IPSEC在企业网上的应用
IPSEC的原理:
IPsec(Internet Protocol Security),是通过对IP协议(互联网协议)的分组进行加密和认证来保护IP协议的网络传输协议族(一些相互关联的协议的集合)。
IPsec由两大部分组成:(1)建立安全分组流的密钥交换协议;(2)保护分组流的协议。前者为網際網路金鑰交換(IKE)协议。后者包括加密分组流的封装安全载荷协议(ESP协议)或认证头协议(AH协议)协议,用于保证数据的机密性、来源可靠性(认证)、无连接的完整性并提供抗重播服务。
IPSec的安全特性主要有:
不可否认性 、反重播性、数据完整性、数据可靠性(加密)、认证。
案例:
在总部路由器R1和分支结构1路由器R2之间和总部路由器R1和分支结构2路由器R3之间各建立一个安全隧道;
实现 PC1代表的子网(192.168.1.x)与PC2代表的子网(192.168.2.x)之间×××通信;
实现 PC1代表的子网(192.168.1.x)与PC3代表的子网(192.168.3.x)之间×××通信;
安全协议采用 ESP 协议,加密算法采用 DES,认证算法采用 sha1-hmac-96,协商方式采用手工方式;
拓扑图:
实验要求:
1、实现分支机构1与总部之间的×××加密通信;
2、实现分支机构2与总部之间的×××加密通信;
3、实现分支机构1与分支机构2之间的×××加密通信;
R1配置:
sysname R1
int eth 0
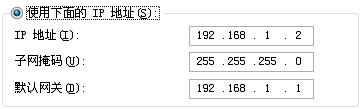
ip add 192.168.1.1 24
quit
int eth 1
ip add 10.1.1.1 24
quit
ip route 0.0.0.0 0.0.0.0 10.1.1.2
acl 3001
rule permit ip source 192.168.1.0 0.0.0.255 destination 192.168.2.0 0.0.0.255
rule permit ip source 192.168.3.0 0.0.0.255 destination 192.168.2.0 0.0.0.255
rule deny ip source any destination any
quit
acl 3002
rule permit ip source 192.168.1.0 0.0.0.255 destination 192.168.3.0 0.0.0.255
rule permit ip source 192.168.2.0 0.0.0.255 destination 192.168.3.0 0.0.0.255
rule deny ip source any destination any
quit
ipsec proposal tran1
encapsulation-mode tunnel
transform esp-new
esp-new encryption-algorithm des
esp-new authentication-algorithm sha1-hmac-96
quit
ipsec policy policy1 10 isakmp
security acl 3001
proposal tran1
tunnel remote 10.2.2.1
quit
ipsec policy policy1 20 isakmp
security acl 3002
proposal tran1
tunnel remote 10.3.3.1
quit
interface eth 1
ipsec policy policy1
quit
ike pre-shared-key abcde remote 10.2.2.1
ike pre-shared-key 12345 remote 10.3.3.1
R2配置:
sysname R2
int eth 0
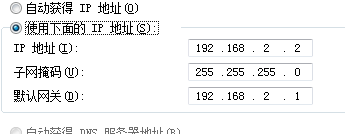
ip add 192.168.2.1 24
quit
int eth 1
ip add 10.2.2.1 24
quit
ip route 0.0.0.0 0.0.0.0 10.2.2.2
acl 3001
rule permit ip source 192.168.2.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
rule permit ip source 192.168.2.0 0.0.0.255 destination 192.168.3.0 0.0.0.255
rule deny ip source any destination any
quit
ipsec proposal tran1
encapsulation-mode tunnel
transform esp-new
esp-new encryption-algorithm des
esp-new authentication-algorithm sha1-hmac-96
quit
ipsec policy policy1 10 isakmp
security acl 3001
proposal tran1
tunnel remote 10.1.1.1
quit
interface eth 1
ipsec policy policy1
quit
ike pre-shared-key abcde remote 10.1.1.1
R3配置:
sysname R3
int eth 0
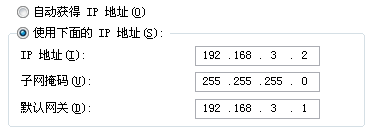
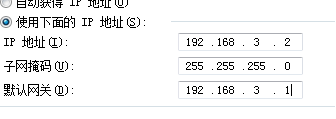
ip add 192.168.3.1 24
quit
int eth 1
ip add 10.3.3.1 24
quit
ip route 0.0.0.0 0.0.0.0 10.3.3.2
acl 3001
rule permit ip source 192.168.3.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
rule permit ip source 192.168.3.0 0.0.0.255 destination 192.168.2.0 0.0.0.255
rule deny ip source any destination any
quit
ipsec proposal tran1
encapsulation-mode tunnel
transform esp-new
esp-new encryption-algorithm des
esp-new authentication-algorithm sha1-hmac-96
quit
ipsec policy policy1 20 isakmp
security acl 3001
proposal tran1
tunnel remote 10.1.1.1
quit
interface eth 1
ipsec policy policy1
quit
ike pre-shared-key 12345 remote 10.1.1.1
SW配置:
vlan 10
port eth0/1
quit
vlan 20
port eth0/3
quit
vlan 30
port eth0/5
quit
int vlan 10
ip add 10.1.1.2 255.255.255.0
quit
int vlan 20
ip add 10.2.2.2 255.255.255.0
quit
int vlan 30
ip add 10.3.3.2 255.255.255.0
quit
测试:
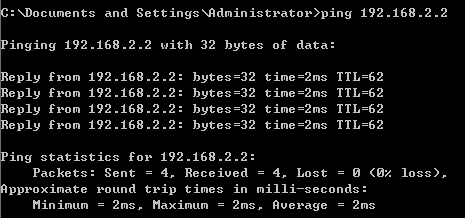
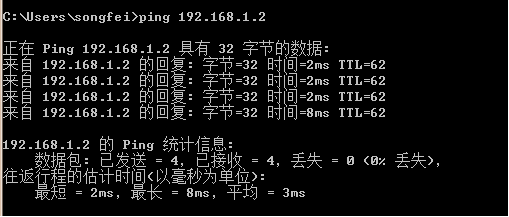
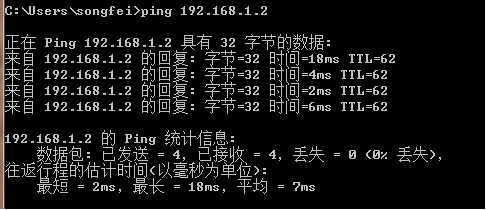
PC1主机ping PC2主机:
PC2主机ping PC1主机:
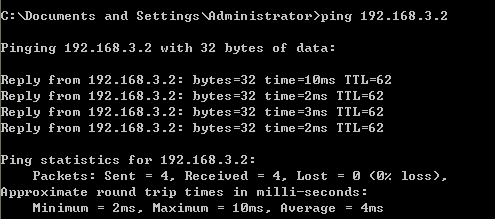
PC1主机ping PC3主机:
PC3主机ping PC1主机:
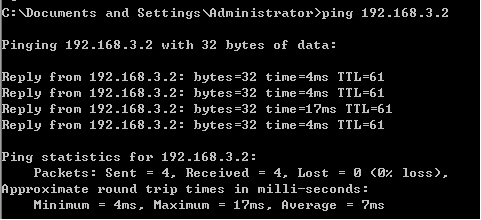
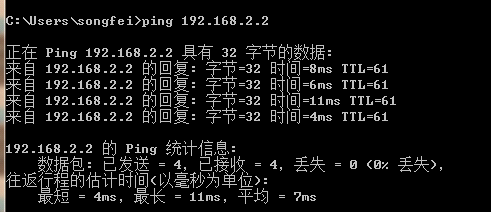
PC2主机ping PC3主机:
PC3主机ping PC2主机:
转载于:https://blog.51cto.com/tellzns/959638







 本文介绍了IPSec在企业网络中的应用案例,通过配置总部路由器R1与分支路由器R2及R3之间的安全隧道,实现了不同子网间的加密通信。采用ESP协议、DES加密算法与SHA1-HMAC认证算法确保数据安全。
本文介绍了IPSec在企业网络中的应用案例,通过配置总部路由器R1与分支路由器R2及R3之间的安全隧道,实现了不同子网间的加密通信。采用ESP协议、DES加密算法与SHA1-HMAC认证算法确保数据安全。

















 2386
2386

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








