权限账号创建流程
#创建zbx账号到kube-system空间
kubectl create serviceaccount zbx -n kube-system
#创建角色
kubectl create -f myroly.yaml
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
namespace: kube-system
name: myrolezzzzzzzzzzz
rules:
- apiGroups: [""]
resources: ["pods"]
verbs: ["get", "watch", "list"]
- apiGroups: ["extensions", "apps"]
resources: ["deployments"]
verbs: ["get", "list", "watch", "create", "update", "patch", "delete"]
#角色关联账号
kubectl create -f mybond-roly.yaml
kind: RoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: role-bind-cnych
namespace: kube-system
subjects:
- kind: ServiceAccount
name: zbx
namespace: kube-system
roleRef:
kind: Role
name: myrolezzzzzzzzzzz
apiGroup: rbac.authorization.k8s.io
#查看kube-system空间账号
kubectl get serviceaccounts -n kube-system
#查看zbx账号的token名
kubectl get secret -n kube-system
#查看空间下所以token值,找到token名
kubectl describe secrets -n kube-system
#用上面查到zbx的token登录web界面
输入kube-system
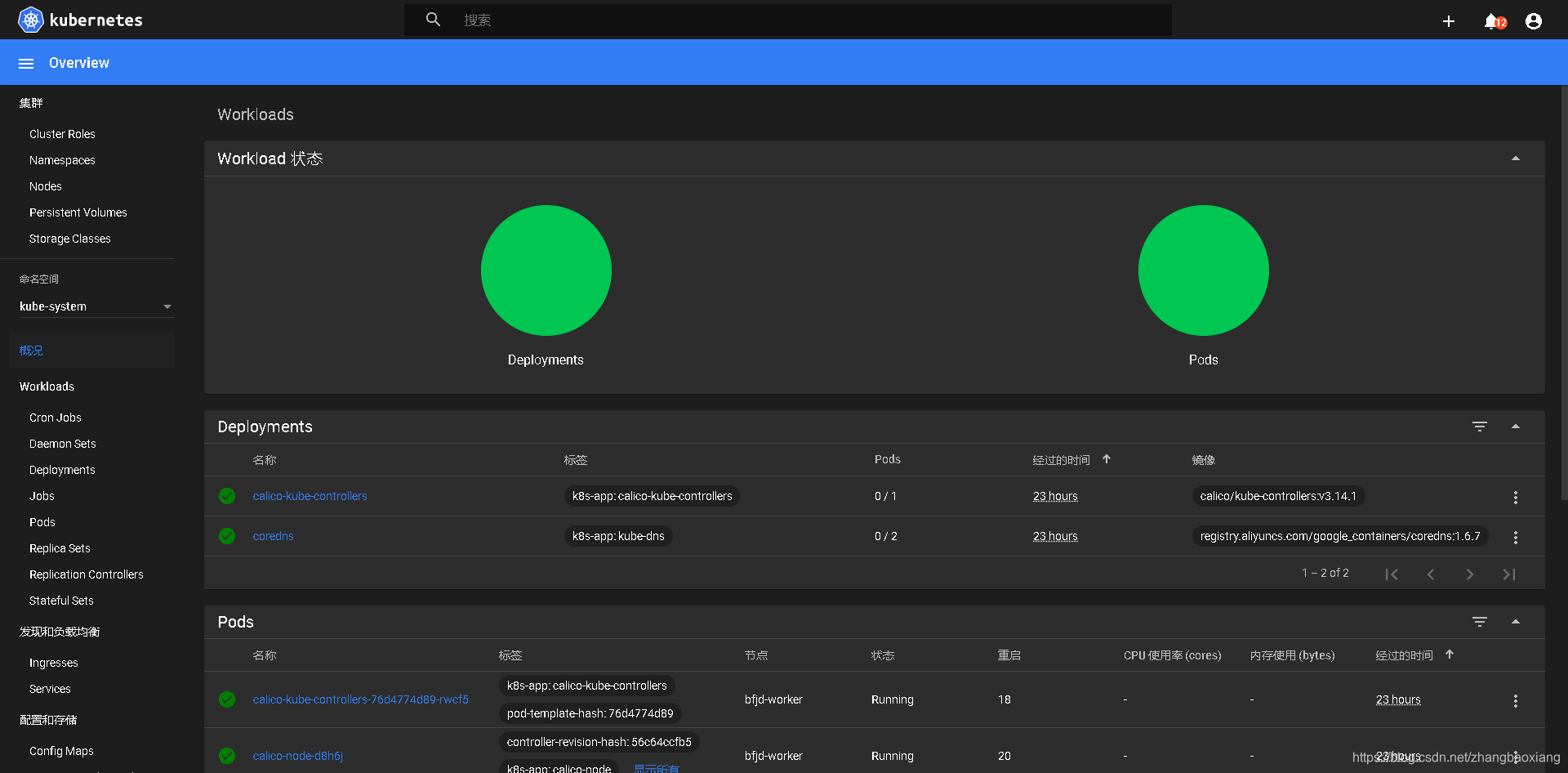
完成
###################其他#############################
#角色信息查询
kubectl get serviceaccounts
kubectl get clusterrolebinding
#删除角色信息
kubectl delete clusterrolebinding kubernetes-dashboard-admin
kubectl delete clusterrolebinding serviceaccount-cluster-admin





 本文详细介绍了在Kubernetes中创建权限账号的具体步骤,包括在kube-system命名空间下创建zbx账号,定义角色及其权限范围,绑定账号到角色,以及查询和使用账号信息的过程。
本文详细介绍了在Kubernetes中创建权限账号的具体步骤,包括在kube-system命名空间下创建zbx账号,定义角色及其权限范围,绑定账号到角色,以及查询和使用账号信息的过程。


















 702
702

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










