解释这段语句什么意思:09-22 10:54:55.564 1000 1732 18185 E subsystem_ramdump: write successful for ramdump fd for /data/vendor/bsplog/wlan/ssr_dump/2025-09-22-10:54:41/ramdump_wpss_2025-09-22_10-54-50.elf
09-22 10:54:55.564 1000 1732 18185 E subsystem_ramdump: read /proc/last_mcrash :adrastea/wpss.mdt: cmnos_thread.c:4003:Asserted in wal_power_debug.c:wal_power_debug_trigger_crash_c
09-22 10:54:55.564 1000 1732 18185 E subsystem_ramdump: /data/vendor/ramdump/mcrash_history is Max, can NOT save more
09-22 10:54:55.564 wifi 3431 3431 D wpa_supplicant: p2p0: Event AVOID_FREQUENCIES (48) received
09-22 10:54:55.564 wifi 3431 3431 I wpa_supplicant: p2p0: CTRL-EVENT-AVOID-FREQ ranges=
09-22 10:54:55.564 wifi 3431 3431 D wpa_supplicant: p2p0: P2P: Update channel list based on frequency avoid event
09-22 10:54:55.564 wifi 3431 3431 D wpa_supplicant: p2p0: Determining shared radio frequencies (max len 2)
09-22 10:54:55.564 wifi 3431 3431 D wpa_supplicant: p2p0: Shared frequencies (len=0): completed iteration
09-22 10:54:55.564 wifi 3431 3431 D wpa_supplicant: p2p0: Determining shared radio frequencies (max len 2)
09-22 10:54:55.564 wifi 3431 3431 D wpa_supplicant: p2p0: Shared frequencies (len=0): completed iteration
09-22 10:54:55.565 wifi 3431 3431 D wpa_supplicant: p2p0: Shared frequencies (len=0): valid for P2P
09-22 10:54:55.565 wifi 3431 3431 D wpa_supplicant: P2P: Add operating class 81
09-22 10:54:55.565 wifi 3431 3431 D wpa_supplicant: P2P: Channels - hexdump(len=13): 01 02 03 04 05 06 07 08 09 0a 0b 0c 0d
09-22 10:54:55.565 wifi 3431 3431 D wpa_supplicant: P2P: Add operating class 115
09-22 10:54:55.565 wifi 3431 3431 D wpa_supplicant: P2P: Channels - hexdump(len=4): 24 28 2c 30
09-22 10:54:55.565 wifi 3431 3431 D wpa_supplicant: P2P: Add operating class 116
09-22 10:54:55.565 wifi 3431 3431 D wpa_supplicant: P2P: Channels - hexdump(len=2): 24 2c
09-22 10:54:55.565 wifi 3431 3431 D wpa_supplicant: P2P: Add operating class 117
09-22 10:54:55.565 wifi 3431 3431 D wpa_supplicant: P2P: Channels - hexdump(len=2): 28 30
09-22 10:54:55.565 wifi 3431 3431 D wpa_supplicant: P2P: Add operating class 118 (client only)
09-22 10:54:55.565 wifi 3431 3431 D wpa_supplicant: P2P: Channels (client only) - hexdump(len=4): 34 38 3c 40
09-22 10:54:55.565 wifi 3431 3431 D wpa_supplicant: P2P: Add operating class 119 (client only)
09-22 10:54:55.565 wifi 3431 3431 D wpa_supplicant: P2P: Channels (client only) - hexdump(len=2): 34 3c
09-22 10:54:55.565 wifi 3431 3431 D wpa_supplicant: P2P: Add operating class 120 (client only)
09-22 10:54:55.565 wifi 3431 3431 D wpa_supplicant: P2P: Channels (client only) - hexdump(len=2): 38 40
09-22 10:54:55.565 wifi 3431 3431 D wpa_supplicant: P2P: Add operating class 124
09-22 10:54:55.565 wifi 3431 3431 D wpa_supplicant: P2P: Channels - hexdump(len=4): 95 99 9d a1
09-22 10:54:55.565 wifi 3431 3431 D wpa_supplicant: P2P: Add operating class 125
09-22 10:54:55.565 wifi 3431 3431 D wpa_supplicant: P2P: Channels - hexdump(len=5): 95 99 9d a1 a5
09-22 10:54:55.566 wifi 3431 3431 D wpa_supplicant: P2P: Add operating class 126
09-22 10:54:55.566 wifi 3431 3431 D wpa_supplicant: P2P: Channels - hexdump(len=2): 95 9d
09-22 10:54:55.566 wifi 3431 3431 D wpa_supplicant: P2P: Add operating class 127
09-22 10:54:55.566 wifi 3431 3431 D wpa_supplicant: P2P: Channels - hexdump(len=2): 99 a1
09-22 10:54:55.566 wifi 3431 3431 D wpa_supplicant: P2P: Add operating class 128
09-22 10:54:55.566 wifi 3431 3431 D wpa_supplicant: P2P: Channels - hexdump(len=8): 24 28 2c 30 95 99 9d a1
09-22 10:54:55.566 wifi 3431 3431 D wpa_supplicant: P2P: Add operating class 130
09-22 10:54:55.566 wifi 3431 3431 D wpa_supplicant: P2P: Add operating class 130 (client only)
09-22 10:54:55.566 wifi 3431 3431 D wpa_supplicant: P2P: Channels - hexdump(len=9): 24 28 2c 30 95 99 9d a1 a5
09-22 10:54:55.566 wifi 3431 3431 D wpa_supplicant: P2P: Channels (client only) - hexdump(len=4): 34 38 3c 40
09-22 10:54:55.567 wifi 3431 3431 D wpa_supplicant: P2P: Update channel list
09-22 10:54:55.567 wifi 3431 3431 D wpa_supplicant: P2P: channels: 81:1,2,3,4,5,6,7,8,9,10,11,12,13 115:36,40,44,48 116:36,44 117:40,48 124:149,153,157,161 125:149,153,157,161,165 126:149,157 127:153,161 128:36,40,44,48,149,153,157,161 130:36,40,44,48,149,153,157,161,165
09-22 10:54:55.567 wifi 3431 3431 D wpa_supplicant: P2P: cli_channels: 118:52,56,60,64 119:52,60 120:56,64 130:52,56,60,64
09-22 10:54:55.567 wifi 3431 3431 D wpa_supplicant: nl80211: Drv Event 103 (NL80211_CMD_VENDOR) received for wlan0
09-22 10:54:55.567 wifi 3431 3431 D wpa_supplicant: nl80211: Vendor event: wiphy=0 vendor_id=0x1374 subcmd=10
09-22 10:54:55.567 wifi 3431 3431 D wpa_supplicant: wlan0: Event AVOID_FREQUENCIES (48) received
09-22 10:54:55.568 wifi 3431 3431 I wpa_supplicant: wlan0: CTRL-EVENT-AVOID-FREQ ranges=
09-22 10:54:55.568 wifi 3431 3431 D wpa_supplicant: wlan0: P2P: Update channel list based on frequency avoid event
09-22 10:54:55.569 wifi 3431 3431 D wpa_supplicant: wlan0: Determining shared radio frequencies (max len 2)
09-22 10:54:55.569 wifi 3431 3431 D wpa_supplicant: wlan0: Shared frequencies (len=0): completed iteration
09-22 10:54:55.569 wifi 3431 3431 D wpa_supplicant: wlan0: Determining shared radio frequencies (max len 2)
09-22 10:54:55.569 wifi 3431 3431 D wpa_supplicant: wlan0: Shared frequencies (len=0): completed iteration
09-22 10:54:55.569 wifi 3431 3431 D wpa_supplicant: wlan0: Shared frequencies (len=0): valid for P2P
09-22 10:54:55.569 wifi 3431 3431 D wpa_supplicant: P2P: Add operating class 81
09-22 10:54:55.569 wifi 3431 3431 D wpa_supplicant: P2P: Channels - hexdump(len=13): 01 02 03 04 05 06 07 08 09 0a 0b 0c 0d
09-22 10:54:55.569 wifi 3431 3431 D wpa_supplicant: P2P: Add operating class 115
09-22 10:54:55.569 wifi 3431 3431 D wpa_supplicant: P2P: Channels - hexdump(len=4): 24 28 2c 30
09-22 10:54:55.569 wifi 3431 3431 D wpa_supplicant: P2P: Add operating class 116
09-22 10:54:55.569 wifi 3431 3431 D wpa_supplicant: P2P: Channels - hexdump(len=2): 24 2c
09-22 10:54:55.569 wifi 3431 3431 D wpa_supplicant: P2P: Add operating class 117
09-22 10:54:55.569 wifi 3431 3431 D wpa_supplicant: P2P: Channels - hexdump(len=2): 28 30
09-22 10:54:55.569 wifi 3431 3431 D wpa_supplicant: P2P: Add operating class 118 (client only)
09-22 10:54:55.569 wifi 3431 3431 D wpa_supplicant: P2P: Channels (client only) - hexdump(len=4): 34 38 3c 40
09-22 10:54:55.569 wifi 3431 3431 D wpa_supplicant: P2P: Add operating class 119 (client only)
09-22 10:54:55.569 wifi 3431 3431 D wpa_supplicant: P2P: Channels (client only) - hexdump(len=2): 34 3c
09-22 10:54:55.569 wifi 3431 3431 D wpa_supplicant: P2P: Add operating class 120 (client only)
09-22 10:54:55.569 wifi 3431 3431 D wpa_supplicant: P2P: Channels (client only) - hexdump(len=2): 38 40
09-22 10:54:55.569 wifi 3431 3431 D wpa_supplicant: P2P: Add operating class 124
09-22 10:54:55.569 wifi 3431 3431 D wpa_supplicant: P2P: Channels - hexdump(len=4): 95 99 9d a1
09-22 10:54:55.569 wifi 3431 3431 D wpa_supplicant: P2P: Add operating class 125
09-22 10:54:55.569 wifi 3431 3431 D wpa_supplicant: P2P: Channels - hexdump(len=5): 95 99 9d a1 a5
09-22 10:54:55.569 wifi 3431 3431 D wpa_supplicant: P2P: Add operating class 126
09-22 10:54:55.569 wifi 3431 3431 D wpa_supplicant: P2P: Channels - hexdump(len=2): 95 9d
09-22 10:54:55.569 wifi 3431 3431 D wpa_supplicant: P2P: Add operating class 127
09-22 10:54:55.570 wifi 3431 3431 D wpa_supplicant: P2P: Channels - hexdump(len=2): 99 a1
09-22 10:54:55.570 wifi 3431 3431 D wpa_supplicant: P2P: Add operating class 128
09-22 10:54:55.570 wifi 3431 3431 D wpa_supplicant: P2P: Channels - hexdump(len=8): 24 28 2c 30 95 99 9d a1
09-22 10:54:55.570 wifi 3431 3431 D wpa_supplicant: P2P: Add operating class 130
09-22 10:54:55.570 wifi 3431 3431 D wpa_supplicant: P2P: Add operating class 130 (client only)
09-22 10:54:55.570 wifi 3431 3431 D wpa_supplicant: P2P: Channels - hexdump(len=9): 24 28 2c 30 95 99 9d a1 a5
09-22 10:54:55.570 wifi 3431 3431 D wpa_supplicant: P2P: Channels (client only) - hexdump(len=4): 34 38 3c 40
09-22 10:54:55.570 wifi 3431 3431 D wpa_supplicant: P2P: Update channel list
09-22 10:54:55.570 wifi 3431 3431 D wpa_supplicant: P2P: channels: 81:1,2,3,4,5,6,7,8,9,10,11,12,13 115:36,40,44,48 116:36,44 117:40,48 124:149,153,157,161 125:149,153,157,161,165 126:149,157 127:153,161 128:36,40,44,48,149,153,157,161 130:36,40,44,48,149,153,157,161,165
09-22 10:54:55.570 wifi 3431 3431 D wpa_supplicant: P2P: cli_channels: 118:52,56,60,64 119:52,60 120:56,64 130:52,56,60,64
09-22 10:54:55.581 10161 4593 7978 W hsbr : [{0}] Failed to resolve name. status={1}
09-22 10:54:55.600 10161 4593 7978 W hsbr : [{0}] Failed to resolve name. status={1}
09-22 10:54:55.604 10200 10875 11981 D JavaheapMonitor: Java heap used=4M max=256M, proc: com.miui.msa.global
09-22 10:54:55.605 10200 10875 11981 V JavaheapMonitor: Check java heap usage finished! Next check delay: 300000
09-22 10:54:55.631 10161 4593 7978 W hsbr : [{0}] Failed to resolve name. status={1}
09-22 10:54:55.698 1000 1732 18185 E subsystem_ramdump: chmod result:0
09-22 10:54:55.708 1000 1732 18185 I subsystem_ramdump: send file name enter
09-22 10:54:55.708 1000 1732 18185 E subsystem_ramdump: send file name open /data/vendor/ramdump/name for read error:6
09-22 10:54:55.708 1000 1732 18185 E subsystem_ramdump: ----mdm_helper cmd:chmod 777 /data/vendor/bsplog/wlan/ssr_dump/2025-09-22-10:54:41/ramdump_wpss_2025-09-22_10-54-50.elf
09-22 10:54:55.744 1000 1732 18185 E subsystem_ramdump: ----run_sh_cmd pid:18255 res:0
09-22 10:54:55.744 1000 1732 18185 E subsystem_ramdump: chmod ramdump, cmd_result:0x0
09-22 10:54:55.744 1000 1732 18185 E subsystem_ramdump: chmod cmd : chmod 777 /data/vendor/bsplog/wlan/ssr_dump/2025-09-22-10:54:41/ramdump_wpss_2025-09-22_10-54-50.elf
09-22 10:54:55.744 1000 1732 18185 E subsystem_ramdump: ----mdm_helper cmd:tar -czvf /data/vendor/bsplog/wlan/ssr_dump/2025-09-22-10:54:41/ramdump_wpss_2025-09-22_10-54-50.tgz /data/vendor/bsplog/wlan/ssr_dump/2025-09-22-10:54:41/ramdump_wpss_2025-09-22_10-54-50.elf
09-22 10:54:55.761 10161 4593 7978 W hsbr : [{0}] Failed to resolve name. status={1}
09-22 10:54:55.778 10161 4593 7978 W hsbr : [{0}] Failed to resolve name. status={1}
09-22 10:54:55.788 10161 4593 7978 W hsbr : [{0}] Failed to resolve name. status={1}
09-22 10:54:55.794 10161 4593 7978 W hsbr : [{0}] Failed to resolve name. status={1}
09-22 10:54:55.838 10161 4593 7978 W hsbr : [{0}] Failed to resolve name. status={1}
09-22 10:54:55.856 10161 4593 7978 W hsbr : [{0}] Failed to resolve name. status={1}
09-22 10:54:55.960 10161 4593 7978 W hsbr : [{0}] Failed to resolve name. status={1}
09-22 10:54:55.964 10161 4593 7978 W hsbr : [{0}] Failed to resolve name. status={1}
09-22 10:54:56.009 1000 1586 1586 W binder:1586_4: type=1400 audit(0.0:3769): avc: denied { search } for name="mcd" dev="dm-57" ino=859 scontext=u:r:surfaceflinger:s0 tcontext=u:object_r:mcd_data_file:s0 tclass=dir permissive=0
09-22 10:54:56.067 99000 7553 7574 E ocessService0:0: failed to create Unix domain socket: Operation not permitted
09-22 10:54:56.067 99001 12386 12409 E ocessService0:0: failed to create Unix domain socket: Operation not permitted
09-22 10:54:56.082 99003 13949 13956 E ocessService0:1: failed to create Unix domain socket: Operation not permitted
09-22 10:54:56.094 10161 4593 7978 W hsbr : [{0}] Failed to resolve name. status={1}
09-22 10:54:56.154 10161 4593 7978 W hsbr : [{0}] Failed to resolve name. status={1}
09-22 10:54:56.162 10161 4593 7978 W hsbr : [{0}] Failed to resolve name. status={1}
09-22 10:54:56.211 10161 4593 7978 W hsbr : [{0}] Failed to resolve name. status={1}
09-22 10:54:56.215 root 1280 18259 I resolv : GetAddrInfoHandler::run: {0 0 0 983040 10226 0}
09-22 10:54:56.215 root 1280 18259 I resolv : GetAddrInfoHandler::run: network access blocked
09-22 10:54:56.217 root 1280 18260 I resolv : GetAddrInfoHandler::run: {0 0 0 983040 10226 0}
09-22 10:54:56.217 root 1280 18260 I resolv : GetAddrInfoHandler::run: network access blocked
09-22 10:54:56.221 10161 4593 7978 W hsbr : [{0}] Failed to resolve name. status={1}
09-22 10:54:56.226 10161 4593 7978 W hsbr : [{0}] Failed to resolve name. status={1}
09-22 10:54:56.271 10161 4593 7978 W hsbr : [{0}] Failed to resolve name. status={1}
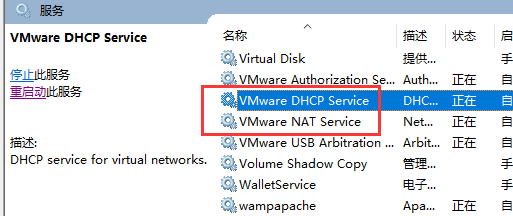
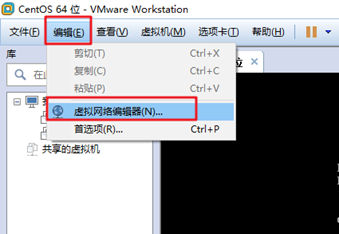
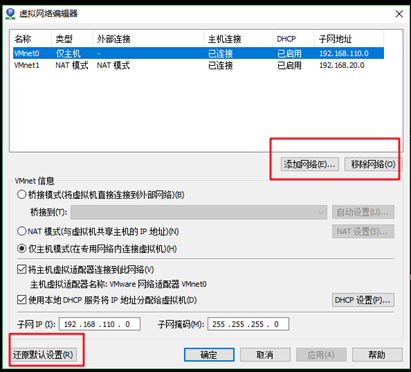




 本文详细介绍了在Linux环境下遇到ifup eth0命令执行失败的常见原因及解决方案,包括修改配置文件、检查虚拟机服务状态和调整虚拟机网络设置等步骤。
本文详细介绍了在Linux环境下遇到ifup eth0命令执行失败的常见原因及解决方案,包括修改配置文件、检查虚拟机服务状态和调整虚拟机网络设置等步骤。

















 3588
3588

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








