lvs配置方法
- nat模式配置
| ip类型 | ip地址 |
|---|---|
| VIP仅主机模式 | 192.168.96.134 |
| DIP | 192.168.149.143 |
| host1IP | 192.168.149.140 |
| host2IP | 192.168.149.137 |
host1配置
[root@host1 ~]# systemctl stop firewalld.service
[root@host1 ~]# setenforce 0
[root@host1 ~]# yum -y install httpd
[root@host1 ~]# systemctl start httpd
[root@host1 ~]# echo "1" > /var/www/html/index.html
生成httpds
[root@host1 ~]# mkdir /etc/pki/CA
[root@host1 ~]# cd /etc/pki/CA
[root@host1 CA]# mkdir private
[root@host1 CA]# (umask 077;openssl genrsa -out private/cakey.pem 2048)
Generating RSA private key, 2048 bit long modulus (2 primes)
.....................................................................................................+++++
.......+++++
e is 65537 (0x010001)
[root@host1 CA]# openssl req -new -x509 -key private/cakey.pem -out cacert.pem -days 365
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:HB
Locality Name (eg, city) [Default City]:WH
Organization Name (eg, company) [Default Company Ltd]:xkq
Organizational Unit Name (eg, section) []:xkq
Common Name (eg, your name or your server's hostname) []:xkq.com
Email Address []:1@1.com
[root@host1 CA]# mkdir certs newcerts crl
[root@host1 CA]# touch index.txt && echo 01 > serial
[root@host1 CA]# (umask 077;openssl genrsa -out httpd.key 2048)
Generating RSA private key, 2048 bit long modulus (2 primes)
......+++++
...........................................+++++
e is 65537 (0x010001)
[root@host1 CA]# openssl req -new -key httpd.key -days 365 -out httpd.csr
Ignoring -days; not generating a certificate
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:HB
Locality Name (eg, city) [Default City]:WH
Organization Name (eg, company) [Default Company Ltd]:xkq
Organizational Unit Name (eg, section) []:xkq
Common Name (eg, your name or your server's hostname) []:xkq.com
Email Address []:1@1.com
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
[root@host1 CA]# openssl ca -in httpd.csr -out httpd.crt -days 365
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 1 (0x1)
Validity
Not Before: Jun 14 12:04:15 2021 GMT
Not After : Jun 14 12:04:15 2022 GMT
Subject:
countryName = CN
stateOrProvinceName = HB
organizationName = xkq
organizationalUnitName = xkq
commonName = xkq.com
emailAddress = 1@1.com
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
1E:D6:51:6F:21:A7:7D:A7:FF:06:D4:6D:13:85:11:50:6C:FD:D5:8C
X509v3 Authority Key Identifier:
keyid:2B:BA:85:7C:6B:8E:0C:74:24:B2:E0:CF:83:43:9D:21:C3:8D:DF:95
Certificate is to be certified until Jun 14 12:04:15 2022 GMT (365 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
安装ssl模板
[root@host1 ~]# dnf -y install mod_ssl
[root@host1 CA]# mv httpd.key httpd.crt /etc/httpd/
[root@host1 CA]# cd /etc/httpd/conf.d/
[root@host1 conf.d]# vim ssl.conf
修改路径
......
SSLCertificateFile /etc/httpd/httpd.crt
SSLCertificateKeyFile /etc/httpd/httpd.key
......
重启httpd
[root@host1 conf.d]# systemctl restart httpd
[root@host1 CA]# mv httpd.key httpd.crt /etc/httpd/
[root@host1 CA]# scp /etc/httpd/httpd.crt 192.168.149.137:/etc/httpd/
root@192.168.149.137's password:
httpd.crt 100% 4495 2.5MB/s 00:00
[root@host1 CA]# scp /etc/httpd/httpd.key 192.168.149.137:/etc/httpd/
root@192.168.149.137's password:
httpd.key 100% 1675 1.6MB/s 00:00
将网关改为调度器的ip
[root@host1 ~]# vim /etc/sysconfig/network-scripts/ifcfg-ens160
TYPE=Ethernet
OTPROTO=static
NAME=ens160
DEVICE=ens160
ONBOOT=yes
IPADDR=192.168.149.140
PREFIX=24
GATEWAY=192.168.149.143
DNS1=114.114.114.114
[root@host1 ~]# ifdown ens160;ifup ens160
host2配置
[root@host2 ~]# systemctl stop firewalld
[root@host2 ~]# setenforce 0
[root@host2 ~]# yum -y install httpd
[root@host2 ~]# systemctl start httpd
[root@host1 ~]# echo "2" > /var/www/html/index.html
[root@host2 ~]# dnf -y install mod_ssl
[root@host2 ~]# cd /etc/httpd/conf.d/
[root@host2 conf.d]# vim ssl.conf
修改路径
......
SSLCertificateFile /etc/httpd/httpd.crt
SSLCertificateKeyFile /etc/httpd/httpd.key
......
重启httpd
[root@host2 conf.d]# systemctl restart httpd
将网关改为调度器的ip
[root@host2 ~]# vim /etc/sysconfig/network-scripts/ifcfg-ens160
TYPE=Ethernet
OTPROTO=static
NAME=ens160
DEVICE=ens160
ONBOOT=yes
IPADDR=192.168.149.137
PREFIX=24
GATEWAY=192.168.149.143
DNS1=114.114.114.114
[root@host2 ~]# ifdown ens160;ifup ens160
调度器配置
[root@lb ~]# systemctl stop firewalld
[root@lb ~]# setenforce 0
[root@lb ~]# yum -y install ipvsadm
开启 IP转发 功能
[root@lb ~]# echo 'net.ipv4.ip_forward = 1' > /etc/sysctl.conf
[root@lb ~]# sysctl -p
net.ipv4.ip_forward = 1
添加并保持规则
[root@lb ~]# ipvsadm -A -t 192.168.96.132:443 -s rr
[root@lb ~]# ipvsadm -a -t 192.168.96.132:443 -r 192.168.149.137:443 -m
[root@lb ~]# ipvsadm -a -t 192.168.96.132:443 -r 192.168.149.140:443 -m
[root@lb ~]# ipvsadm -A -t 192.168.96.132:80 -s rr
[root@lb ~]# ipvsadm -a -t 192.168.96.132:80 -r 192.168.149.140:80 -m
[root@lb ~]# ipvsadm -a -t 192.168.96.132:80 -r 192.168.149.137:80 -m
[root@lb ~]# ipvsadm -Sn > /etc/sysconfig/ipvsadm
[root@lb ~]# cat /etc/sysconfig/ipvsadm
-A -t 192.168.96.134:80 -s rr
-a -t 192.168.96.134:80 -r 192.168.149.137:80 -m -w 1
-a -t 192.168.96.134:80 -r 192.168.149.140:80 -m -w 1
-A -t 192.168.96.134:443 -s rr
-a -t 192.168.96.134:443 -r 192.168.149.137:443 -m -w 1
-a -t 192.168.96.134:443 -r 192.168.149.140:443 -m -w 1
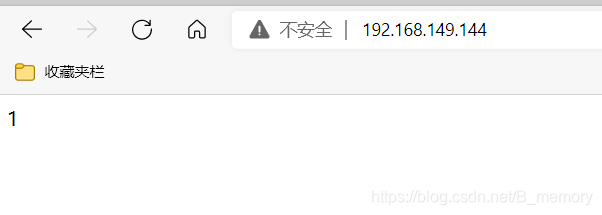
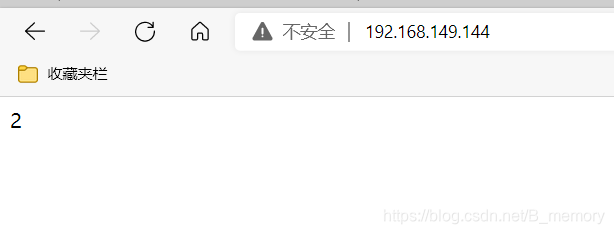
测试
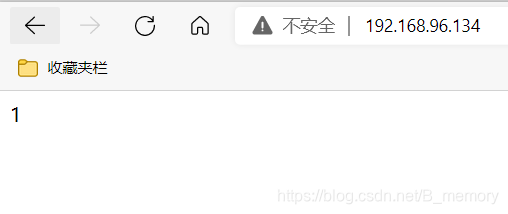
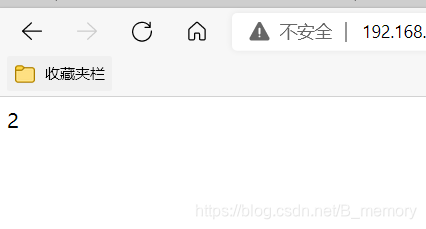
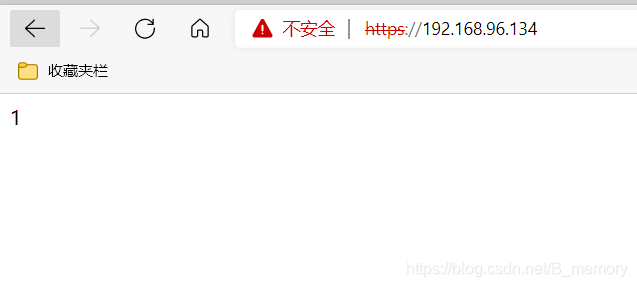
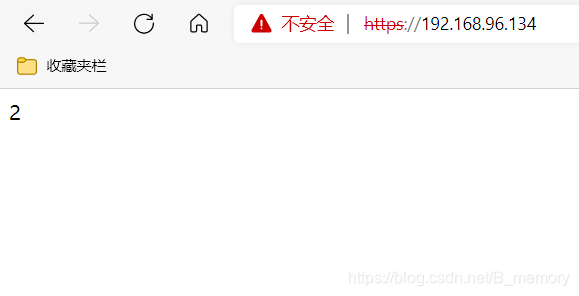
dr模式
| ip类型 | ip地址 |
|---|---|
| VIP虚拟的 | 192.168.149.144 |
| DIP | 192.168.149.143 |
| host1IP | 192.168.149.140 |
| host2IP | 192.168.149.137 |
host1配置
[root@host1 ~]# systemctl stop firewalld.service
[root@host1 ~]# setenforce 0
[root@host1 ~]# yum -y install httpd
[root@host1 ~]# systemctl start httpd
[root@host1 ~]# echo "1" > /var/www/html/index.html
生成httpds
[root@host1 ~]# mkdir /etc/pki/CA
[root@host1 ~]# cd /etc/pki/CA
[root@host1 CA]# mkdir private
[root@host1 CA]# (umask 077;openssl genrsa -out private/cakey.pem 2048)
Generating RSA private key, 2048 bit long modulus (2 primes)
.....................................................................................................+++++
.......+++++
e is 65537 (0x010001)
[root@host1 CA]# openssl req -new -x509 -key private/cakey.pem -out cacert.pem -days 365
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:HB
Locality Name (eg, city) [Default City]:WH
Organization Name (eg, company) [Default Company Ltd]:xkq
Organizational Unit Name (eg, section) []:xkq
Common Name (eg, your name or your server's hostname) []:xkq.com
Email Address []:1@1.com
[root@host1 CA]# mkdir certs newcerts crl
[root@host1 CA]# touch index.txt && echo 01 > serial
[root@host1 CA]# (umask 077;openssl genrsa -out httpd.key 2048)
Generating RSA private key, 2048 bit long modulus (2 primes)
......+++++
...........................................+++++
e is 65537 (0x010001)
[root@host1 CA]# openssl req -new -key httpd.key -days 365 -out httpd.csr
Ignoring -days; not generating a certificate
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:HB
Locality Name (eg, city) [Default City]:WH
Organization Name (eg, company) [Default Company Ltd]:xkq
Organizational Unit Name (eg, section) []:xkq
Common Name (eg, your name or your server's hostname) []:xkq.com
Email Address []:1@1.com
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
[root@host1 CA]# openssl ca -in httpd.csr -out httpd.crt -days 365
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 1 (0x1)
Validity
Not Before: Jun 14 12:04:15 2021 GMT
Not After : Jun 14 12:04:15 2022 GMT
Subject:
countryName = CN
stateOrProvinceName = HB
organizationName = xkq
organizationalUnitName = xkq
commonName = xkq.com
emailAddress = 1@1.com
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
1E:D6:51:6F:21:A7:7D:A7:FF:06:D4:6D:13:85:11:50:6C:FD:D5:8C
X509v3 Authority Key Identifier:
keyid:2B:BA:85:7C:6B:8E:0C:74:24:B2:E0:CF:83:43:9D:21:C3:8D:DF:95
Certificate is to be certified until Jun 14 12:04:15 2022 GMT (365 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
安装ssl模板
[root@host1 ~]# dnf -y install mod_ssl
[root@host1 CA]# mv httpd.key httpd.crt /etc/httpd/
[root@host1 CA]# cd /etc/httpd/conf.d/
[root@host1 conf.d]# vim ssl.conf
修改路径
......
SSLCertificateFile /etc/httpd/httpd.crt
SSLCertificateKeyFile /etc/httpd/httpd.key
......
重启httpd
[root@host1 conf.d]# systemctl restart httpd
将证书传给host2
[root@host1 CA]# scp /etc/httpd/httpd.crt 192.168.149.137:/etc/httpd/
root@192.168.149.137's password:
httpd.crt 100% 4495 2.5MB/s 00:00
[root@host1 CA]# scp /etc/httpd/httpd.key 192.168.149.137:/etc/httpd/
root@192.168.149.137's password:
httpd.key 100% 1675 1.6MB/s 00:00
[root@host1 httpd]# ifconfig lo:0 192.168.149.144/32 broadcast 192.168.149.144 up
[root@host1 httpd]# route add -host 192.168.149.144 dev lo:0
[root@host1 ~]# vim /etc/sysconfig/network-scripts/ifcfg-ens160
TYPE=Ethernet
OTPROTO=static
NAME=ens160
DEVICE=ens160
ONBOOT=yes
IPADDR=192.168.149.140
PREFIX=24
GATEWAY=192.168.149.2
DNS1=114.114.114.114
[root@host1 ~]# cd /etc/httpd/
[root@host1 httpd]# cat >> /etc/sysctl.conf <<EOF
> net.ipv4.conf.all.arp_ignore=1
> net.ipv4.conf.all.arp_announce=2
> EOF
[root@host1 httpd]# sysctl -p
net.ipv4.conf.all.arp_ignore = 1
net.ipv4.conf.all.arp_announce = 2
[root@host1 ~]# ifdown ens160;ifup ens160
host2配置
[root@host2 ~]# systemctl stop firewalld
[root@host2 ~]# setenforce 0
[root@host2 ~]# yum -y install httpd
[root@host2 ~]# systemctl start httpd
[root@host1 ~]# echo "2" > /var/www/html/index.html
[root@host2 ~]# dnf -y install mod_ssl
[root@host2 ~]# cd /etc/httpd/conf.d/
[root@host2 conf.d]# vim ssl.conf
修改路径
......
SSLCertificateFile /etc/httpd/httpd.crt
SSLCertificateKeyFile /etc/httpd/httpd.key
......
重启httpd
[root@host2 conf.d]# systemctl restart httpd
[root@host2 ~]# ifconfig lo:0 192.168.149.144/32 broadcast 192.168.149.144 up
[root@host2 ~]# route add -host 192.168.149.144 dev lo:0
[root@host2 ~]# vim /etc/sysconfig/network-scripts/ifcfg-ens160
TYPE=Ethernet
OTPROTO=static
NAME=ens160
DEVICE=ens160
ONBOOT=yes
IPADDR=192.168.149.137
PREFIX=24
GATEWAY=192.168.149.2
DNS1=114.114.114.114
[root@host2 ~]# ifdown ens160;ifup ens160
[root@host2 ~]# cat >> /etc/sysctl.conf <<EOF
> net.ipv4.conf.all.arp_ignore=1
> net.ipv4.conf.all.arp_announce=2
> EOF
[root@host2 ~]# sysctl -p
net.ipv4.conf.all.arp_ignore = 1
net.ipv4.conf.all.arp_announce = 2
调度器配置
[root@lb ~]# systemctl stop firewalld
[root@lb ~]# setenforce 0
[root@lb ~]# yum -y install ipvsadm
[root@lb ~]# vim /etc/sysconfig/network-scripts/ifcfg-ens160
TYPE=Ethernet
BOOTPROTO=static
NAME=ens160
DEVICE=ens160
ONBOOT=yes
IPADDR0=192.168.149.143
PREFIX0=24
IPADDR1=192.168.149.144
PREFIX1=24
GATEWAY=192.168.149.2
DNS1=114.114.114.114
[root@lb ~]# ifdown ens160;ifup ens160
添加规则
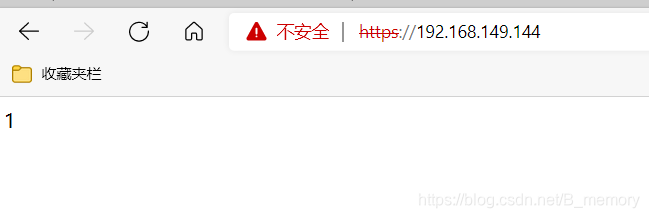
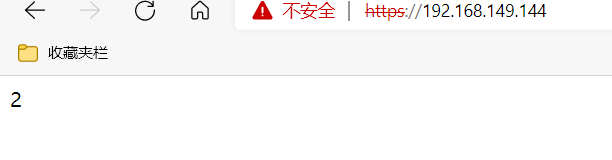
[root@lb ~]# ipvsadm -A -t 192.168.149.144:80 -s rr
[root@lb ~]# ipvsadm -a -t 192.168.149.144:80 -r 192.168.149.140:80 -g
[root@lb ~]# ipvsadm -a -t 192.168.149.144:80 -r 192.168.149.137:80 -g
[root@lb ~]# ipvsadm -A -t 192.168.149.144:443 -s rr
[root@lb ~]# ipvsadm -a -t 192.168.149.144:443 -r 192.168.149.137:443 -g
[root@lb ~]# ipvsadm -a -t 192.168.149.144:443 -r 192.168.149.140:443 -g
[root@lb ~]# ipvsadm -Ln
IP Virtual Server version 1.2.1 (size=4096)
Prot LocalAddress:Port Scheduler Flags
-> RemoteAddress:Port Forward Weight ActiveConn InActConn
TCP 192.168.149.144:80 rr
-> 192.168.149.137:80 Route 1 0 0
-> 192.168.149.140:80 Route 1 0 0
TCP 192.168.149.144:443 rr
-> 192.168.149.137:443 Route 1 0 0
-> 192.168.149.140:443 Route 1 0 0
haproxy配置
[root@lb ~]# yum -y install make gcc pcre-devel bzip2-devel openssl-devel systemd-devel
[root@lb ~]# useradd -r -M -s /sbin/nologin haproxy
[root@lb ~]# useradd -r -M -s /sbin/nologin haproxy
[root@lb ~]# tar xf haproxy-v2.3.0.tar.gz
[root@lb ~]# cd haproxy-2.3.0/
[root@lb haproxy-2.3.0]# make clean
[root@lb haproxy-2.3.0]# make -j $(grep 'processor' /proc/cpuinfo |wc -l) \
> TARGET=linux-glibc \
> USE_OPENSSL=1 \
> USE_ZLIB=1 \
> USE_PCRE=1 \
> USE_SYSTEMD=1
[root@lb haproxy-2.3.0]# make install PREFIX=/usr/local/haproxy
[root@lb haproxy-2.3.0]# echo "export PATH=/usr/local/haproxy/sbin:$PATH">/etc/profile.d/haproxy.sh
[root@lb haproxy-2.3.0]# . /etc/profile.d/haproxy.sh
[root@lb haproxy-2.3.0]# which haproxy
/usr/local/haproxy/sbin/haproxy
[root@lb haproxy-2.3.0]# echo 'net.ipv4.ip_nonlocal_bind = 1' >> /etc/sysctl.conf
[root@lb haproxy-2.3.0]# echo 'net.ipv4.ip_forward = 1' >> /etc/sysctl.conf
[root@lb haproxy-2.3.0]# sysctl -p
net.ipv4.ip_forward = 1
net.ipv4.ip_nonlocal_bind = 1
[root@lb haproxy-2.3.0]# mkdir /etc/haproxy
[root@lb haproxy-2.3.0]# cat > /etc/haproxy/haproxy.cfg <<EOF
> #--------------全局配置----------------
> global
> log 127.0.0.1 local0 info
> #log loghost local0 info
> maxconn 20480
> #chroot /usr/local/haproxy
> pidfile /var/run/haproxy.pid
> #maxconn 4000
> user haproxy
> group haproxy
> daemon
> #---------------------------------------------------------------------
> #common defaults that all the 'listen' and 'backend' sections will
> #use if not designated in their block
> #---------------------------------------------------------------------
> defaults
> mode http
> log global
> option dontlognull
> option httpclose
> option httplog
> #option forwardfor
> option redispatch
> balance roundrobin
> timeout connect 10s
> timeout client 10s
> timeout server 10s
> timeout check 10s
> maxconn 60000
> retries 3
> #--------------统计页面配置------------------
> listen admin_stats
> bind 0.0.0.0:8189
> stats enable
> mode http
> log global
> stats uri /haproxy_stats
> stats realm Haproxy\ Statistics
> stats auth admin:admin
> #stats hide-version
> stats admin if TRUE
> stats refresh 30s
> #---------------web设置-----------------------
> listen webcluster
> bind 0.0.0.0:80
> mode http
> #option httpchk GET /index.html
> log global
> maxconn 3000
> balance roundrobin
> cookie SESSION_COOKIE insert indirect nocache
> server web01 192.168.149.140:80 check inter 2000 fall 5
> server web02 192.168.149.137:80 check inter 2000 fall 5
> EOF
- haproxy.service文件编写
[root@lb haproxy-2.3.0]# cat > /usr/lib/systemd/system/haproxy.service <<EOF
> [Unit]
> Description=HAProxy Load Balancer
> After=syslog.target network.target
>
> [Service]
> ExecStartPre=/usr/local/haproxy/sbin/haproxy -f /etc/haproxy/haproxy.cfg -c -q
> ExecStart=/usr/local/haproxy/sbin/haproxy -Ws -f /etc/haproxy/haproxy.cfg -p /var/run/haproxy.pid
> ExecReload=/bin/kill -USR2 $MAINPID
>
> [Install]
> WantedBy=multi-user.target
> EOF
[root@lb haproxy-2.3.0]# systemctl daemon-reload
- 启用日志
[root@lb haproxy-2.3.0]# vim /etc/rsyslog.conf
local0.* /var/log/boot.log
[root@lb haproxy-2.3.0]# systemctl restart rsyslog
- 重启服务
[root@lb haproxy-2.3.0]# systemctl restart haproxy
[root@lb haproxy-2.3.0]# ss -antl
State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
LISTEN 0 128 0.0.0.0:80 0.0.0.0:*
LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
LISTEN 0 128 0.0.0.0:8189 0.0.0.0:*
LISTEN 0 128 [::]:22 [::]:*
测试
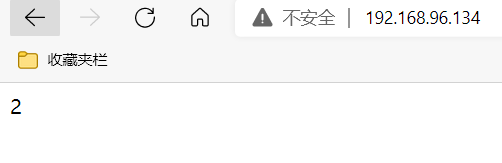
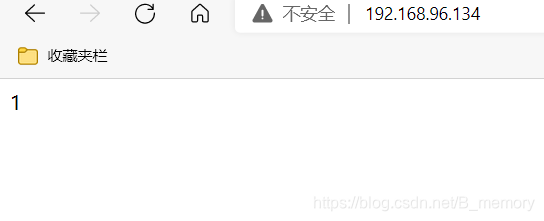
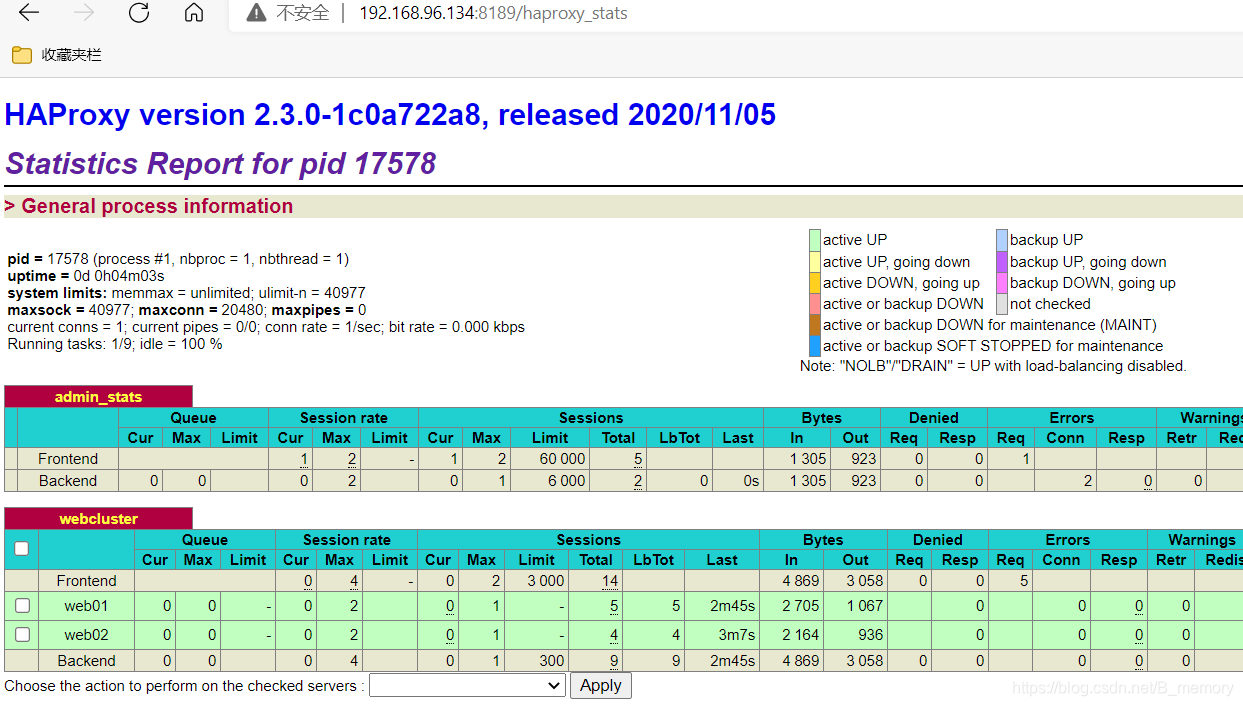




 本文详细介绍了LVS的nat模式和dr模式的配置步骤,包括host1和host2的设置,以及调度器的配置。在nat模式下,重点讲解了调度器的配置和测试过程;而在dr模式中,同样涵盖了主机配置和测试环节。此外,还阐述了haproxy的配置,包括haproxy.service文件的编写、启用日志和重启服务的步骤,以实现高可用负载均衡。
本文详细介绍了LVS的nat模式和dr模式的配置步骤,包括host1和host2的设置,以及调度器的配置。在nat模式下,重点讲解了调度器的配置和测试过程;而在dr模式中,同样涵盖了主机配置和测试环节。此外,还阐述了haproxy的配置,包括haproxy.service文件的编写、启用日志和重启服务的步骤,以实现高可用负载均衡。
















 1625
1625

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








