1、zookeeper的安装(单机)
1、环境变量配置
export ZOOKEEPER_HOME=/data/zookeeper-3.4.12
export JAVA_HOME=/data/java/jdk1.8.0_131
export PATH=$ZOOKEEPER_HOME/bin:$JAVA_HOME/bin:$PATH
2、配置文件
# The number of milliseconds of each tick
tickTime=2000
# The number of ticks that the initial
# synchronization phase can take
initLimit=10
# The number of ticks that can pass between
# sending a request and getting an acknowledgement
syncLimit=5
# the directory where the snapshot is stored.
# do not use /tmp for storage, /tmp here is just
# example sakes.
dataDir=/data/zookeeper-3.4.12/data
# the port at which the clients will connect
clientPort=2181
# the maximum number of client connections.
# increase this if you need to handle more clients
#maxClientCnxns=60
#
# Be sure to read the maintenance section of the
# administrator guide before turning on autopurge.
#
# http://zookeeper.apache.org/doc/current/zookeeperAdmin.html#sc_maintenance
#
# The number of snapshots to retain in dataDir
#autopurge.snapRetainCount=3
# Purge task interval in hours
# Set to "0" to disable auto purge feature
#autopurge.purgeInterval=1
3、启动zk
4、推荐参考
2、Zookeeper 开启kerberos
在kerberos服务器henghe-01上,使用root用户,在/root/keytabs目录下,创建Zookeeper的principal
Authenticating as principal test/admin@HADOOP.COM with password.
kadmin.local: list_principals
K/M@HADOOP.COM
kadmin/admin@HADOOP.COM
kadmin/changepw@HADOOP.COM
kadmin/henghe-01.hadoop.com@HADOOP.COM
kiprop/henghe-01.hadoop.com@HADOOP.COM
krbtgt/HADOOP.COM@HADOOP.COM
root/admin@HADOOP.COM
test@HADOOP.COM
zookeeper/henghe-01.hadoop.com@HADOOP.COM
zookeeper@HADOOP.COM
kadmin.local: addprinc -randkey zookeeper/henghe-01.hadoop.com@HADOOP.COM
WARNING: no policy specified for zookeeper/henghe-01.hadoop.com@HADOOP.COM; defaulting to no policy
Principal "zookeeper/henghe-01.hadoop.com@HADOOP.COM" created.
kadmin.local: xst -k zookeeper.keytab zookeeper/henghe-01.hadoop.com@HADOOP.COM
Entry for principal zookeeper/henghe-01.hadoop.com@HADOOP.COM with kvno 2, encryption type aes256-cts-hmac-sha1-96 added to keytab WRFILE:zookeeper.keytab.
Entry for principal zookeeper/henghe-01.hadoop.com@HADOOP.COM with kvno 2, encryption type aes128-cts-hmac-sha1-96 added to keytab WRFILE:zookeeper.keytab.
Entry for principal zookeeper/henghe-01.hadoop.com@HADOOP.COM with kvno 2, encryption type des3-cbc-sha1 added to keytab WRFILE:zookeeper.keytab.
Entry for principal zookeeper/henghe-01.hadoop.com@HADOOP.COM with kvno 2, encryption type arcfour-hmac added to keytab WRFILE:zookeeper.keytab.
Entry for principal zookeeper/henghe-01.hadoop.com@HADOOP.COM with kvno 2, encryption type camellia256-cts-cmac added to keytab WRFILE:zookeeper.keytab.
Entry for principal zookeeper/henghe-01.hadoop.com@HADOOP.COM with kvno 2, encryption type camellia128-cts-cmac added to keytab WRFILE:zookeeper.keytab.
Entry for principal zookeeper/henghe-01.hadoop.com@HADOOP.COM with kvno 2, encryption type des-hmac-sha1 added to keytab WRFILE:zookeeper.keytab.
Entry for principal zookeeper/henghe-01.hadoop.com@HADOOP.COM with kvno 2, encryption type des-cbc-md5 added to keytab WRFILE:zookeeper.keytab.
kadmin.local:
生成如下文件:(注意该文件权限赋予 400 且属组用户要匹配进程 启动用户)
chown -R zookeeper:zookeeper zookeeper.keytab
chmod 400 zookeeper.keytab
将该文件放到 zk 的 conf 的目录下。
修改zoo.cfg,添加以下安全相关的配置
追加
authProvider.1=org.apache.zookeeper.server.auth.SASLAuthenticationProvider
jaasLoginRenew=3600000
在conf目录创建java.env文件,添加以下内容
export JVMFLAGS="-Djava.security.auth.login.config=/data/zookeeper-3.4.12/conf/jaas.conf"
在conf目录创建jaas.conf文件
Server {
com.sun.security.auth.module.Krb5LoginModule required
useKeyTab=true
keyTab="/data/zookeeper-3.4.12/conf/zookeeper.keytab"
storeKey=true
useTicketCache=false
principal="zookeeper/henghe-01.hadoop.com@HADOOP.COM";
};
注意:如果修改jaas.conf配置,则一定要重启zkServer,否则会导致zkClient连不上,
可能是因为zkClinet和zkServer使用同一个jaas配置,实际zkClient应该配置自己的keytab用于访问,
而不是配置成和Server一样,可以在其他机器上面新建一个用户作为访问的客户端。
zookeeper 进程使用 zookeeper 用户启动,
su zookeeper
zkServer.sh start
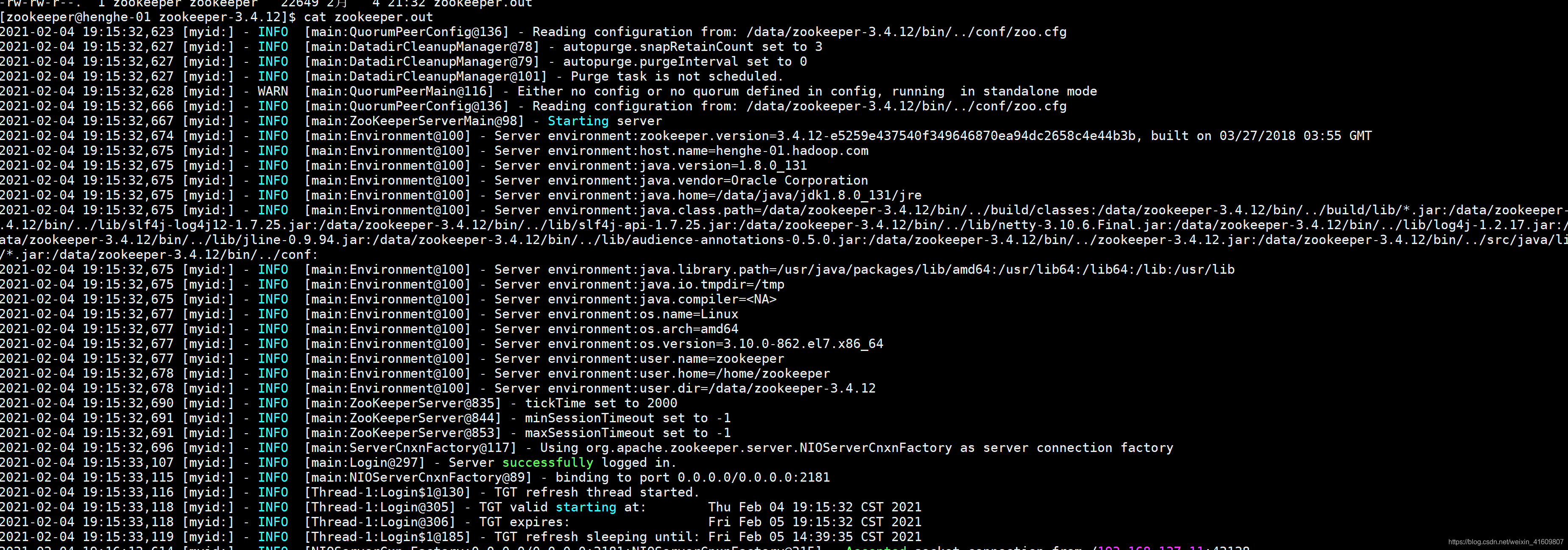
由上图可知,服务端开启kerberos成功。
启动完毕 zookeeper 可以在 zk 节点上进入 zkCli
zkCli.sh -server henghe-01:2181
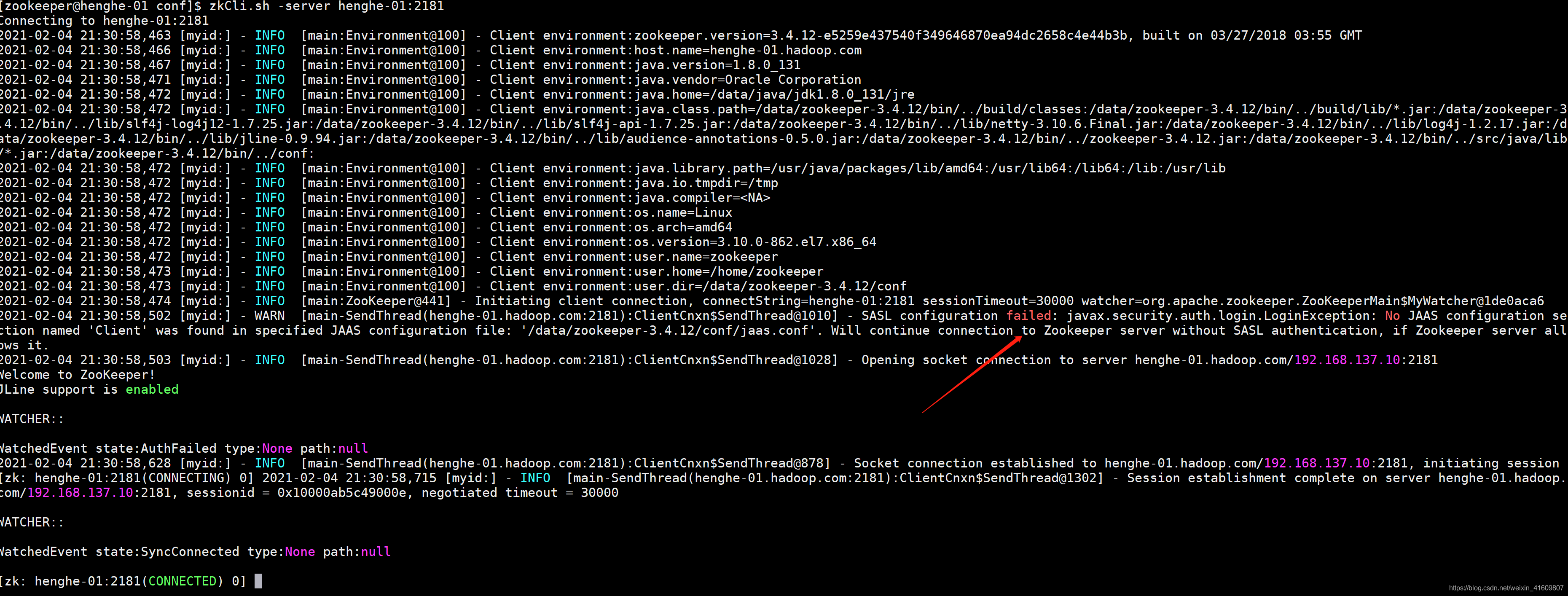
由上图可以看到权限认证失败,主要原因是我们没有配置客户端的认证规则。
3、配置客户端认证
其他相关配置一致,主要添加jaas.conf
vim jaas.conf
Client {
com.sun.security.auth.module.Krb5LoginModule required
useKeyTab=true
keyTab="/data/zookeeper-3.4.12/conf/zookeeper.keytab"
storeKey=true
useTicketCache=false
principal="zookeeper/henghe-01.hadoop.com@HADOOP.COM";
};
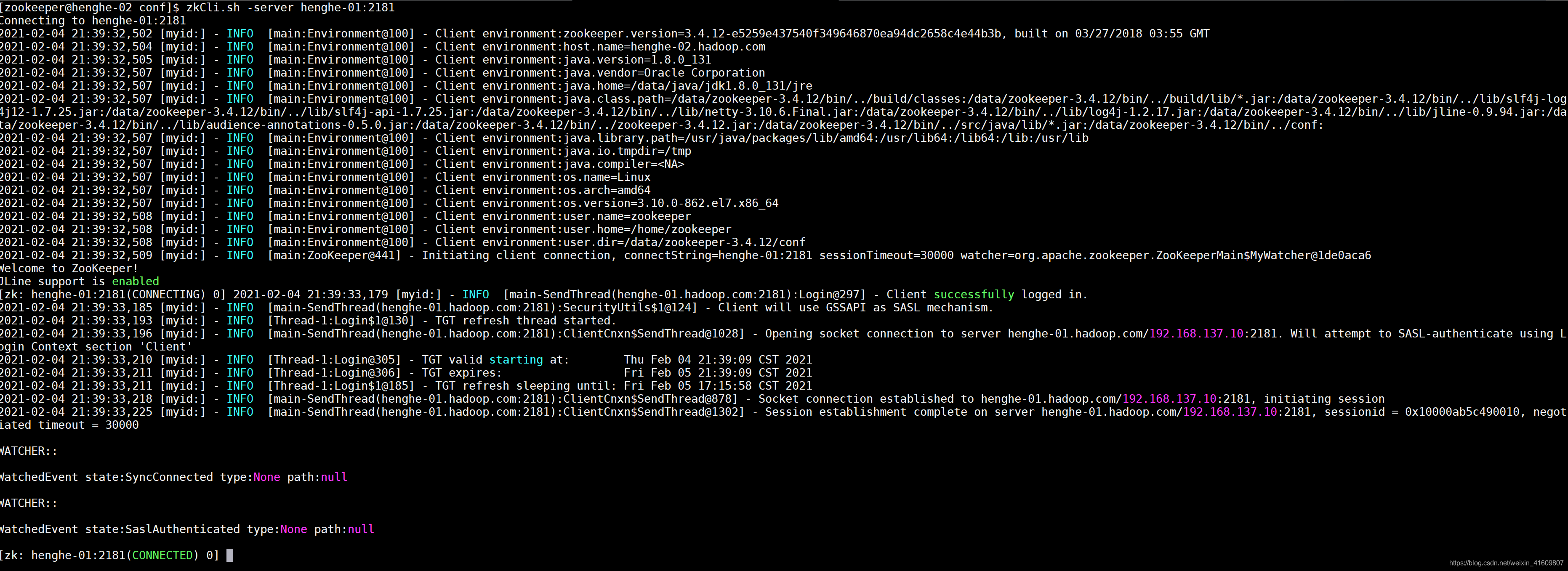
由上图可知添加相关配置后,可以通过权限验证正常登录。
4、节点权限认证
4.1 创建节点并设置ACL权限
[zk: henghe-01:2181(CONNECTED) 0] create /test "ad"
Created /test
[zk: henghe-01:2181(CONNECTED) 1] getAcl /test
'world,'anyone
: cdrwa
[zk: henghe-01:2181(CONNECTED) 2] setAcl /test sasl:zookeeper/henghe-01.hadoop.com@HADOOP.COM:cdwra
cZxid = 0x5e
ctime = Thu Feb 04 21:42:29 CST 2021
mZxid = 0x5e
mtime = Thu Feb 04 21:42:29 CST 2021
pZxid = 0x5e
cversion = 0
dataVersion = 0
aclVersion = 1
ephemeralOwner = 0x0
dataLength = 2
numChildren = 0
[zk: henghe-01:2181(CONNECTED) 3] getAcl /test
'sasl,'zookeeper/henghe-01.hadoop.com@HADOOP.COM
: cdrwa
[zk: henghe-01:2181(CONNECTED) 4]
4.2远程访问节点(未授权节点)
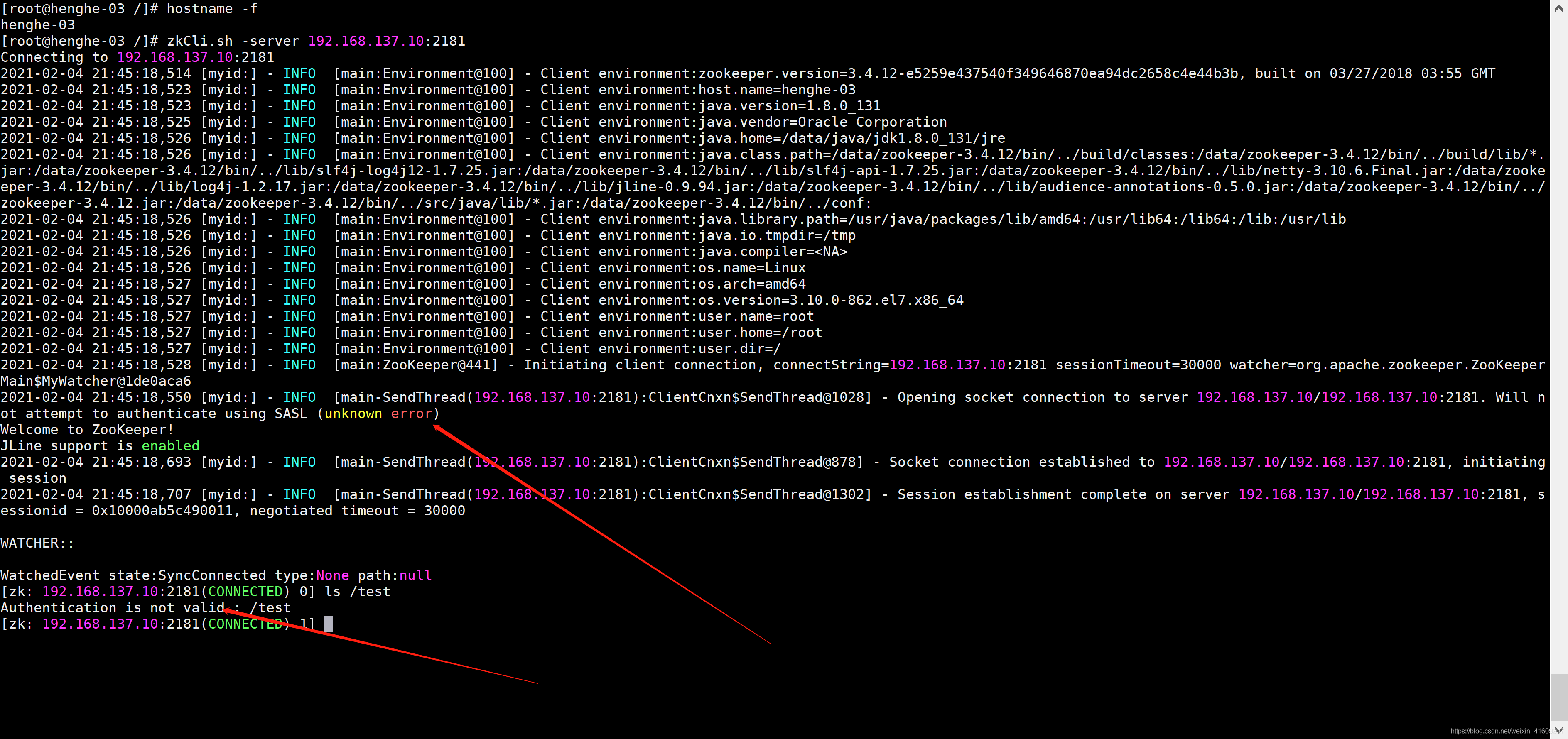
4.3远程访问节点(授权节点)

上图中的认证principal是zookeeper/henghe-01.hadoop.com@HADOOP.COM与节点的ACL一致。
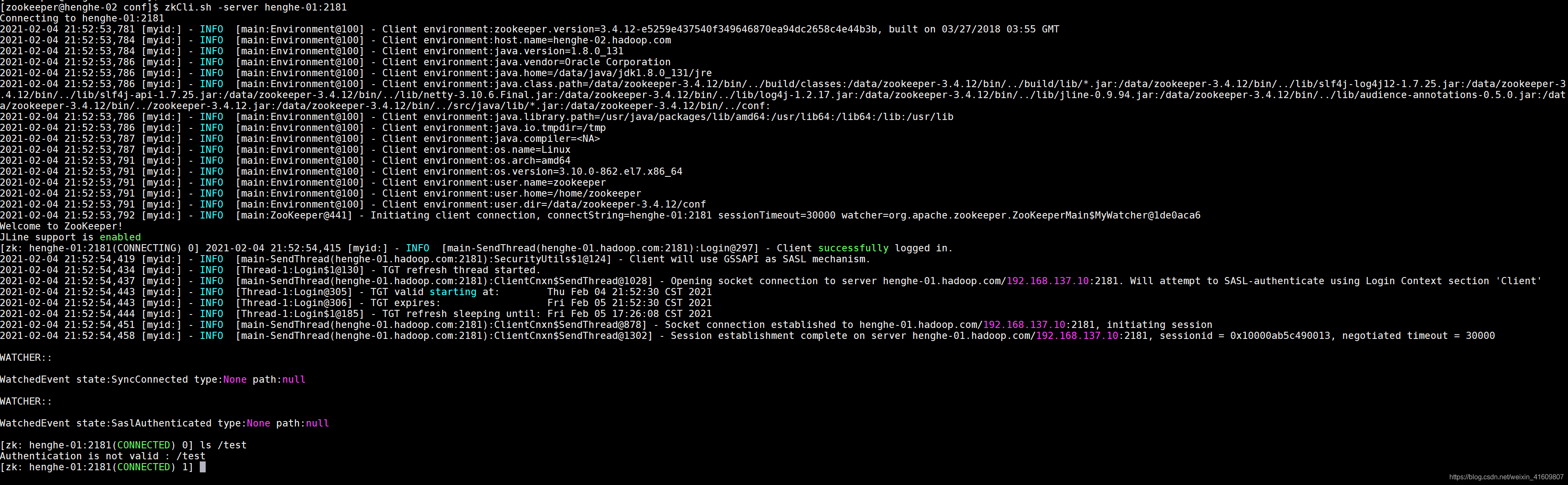
再次验证principal是zookeeper/henghe-02.hadoop.com@HADOOP.COM与节点的ACL不一致。虽然可以登录但是权限认证不过无法访问对应的节点。








 本文档详细介绍了Zookeeper的单机安装步骤,包括环境变量配置、配置文件设置及启动过程。接着,重点阐述了如何在Kerberos环境中为Zookeeper开启认证,包括创建principal、配置jaas.conf和java.env文件。最后,展示了客户端认证的配置方法以及节点权限认证的示例,强调了ACL权限设置和不同principal访问权限的差异。
本文档详细介绍了Zookeeper的单机安装步骤,包括环境变量配置、配置文件设置及启动过程。接着,重点阐述了如何在Kerberos环境中为Zookeeper开启认证,包括创建principal、配置jaas.conf和java.env文件。最后,展示了客户端认证的配置方法以及节点权限认证的示例,强调了ACL权限设置和不同principal访问权限的差异。

















 4421
4421

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








