As the DIS of the ISO21434 is finally available. This is a collection of the insights and discussions we had while reading it. Read now inside the ISO/SAE 21434.
Work Products
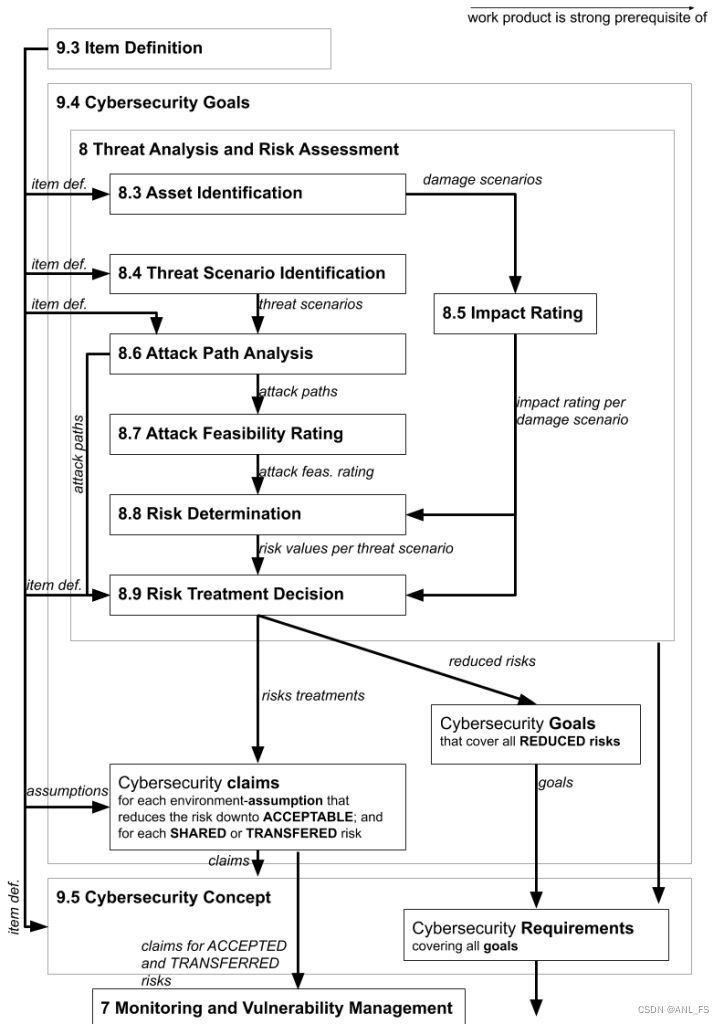
The DIS of ISO21434 distinguishes the three kinds of product phases concept phase, development phase, and operation phase. The general endeavor of performing a TARA is described in chapter 8. The concept phase, as described in chapter 9, consists of defining the item (9.3 Item Definition), finding Cybersecurity Goals (section 9.4) and bundling them into a whole Cybersecurity Concept (section 9.5). The major part of identifying Cybersecurity Goals is to invoke the TARA that is described in chapter 8.
The main steps when performing an ISO21434-conform TARA are (in order of an idealized linear execution):
Item Definition (section 9.3)
Asset Identification (section 8.3)
Threat Scenario Identification (section 8.4)
Impact Rating (section 8.5)
Attack Path Analysis (section 8.6)
Attack Feasibility Rating (section 8.7)
Risk Determination (section 8.8)
Risk Treatment Decision (section 8.9)
Cybersecurity Goals [RQ-09-07]
Cybersecurity Claims [RQ-09-08]
Cybersecurity Concept (section 9.5)
Insights
As this place is a living document, we are continuously adding the questions and discussions that arise. Here you go with some of them.
How to identify relevant Assets according to ISO 21434?
In Clause 8.3, the DIS of ISO21434 allows to enumerate the relevant assets with a variety of methods. As examples, it suggests to enumerate them by their impact rating, or threat scenarios, or even using predefined catalogues.
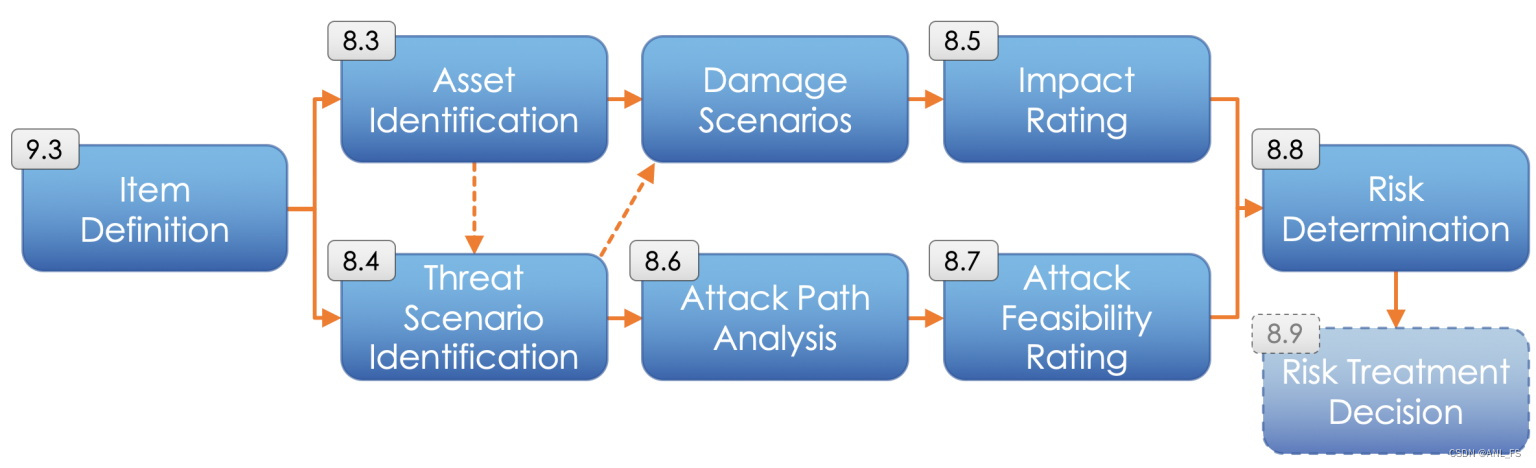
Notably, ISO21434 includes the Damage Scenarios as a result of the Asset Identification. As a result, in our figure above between Asset Identification, Threat Scenario Identification and Damage Scenario Identification; the arrows can actually go in various ways, depending on the applied method.
转载于:Inside the ISO/SAE 21434 – YSEC
如果有ISO/SAE 21434标准相关的技术或认证问题,大家可以随时与我联系(微信号:anling_service 电话:13699224050)。























 646
646

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








