1.逆向目标
声明:本文只作学习研究,禁止用于非法用途,否则后果自负,如有侵权,请告知删除,谢谢!(手动狗头)
(PS:wc,昨天才刚刚用了抓个包,今天微信就封号了,诶。兄弟们还是小心为妙)
我们要抓的是捡漏专区里的商品

2.抓包分析逆向参数

首先请求头中有个时间戳要搞

请求体里有个data


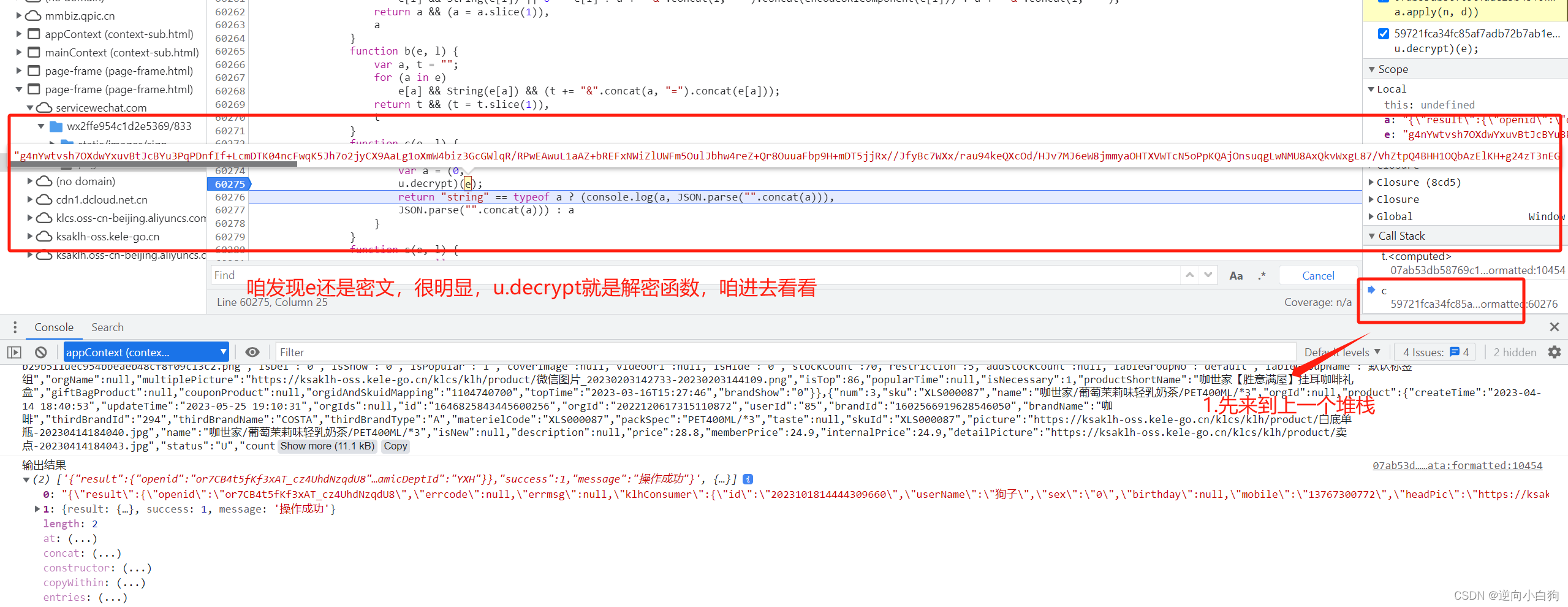
3.寻找加密函数位置


发现d就是咱们一直输出的明文结果,咱们直接在上面插桩,输出d


很明显,咱需要的解密函数就是u.decrypt,打印下
发现定位到a.decrypt,这不知道为啥前端程序员要先base64解码后又base64编码,最后aes解密

咱先把那key和iv搞到,往下看看

诶,发现都一样,那咱就猜想,咱的data和timestamp是先aes加密再base64编码,打印下看看
import base64
from Crypto.Cipher import AES
import time
from Crypto.Util.Padding import pad, unpad
t = str(int(time.time() * 1000))
key = b"qP2$bG9;vA0^uW0:"
iv = b"qP2$bG9;vA0^uW0:"
aes = AES.new(key, AES.MODE_CBC, iv)
print(aes.decrypt(base64.b64decode('llUt60iVpv30MUke6w+TN+b6yBdJJKw4JZ4Uavfazng=')).decode())
aes = AES.new(key, AES.MODE_CBC, iv)
print(aes.decrypt(base64.b64decode('EOMKt/Msn57pXYvYlMryxw==')).decode())运行结果

嘿,出来了,轻轻松松,现在一切都明了了,什么?你还不明白,好吧,我再重新整理下
4.代码整合
'''
1.首先一个时间戳t = str(int(time.time() * 1000))进行aes加密后base64编码
2.再给data(id=1666739861421326337)进行aes加密后base64编码
3.最后返回的结果又要用aes解密,base64解码
'''
# -*- coding: utf-8 -*-
'''
@IDE : PyCharm
@version : 3.9
@Auth : gouzi
@time : 2023/10/18 14:51
@Description:
'''
import json
import requests
import base64
from Crypto.Cipher import AES
import time
from Crypto.Util.Padding import pad, unpad
t = str(int(time.time() * 1000))
key = b"qP2$bG9;vA0^uW0:"
iv = b"qP2$bG9;vA0^uW0:"
aes = AES.new(key, AES.MODE_CBC, iv)
headers = {
"Accept": "*/*",
"Accept-Language": "zh-CN,zh;q=0.9",
"Connection": "keep-alive",
"Content-Type": "application/json;charset=utf-8",
"Referer": "https://servicewechat.com/wx2ffe954c1d2e5369/833/page-frame.html",
"Sec-Fetch-Dest": "empty",
"Sec-Fetch-Mode": "cors",
"Sec-Fetch-Site": "cross-site",
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Safari/537.36 MicroMessenger/7.0.20.1781(0x6700143B) NetType/WIFI MiniProgramEnv/Windows WindowsWechat/WMPF XWEB/8447",
"timestamp": base64.b64encode(aes.encrypt(pad(t.encode(), 16))),
"xweb_xhr": "1"
}
url = "https://klhadm2.kele-go.cn/klh/product/activitySinglePageConfig/api/queryDetails"
aes = AES.new(key, AES.MODE_CBC, iv)
#print(aes.decrypt(base64.b64decode('llUt60iVpv30MUke6w+TN+b6yBdJJKw4JZ4Uavfazng=')).decode())#2023101814444309660
data = base64.b64encode(aes.encrypt(pad('id=1666739861421326337'.encode(),16)))
print(data.decode())
params = {
"data": data
}
response = requests.get(url, headers=headers, params=params).text
print(response)
aes = AES.new(key, AES.MODE_CBC, iv)
print(unpad(aes.decrypt(base64.b64decode(response)), 16).decode())
运行结果:

芜湖,出来了,别急,我还有个想法,就是如果传入的是明文值呢?

这是啥?

好吧。。。。
5.难度分析
中等,别看我分析的那么简简单单,我可是卡在加密参数那整整几个小时,靠,一直在找到底是哪里生成的加密参数,md,结果偶然一试发现可以直接解码得到,算了,当踩了下坑吧,发出来希望大家能够避免。嗯,就这样,祝福大家平平安安。
























 543
543

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








