文章目录
新年快乐
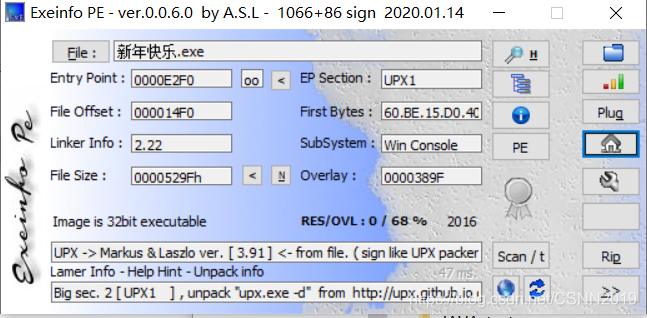
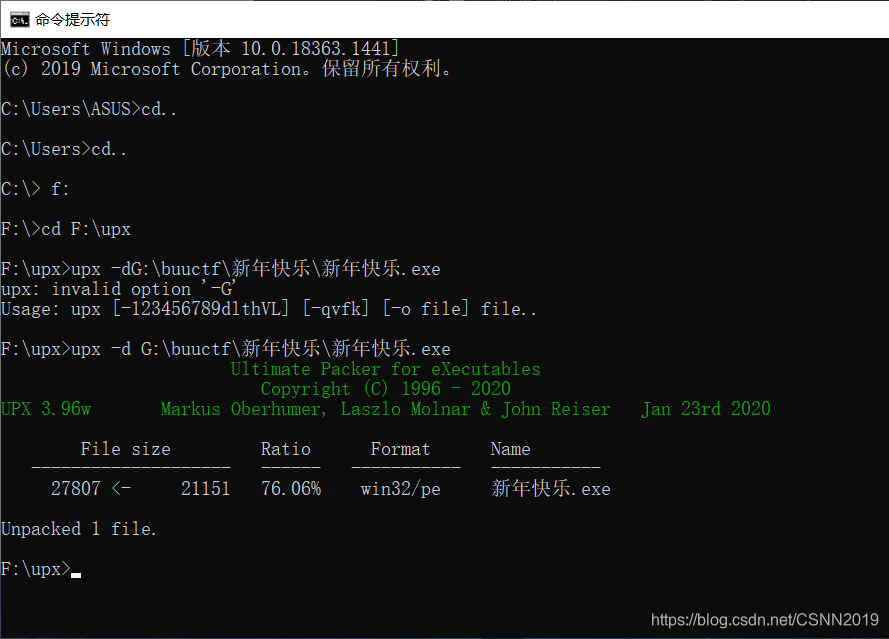
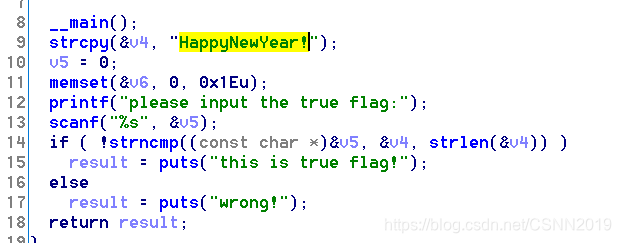
内涵的软件
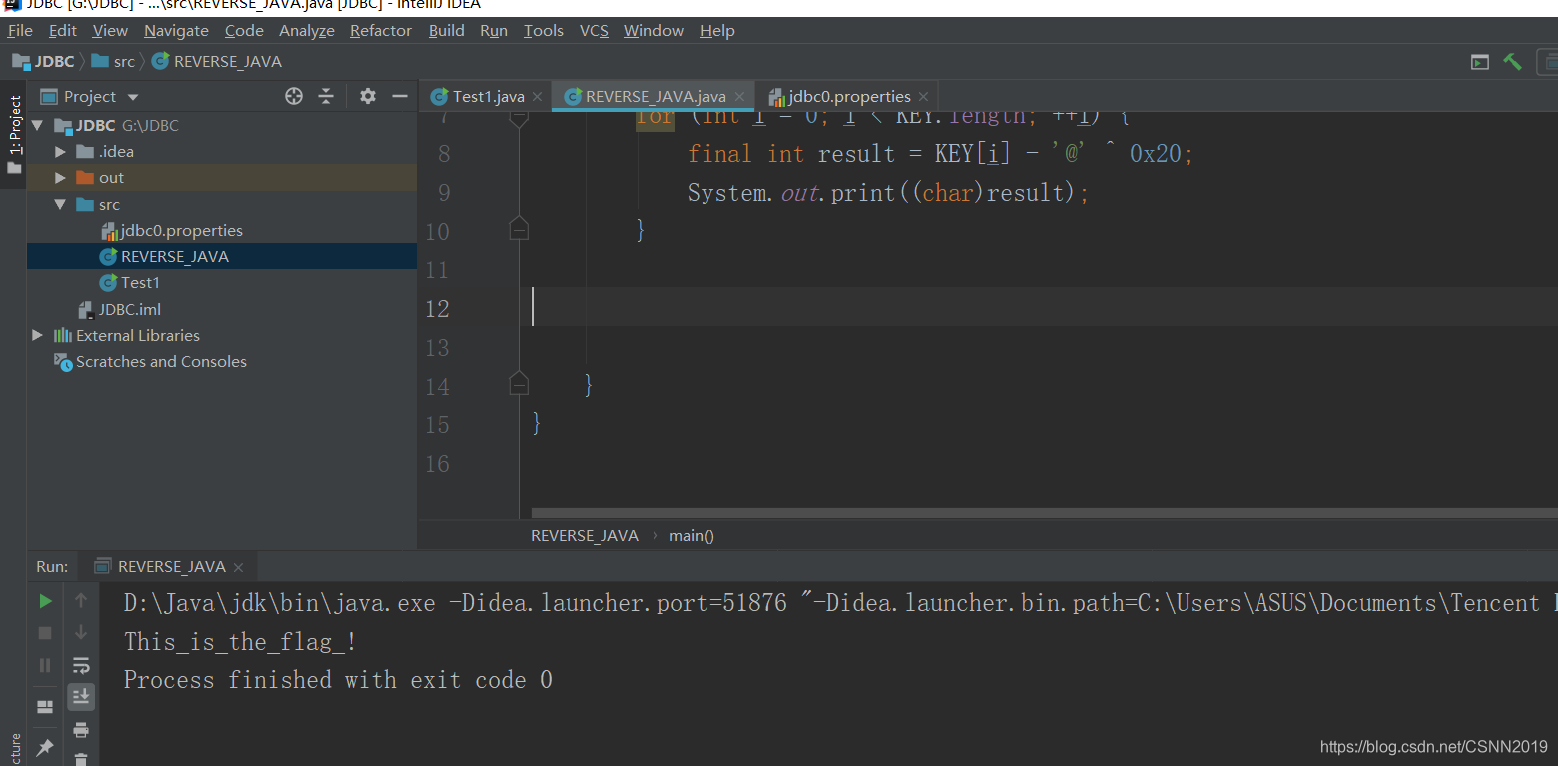
flag{49d3c93df25caad81232130f3d2ebfad}
Java逆向解密
import java.util.*;
public class Reverse
{
public static void main(final String[] args) {
final Scanner s = new Scanner(System.in);
System.out.println("Please input the flag \uff1a");
final String str = s.next();
System.out.println("Your input is \uff1a");
System.out.println(str);
final char[] stringArr = str.toCharArray();
Encrypt(stringArr);
}
public static void Encrypt(final char[] arr) {
final ArrayList<Integer> Resultlist = new ArrayList<Integer>();
for (int i = 0; i < arr.length; ++i) {
final int result = arr[i] + '@' ^ 0x20;
Resultlist.add(result);
}
final int[] KEY = { 180, 136, 137, 147, 191, 137, 147, 191, 148, 136, 133, 191, 134, 140, 129, 135, 191, 65 };
final ArrayList<Integer> KEYList = new ArrayList<Integer>();
for (int j = 0; j < KEY.length; ++j) {
KEYList.add(KEY[j]);
}
System.out.println("Result:");
if (Resultlist.equals(KEYList)) {
System.out.println("Congratulations\uff01");
}
else {
System.err.println("Error\uff01");
}
}
}
贴脚本:
public class REVERSE_JAVA {
public static void main(String[] args) {
final int[] KEY = { 180, 136, 137, 147, 191, 137, 147, 191, 148, 136, 133, 191, 134, 140, 129, 135, 191, 65 };
final ArrayList<Integer> Resultlist = new ArrayList<Integer>();
for (int i = 0; i < KEY.length; ++i) {
final int result = KEY[i] - '@' ^ 0x20;
System.out.print((char)result);
}
}
}
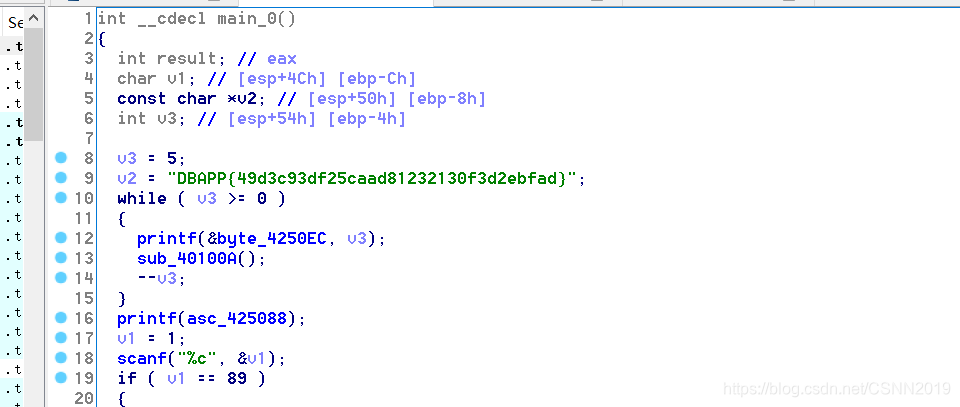
刮开有奖
sub_4010F0((int)&v7, 0, 10);(加密函数)
v7 = 90;
v8 = 74;
v9 = 83;
v10 = 'E';
v11 = 'C';
v12 = 'a';
v13 = 'N';
v14 = 72;
v15 = 51;
v16 = 110;
v17 = 103;
sub_4010F0((int)&v7, 0, 10);
int __cdecl sub_4010F0(int a1, int a2, int a3)
{
int result; // eax
int i; // esi
int v5; // ecx
int v6; // edx
result = a3;
for ( i = a2; i <= a3; a2 = i )
{
v5 = 4 * i;
v6 = *(_DWORD *)(4 * i + a1);
if ( a2 < result && i < result )
{
do
{
if ( v6 > *(_DWORD *)(a1 + 4 * result) )
{
if ( i >= result )
break;
++i;
*(_DWORD *)(v5 + a1) = *(_DWORD *)(a1 + 4 * result);
if ( i >= result )
break;
while ( *(_DWORD *)(a1 + 4 * i) <= v6 )
{
if ( ++i >= result )
goto LABEL_13;
}
if ( i >= result )
break;
v5 = 4 * i;
*(_DWORD *)(a1 + 4 * result) = *(_DWORD *)(4 * i + a1);
}
--result;
}
while ( i < result );
}
LABEL_13:
*(_DWORD *)(a1 + 4 * result) = v6;
sub_4010F0(a1, a2, i - 1);
result = a3;
++i;
}
return result;
}
照着加密函数写一下,本来想动调的,结果下了断点,鼠标和键盘都快搞炸了,这程序还是没法进行交互式进行。。。。。
#include <stdio.h>
#include <string.h>
int sub_4010F0(char*a1, int a2, int a3)
{
int result; // eax
int i; // esi
int v5; // ecx
int v6; // edx
result = a3;
for ( i = a2; i <= a3; a2 = i )
{
v5 = i;
v6 = a1[i];
if ( a2 < result && i < result )
{
do
{
if ( v6 > a1[result] )
{
if ( i >= result )
break;
++i;
a1[v5]= a1[result];
if ( i >= result )
break;
while ( a1[i] <= v6 )
{
if ( ++i >= result )
goto LABEL_13;
}
if ( i >= result )
break;
v5 = i;
a1[result] = a1[i];
}
--result;
}
while ( i < result );
}
LABEL_13:
a1[result]= v6;
sub_4010F0(a1, a2, i - 1);
result = a3;
++i;
}
return result;
}
int main()
{
char s[]="ZJSECaNH3ng";
printf("%s",s\n);
sub_4010F0(s,0,10);
printf("%s",s);
return 0;
}
运行结果:
ZJSECaNH3ng
3CEHJNSZagn
sub_401000((int)&v26, strlen(&v26));
v4 = sub_401000((int)&v26, strlen(&v26));
memset(&v26, 0, 0xFFFFu);
v27 = v21;
v26 = v20;
v28 = v22;
v5 = sub_401000((int)&v26, strlen(&v26));
_BYTE *__cdecl sub_401000(int a1, int a2)
{
int v2; // eax
int v3; // esi
size_t v4; // ebx
_BYTE *v5; // eax
_BYTE *v6; // edi
int v7; // eax
_BYTE *v8; // ebx
int v9; // edi
signed int v10; // edx
int v11; // edi
signed int v12; // eax
signed int v13; // esi
_BYTE *result; // eax
_BYTE *v15; // [esp+Ch] [ebp-10h]
_BYTE *v16; // [esp+10h] [ebp-Ch]
int v17; // [esp+14h] [ebp-8h]
int v18; // [esp+18h] [ebp-4h]
v2 = a2 / 3;
v3 = 0;
if ( a2 % 3 > 0 )
++v2;
v4 = 4 * v2 + 1;
v5 = malloc(v4);
v6 = v5;
v15 = v5;
if ( !v5 )
exit(0);
memset(v5, 0, v4);
v7 = a2;
v8 = v6;
v16 = v6;
if ( a2 > 0 )
{
while ( 1 )
{
v9 = 0;
v10 = 0;
v18 = 0;
do
{
if ( v3 >= v7 )
break;
++v10;
v9 = *(unsigned __int8 *)(v3++ + a1) | (v9 << 8);
}
while ( v10 < 3 );
v11 = v9 << 8 * (3 - v10);
v12 = 0;
v17 = v3;
v13 = 18;
do
{
if ( v10 >= v12 )
{
*((_BYTE *)&v18 + v12) = (v11 >> v13) & 0x3F;
v8 = v16;
}
else
{
*((_BYTE *)&v18 + v12) = 64;
}
*v8++ = byte_407830[*((char *)&v18 + v12)];
v13 -= 6;
++v12;
v16 = v8;
}
while ( v13 > -6 );
v3 = v17;
if ( v17 >= a2 )
break;
v7 = a2;
}
v6 = v15;
}
result = v6;
*v8 = 0;
return result;
}
找到一个数组:
*v8++ = byte_407830[*((char *)&v18 + v12)];
byte_407830 db 41h ; DATA XREF: sub_401000+C0↑r
.rdata:00407831 db 42h ; B
.rdata:00407832 db 43h ; C
.rdata:00407833 db 44h ; D
.rdata:00407834 db 45h ; E
.rdata:00407835 db 46h ; F
.rdata:00407836 db 47h ; G
.rdata:00407837 db 48h ; H
.rdata:00407838 db 49h ; I
.rdata:00407839 db 4Ah ; J
.rdata:0040783A db 4Bh ; K
.rdata:0040783B db 4Ch ; L
.rdata:0040783C db 4Dh ; M
.rdata:0040783D db 4Eh ; N
.rdata:0040783E db 4Fh ; O
.rdata:0040783F db 50h ; P
.rdata:00407840 db 51h ; Q
.rdata:00407841 db 52h ; R
.rdata:00407842 db 53h ; S
.rdata:00407843 db 54h ; T
.rdata:00407844 db 55h ; U
.rdata:00407845 db 56h ; V
.rdata:00407846 db 57h ; W
.rdata:00407847 db 58h ; X
.rdata:00407848 db 59h ; Y
.rdata:00407849 db 5Ah ; Z
.rdata:0040784A db 61h ; a
.rdata:0040784B db 62h ; b
.rdata:0040784C db 63h ; c
.rdata:0040784D db 64h ; d
.rdata:0040784E db 65h ; e
.rdata:0040784F db 66h ; f
.rdata:00407850 db 67h ; g
.rdata:00407851 db 68h ; h
.rdata:00407852 db 69h ; i
.rdata:00407853 db 6Ah ; j
.rdata:00407854 db 6Bh ; k
.rdata:00407855 db 6Ch ; l
.rdata:00407856 db 6Dh ; m
.rdata:00407857 db 6Eh ; n
.rdata:00407858 db 6Fh ; o
.rdata:00407859 db 70h ; p
.rdata:0040785A db 71h ; q
.rdata:0040785B db 72h ; r
.rdata:0040785C db 73h ; s
.rdata:0040785D db 74h ; t
.rdata:0040785E db 75h ; u
.rdata:0040785F db 76h ; v
.rdata:00407860 db 77h ; w
.rdata:00407861 db 78h ; x
.rdata:00407862 db 79h ; y
.rdata:00407863 db 7Ah ; z
.rdata:00407864 db 30h ; 0
.rdata:00407865 db 31h ; 1
.rdata:00407866 db 32h ; 2
.rdata:00407867 db 33h ; 3
.rdata:00407868 db 34h ; 4
.rdata:00407869 db 35h ; 5
.rdata:0040786A db 36h ; 6
.rdata:0040786B db 37h ; 7
.rdata:0040786C db 38h ; 8
.rdata:0040786D db 39h ; 9
.rdata:0040786E db 2Bh ; +
.rdata:0040786F db 2Fh ; /
.rdata:00407870 db 3Dh ; =
很正常的base64,顺序没变,外加后面
核心
if ( String == v7 + 34
&& v19 == v11
&& 4 * v20 - 141 == 3 * v9
&& v21 / 4 == 2 * (v14 / 9)
&& !strcmp(v4, "ak1w")
&& !strcmp(v5, "V1Ax") )
v4和v5都是经过base64编码后的字符串,所以我们分别对ak1w和V1Ax进行解码即可,分别为jMp和WP1
仔细观察后,也就是
UJWP1jMp
先给出一个字符串,然后有两个经过base64加密,然后再来凑起来






















 1054
1054

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










