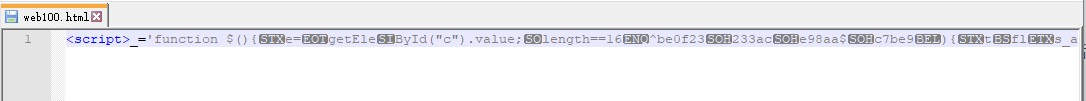
 我们将其放在phpstudy的www先,在浏览器中看看是个啥样子!
我们将其放在phpstudy的www先,在浏览器中看看是个啥样子!
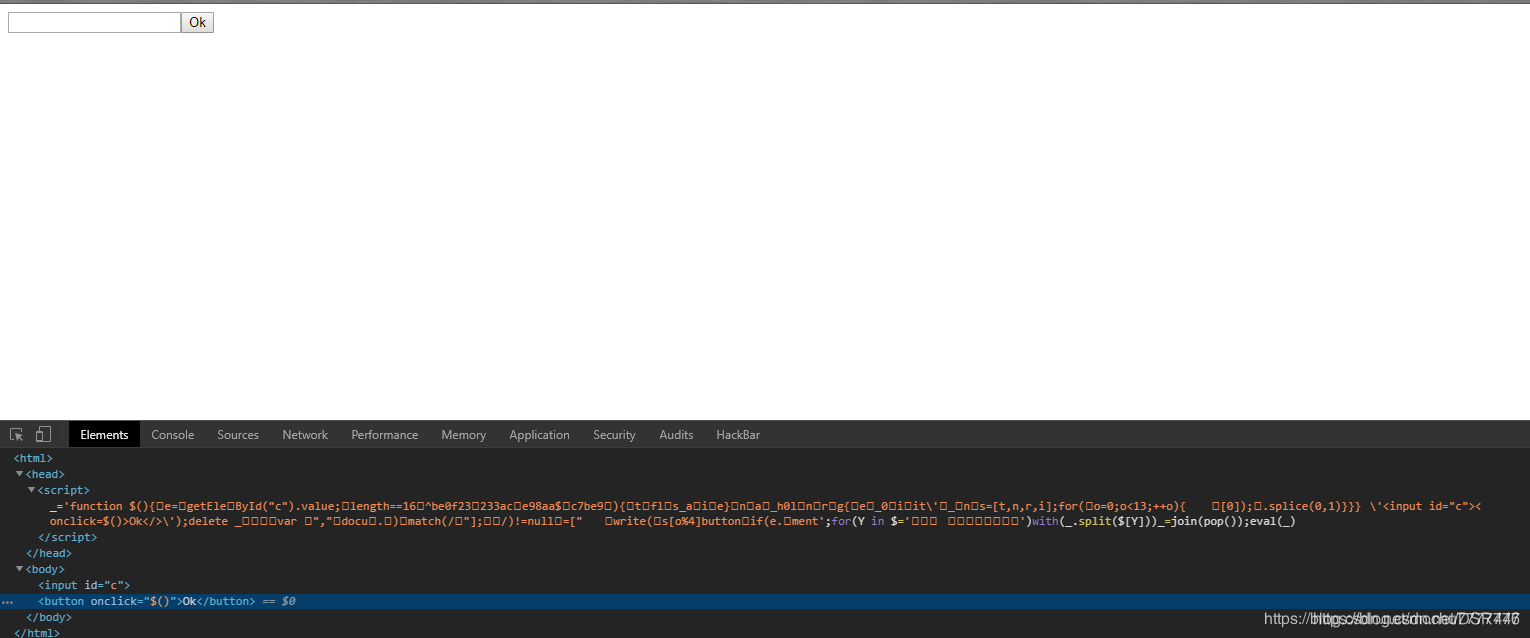 eval函数,这是执行函数;这里执行了_变量中的内容也就是’'中的内容,但是,要注意的是,它并没有执行()函数,仅仅执行了字符串而已(从而导致乱码),因而页面html页面没有任何显示,只显示了input标签的内容,但是我们想让源代码正常显示出来,不进行执行,那么,我们就用到了alert弹窗(将eval函数改为alert),将乱码的()函数,仅仅执行了字符串而已(从而导致乱码),因而页面html页面没有任何显示,只显示了input标签的内容,但是我们想让源代码正常显示出来,不进行执行,那么,我们就用到了alert弹窗(将eval函数改为alert),将乱码的()函数,仅仅执行了字符串而已(从而导致乱码),因而页面html页面没有任何显示,只显示了input标签的内容,但是我们想让源代码正常显示出来,不进行执行,那么,我们就用到了alert弹窗(将eval函数改为alert),将乱码的()函数源码完整显示出来
eval函数,这是执行函数;这里执行了_变量中的内容也就是’'中的内容,但是,要注意的是,它并没有执行()函数,仅仅执行了字符串而已(从而导致乱码),因而页面html页面没有任何显示,只显示了input标签的内容,但是我们想让源代码正常显示出来,不进行执行,那么,我们就用到了alert弹窗(将eval函数改为alert),将乱码的()函数,仅仅执行了字符串而已(从而导致乱码),因而页面html页面没有任何显示,只显示了input标签的内容,但是我们想让源代码正常显示出来,不进行执行,那么,我们就用到了alert弹窗(将eval函数改为alert),将乱码的()函数,仅仅执行了字符串而已(从而导致乱码),因而页面html页面没有任何显示,只显示了input标签的内容,但是我们想让源代码正常显示出来,不进行执行,那么,我们就用到了alert弹窗(将eval函数改为alert),将乱码的()函数源码完整显示出来
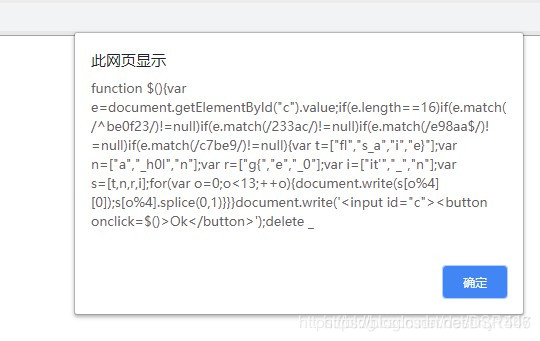
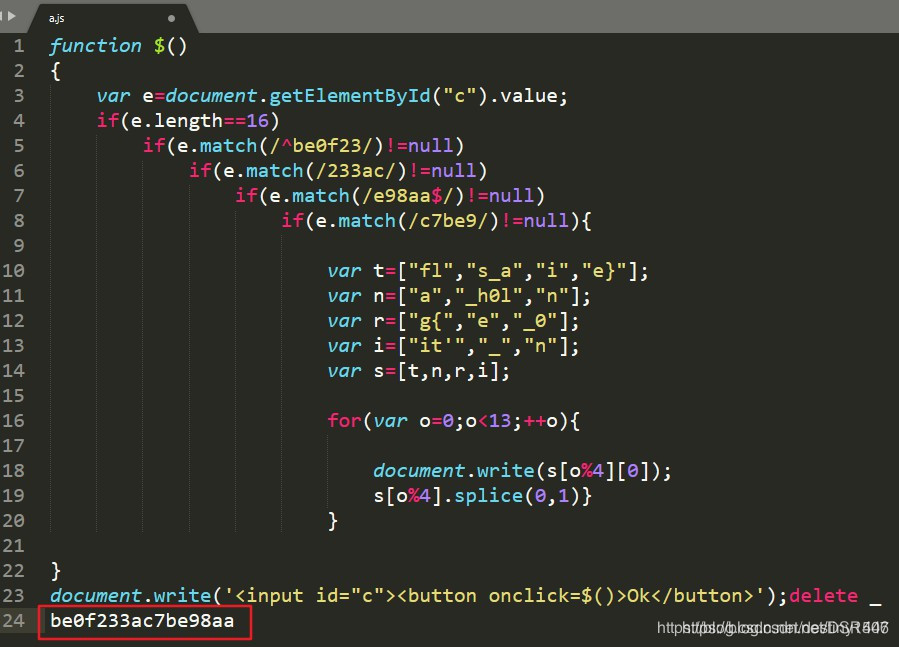 `e.length==16
`e.length==16
e.match(/^be0f23/)!=null
e.match(/233ac/)!=null
e.match(/e98aa/)!=nulle.match(/c7be9/)!=null‘这里又用到了正则表达式表示开头一定要匹配到be0f23,/)!=null
e.match(/c7be9/)!=null
`
这里又用到了正则表达式
^表示开头一定要匹配到be0f23,/)!=nulle.match(/c7be9/)!=null‘这里又用到了正则表达式表示开头一定要匹配到be0f23,表示结尾一定要匹配到e98aa,其它的只要匹配到就好,没有位置要求
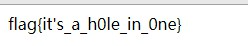
于是我们构造e的值
e=be0f233ac7be98aa





 本文探讨了在PHPStudy环境下利用Eval函数执行字符串内容的现象,及通过改用Alert函数使原本因执行而乱码的HTML源代码得以完整显示的方法。文中详细解释了如何构造特定字符串,并使用正则表达式进行匹配验证。
本文探讨了在PHPStudy环境下利用Eval函数执行字符串内容的现象,及通过改用Alert函数使原本因执行而乱码的HTML源代码得以完整显示的方法。文中详细解释了如何构造特定字符串,并使用正则表达式进行匹配验证。
















 1万+
1万+

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








