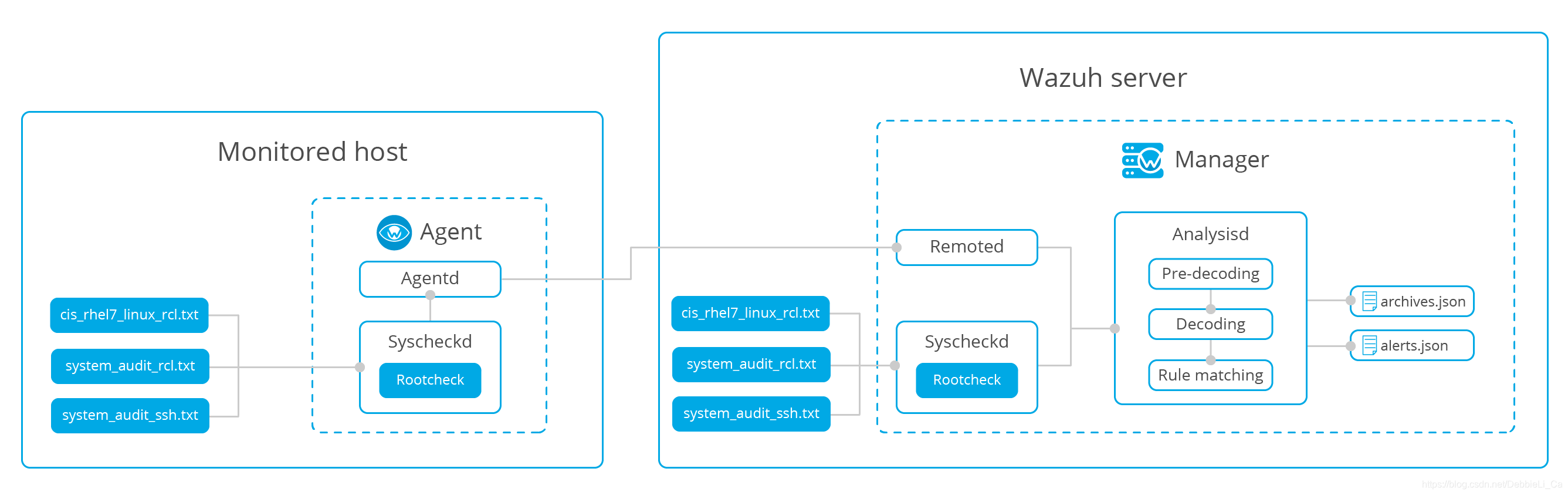
包含的logcollector模块收集信息后将数据收集起来送到server端进行分析
这里实现了远程接收系统日志:(自定义端口接受和存储在纯文本文件里)
<ossec_config>
<remote>
<connection>syslog</connection>
<port>513</port>
<protocol>tcp</protocol>
<allowed-ips>192.168.2.0/24</allowed-ips>
</remote>
</ossec_config>
实现自定义端口的代码里表明了
- manager会接收从网络传来的系统日志信息
- 定义wazuh需要监听检索日志的端口为空闲端口513
- 定义了传输协议
- 定义日志来源IP
File integrity monitoring
该模块定期扫描,把受监视的文件与之前对比是否存在修改、删除、新增然后将结果同步到数据库并且输送到manager。如果存在差别便会生成报警。
kibana中可以实时看到可视化结果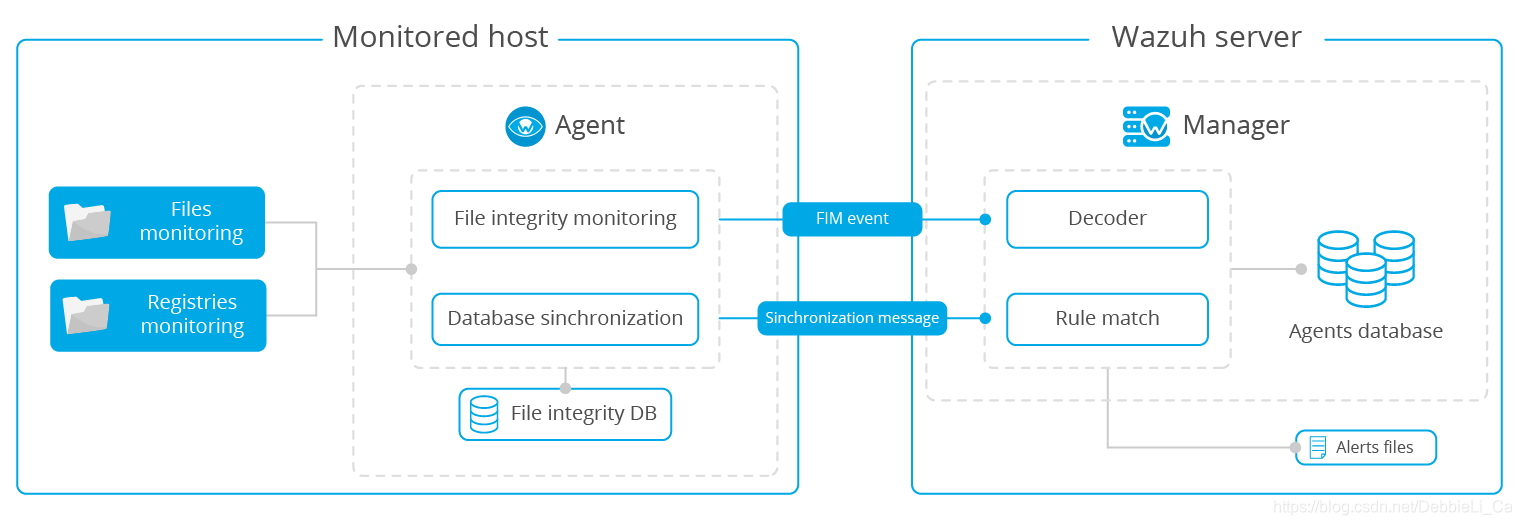
Anomaly and malware detection
这个模块主要包含功能有
文件监控
监控注册表
系统调用
rootkit签名
Security Configuration Assessment
安全配置评估(SCA),通过扫描策略文件评估主机是否安全
Monitoring security policies——>Rootcheck
通过根检查引擎查看:
- 检查进程是否正在运行
- 检查文件是否存在
- 检查文件的内容是否包含模式,或者Windows注册表项是否包含字符串或仅存在。
Monitoring system calls
是Linux系统会提供的服务哦~通过追踪到的安全事件信息和规则进行匹配,查看是否违反安全策略的设定。
Command monitoring
wazuh会收集Agent端特定的需要监视的命令以日志的形式发送给server。可以监视正在运行的Windows进程,磁盘空间的利用率,检查输出是否更改,平均负载和USB的存储
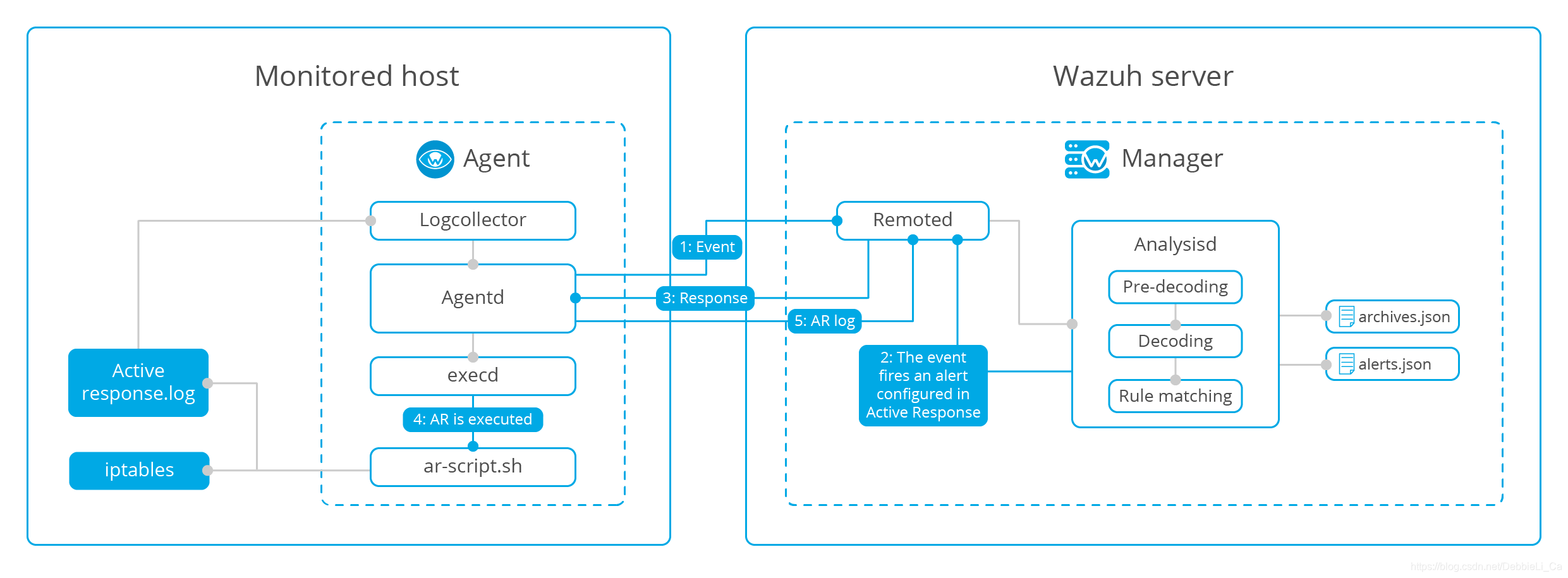
Active Response
当使用规则触发警报时,会采取自动对策来执行对应脚本
Agent Labels
将不同的代理组分类,分组将会展示在JSON格式的输出里,例如!
{
"timestamp": "2017-03-07T13:31:41-0800",
"rule": {
"level": 7,
"description": "Integrity checksum changed.",
"id": "550",
"firedtimes": 1,
"groups": [
"ossec",
"syscheck"
],
"pci_dss": [
"11.5"
]
},
"agent": {
"id": "001",
"name": "92603de31548",
"ip": "192.168.66.1",
"labels": {
"aws": {
"instance-id": "i-052a1838c",
"sec-group": "sg-1103"
},
"network": {
"ip": "172.17.0.0",
"mac": "02:42:ac:11:00:02"
}
}
},
"manager": {
"name": "ubuntu"
},
"full_log": "Integrity checksum changed for: '/var/ossec/etc/ossec.conf' Size changed from '3663' to '3664' Old md5sum was: '98b351df146410f174a967d726f9965e' New md5sum is : '7f4f5846dcaa0013a91bd6d3ac4a1915' Old sha1sum was: 'c6368b866a835b15baf20976ae5ea7ea2788a30e' New sha1sum is : 'c959321244bdcec824ff0a32cad6d4f1246f53e9'",
"syscheck": {
"path": "/var/ossec/etc/ossec.conf",
"size_before": "3663",
"size_after": "3664",
"perm_after": "100640",
"uid_after": "0",
"gid_after": "999",
"md5_before": "98b351df146410f174a967d726f9965e",
"md5_after": "7f4f5846dcaa0013a91bd6d3ac4a1915",
"sha1_before": "c6368b866a835b15baf20976ae5ea7ea2788a30e",
"sha1_after": "c959321244bdcec824ff0a32cad6d4f1246f53e9",
"event": "modified"
},
"decoder": {
"name": "syscheck_integrity_changed"
},
"location": "syscheck"
}
或者是以电子邮件的形式:!!
Wazuh Notification.
2017 Mar 07 13:31:41
Received From: (92603de31548) 192.168.66.1->syscheck
Rule: 550 fired (level 7) -> "Integrity checksum changed."
Portion of the log(s):
aws.instance-id: i-052a1838c
aws.sec-group: sg-1103
network.ip: 172.17.0.0
network.mac: 02:42:ac:11:00:02
Integrity checksum changed for: '/var/ossec/etc/ossec.conf'
Old md5sum was: '98b351df146410f174a967d726f9965e'
New md5sum is : '7f4f5846dcaa0013a91bd6d3ac4a1915'
Old sha1sum was: 'c6368b866a835b15baf20976ae5ea7ea2788a30e'
New sha1sum is : 'c959321244bdcec824ff0a32cad6d4f1246f53e9'
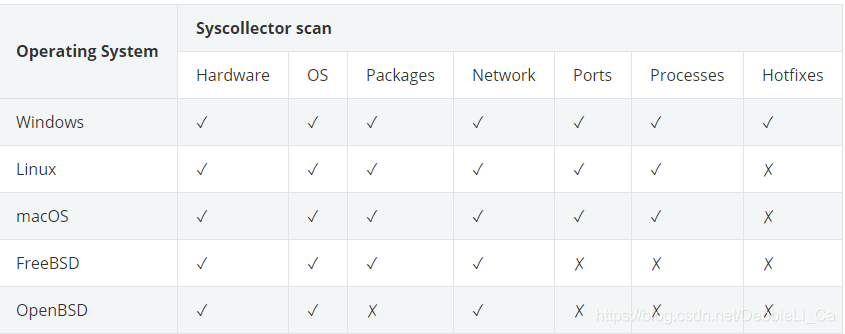
System inventory
在这个模块,使用Syscollector收集信息,比如系统硬件组件的基本信息、操作系统的基本信息等等…
下面给出了它适用的操作系统以及扫描的模块:
Vulnerability detection
可以检测agent端已安装的应用程序是否存在漏洞定期发送给server端
VirusTotal integration
从3.0.0版本开始wazuh就可以集成VirusTotal扫描文件中是否包含恶意内容(病毒,蠕虫,特洛伊木马)
Osquery
从3.5.0版本开始可以设置Osquery配置并收集由Osquery生成的信息以将其发送给manager,并在必要时生成相应的警报。
eg:
{
"timestamp": "2018-07-30T13:54:46.476+0000",
"rule": {
"level": 3,
"description": "osquery data grouped",
"id": "24010",
"firedtimes": 207,
"mail": false,
"groups": [
"osquery"
]
},
"agent": {
"id": "000",
"name": "manager"
},
"manager": {
"name": "manager"
},
"id": "1532958886.437707",
"full_log": "{\"name\":\"system_info\",\"hostIdentifier\":\"manager\",\"calendarTime\":\"Mon Jul 30 13:54:45 2018 UTC\",\"unixTime\":1532958885,\"epoch\":0,\"counter\":461,\"columns\":{\"cgroup_namespace\":\"4026531835\",\"cmdline\":\"\",\"cwd\":\"/\",\"disk_bytes_read\":\"0\",\"disk_bytes_written\":\"0\",\"egid\":\"0\",\"euid\":\"0\",\"gid\":\"0\",\"ipc_namespace\":\"4026531839\",\"mnt_namespace\":\"4026531840\",\"name\":\"migration/0\",\"net_namespace\":\"4026531957\",\"nice\":\"0\",\"on_disk\":\"-1\",\"parent\":\"2\",\"path\":\"\",\"pgroup\":\"0\",\"pid\":\"9\",\"pid_namespace\":\"4026531836\",\"resident_size\":\"\",\"root\":\"/\",\"sgid\":\"0\",\"start_time\":\"0\",\"state\":\"S\",\"suid\":\"0\",\"system_time\":\"2\",\"threads\":\"1\",\"total_size\":\"\",\"uid\":\"0\",\"user_namespace\":\"4026531837\",\"user_time\":\"0\",\"uts_namespace\":\"4026531838\",\"wired_size\":\"0\"},\"action\":\"added\"}",
"decoder": {
"name": "json"
},
"data": {
"action": "added",
"name": "system_info",
"hostIdentifier": "manager",
"calendarTime": "Mon Jul 30 13:54:45 2018 UTC",
"unixTime": "1532958885",
"epoch": "0",
"counter": "461",
"columns": {
"cgroup_namespace": "4026531835",
"cmdline": "",
"cwd": "/",
"disk_bytes_read": "0",
"disk_bytes_written": "0",
"egid": "0",
"euid": "0",
"gid": "0",
"ipc_namespace": "4026531839",
"mnt_namespace": "4026531840",
"name": "migration/0",
"net_namespace": "4026531957",
"nice": "0",
"on_disk": "-1",
"parent": "2",
"path": "",
"pgroup": "0",
"pid": "9",
"pid_namespace": "4026531836",
"resident_size": "",
"root": "/",
"sgid": "0",
"start_time": "0",
"state": "S",
"suid": "0",
"system_time": "2",
"threads": "1",
"total_size": "",
"uid": "0",
"user_namespace": "4026531837",
"user_time": "0",
"uts_namespace": "4026531838",
"wired_size": "0"
}
},
"predecoder": {
"hostname": "manager"
},
"location": "osquery"
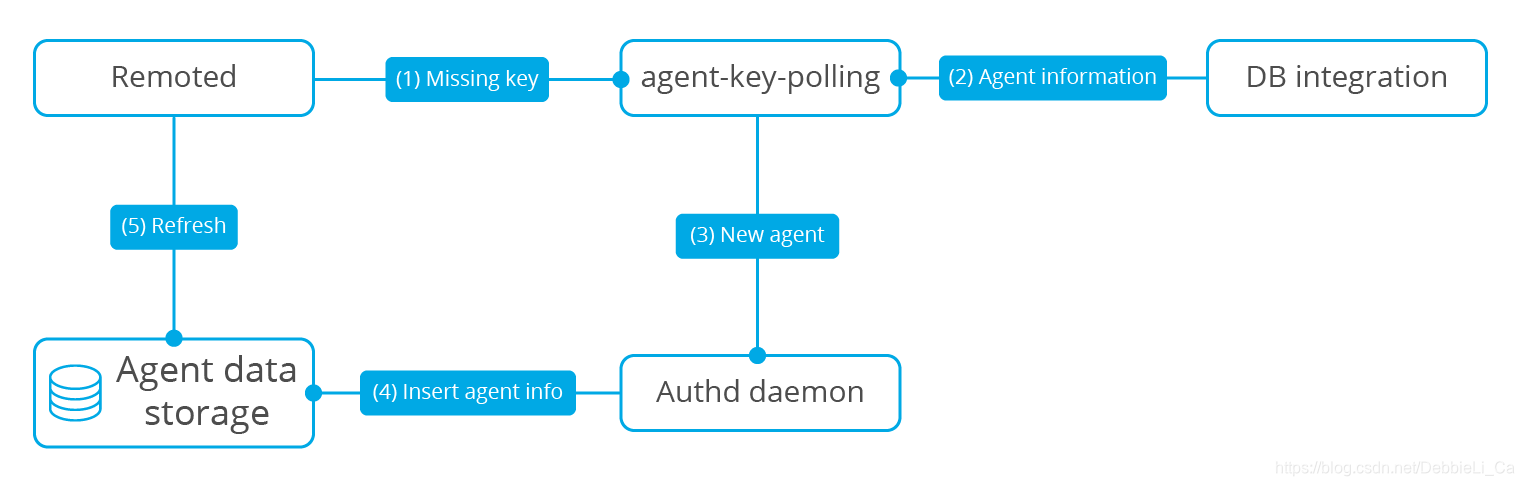
Agent key polling
polling:轮询,由CPU定时发出询问,依序询问每一个周边设备是否需要其服务,有即给予服务,服务结束后再问下一个周边,接着不断周而复始
这个模块是获取到存储在外部数据库里的用户密钥





 本文介绍Wazuh安全监控系统的整体架构及其Agent端功能,包括日志收集、文件完整性监控、异常与恶意软件检测等。同时展示了如何配置远程接收系统日志及安全配置评估方法。
本文介绍Wazuh安全监控系统的整体架构及其Agent端功能,包括日志收集、文件完整性监控、异常与恶意软件检测等。同时展示了如何配置远程接收系统日志及安全配置评估方法。
















 2452
2452

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








