Web
灏妹的web
什么都没有就直接扫了,
然后访问这个就发现了flag
/.idea/dataSources.xml
EZupload
访问?source=1就可以拿到源码,但并没有什么用
网上没找到怎么latte注入,先放着学会了我再来补,呜呜呜太菜了
<?php
error_reporting(0);
require 'vendor/autoload.php';
$latte = new Latte\Engine;
$latte->setTempDirectory('tempdir');
$policy = new Latte\Sandbox\SecurityPolicy;
$policy->allowMacros(['block', 'if', 'else','=']);
$policy->allowFilters($policy::ALL);
$policy->allowFunctions(['trim', 'strlen']);
$latte->setPolicy($policy);
$latte->setSandboxMode();
$latte->setAutoRefresh(false);
if(isset($_FILES['file'])){
$uploaddir = '/var/www/html/tempdir/';
$filename = basename($_FILES['file']['name']);
if(stristr($filename,'p') or stristr($filename,'h') or stristr($filename,'..')){
die('no');
}
$file_conents = file_get_contents($_FILES['file']['tmp_name']);
if(strlen($file_conents)>28 or stristr($file_conents,'<')){
die('no');
}
$uploadfile = $uploaddir . $filename;
if (move_uploaded_file($_FILES['file']['tmp_name'], $uploadfile)) {
$message = $filename ." was successfully uploaded.";
} else {
$message = "error!";
}
$params = [
'message' => $message,
];
$latte->render('tempdir/index.latte', $params);
}
else if($_GET['source']==1){
highlight_file(__FILE__);
}
else{
$latte->render('tempdir/index.latte', ['message'=>'Hellow My Glzjin!']);
}
Misc
真签到
Yusa的小秘密

提示也说了不是简单的LSB和RGB,后面找到了YCRCB
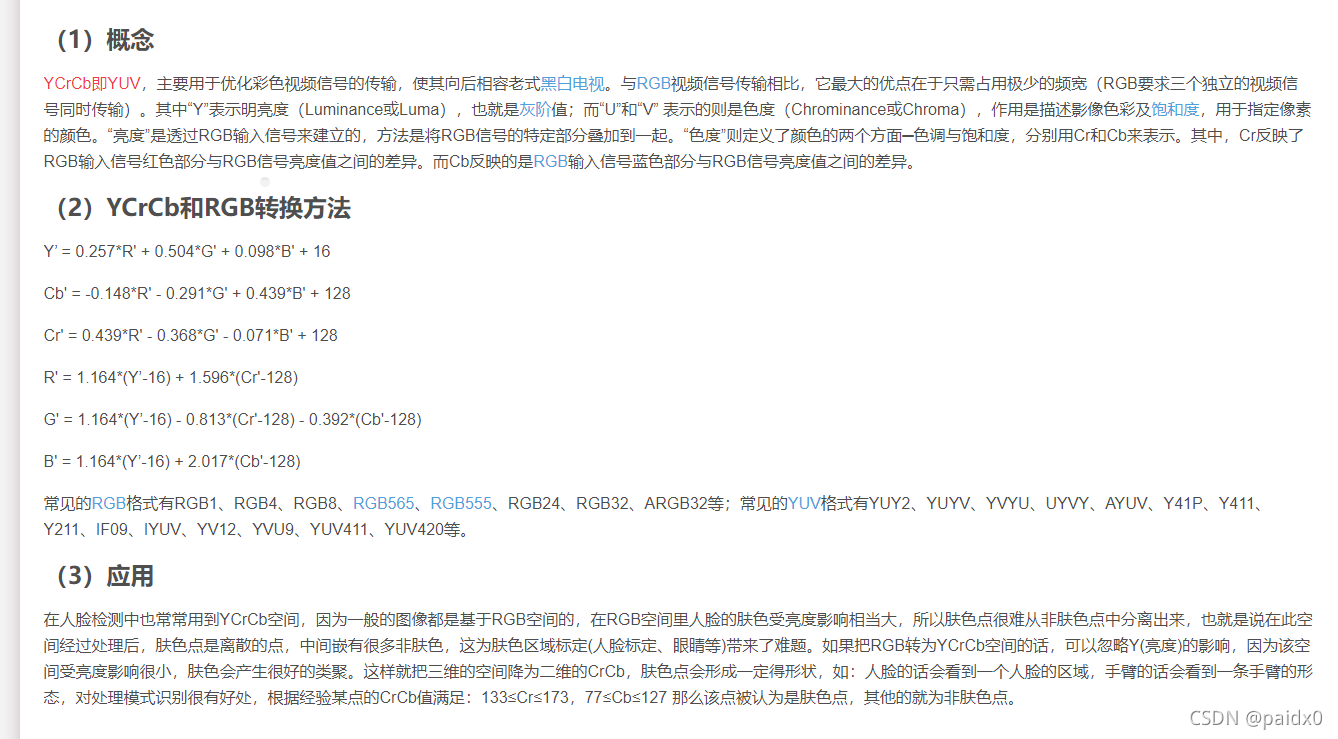
from cv2 import *
img = cv2.imread(r'C:\Users\Administrator\Downloads\misc4.png')
cv_color = cv2.cvtColor(img, cv2.COLOR_BGR2YCrCb)
cv2.imwrite(r'C:\Users\Administrator\Downloads\flag.png', cv_color)
得到一张新的图片再去查看flag






 博客探讨了Web安全问题,涉及Latte模板引擎的沙箱模式及上传文件过滤。同时,文章提到了图像处理中的YCRCB色彩空间,通过代码展示了从BGR转换为YCRCB的过程,并暗示该色彩空间对于解密隐藏信息的重要性。
博客探讨了Web安全问题,涉及Latte模板引擎的沙箱模式及上传文件过滤。同时,文章提到了图像处理中的YCRCB色彩空间,通过代码展示了从BGR转换为YCRCB的过程,并暗示该色彩空间对于解密隐藏信息的重要性。

















 1861
1861

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










