通过文件下载,可以下载到目标网站的数据库配置文件或网站信息文件,对后续的渗透有很大帮助!
文件下载
靶场环境pikachu
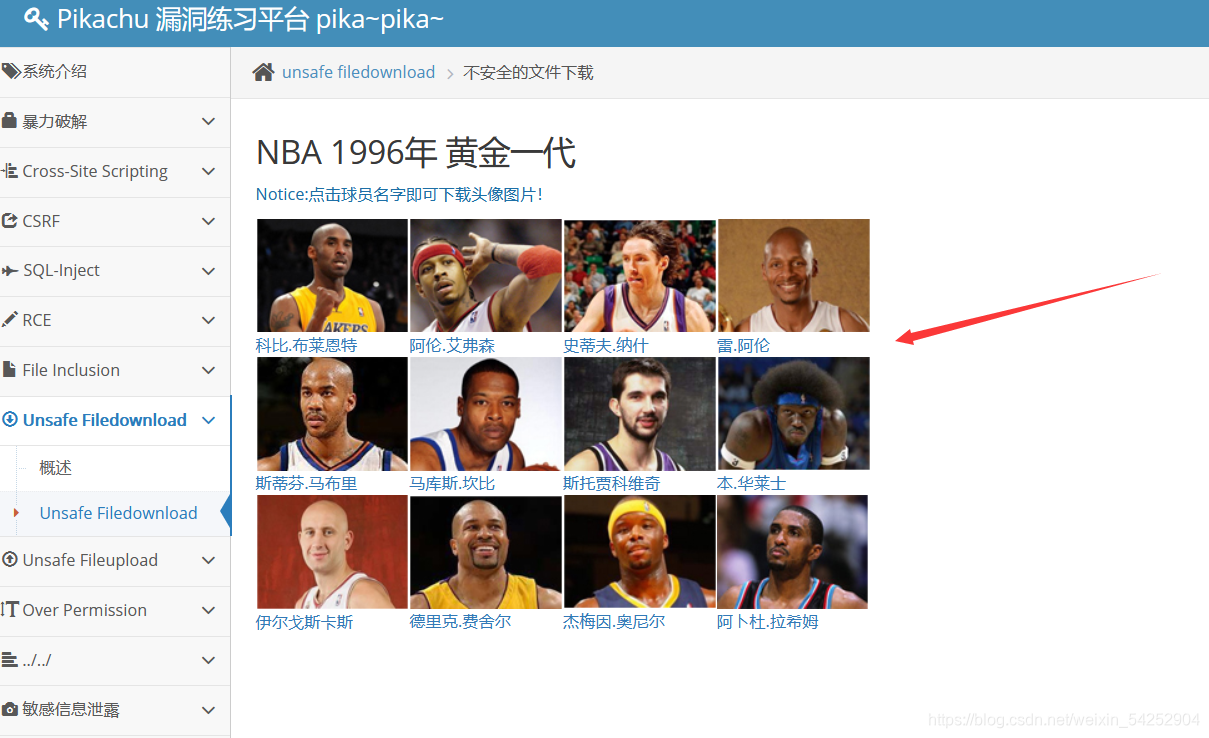
右键点击图片链接查看
http://172.21.22.23:88/vul/unsafedownload/execdownload.php?filename=kb.png
http://172.21.22.23:88/vul/unsafedownload/execdownload.php?filename=ai.png
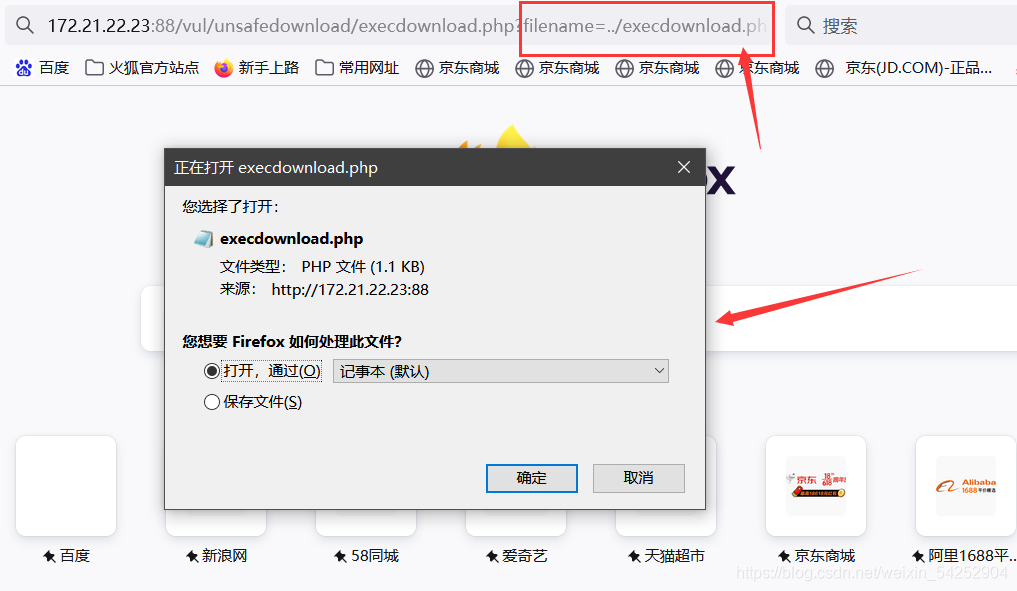
把filename的值改为上一层的php文件
http://172.21.22.23:88/vul/unsafedownload/execdownload.php?filename=…/execdownload.php
访问即可下载
同样可以在下载的文件中查找敏感文件信息进行下载
如何知道网站目录的信息结构:
通过扫描工具如御剑扫描,burpsuit,
只要字典足够好,什么都能扫得到!
判断
根据参数值
- read.xxx?filename=
- down.xxx?filename=
- readfile.xxx?file=
- downfile.xxx?file=
- …/ …\ .\ ./等
- %00 ? %23 %20 .等
- &readpath=、&filepath=、&path=、&inputfile=、&url=、&data=、&readfile=、
- &menu=、META-INF= 、WEB-INF
测试网站
只是练习,不搞破坏!
https://www.znds.com/
鼠标右键复制链接查看
http://down.znds.com/getdownurl/?s=L2Rvd24vMjAyMTA1MzEvdHhzcDE2MTU4XzcuNC4wLjEwMTBfZGFuZ2JlaS5hcGs=
base64解密后为
http://down.znds.com/getdownurl/s=/down/20210531/txsp16158_7.4.0.1010_dangbei.apk
如果把s后面的文件换成网络的php文件就能下载
下载时要把s后面的参数值进行base64加密
CTF考题
点击Help复制链接
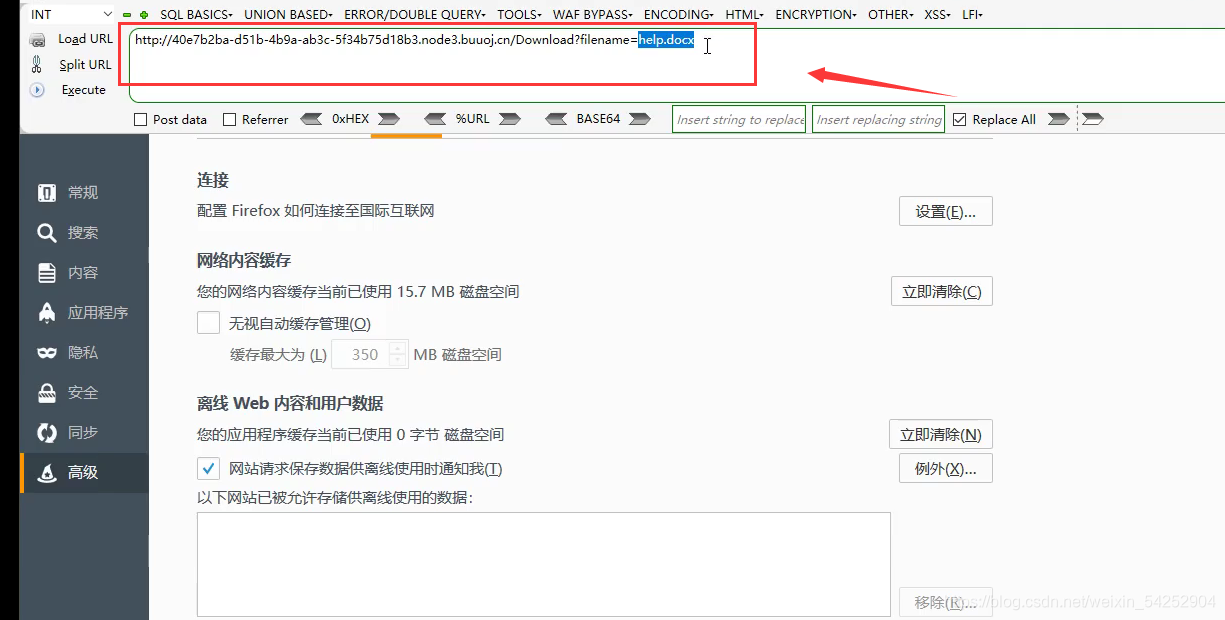
filename=help.docx
很像文件下载
javaweb开放一般文件下载都以post方式进行提交
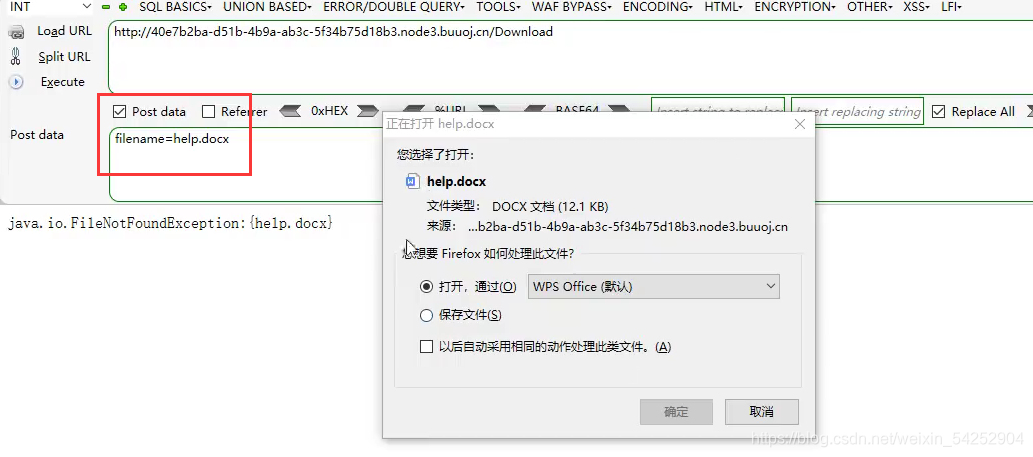
通过抓取数据包得知是javaweb开放
由于javaweb有WEB-INF/web.xml的配置问件
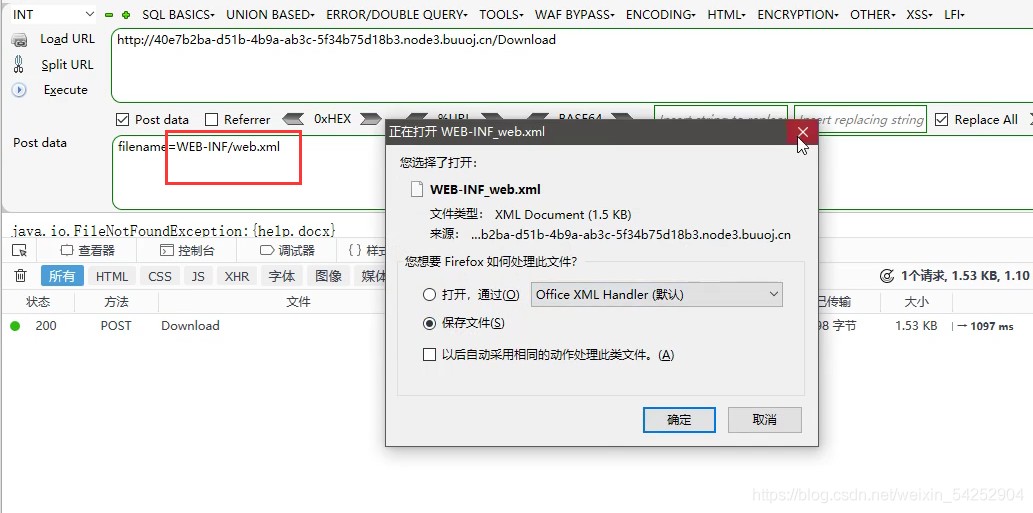
成功下载,打开获取flag!
漏洞文件下载
百度杯
挺难的!





 本文探讨了文件下载漏洞在CTF竞赛中的应用,涉及网站目录探测、PHP文件注入、百度杯登录绕过、小米路由器敏感文件获取等内容,展示了渗透测试技术和常见漏洞利用技巧。
本文探讨了文件下载漏洞在CTF竞赛中的应用,涉及网站目录探测、PHP文件注入、百度杯登录绕过、小米路由器敏感文件获取等内容,展示了渗透测试技术和常见漏洞利用技巧。
 最低0.47元/天 解锁文章
最低0.47元/天 解锁文章

















 421
421

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








